N. The Lazarus Group from Korea Uses Known Flaws to Target Software Vendor
N. The Lazarus Group from Korea Uses Known Flaws to Target Software Vendor
A recent effort in which an unidentified software provider was hacked by making use of known security holes in another well-known program has been linked to the North Korea-aligned Lazarus Group.
According to Kaspersky, the assault sequences resulted in the threat actor using malware families including SIGNBT and LPEClient, a well-known hacking tool, for victim profiling and payload distribution.
Seongsu Park, Security Researcher
| “The attacker displayed a high degree of skill by introducing SIGNBT malware for victim control and using sophisticated evasion strategies.” “The attack was carried out by the SIGNBT malware, which used advanced techniques and a varied infection chain.”
“The Lazarus Group continued to target other software makers and exploit vulnerabilities in the company’s software.” As of mid-July 2023, some victims are allegedly being singled out as part of the most recent action. “In the current cybersecurity environment, The Lazarus Group is still a very active and adaptable adversary.” “The threat actor has proven to have a thorough awareness of IT settings and has honed their strategies to include taking advantage of flaws in well-known software. Once first infections are made, they may effectively propagate their virus thanks to this strategy.” |
The Russian Cybersecurity Vendor
| The target of the exploit, a software development company, had previously been the target of several Lazarus assaults, indicating an attempt to either steal source code or breach the software supply chain, as demonstrated by the 3CX supply chain attack. |
According to the company, the victims were the focus of reputable security software that uses digital certificates to secure web connections. The specific method by which the program was weaponized to spread SIGNBT is still unknown, and the software’s name was not revealed.
In addition to using different strategies to become and stay persistent on infected computers, the attack chains use an in-memory loader that serves as a conduit for the SIGNBT malware to be launched.
SIGNBT’s primary purpose is to connect to a distant server and obtain more commands to be executed on the compromised host. The malware’s usage of unusual strings prefixed with “SIGNBT” in its HTTP-based command-and-control (C2) communications has earned it the moniker.
- SIGNBTLG, for the initial connection
- SIGNBTKE, for gathering system metadata upon receiving a SUCCESS message from the C2 server
- SIGNBTGC, for fetching commands
- SIGNBTFI, for communication failure
- SIGNBTSR, for a successful communication
In contrast, the Windows backdoor has a vast array of tools at its disposal to take over the victim’s computer. Process enumeration, file, and directory actions, and the delivery of payloads like LPEClient and other tools for dumping credentials are all included in this.
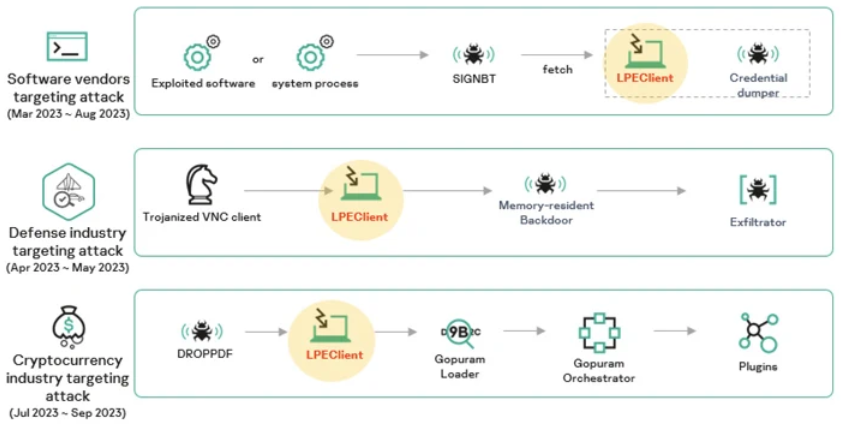
Using a variety of entry channels and infection techniques, Kaspersky claimed to have discovered at least three distinct Lazarus campaigns in 2023. However, the final-stage malware was always delivered by the LPEClient virus.
An implant known as Gopuram, which was utilized in cyberattacks on Bitcoin companies by using a trojanized version of the 3CX audio and video conferencing software, was made possible by one such campaign.
In addition to serving as evidence of the Lazarus Group’s constantly developing and growing toolkit of strategies, tactics, and techniques, the most recent discoveries represent only the most recent instance of cyber activities connected to North Korea.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security
Read More Article here
How to Keep Your Business A float in a Tense Situation?
A New Case of SIM SWAP Fraud in India’s Capital
After the iPhone 8, ALL Apple Smartphones Are In Grave Danger






