Nim-Based Malware is Delivered Using Bogus Microsoft Word Documents
Nim-Based Malware is Delivered Using Bogus Microsoft Word Documents
A new phishing attempt is using counterfeit Microsoft Word documents as an enticement to send a Nim programming language backdoor.
“Malware developed using unusual programming languages puts the safety community at a disadvantage because the unfamiliarity of researchers and reverse engineers can impede their inquiry,” Netskope researchers Ghanashyam Satpathy and Jan Michael Alcantara said.

Nim-based malware has been rare in the threat landscape, but that is progressively changing as attackers continue to either create bespoke tools from scratch using the language or convert current versions of their malicious programs to it.
This has been proved in the cases of loaders like NimzaLoader, Nimbda, and IceXLoader, and ransomware families like Dark Power and Kanti.

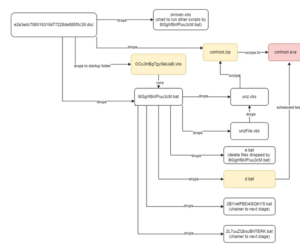
The Netskope attack chain begins with a phishing email with a Word document attachment that, when viewed, prompts the user to enable macros in order to start the deployment of the Nim malware. The sender of the email poses as a Nepali government official.
Once launched, the implant is in charge of enumerating running processes to determine the presence of recognized analysis tools on the infected host and swiftly terminating itself if one is found.

Otherwise, the backdoor connects to a remote server that impersonates a Nepalese official domain, including the National Information Technology Center (NITC) and waits for more instructions. The command-and-control (C2) servers have been rendered inoperable –
- mail[.]mofa[.]govnp[.]org
- nitc[.]govnp[.]org
- mx1[.]nepal[.]govnp[.]org
- dns[.]govnp[.]org
The researchers stated that Nim is a computer language that is both statically typed and compiled. “In addition to its recognizable syntax, the cross-compilation capabilities of this programming language enable attackers to create a single variant of malware that can be compiled to run on various platforms.”
Cyble has disclosed a social engineering effort that utilizes messages on social media platforms to distribute a new Python-based stealer malware dubbed Editbot Stealer. This virus is specifically designed to collect and extract valuable data through a Telegram channel controlled by the attacker.
While threat actors are testing novel malware variants, phishing campaigns have also been detected disseminating well-known malware like DarkGate and NetSupport RAT through email and compromised websites that employ deceptive update baits (also known as RogueRaticate). These activities are particularly prevalent within a group referred to as BattleRoyal.

Proofpoint, an enterprise security firm, reported the detection of a minimum of 20 campaigns employing DarkGate malware from September to November 2023. Subsequently, these campaigns transitioned to using NetSupport RAT earlier this month.
In early October 2023, a notable attack sequence was discovered. This sequence involved the combination of two traffic delivery systems (TDSs) – 404 TDS and Keitaro TDS. The purpose of this combination was to filter and redirect victims who met specific criteria. These victims were directed to a domain controlled by the attacker, which hosted a payload that took advantage of a security vulnerability known as CVE-2023-36025. This vulnerability, which had a high severity level, allowed for the bypassing of Windows SmartScreen. Microsoft addressed this vulnerability in November 2023.

BattleRoyal exploited this vulnerability as a zero-day, one month prior to its public disclosure by the technology giant.
DarkGate is specifically engineered to illicitly acquire data and acquire supplementary malware payloads, whilst NetSupport RAT, originally developed as a legitimate remote administration tool, has transformed into a powerful weapon utilized by malicious individuals to infiltrate systems and gain unrestricted remote control.

Proofpoint stated that cybercriminal threat actors are employing innovative attack chains, which encompass the utilization of diverse TDS tools, in order to facilitate the transmission of malware.
“Moreover, the actor employs both email and deceptive update lures, demonstrating the utilization of diverse social engineering tactics to persuade users into installing the ultimate payload.”
TA571 and TA577, two threat actors notorious for spreading several types of malware such as AsyncRAT, NetSupport, IcedID, PikaBot, and QakBot (also known as Qbot), have also utilized DarkGate.
“TA577, a highly notable distributor of Qbot, resumed the use of email threat data in September to distribute DarkGate malware. Subsequently, it has been observed deploying PikaBot in extensive campaigns consisting of tens of thousands of messages,” stated Selena Larson, a senior threat intelligence analyst at Proofpoint, in an interview with a reputable news organization.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE NEWS HERE






