Phishing Your Multi-Factor Authentication Codes is a Simple Task for Fraudsters. Here is How To Prevent It
Phishing Your Multi-Factor Authentication Codes is a Simple Task for Fraudsters. Here is How To Prevent It
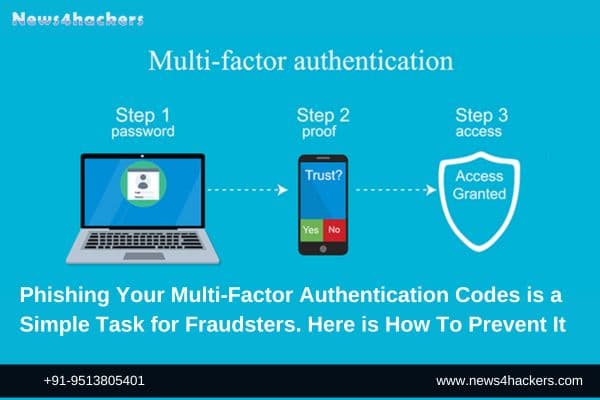
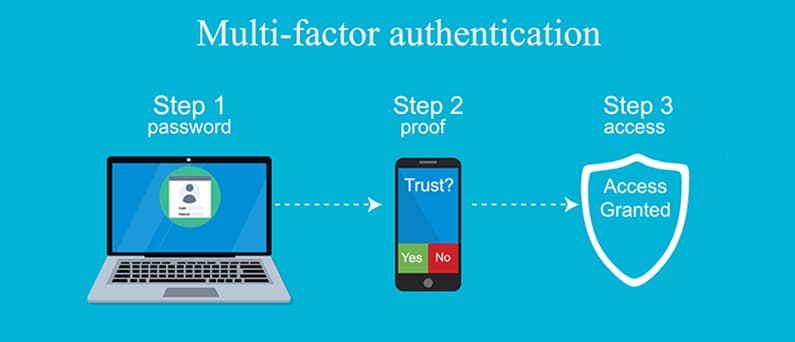
Multi-factor authentication (MFA) is becoming mandated on an increasing number of websites and services, which makes it significantly more difficult for fraudsters to gain access to your accounts when they are used. Oh, that is a wonderful thing.
On the other hand, as security advances, so do cybercriminals, who are constantly looking for new ways to perpetrate fraud against us.
There is a form of phishing that we are referring to as authentication-in-the-middle that recently appeared in online media. In spite of the fact that these methods, which are derived from man-in-the-middle attacks (MitM), have been around for some time, it seems that they are gaining popularity at the moment.

The way it works is that a user is tricked into visiting a phishing website that is disguised as a website that they typically visit, such as a bank account, an email account, or a social network account. Immediately after the user inputs their login credentials into the phony website, the information is then forwarded by the hackers to the real website, without the user being aware of the change.

After that, the user is prompted to complete their multi-factor authentication process. After they have finished this, which typically involves inputting a code or accepting a push notification, the information is then transmitted to the crooks, which enables them to proceed with the login process for the website.
Once the crooks have gained access to an account, they have the ability to manipulate the settings of the account, such as the email address, phone number, and password, in order to prevent the user from being able to log in. Alternatively, they can just empty out a bank account. If you are attempting to update one of these crucial settings, you may find that this helps you understand why many platforms ask for your personal identification number (PIN) or other authentication method once more

Links from social networking platforms or emails, where it may be difficult to determine whether a link is a genuine one, are used to lead victims to phishing websites such as these. Phishing websites can even appear in sponsored search results, which is similar to how we reported on scams involving technological assistance professionals.
How To Protect Yourself from Authentication-in-the-Middle Attacks?
There are several preventive measures that you can employ to protect yourself from authentication-in-the-middle Attacks. Some of the prominent ways are mentioned below in the following table:
| Keep your wits about you | The first step in avoiding con artists is to get familiar with the methods that they use. Keep in mind that you should not presume that sponsored search results are legitimate, and have faith that if anything appears odd, it most likely is. |
| Use security software | There are numerous security tools that block recognized phishing websites; nevertheless, domains are frequently temporary and are changed in a short amount of time. For your protection, Malwarebytes Browser Guard can be of assistance. |
| Use a password manager | It is not possible for password managers to automatically fill in a password for a fraudulent website, even if the website appears to be authentic to you. |
| Consider passkeys | In order to defend yourself against a wide variety of attacks, it is imperative that you continue to make use of multi-factor authentication, which is still something that should be enabled. Passkeys, on the other hand, will not enable cybercriminals to log in to your account in this manner since authentication-in-the-middle attacks are only effective with specific types of multi-factor authentication (MFA). Passkeys have already been implemented by a number of services, and there is no question that they will continue to be used in the future. |
Join a Decent Career in Cybersecurity For A Greater Good!
Users who wish to know more about these, as well as other fundamentals of ethical hacking and cybersecurity concepts, can opt for this mesmerizing training program of 1 Year Diploma in Cybersecurity Course by Craw Security, one of the leading cybersecurity training institutions in India. Technically, Craw Security is the sister vertical of News4Hackers, the Best Cybersecurity Info, and News Portal.
To know more about the same, or any other superb category training and certifications duly available on the Official Website of Craw Security, you can give them a call at their hotline mobile number +91-9513805401 and have an interaction with their team of professional study consultants to guide you better.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE






