Plugin RCE vulnerability affects 600K WordPress Sites

Plugin RCE vulnerability affects 600K WordPress Sites
A critical RCE vulnerability that affects 600k WordPress sites has been discovered in Essential Addons for Elementor, a popular WordPress plugin used in over a million websites.
It affects versions 5.0.4 and earlier.
An unauthenticated user can exploit the vulnerability through a local file inclusion attack, such as a PHP file, to execute code on the site.
“The local file inclusion vulnerability has to do with the use of user input data in PHP’s include function, which is part of the ajax_load_more and ajax_eael_product_gallery functions,” explain PatchStack researchers who found the vulnerability.
This attack requires that the site has the “dynamic gallery” and “product gallery” widgets enabled so that a none token check is performed.
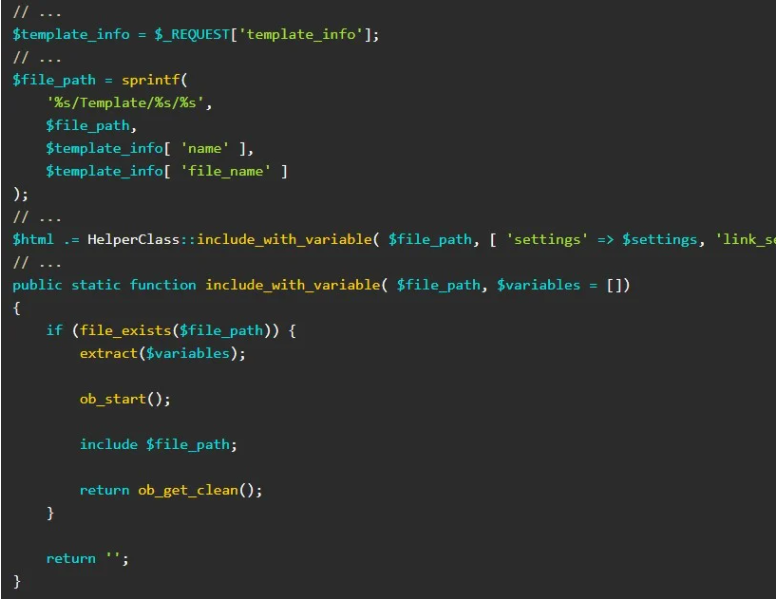
Example of code causing the error
Source: Patch Stack
Two patching attempts failed
The vulnerability was discovered by researcher Wai Yan Muo Thet on January 25, 2022, and the plugin developer already knew about it at the time.
As a result, the author released version 5.0.3 to address this issue by applying a “sanitize_text_field” function on user input data. However, this sanitization does not prevent local payloads from being included.
Second, version 5.0.4 added the “sanitize_file_name” function, attempting to remove special characters, dots, slashes, and anything else that could override the text sanitization step.
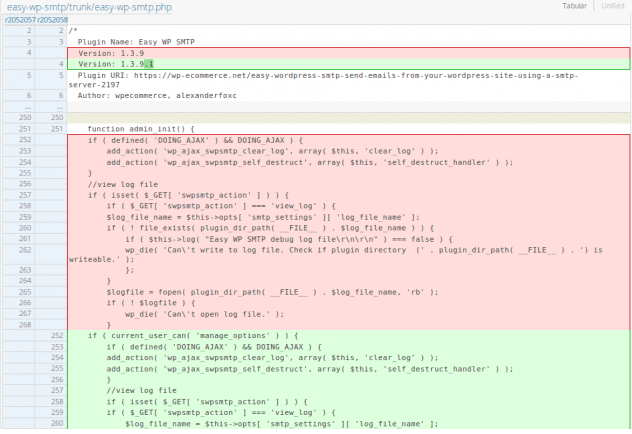
Function to clean up a text field
Source: Patch Stack
According to Patchstack, this was the version that was tested and found to be vulnerable, so the developer was informed that the fix was insufficient.
In version 5.0.5, the author implemented PHP’s “realpath” function, which prevents malicious pathname resolutions.
Limit and update
According to WordPress download statistics, this version was released last week, on January 28, 2022, and has only been downloaded 380,000 times up to this point.
More than 600,000 WordPress sites do not yet have the security update installed since the plugin is installed on over 1 million sites.
The Essential Addons for Elementor can be downloaded here or installed directly from the WordPress dashboard if you are one of the many people using it.
You can prevent actors from exploiting local file inclusion errors by following these steps, even if they can’t be fixed immediately:
Store your file paths in a secure database and assign each a unique ID. On the admissions list, only use verified and secured files.
Don’t put files on a web server that can be hacked, use a database instead.






