Specialists Issue a Caution to iPhone Users Regarding a Cunning Fake Lockdown Mode Attack

Malignant individuals can utilize an innovative technique of tampering after exploitation to visually mislead a victim into falsely perceiving that their Apple iPhone is operating in Lockdown Mode, while in reality, it is not. This can enable clandestine assaults to be executed.
The innovative technique, elucidated by Jamf Threat Labs in a study disseminated to The Hacker News, demonstrates that in the event a hacker has already penetrated your device, they can circumvent Lockdown Mode by triggering its activation.

Put simply, the objective is to enable the activation of a Fake Lockdown Mode on a device that has been penetrated by an attacker using alternative methods, such as exploiting unaddressed security vulnerabilities that can initiate the execution of unauthorized code.
Lockdown Mode, implemented by Apple in iOS 16, is an advanced security feature designed to protect persons at high risk from complex digital threats, such as mercenary spyware, by reducing the vulnerability to attacks.
What it fails to accomplish is to stop the activation of harmful software on a compromised device, thereby enabling a trojan that has been installed on it to control Lockdown Mode and create a false sense of security for users.
“If a phone is infected, there are no measures in place to prevent the malware from running in the background, regardless of whether the user activates Lockdown Mode or not,” stated security experts Hu Ke and Nir Avraham.
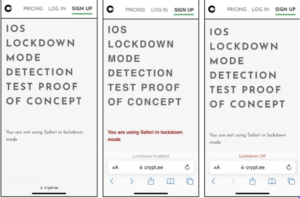
The imitation Lockdown Mode is achieved by intercepting functions that are activated when the setting is enabled, such as setLockdownModeGloballyEnabled, lockdownModeEnabled, and isLockdownModeEnabledForSafari. This interception creates a file named “/fakelockdownmode_on” and triggers a userspace reboot, which terminates all processes and restarts the system without affecting the kernel.
Furthermore, this implies that a malware program installed on the device without any means of long-term survival will persist and covertly monitor its users even after a reboot of this nature.

“According to Michael Covington, vice president of portfolio strategy at Jamf, users are less likely to suspect any malicious activity if they are deceived into thinking that their device is functioning normally and that they can activate additional security features.”
“It was unexpected that a security feature that received a lot of attention would have the user interface and implementation reality separated.”

In addition, a malicious party might modify the Lockdown Mode of the Safari web browser to enable the viewing of PDF files, which are typically restricted while the feature is on.
The researchers stated that Apple has upgraded Lockdown Mode to the kernel level starting with iOS 17. “This strategic action is a significant advancement in improving security, as modifications implemented by Lockdown Mode in the kernel generally cannot be reversed without performing a system reboot, due to the presence of current security measures.”

Jamf’s disclosure comes almost four months after it showcased an additional innovative technique on iOS 16. This technique might be exploited to evade detection and retain control over an Apple device by deceiving the user into believing that their iPhone’s Airplane Mode is activated.
“According to Covington, Jamf’s research has examined the ways in which interfaces establish trust and offer users reassurance regarding the security of a device through the exploration of Fake Airplane Mode and Fake Lockdown Mode.” “Our research demonstrates that user interfaces are susceptible to manipulation.”

“The threat landscape is changing, with examples such as phishing attacks delivered through HTTPS to deceive users into believing a website is secure, or malware that deceives users into thinking that safety features like Airplane Mode or Lockdown Mode are enabled.” We perceive these advancements as a progression of social engineering methods and anticipate their increased utilization in the future.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE





