Starlink Successfully Hacked Using $25 Modchip

At Black Hat, Researcher Lennert Wouters from Belgian, revealed how he ran a successful fault injection attack on a user terminal for SpaceX’s satellite-based internet system.
SpaceX, Lennert Wouters
A Cyber security researcher from belgian, hacked Elon Musk starlink, a satellite based internet system that was operated by SpaceX. In order to hack it, a homemade circuit board was used worth $25.

To get access, voltage fault injection attack was done on a Starlink User Terminal (UT)/ Satellite Dish that is used by authenticated users to access the system. It allowed him to break into the dish and explore the Starlink network the way he wanted. A presentation called “Glitched on Earth by Humans” at the annual ethical hacker conference, this week was the evidence of this attack.
Report on Wired, Presentation, Wednesday
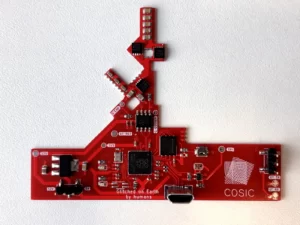
Wouters himself stripped down a satellite dish he bought, after that he made the custom board/ modchip that can be attached to the Starlink dish.
Tweet, Presentation, Material Assembled
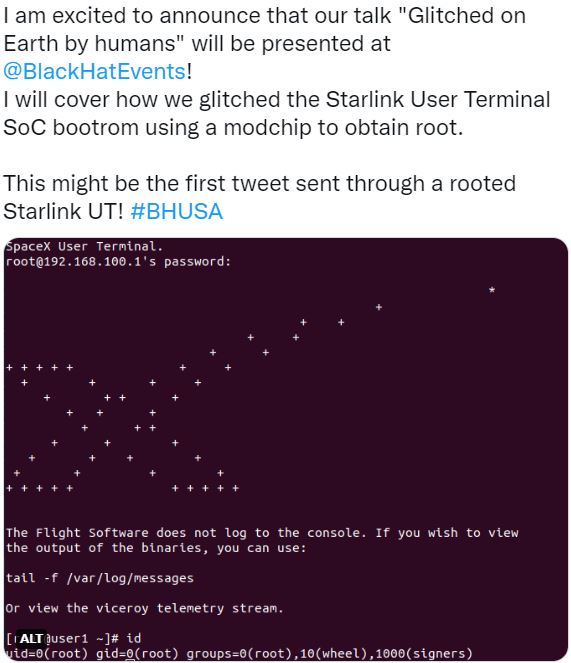
To create the toll, low-cost, off-the-shelf parts were used in the process. It was used to obtain root access by glitching the Starlink UT security operations center bootrom. He said that it was sent via a rooted Starlink UT.
The report, Process of making Modchip
- To design the modchip, Wouters scanned the Starlink dish.
- Then he created the design to fit over the existing Starlink board.
- He soldered the modchip to the existing Starlink PCB.
- Afterward, he connected it using a few wires.
| Note– The modchip was consisting of a Raspberry Pi microcontroller, flash storage, electronic switches and a voltage regulator |
Irreversible Mistake
Attack Procedure
- After attaching the tool to the Starlink dish, it launched a fault injection attack.
- That’s to temporarily short the system.
- It allowed bypassing Starlink’s security protections.
- That lets Wouters break into locked parts of the system.
Report
- His attack runs the glitch in contrast to the first bootloader.
- ROM bootloader that’s burned onto the system-on-chip can’t be updated.
- Then he deployed patched firmware on bootloaders.
- That gave him control of the dish.
Wouters first ran the attack in a lab before installing the modchip on the dish. That was exposed in a write-up about his presentation posted on the conference’s site. Once he gained access to the system, he could explore the Starlink network & its communication links.
Moreover, several other researchers could potentially build on the work to further exploit the Starlink ecosystem. Before publicly explaining this issue, he reported this vulnerability to SpaceX in a responsible way via its bug bounty program.
“Our attack results in an unfixable compromise of the Starlink UT and allows us to execute arbitrary code,” Wouters wrote. “The ability to obtain root access on the Starlink UT is a prerequisite to freely explore the Starlink network.”
Implications for Starlink
The Starlink is SpaceX’s low Earth orbit satellite constellation. It’s a project that has a goal to offer satellite internet coverage globally. Since 2018, 3,000 small satellites already are offering internet to areas where terrestrial networks can’t reach.
Companies such as Boeing, Amazon and Telesat did launch their own satellite constellations to provide internet from space.
Starlink System has Starlink’s UT as one of its three core components. Rest are the satellites that run about 340 miles above the Earth’s surface to beam down internet connections, and gateways. Those things are kept in use to transmit connections up to the satellites. The UTs also converse with satellites to offer internet access on Earth.
As has ever happened to any tech in history, due to the rise in utilization and installation of Starlink and rest satellite constellations cyber criminals got a greater cause to intervene in such matters to find loopholes in the security to attack severely.
Russia Intrude, Attack
Well, Russia saw benefit in attacking satellites offering online communication in Europe via attacking its technology physically as Russian Troops entered Ukraine on Feb 24. This attack was considered successful as it blocked communication services in Ukraine at just the time Russia wanted it.
It does affect other parts of Europe. Moreover, it also had a wavy effect that jammed fighting planes, navigation systems, and other important infrastructure.
Actions Taken by SpaceX
In consideration and the demand of the company, in the name of security, SpaceX reverted to Wouters’ presentation via inviting security researchers to “bring on the bugs”. That is to help the organization in protecting the Starlink System. Also, a brief explanation is demanded from researchers about how their techniques would protect Starlink.
The paper also congratulates Wouters’ research, calling it “technically impressive” before poking a series of holes in it and assuring that Starlink’s “defense-in-depth approach to security limits the overall impact of this issue to our network and users.”