THE CARTHAGE AREA HOSPITAL AND THE CLAYTON-HEPBURN MEDICAL CENTER IN NEW YORK WERE HIT BY THE LOCKBIT RANSOMWARE GANG
In New York, the Carthage Area Hospital and the Clayton-Hepburn Medical Center were both compromised by the LockBit ransomware organization.
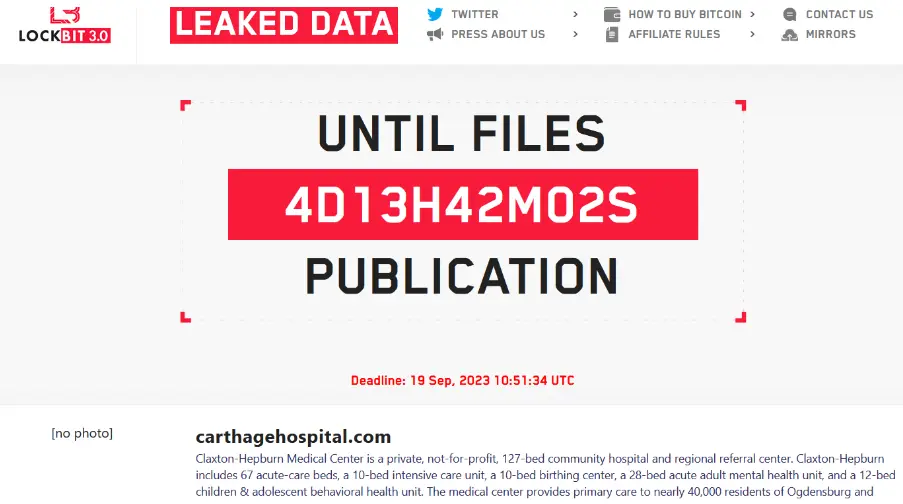
The Carthage Area Hospital and Claxton-Hepburn Medical Center are two significant hospitals the Lockbit ransomware gang claims to have been compromised. In upstate New York, the two hospitals provide care for hundreds of thousands of patients.
The two hospitals have been suffering greatly due to the hack that happened at the end of August in recent weeks. On September 2, the phone systems were repaired. However, a number of other services were impacted by the intrusions.
Emergency departments at Claxton and Carthage have been diverted out of an abundance of caution. Most of the appointments were rescheduled, and the patients were moved to other regional hospitals.
Hospital Administration
| “All patients with rescheduled appointments will be contacted. Any patient with a medical emergency should still call their doctor. Patients with urgent needs should visit the closest emergency room..” |

The two hospitals are currently battling cyberattack recovery.
Along with the Division of Homeland Security and Emergency Services and the New York State Department of Health, the FBI looked into the occurrence.
The Record Media Reported
The Claxton-Hepburn Medical Center said it would keep canceling outpatient appointments at clinics and doctor’s offices this week due to the serious nature of the situation there.
The hospitals have now been included in the LockBit ransomware gang’s Tor leak site. If the victims don’t pay the ransom, the gang allegedly plans to disclose the allegedly stolen material by September 19, 2023.
The gang has not yet made any samples of the allegedly stolen material public as evidence of the attack.
The Lockbit gang and its associates have attacked hospitals before. The LockBit ransomware group officially apologized for the attack on the Hospital for Sick Children (SickKids) in January and provided the hospital with a free decryptor.
It is well known that the organization forbids its affiliates from attacking healthcare institutions. Its policy prevents encrypting the systems of companies where failure could result in fatalities.
The gang claimed that one of its associates assaulted SickKids in violation of the organization’s guidelines, and as a result, the affiliate was blacklisted.
Other healthcare institutions have also been targeted in the past by Lockbit gang associates. Early in December 2022, a cyberattack that was ascribed to the organization targeted the Hospital Center of Versailles.
As a result of the cyberattack, the Hospital Centre of Versailles—which houses Andre-Mignot Hospital, Richaud Hospital, and the Despagne Retirement Home—had to suspend operations and relocate some patients.
In August, the gang attacked the Center Hospitalier Sud Francilien (CHSF), a hospital southeast of Paris. The attack disrupted the emergency services and surgeries and forced the hospital to refer patients to other structures.
Local Media
| Threat actors demand a $10 million ransom for the decryption key to restore encrypted data. |
US hospitals were lately the target of other ransomware assaults. Because it disclosed the intrusion of Prospect Medical Holdings and the theft of personal data from the company, the Rhysida ransomware group recently garnered news.
Prospect Medical Holdings was blackmailed by the Rhysida ransomware organization with the release of the stolen data if a ransom of 50 Bitcoins (worth $1.3 million) was not paid. This week, the same organization asserted that it had broken into three additional US hospitals.
At the end of August, a cyber attack affected the systems of three hospitals and other medical institutions run by Singing River Health System.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective,which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.
Read More Article Here:
Engineering graduate loses Rs. 20 lakh after joining a Telegram group to look for work
Google Defends its Search Business in the Largest U.S. Antitrust Case of the Century.







