Top 5 Most Popular Cyberattack Types in 2023

In a general tone, cyberattacks are malicious acts taken by people or organizations to enter computer systems, networks, and other electronic devices without authorization, disrupt, or harm them. These assaults may be intended to steal confidential information, cause financial harm, or interfere with business operations.
In this blog post, we will update you about the Top 5 Most Popular Cyberattack Types in 2023. Moreover, if you wish to know more about the same or any other cybersecurity concept, you may join a fully-fledged cybersecurity training program by Craw Security. In addition, Craw Security offers world-class cybersecurity training under the guidance of proactive training professionals having years of authentic experience.
1. Phishing Attacks

Definition and Description
Phishing Attacks mean delivering false emails or messages that seem to come from a reliable source in order to dupe people into disclosing personal information or clicking on a dangerous link.
Popular phishing techniques in 2023
A few popular phishing methods have been utilized in the past and might be employed again in the future. Some of them are given below:
| Spear Phishing | This type of targeted phishing involves delivering messages that are tailored to certain people or groups and pretending to be from a reliable source, like a coworker or a vendor. Tricking an individual into disclosing personal information or clicking on a harmful link is the aim. |
| Business Email Compromise (BEC) | BEC attacks entail posing as a senior executive or another reliable individual within a corporation to deceive staff into taking unlawful activities, such as sending money to a phony account. |
| Smishing | Smishing is a type of phishing in which SMS messages are used to deceive people into clicking on a dangerous link or divulging personal info. |
| Vishing | Vishing is the practice of tricking people into divulging confidential data, including account numbers or passwords, through voice conversations. |
| Social Media Phishing | In order to deceive people into disclosing personal information or clicking on a dangerous link, this entails creating fictitious social media accounts or pages. |
How to protect yourself from phishing attacks?
A person may secure one’s individual data or classified business information from the harmful phishing attack by adopting the following changes:
- Be cautious of unsolicited emails and messages
- Verify the sender
- Check for spelling and grammar errors
- Use security software
- Enable multi-factor authentication
- Use strong passwords
- Stay informed
2. Ransomware

Definition and Description
A sort of malicious software known as ransomware conceals the data of a victim or prevents the victim from using a computer system or network before demanding payment, typically in the form of cryptocurrency, to unlock the contents or restore access. The victim’s data is ultimately held bound by the ransomware cyber adversary until the ransom payment is paid.
Various methods, such as phishing emails, malicious attachments, or taking advantage of holes in computer systems, can be used to spread ransomware. Once a system has been infected, the ransomware usually begins to encrypt files and then displays a message to the user demanding the funds within a predetermined window of time.
Different types of ransomware in 2023
Some common types of ransomware attacks have been giving trouble to the common people till now and will be providing the same for a longer period of time. In addition, we have mentioned some different types of ransomware in 2023 in the following table:
| Crypto ransomware | The target’s files are encrypted by this kind of ransomware, which makes them unavailable unless the ransom is paid. Crypto ransomware examples include the WannaCry and Locky viruses. |
| Locker ransomware | Until the ransom amount is paid, locker ransomware shuts the user out of their desktop, laptop, or smartphone, stopping them from obtaining any files or programs. Jigsaw and Petya are a couple of locker ransomware examples. |
| Scareware | Scareware is a sort of ransomware that pretends to be a virus or other malware by displaying bogus alarms or notifications on the victim’s computer screen. After that, the victim is asked to provide a fee to end the alleged threat. Scareware comprises applications like System Security and WinFixer. |
| Doxware | Doxware, commonly referred to as leakware, is a sort of ransomware that not just conceals the data of the victim but also makes the threat to post private or confidential information publicly unless a ransom payment is received. Doxware includes programs like Maze and REvil/Sodinokibi. |
| Mobile ransomware | Smartphones and tablets are the primary targets of mobile ransomware, which may either halt the gadget or encrypt files belonging to the victim until the ransom payment is made. Fusob and Koler are a couple of instances of mobile ransomware. |
Ransomware-as-a-service (RaaS) in 2023
A sort of cybercrime company structure known as ransomware-as-a-service (RaaS) enables people with little to no technical ability to start ransomware attacks. In exchange for a cut of the revenues, RaaS gives potential attackers access to pre-built ransomware programs, technical help, and occasionally even distribution routes.
How to prevent and respond to ransomware attacks?
Technical safeguards and user education are used to prevent ransomware attacks. The following actions can be taken to stop ransomware attacks:
- Keep software and operating systems up-to-date
- Use anti-virus software
- Be cautious of suspicious emails and attachments
- Regularly back up important data
- Implement network segmentation
3. Malware

Definition and Description
A malicious software program known as malware is made to harm, interfere with, or seize authority over a computer system, network, or other device without the owner’s permission or knowledge. Malware can appear in a wide variety of ways and is always changing to avoid detection and security measures.
Various channels, such as attachments to emails, fraudulent websites, contaminated software downloads, and social engineering techniques, may spread malware. After being installed, malware can have a variety of detrimental effects on the victim’s personal computer or network, including poor performance, the theft of confidential data, and the ability for remote attacker control.
Popular malware types in 2023
Some common types of malware include:
| Viruses | An example of malware is a virus, which spreads throughout a computer by reproducing and joining up with trustworthy files or programs. |
| Trojans | Trojans are a subset of malware that impersonate trustworthy programs to deceive visitors into downloading and installing them. |
| Ransomware | Malware, known as ransomware, encrypts the victim’s data and prevents access to them unless a ransom is paid. |
| Spyware | A form of malware known as spyware tracks the victim’s behavior without their authorization or agreement, frequently with the intention of collecting sensitive data. |
| Adware | A form of malware known as adware causes pop-ups or unwelcome adverts to appear on the victim’s computer. |
Malware distribution methods in 2023
Malware dissemination techniques are always changing and becoming more complex. Here are a few widespread malware distribution techniques for 2023:
- Email phishing
- Malvertising
- Drive-by downloads
- Social engineering
- Watering hole attacks
How to detect and remove malware infections?
Malware infections can be difficult and time-consuming to detect and remove. However, you can follow these below-mentioned best practices to identify and get rid of malware infections hassle-free:
- Use anti-virus software
- Monitor for suspicious activity
- Check your browser extensions
- Use malware removal tools
- Backup and restore
- Seek professional help
4. DDoS Attacks

Definition and Description
The term “Distributed Denial of Service” refers to a particular kind of cyberattack that occurs when a cyber intruder utilizes numerous hijacked devices or systems to saturate a targeted website, server, or network with a great deal of traffic or requests. A DDoS attack seeks to take over the target system, rendering it inaccessible to authorized users and disrupting the service.
A botnet is a network of computers that have been infested with malware and are currently under an intruder’s control. It can be utilized to launch a DDoS assault. The target system can be efficiently overloaded and rendered inoperable by the intruder using the botnet by transmitting a lot of traffic or queries to it.
Distributed Denial-of-Service (DDoS) attacks in 2023
Some of the latest trends in DDoS attacks are mentioned below:
| Amplification attacks | A vulnerable server receives a modest quantity of traffic and replies by sending a large volume of traffic to the intended recipient in an amplification attack. It enables attackers to increase the volume of traffic they may deliver to the target, strengthening the attack. |
| IoT botnets | Networks of hacked Internet of Things (IoT) devices that may be employed to conduct DDoS assaults are known as IoT botnets. Attackers will become increasingly dependent on IoT botnets in 2023 because there are so many susceptible IoT devices and so few security safeguards in place to defend them. |
| Application-layer attacks | Application-layer attacks are designed to deplete the resources of specific apps or services, like web servers or databases, by delivering a huge number of requests. These attacks may be more challenging to identify and stop than other DDoS attacks. |
| Ransom DDoS attacks | Attackers who use ransom DDoS tactics promise to conduct a DDoS attack against a target if a monetary ransom is not paid. Attackers are utilizing this technique to extort funds from companies and organizations more frequently in 2023. |
| 5G-based DDoS attacks | Faster and more dependable communication is made possible by 5G technology, but it can also be exploited to carry out more potent DDoS attacks. In addition, attackers are anticipated to use 5G networks in 2023 to launch more intricate and sophisticated DDoS attacks. |
Popular DDoS attack vectors in 2023
DDoS attacks can be launched utilizing a wide range of attack vectors, each of which focuses on a particular system vulnerability or weak point. The most common DDoS attack methods in 2023 are listed below:
- Volumetric attacks
- SYN Flood attacks
- DNS amplification attacks
- Application-layer attacks
- IoT botnet attacks
How to protect against DDoS attacks?
By enabling yourself to accept varied methodologies in order to protect against DDoS attacks, you can adapt the following changes:
- Implement DDoS mitigation strategies
- Keep software and systems up-to-date
- Monitor network traffic
- Conduct regular security audits
- Use traffic filtering and rate-limiting
- Develop a response plan
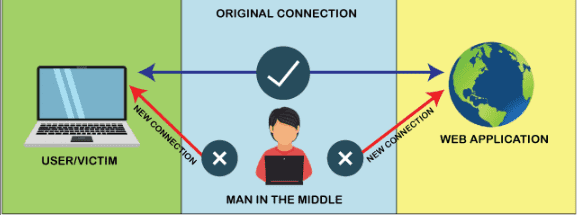
5. Man-in-the-Middle (MitM) Attacks
Definition and Description
A cyberattack known as a “man-in-the-middle” (MitM) attack occurs when an attacker listens in on a conversation between two people and steals or modifies sensitive data without the other party’s knowledge. In a MitM attack, the attacker can read, change, and read between the two parties’ communications without either party’s knowledge or agreement.
By standing in the way of the two parties and intercepting their communication, the attacker efficiently functions as the channel’s middleman. ARP spoofing, DNS spoofing, SSL stripping, or phishing attacks are just a few of the techniques the attacker can employ to conduct a MitM attack.
Popular MitM attack techniques in 2023
These are some common MitM attack strategies that will be used in 2023:
| ARP Spoofing | Intruders can employ ARP (Address Resolution Protocol) counterfeiting in order to intercept network traffic by tricking the device used by the victim into rerouting traffic to the intruder’s device by delivering false ARP messages to the victim’s device. |
| DNS Spoofing | The goal of a DNS (Domain Name System) spoofing attack is to route traffic from the device of the victim to a fraudulent website by intercepting the victim’s device’s DNS request and sending a phony DNS response. |
| SSL Stripping | HTTPS traffic is intercepted via SSL (Secure Socket Layer) stripping attacks, which downgrade the encrypted channel to an unsecured HTTP connection. As a result, the intruder is able to see and change the two parties’ dialogue. |
| Wi-Fi Spoofing | To trick users into connecting to the phony network, attackers can create a bogus Wi-Fi network with a name that sounds similar to a real network. As soon as they are in contact, the attacker can listen in on and change the victim’s dialogue. |
| Email Spoofing | Attackers can deceive users into supplying confidential data by sending fraudulent emails that look to be from a reputable source, like a bank or other financial institution, using email spoofing techniques. |
| Bluetooth Spoofing | Attackers can obtain confidential information or take control of Bluetooth-enabled devices by intercepting and manipulating Bluetooth signals using Bluetooth spoofing tactics. |
How to prevent and mitigate MitM attacks?
Some of the premier ways to prevent and mitigate MitM attacks:
- Use Encryption,
- Keep Software and Systems Up-to-Date,
- Use Two-Factor Authentication,
- Avoid Public Wi-Fi Networks,
- Verify Website and Email Authenticity,
- Use a Firewall,
- Deploy Anti-Malware Software, etc.
Kindly read another article:
Nigerian National from Delhi is Detained by Pune Police for Online Gift Scam
RSAC 2023 Revealed 10 Innovative and Amazing Cybersecurity Tools