What Ethical Hacking Skills Do Professionals Need?

What Ethical Hacking Skills Do Professionals Need?
In the universe of cybersecurity, the term “hacker” is commonly employed to refer to individuals possessing sophisticated computer technology expertise, enabling them to deceive businesses or circumvent security measures in order to gain unauthorized access to networks. Certain hackers utilize their expertise to engage in fraudulent activities, theft, or other illicit behaviors, but others derive pleasure from the inherent difficulty. Irrespective of the underlying reasons, it is projected that cybercrime will result in a global financial loss of $6 trillion by 2021. Additionally, a single organization is targeted by ransomware every 11 seconds.

The process of recovering after a cyberattack incurs both temporal and financial expenses, with no assurance of complete restoration for the affected company. Data breaches, a form of cybercrime, have the potential to harm a company’s reputation among consumers and clients and may result in legal consequences. Therefore, possessing ethical hacking skills is crucial for every organization that has a significant online presence.
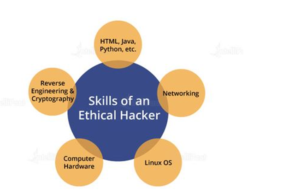
Yes, you have correctly perceived the information. Ethical hackers, often known as “white hat” hackers, possess the ability to adopt the mindset of malicious individuals that their organizations aim to thwart. Through the process of stress-testing an organization’s networks and operations, vulnerabilities can be identified and potential cyber-attacks can be anticipated more effectively, hence mitigating the risk of being compromised.

What Do Ethical Hackers Do?
An ethical hacker is, in many respects, comparable to a secret shopper who enters retail establishments while anonymous in order to identify flaws and provide input on areas that require development. Secret consumers might even fabricate instances of shoplifting in order to evaluate the security of a store. Likewise, ethical hacking expertise — akin to that utilized by cybercriminals—is of immeasurable value to organizations seeking to identify vulnerabilities, fortify their networks, and enhance their processes.

Even though organizations frequently utilize penetration testers to inspect a limited number of potential network vulnerabilities, ethical hackers fulfill a significantly more comprehensive function. Furthermore, they might attempt to deceive employees into divulging sensitive information, examine the storage and security measures in place for laptops and mobile devices, and investigate every conceivable method by which a “black hat” hacker could cause damage.
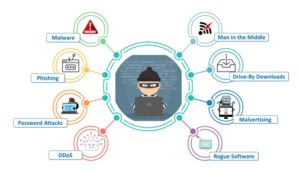
Ethical hackers, according to the EC-Council, the preeminent certification organization for cyber security professionals, are “employees of an organization who can be relied upon to attempt to breach computer systems and networks utilizing the same methods and techniques employed by malicious hackers.” Although ethical hackers may emerge from the “dark side” after reimbursing their social obligations, it is also possible to acquire certification and develop ethical hacking skills through classroom instruction.
Ethical Hacking Skills and the Role of a White Hat Hacker
Simply stated, the role of an ethical hacker is to simulate the activities of a malicious hacker within an organization, approaching it as if it were a cybercriminal, without actually launching an attack. Instead, they will diligently disclose any vulnerabilities or concerns and actively pursue remedial actions to fortify the defenses of the system.

An ethical hacker may utilize any combination of the following methods to infiltrate a system or identify weaknesses:
- Conducting a system scan of an organization using port scanning tools such as Nessus or Nmap in order to identify unprotected ports. It is possible to examine the vulnerabilities associated with each of these ports and implement corrective actions.
- Verifying that security patch installations are not susceptible to exploitation.
- Participating in social engineering techniques, such as dumpster diving, which involves physically searching through waste cans for passwords, charts, sticky notes, or any other vital information that could be exploited to launch an attack.
- Incorporating additional social engineering strategies, such as shoulder surfing or playing the kindness card, to trick employees into divulging their credentials.
- Engaging in activities designed to circumvent intrusion detection systems (IDS), intrusion prevention systems (IPS), honeypots, and firewalls.
- Intrusion into wireless networks, circumvention and hacking of encryption, and takeover of web servers and applications.
- Examining matters pertaining to the pilferage of laptops and employee malfeasance.
Legitimate hackers have an obligation to disclose any vulnerabilities they encounter in the course of their operations, as such information is considered privileged and could potentially be exploited for illicit intentions. Undoubtedly, even the most advanced ethical hacking capabilities are rendered futile in the event that the organization neglects to sufficiently address any identified vulnerabilities or issues that are disclosed.
What Skills and Certifications Should an Ethical Hacker Obtain?
Being a former “bad hacker” who has chosen to don a white hat instead of a black one suggests that you are likely well-informed about the techniques utilized in the industry. Nonetheless, it is important to acknowledge that ethical hacking skills, similar to unethical hacking skills, are in a constant state of development. In light of the fact that vigilant individuals are consistently striving to discern the most recent schemes, it is critical to sustain one’s advantage through vigilant monitoring of developments.

As with any other occupation, an essential element of achievement is a fervent interest in the field. In conjunction with a comprehensive understanding of networking and programming, this will facilitate an individual’s achievement in the domain of ethical hacking. In addition to possessing the ability to think like a black hat hacker, which is a fundamental aspect of ethical hacking development, it is imperative to have a well-defined objective of bolstering the security of your employer or client.

Similar to other positions within computer and network security, ethical hackers are in significant demand, and this demand will only grow in tandem with the escalating severity and financial implications of cyber attacks. Organizations in dire need of certified and experienced ethical hackers are, as expected, willing to pay a premium for their services. The average annual salary for a certified ethical hacker in the United States is $90,000. However, for seasoned professionals, salaries often exceed the $120,000 threshold.
The CEH (v12) certification is an obvious choice for the following: security professionals, forensic analysts, intrusion analysts, and most significantly, individuals who aspire to enter these disciplines and refine their ethical hacking abilities. Indeed, numerous IT companies have instituted CEH certification as a prerequisite for employment in security-related roles. Having the most recent CEH certification will facilitate access to a lucrative and fulfilling profession.

The CEH (v12) – Certified Ethical Hacking Training and Certification course offered by Craw Security educates its learners on the intricacies of backdoors, trojans, and countermeasures. This enhances their comprehension of more advanced topics such as intrusion detection systems, firewalls, honeypots, and wireless hacking. If you wish to enroll in this corresponding certification course of CEH v12 Training in Delhi by Craw Security, then you may give them a call at their hotline mobile number +91-9513805401.

Moreover, Craw Security is the sister company of News4Hackers, a leading cybersecurity information, and news portal, which is widely recognized for its immense contribution to providing enhanced cyber attack news and informatory articles in the public interest.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE
The New Secret Code Function of WhatsApp Enables Password Protection for Private Conversations
Japan’s Space Agency Hit by a Cyber Attack, Targets at Active Directory
Infosys Employee Got Scammed of ₹3.7 Crore









