A Serious SQLi Vulnerability Endangers More Than 200K Websites: Coming Up With An WordPress Plugin Alert

A Serious SQLi Vulnerability Endangers More Than 200K Websites: Coming Up With An WordPress Plugin Alert
With over 200,000 active installs, the well-known WordPress plugin Ultimate Member has a serious security problem that has come to light.
With a maximum score of 10, the vulnerability identified as CVE-2024-1071 has a CVSS score of 9.8. It is acknowledged that security researcher Christiaan Swiers found and reported the vulnerability.
Wordfence, WordPress Security Company, Advisory, Last Week
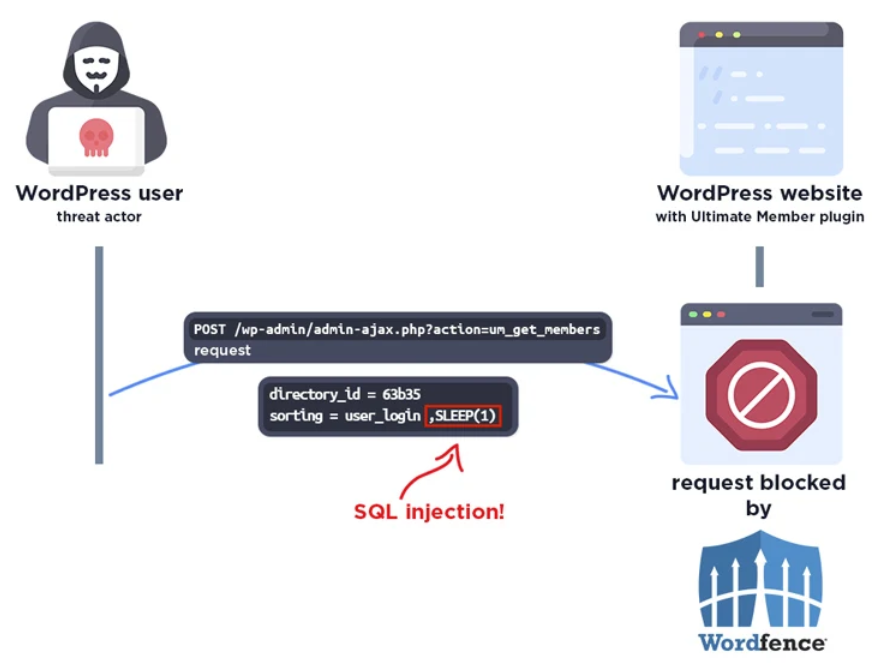
| The plugin is “vulnerable to SQL Injection via the ‘sorting’ parameter in versions 2.1.3 to 2.8.2 due to insufficient escaping on the user-supplied parameter and lack of sufficient preparation on the existing SQL query.” |
Consequently, the vulnerability might be leveraged by unauthenticated attackers to append more SQL searches to pre-existing queries and retrieve confidential information from the database.
Note that only users who have enabled the “Enable custom table for usermeta” option in the plugin settings are impacted by this issue.
The plugin developers released version 2.8.3 on February 19, 2024, which includes a remedy for the issue, in response to responsible disclosure on January 30, 2024.
Updating the plugin to the most recent version is encouraged for users to minimize potential threats, especially because Wordfence has already stopped one effort in the last 24 hours to take advantage of the vulnerability.
Another vulnerability in the same plugin (CVE-2023-3460, CVSS score: 9.8) was actively used by threat actors in July 2023 to establish rogue admin users and take over susceptible websites.
The development coincides with a rise in a new effort that uses infected WordPress websites to either directly inject cryptocurrency drainers like Angel Drainer or divert users to Web3 phishing sites that are infected with drainers.
Denis Sinegubko, Sucuri Researcher
| “These attacks leverage phishing tactics and malicious injections to exploit the Web3 ecosystem’s reliance on direct wallet interactions, presenting a significant risk to both website owners and the safety of user assets.” |
It also comes after the discovery of a brand-new drainer-as-a-service (DaaS) scheme known as CG (short for CryptoGrab), which manages an affiliate network with 10,000 members that speak Chinese, English, and Russian.
Cyfirma, Report, Last Month
| Actor-controlled Telegram channels pose a hazard since they can direct attackers to a telegram bot that helps them conduct fraud operations independently of third parties.
“In addition to offering Cloudflare security for the newly registered domain, the bot enables a user to obtain a free domain, clone an existing template for the new domain, and specify the wallet address to which the fraudulent cash should be paid.” |
Additionally, the threat organization has been seen cloning an already-existing, genuine website and adding Cloudflare security to it using two specially created Telegram bots, named SiteCloner and CloudflarePage, respectively. The majority of the time, hacked X (previously Twitter) accounts are used to distribute these pages.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for the News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.
READ MORE ARTICLE HERE






