Cyber Security vs Information Security: The Ultimate Guide

The distinction between cyber security and information security ( Cyber Security vs Information Security ) is frequently blurred in the perception of individuals without specialized knowledge in the field. Although the fundamental premise remains the same, there are notable distinctions in their overall emphasis and execution. There exists a distinct trajectory for each sector, with infrequent instances of convergence. The objective of this tutorial is to provide an academic exploration of the distinctions between cyber security and information security, elucidating the respective roles and activities of each sector.
What Is Information Security?
Information security, sometimes known as InfoSec, encompasses the methodologies and protocols employed by organizations to safeguard their data. This encompasses a range of policy configurations that serve to restrict unauthorized individuals from gaining access to company or personal data. The field of information security is characterized by its rapid evolution and dynamic nature, encompassing a wide range of activities such as network and security design, as well as testing and auditing.
The field of information security is concerned with safeguarding sensitive data against unauthorized actions, including but not limited to examination, alteration, documentation, interruption, or elimination. The primary objective is to ensure and maintain the confidentiality of critical data, such as client account details, financial records, and intellectual assets.
What constitutes the field of information security? The three key aspects to be considered are governance, secrecy, and integrity.
Governance Framework
The Information Security and Governance Framework (ISGF) comprises a collection of recommendations and optimal approaches for the effective management of information security within an organizational context. The framework facilitates the process of identifying, categorizing, and safeguarding confidential data, as well as adopting security measures and protocols. The ISGF encompasses recommendations pertaining to incident response and disaster recovery as well.
The International Standards for Grid Federation (ISGF) is founded upon a multitude of global standards, one of which is the ISO/IEC 27001:2013 standard that pertains to the management systems for information security. The alignment of the mentioned system with the NIST Cybersecurity Framework and the EU General Data Protection Regulation (GDPR) is evident.
The International Standard for Good Governance (ISGF) has been developed with the intention of accommodating and adjusting to the unique requirements of an organization. This technology has the potential to be utilized by businesses of all sizes and across diverse industries.
Confidentiality
Confidentiality refers to the safeguarding of information to prevent its unlawful dissemination. Confidential information should not be disclosed to individuals who lack a legitimate need for access. Maintaining confidentiality is of utmost importance for safeguarding personal as well as business-related information. The disclosure of personal information, such as medical records or financial data, should be limited to individuals who possess a genuine necessity for access. Maintaining the confidentiality of business information, such as trade secrets or competitive tactics, is crucial in order to safeguard against competitors gaining the upper hand.
Ensuring the security and confidentiality of electronic information is of utmost importance. Information security measures are implemented to mitigate the risk of unauthorized access, ensuring that only authorized individuals are able to access sensitive information. On the other hand, confidentiality measures are put in place to prevent unauthorized disclosure, safeguarding the confidentiality of the information from being accessed or shared with unauthorized parties. Both factors are crucial in ensuring the security of electronic information.
Integrity
Integrity is a multifaceted concept encompassing both the virtue of honesty and the possession of robust moral convictions. Additionally, it denotes a condition of completeness and unity, devoid of division or fragmentation. Within the realm of data, the concept of integrity pertains to the precision and entirety of the information. The significance of data integrity lies in its ability to prevent erroneous or insufficient data, which might result in erroneous decision-making or actions. The preservation of data integrity is critical throughout all stages of the data life cycle, encompassing data gathering, storage, processing, and dissemination.
The preservation of information security and integrity is of utmost importance as it serves to safeguard the confidentiality, availability, and integrity of data. The safeguarding of data from illegal access, use, disclosure, interception, or destruction is imperative due to its inherent value as an asset. Data encompasses a wide range of information, which may consist of confidential data belonging to either businesses or individual users.
Availability
The concept of availability refers to the extent to which a system can be accessible and utilized. In order to safeguard the confidentiality and accessibility of information, it is imperative for businesses to establish and implement comprehensive policies and procedures aimed at safeguarding their data. In addition, it is imperative for organizations to establish a comprehensive strategy for effectively addressing security events. Moreover, it is imperative for individuals to do frequent system testing and diligently back up their data.
Organizations that fail to prioritize information security and availability face the potential consequences of data breaches, including financial losses, reputational harm, and regulatory sanctions. Data breaches might potentially result in periods of inactivity, interrupting the normal functioning of business activities and resulting in decreased productivity.
What Is Cyber Security?
Cybersecurity encompasses the comprehensive measures undertaken to safeguard computer systems, networks, devices, and applications against various forms of cyber assaults. The proliferation of digital transformation has led to a significant escalation in cyber security risks, hence posing a substantial risk to the security of sensitive data.

Due to the intricate nature of geopolitics and the increasingly diverse range of attack strategies, both enterprises and national governments have come to recognize cyber security as a significant issue. An emerging trend observed in numerous organizations is the integration of information risk management as an integral component of their overarching risk management strategy.
The following article delves into the subject of cyber security frameworks, exploring their various types, the advantages they offer, and the recommended practices for their implementation.
Cybersecurity is commonly seen as a focal point for mitigating the risks posed by the subsequent threats.
Social Engineering
According to estimates, social engineering assaults account for more than 90 percent of all data breaches. Social engineering is a sort of security attack that capitalizes on human contact to manipulate individuals into allowing unauthorized access to systems and networks or inadvertently disclosing confidential information. Attackers employ diverse methodologies to exploit human susceptibilities, including manipulation of anxieties and emotions.
Phishing/Vishing/Smishing
In the realm of cybersecurity, phishing, vishing, and smishing represent prevalent and perilous dangers. Phishing refers to the fraudulent practice of deceiving individuals into divulging sensitive information, such as credit card numbers, usernames, passwords, and other personal data, by masquerading as a trustworthy entity. Vishing is like phishing, only that it employs voice calls or text messages instead of emails. Similarly, smishing refers to a form of phishing that exploits SMS messages as a means to entice individuals into being victims.
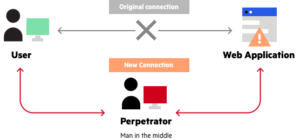
Phishing kits are malevolent instruments employed by cybercriminals for the purpose of initiating phishing campaigns. A phishing kit encompasses a comprehensive set of tools and resources that enable cybercriminals to execute phishing attacks effectively. These kits typically consist of pre-designed templates, scripts, and detailed instructions, providing the necessary components for carrying out such malicious activities. Phishing kits facilitate the streamlined execution of advanced attacks, enabling individuals with limited expertise in criminal activities to engage in such malicious endeavors.
A Man-in-the-Middle (MITM) phishing kit refers to a specific kind of phishing kit that empowers malicious actors to intercept and reroute network communication between two parties, hence facilitating the illicit acquisition of sensitive data, including login credentials and financial information. Man-in-the-middle (MITM) phishing assaults can result in significant ramifications for both individuals and companies.
Pretexting
Pretexting entails the act of fabricating and employing a fictitious or deceptive online persona with the intention of acquiring confidential information or gaining unauthorized access to someone else’s accounts. According to cybersecurity specialists, there is a growing concern regarding the increasing prevalence of pretexting, which can be attributed to the enhanced sophistication of criminal tactics.
Pretexting is often used to access someone’s email or social media accounts. Through the act of assuming the identity of the account owner, the offender is able to initiate password resets, transmit communications, and gain unauthorized entry to confidential data. Pretexting may also facilitate the acquisition of financial data, including credit card or bank account details.
Baiting
Baiting is a cybersecurity strategy wherein an assailant employs enticing content to entice unsuspecting individuals into interacting with a harmful hyperlink or accessing a malevolent attachment. The bait employed in such instances can encompass a wide range of stimuli designed to captivate the intended target, including but not limited to alluring electronic correspondence, intriguing written material, or seemingly innocuous digital appendages. Upon the victim’s engagement with the bait, the attacker is able to initiate the execution of the attack.
The utilization of baiting as a tactic is deemed beneficial due to its ability to exploit the human factor. Regardless of the robustness of a company’s cybersecurity measures, its vulnerability remains inherent when an employee succumbs to a baiting attack.
Quid Pro Quo
In a quid pro quo assault, the perpetrator initiates communication with the target individual and assumes a false identity as a representative of a bona fide institution. Subsequently, they proceed to solicit information or seek a favor in return for a reciprocal offering. As an illustration, the perpetrator may assert that they will furnish the target with a complimentary software upgrade contingent upon the target disclosing their credit card details.
Identifying these attacks might pose challenges due to the hacker’s frequent utilization of deceptive email addresses and websites designed to mimic authentic sources. Moreover, it is presumed that the majority of individuals are inclined to offer assistance to an authentic establishment.
What are Cloud and Network Security?
Cloud and network security are paramount in ensuring the safety and integrity of data. Encryption and various security measures are implemented to safeguard data from unauthorized access.
Network security refers to the measures taken to safeguard a network from unauthorized access. This includes the implementation of mechanisms that restrict network access solely to authorized users, as well as the encryption of all data transmitted within the network. The implementation of firewalls is an integral aspect of network security, serving to prevent illegal traffic from gaining access to the network.
Cloud security refers to the measures and protocols implemented to safeguard data stored in cloud computing environments, with the primary objective of preventing unauthorized individuals from accessing or altering the information. This entails the implementation of measures to restrict access to authorized individuals exclusively, as well as the encryption of any data stored in the cloud. Cloud security encompasses many security measures, including the implementation of firewalls and other protective mechanisms, to mitigate the risk of unwanted data access.
Cloud and network security plays a crucial role in ensuring the protection and integrity of data. Nevertheless, each of these options possesses its own set of benefits and drawbacks. When making a decision on the selection of a security solution for data protection, it is imperative to carefully evaluate and analyze both available possibilities in order to develop an effective strategy that effectively addresses and balances the demands of both critical objectives.
Cyber Security Threats and Attacks
Numerous cybersecurity threats and attacks possess the potential to compromise the security of individuals, corporations, and governments. Several of the more prevalent examples include:
- Phishing scams encompass fraudulent electronic communications, such as emails, that mimic the appearance of authentic sources. However, these messages originate from malicious individuals who aim to deceive recipients into divulging personal information or compromising their computer systems with malware.
- The term “malware” is derived from the phrase “malicious software” and pertains to software applications that are specifically created with the intention of causing harm or rendering computer systems inoperable. The prevalent forms of malware encompass viruses, worms, and trojan horses.
- Denial of service (DoS) attacks refer to deliberate efforts aimed at rendering a computer or network resource inaccessible to its designated users through the inundation of the target with an excessive volume of traffic or data demands.
- SQL injection attacks exploit vulnerabilities present in web applications that utilize Structured Query Language (SQL) for database interaction. Malicious actors have the capability to inject malevolent SQL code into input fields present on a webpage, enabling the execution of unauthorized activities or the acquisition of sensitive data.
- Cross-site scripting (XSS) attacks encompass a kind of injection attack wherein malevolent code is inserted into a webpage or web application. Malicious actors possess the capability to illicitly acquire cookies, login credentials, and other forms of confidential data.
- Man-in-the-middle (MitM) attacks encompass a category of eavesdropping attacks wherein an assailant intercepts the communication between two entities and proceeds to eavesdrop on or manipulate the transmitted data.
- Buffer overflow attacks manifest when assailant endeavors to exceed the capacity of a memory buffer by writing an excessive amount of data, hence resulting in the corruption of data or the execution of malevolent code.
Cyber Security vs. Information Security
The ongoing online discourse about the semantic distinction between cyber security and information security warrants an examination of cyber security as a subset of information security. Information security can be conceptualized as an overarching framework wherein cyber security, cryptography, and mobile computing are encompassed as distinct components.
However, establishing a definitive differentiation might pose challenges, particularly considering that mere geographical factors can have an influence. The term “cyber security” is extensively employed within the United States, but in various other nations, it is often referred to as “information security.” Various variables, including the ones mentioned, have contributed to the sustained existence of the ongoing discourse surrounding the comparison between cyber security and information security.

Additional variations might be observed within the discourse surrounding cyber security versus information security. Cybersecurity pertains to the safeguarding of information inside the realm of cyberspace, whereas information security encompasses the protection of data not just within cyberspace but also extends to other domains. To clarify, it should be noted that the Internet or the endpoint device may be only a fraction of the broader context. Both cybersecurity and information security encompass the safeguarding of cyberspace against various forms of malicious software, such as ransomware, spyware, malware, and other detrimental programs that have the potential to cause significant disruptions and damage. In contrast, cyber security experts possess a highly specialized and specific area of expertise.
Cybersecurity experts actively engage in safeguarding servers, endpoints, databases, and networks by identifying and addressing risks arising from gaps and misconfigurations. In alternative terms, their primary duty entails the prevention of breaches. Individuals who possess exceptional talent often exhibit a cognitive approach akin to that of hackers, and it is plausible that some of these individuals may have previously engaged in hacking activities. Indeed, data loss prevention is a significant problem for information security specialists. Collaboration with cyber peers is undertaken to collectively address the matter at hand, with the potential for assuming a more comprehensive responsibility in the prioritization of highly sensitive data and the formulation of a recovery strategy in the event of a security breach.
It is advantageous to consider the distinction between data and information at a more fundamental level. Data can encompass a wide range of information, such as numerical values, although it is important to acknowledge that not all data holds the same significance or value. The interpretation of the data and its level of sensitivity are within the domain of information security experts. In the event that a numerical sequence was to represent a customer’s credit card number, it becomes the duty of information security teams to guarantee their adherence to governmental standards. Once more, they collaborate closely with their cyber counterparts to ensure the security of the most vital data. However, they bear a considerably larger portion of the overall security responsibility within a business.
| Cyber Security | Information Security |
| The safeguarding of data in the digital space. | Assists in establishing secure means of data accessibility. |
| Risks include malware and network attacks. | It is imperative to ensure the accuracy of information and restrict unauthorized access. |
| Safeguarding data through the utilization of encryption techniques. | The consideration of compliance and policies is taken into account. |
Looking to Gain More Practical Knowledge on Cybersecurity?
The study of cyber security holds significant interest for individuals immersed in the digital space. However, a subset of individuals seeks to assume a proactive stance in safeguarding both information and cyber security. If you are interested, please consider exploring the 1 Year Diploma in Cyber Security Course by Craw Security, which is a sister vertical of News4Hackers and the Best Cybersecurity Training Institute in India, which tends to be a proven leading tech frontier in providing world-class IT Security Education to all the persons and enterprises in Pan India.
Hence, rather than wasting your precious time searching for good courses at every other website, try to take a demo session in Craw Security at the earliest availability. Book your slots by giving them a call at their hotline mobile number, +91-9513805401, and have a word with their highly excelled team of educational consultants.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Read More Article here





