Malicious Browser Extensions Steal Users’ Passwords & Cryptos which was deployed via malware

ViperSoftX! What is this malicious thing, and how it is possible for it to get the data out of your chrome. Well, because of this malware a lot of people suffered and it uses an extension to steal user’s passwords and cryptos.
These extensions are especially customed for stealing data and can run on chromium-based web browsers. The transporter of these extensions is a malware known as ViperSoftX.
VenomSoftX Software Installer was the add-on which was found out by Czech-based cybersecurity company. Also, its amazing features came in front that allows:
- Access Website Visit
- Steal Credentials
- Clipboard Data
- Swap Cryptocurrency Address via AiTM attack (adversary-in-the-middle).
Feb, 2022
Fortinet recognized ViperSoftX as JavaScript-based remote access trojan and cryptocurrency stealer.
Colin Cowie, Threat Analyst, Sophos
He found out early this year about that malware that it was using a browser extension to further move its information-gathering goals.
| Jan Rubin, Avast Researcher
“He said in a technical write-up- ● This multi-stage stealer exhibits interesting hiding capabilities, concealed as small PowerShell Scripts on a single line in the middle of otherwise innocent-looking large log files, among others,” ● “Extension gave it a shot by imitating as a popular browser extension known as Google Sheets. ● VenomSoftX is a data stealer installed onto unaware victim’s browser that gets full access over to each website user visits from the infected browser. ● “Since the transactions on blockchains/ledgers are inherently irreversible, when the user checks the transaction history of payments afterward, it is already too late,” |
Main focus of ViperSoftX is on:
- Stealing Cryptocurrencies
- Clipboard Swapping
- Fingerprinting the infected machine
- Downloading & Running Arbitrary Additional Payloads
- Giving commands.
The ViperSoftX malware was distributed via cracked software that are available over file-sharing sites. This method was used to let the downloaders believe that those were genuine applications with open features.
Those who downloaded these operable files got clear cracked software with added files that all access over the host, and apply the ViperSoftX PowerShell Script.
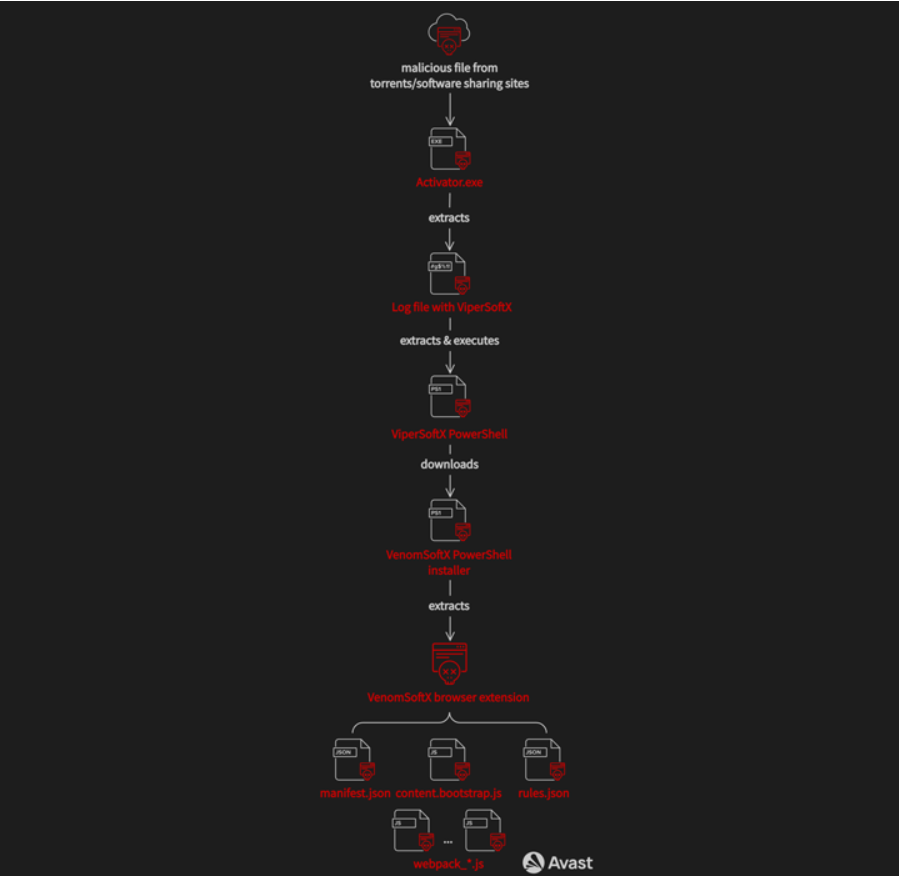
Latest versions of this malware can also load VenomSoftX add-on, which they get from a remote server, and implement on Chromium-based browsers. Some of those are:
- Google Chrome
- Microsoft Edge
- Opera
- Brave
- Vivaldi
Process of installing
- Searching – LNK files for the browser applications
- It modifies shortcuts with a “–load-extension” command line switch.
- That switch points to the path where the unpacked extension is.
This also needs attention that – Load Extension Tactoc is also getting in use by another browser-based data stealer known as Chromeloader/ Choziosi Loader/ ChromeBack.
Both VenomSoftX and ViperSoftX are customized to steal cryptocurrencies from victims. However, unlike ViperSoftX, VenomSoftX cooperates with API request to drain digital assets via crypto exchanges. There, ViperSoftX acts like a clipper to reroute fund transfers to an attacker-controlled wallet.
Extension targeted potential services such as:
- com
- Binance
- Coinbase
- io
- Kucoin
Well, now the attack made an enhancement in its performance. Traditional clipboard swapping now doesn’t make any unnecessary moments that could create any suspense. That’s because wallet address is being replaced at a much faster rate.
Avast
Since early 2022, 93,000 infections were detected and blocked. In that attack, Majority of users from following locations:
- India
- The U.S.
- Italy
- Brazil
- The U.K.
- Canada
- France
- Pakistan
- South Africa
Nov, 8, 2022
Analysis proved that the adversary made a profit of $1,30,421 in various cryptocurrencies by the operations, and it was accurate from the hard-coded wallet addresses in the revealed samples. Well, after a perfect calculation amount dropped to $1,04,500.
Kindly read more articles:
5 Million AirAsia Traveler Data were stolen by Daixin with Employees
AXLocker Ransomware Encrypted Files and Accessing your Discord Accounts. Be Aware!