5 Million AirAsia Traveler Data were stolen by Daixin with Employees

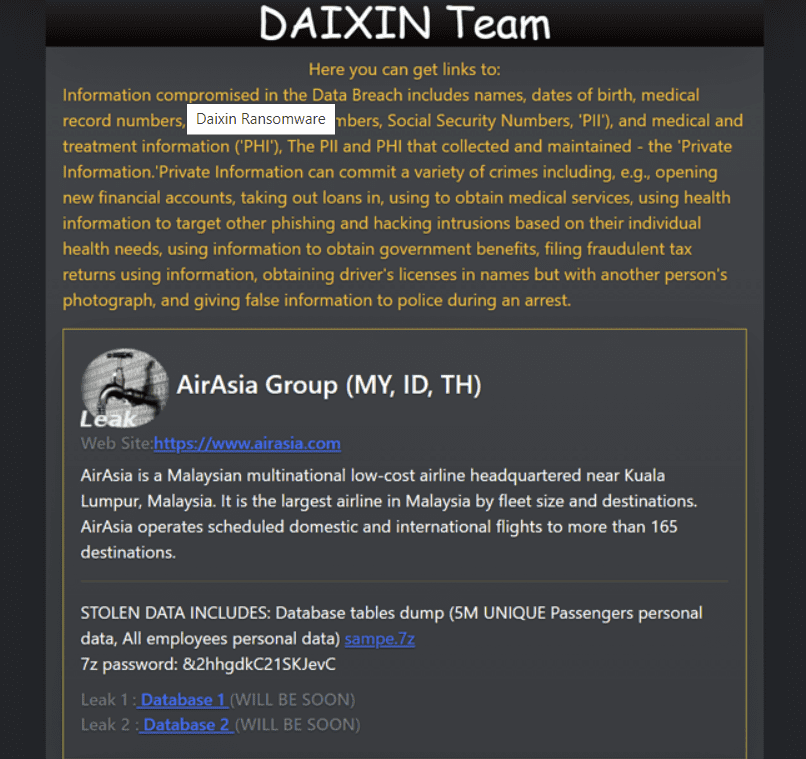
Malaysian Low-cost Airline “AirAsia” suffered a massive data breach. Daixin Team (Adversary) was the one to operate this malicious operation, and the leak included sample data while the release was done on Data Leak Portal.

It took a whole week to unleash news about the attack when the organization already became a victim of a ransomware attack on Nov 11 and 12. Daixin Team was already in the Headlines a few days ago for CISA Alert.
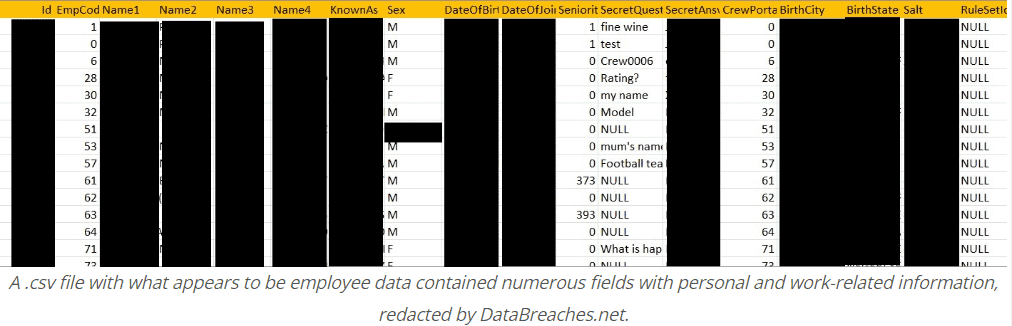
After compromising the data of AirAsia, they informed DataBreaches.net about the attack and said – 5 Million Unique Passengers and all employees’ data were victimized in this operation. Daixin provided 2 .csv files to both Data Breaches and AirAsia Group.
One of them involved data related to named passengers. There the second one included employees’ data with several fields that were:
- Name
- Date of Birth
- Country of Birth
- Location
- Date of Employment
- Secret Query
- Answer
- Salt
Spokesperson, Daixin
“AirAsia reverted to the attack. They started chatting and asked – if Daixin’s negotiator could provide a sample of the data leaked in the attack. While they got the sample, they stood and asked – on what grounds Daixin would delete the data in exchange for payment.”
The victimized organization didn’t even try to start any negotiations. This could have expressed that they never had any heart to pay the price for the same.
Spokesperson to DataBreaches
‘Usually, everyone wants to negotiate a smaller amount,”
DataBreaches.net didn’t even know the calculation; Daixin demanded a Decryption Key. Also, for the deletion count of data that had been exfiltrated and about informing AirAsia Group of the loopholes that got exposed & exploited.
The unleashed samples revealed passenger data and booking IDs, along with sensitive information related to company staff.
Good Deeds from Daixin
In the process of encryption, Daixin left locking “XEN, RHEL (host of flying arms, like – radars, air traffic control, and many more). Daixin has made it clear to DataBreaches.net that there were several attempts where they stepped back from encrypting or destroying anything if the estimated results could be chaotic.
However, Daixin left the organization as it was after the event; there, the attacker destroyed backups and had control over many resources. According to them, “We could have done more than that if we ever had a thought about it.”
The reason for the attack was the poor security measures of the AirAsia Organization.
Mostly, the unworthy cause of the attack was the company’s lack of standards and absence of proper security measures. This annoyed Daixin to the extent that they left the ground and retreated from making any further attacks.
Daixin took AirAsia as a Garbage Bag that shouldn’t be there in the first place. Their Pentesters said – let the newbies clean this trash; that have enough time.
| ● DataBreaches.net was shocked because they didn’t hear of any other incident like this. They got reported by adversaries for getting annoyed by the underperformance of security of another organization.
● DataBreaches.net – Daixin’s spokesperson – AirAsia’s poor security management enhanced its system or not. The spokesperson replied. ● “Totally! Internal Management lacked a set of rules, which resulted in low performance. Every new system admin seemed to have built a shed next to the previous building.” |
| ● In any event, Daixin informed DataBreaches that in addition to leaking the passenger and employee data on their dedicated leak site, the group plans to make information about the network — “including backdoors” — available privately and freely on hacker forums.
● “The DAIXIN Team disclaims responsibility for future negative consequences,” they told DataBreaches.net. |
18, Nov, 2022
Asia Group’s Data Protection Officer received an email from DataBreaches.net and on again on 19, Nov, 2022. However, they got no response.
During these years, Malaysian Businesses have often been targeted by adversaries. This was accumulated by the count of database leaks on hacking-related forums/ site attest searching. The current victim is not the only one that suffered from Daixin’s cyber-attacks. Malaysian Airlines explained data security events in both years, which were 2020, & 2021.
Jan, 2022
AirAsia Group turned the tables and became Capital A Berhad, running as AirAsia. Moreover, this organization is one of Malaysia’s MNCs (low-cost Airlines). Also, it became the largest airline in Malaysia, according to fleet size and locations.
| “Daixin Team was recently the subject of an advisory from the U.S. cybersecurity and intelligence agencies, which warned of attacks mainly aimed at the healthcare sector.
Other victims of the criminal group include: ● Fitzgibbon Hospital, ● Trib Total Media, ● ista International, ● GmbH, ● and OakBend Medical. |
For more amazing facts & information like this, you can follow us on News4Hackers. Leave a comment if you have any queries.
Kindly read more articles :
AXLocker Ransomware Encrypted Files and Accessing your Discord Accounts. Be Aware!
Data Breach Case of 12,000 Patients has been Disclosed by New York-Presbyterian Hospital.







