10 Excellent Tools To Keep Complete Anonymity Online
10 Excellent Tools To Keep Complete Anonymity Online
At the moment, everyone seems involved in a struggle.
Although not immediately apparent, the majority of the world’s population is already being impacted. In fact, no physical weapons, including bombs, aircraft, or vehicles, are utilized in this conflict.
This conflict concerns our online privacy.

Identity theft constituted 69% of data intrusions, according to a survey conducted last year. According to another survey, the global incidence of identity theft-related data breaches has increased consistently over the past four years. This trend is expected to continue as hackers acquire easier access to increasingly sophisticated tools.
By enforcing stronger data protection norms on data controllers and processors, the EU’s GDPR may halt this trend. Ads that monitor our online activities have been utilized by these entities to collect and store our information for years; this is yet another reason to safeguard our online anonymity.
However, this fresh rule has only been implemented within the EU for over a month. It will therefore be some time before its long-term effects become apparent.
What steps ought we to take in the event that malicious hackers attempt to acquire and exploit our personal information?
The answer is pretty simple. We protect ourselves by utilizing the available tools that ensure our complete online anonymity.
Thus, the following is a list that you might discover to be beneficial.
1. VPNs
A virtual private network (VPN) ensures user anonymity by concealing their true IP address and online activities from inquisitive eyes.
Your browser typically transmits a query containing your IP address whenever you conduct an online search. This query is forwarded by your ISP to a DNS server, which subsequently directs you to the appropriate website.

Undoubtedly, your ISP (as well as each server that processed your query) possesses the capability and is probably inclined to observe and track any data that traverses their infrastructure, including your IP address and personal information. This enables them to monitor your every online activity.
By encrypting your data and designating you an anonymous IP, a VPN safeguards your identity. This entails encrypting any queries transmitted to the ISP, thereby preventing the display of the actual IP address.

Because of this, utilizing a VPN is among the most effective methods for maintaining online anonymity.
Nevertheless, every VPN is not created equal. You must select the most effective one if you desire absolute security. Additionally, avoid complimentary VPNs. The majority generate revenue through the sale of user data to advertisers.
You should conduct a comparative analysis of multiple VPNs in order to identify the most suitable one. However, this is easier said than done given the abundance of VPN services available.
Consult reputable website evaluations in order to identify the most suitable virtual private network (VPN) for your requirements.
2. TOR Browser
The Onion Router (TOR) is a web browser that further enhances your online anonymity through the utilization of multiple layers of encryption. As a result, your internet activity, encompassing “visits to websites, online posts, instant messages, and other communication forms,” is safeguarded.

It operates by initially applying three layers of encryption to your data. Following this, your data is bounced three times, with each bounce removing one layer of encryption. After reaching the intended server, the data “reestablishes” each layer it has previously lost as it subsequently returns to your device.

Additionally, TOR can be enhanced by utilizing it in conjunction with a compatible VPN.
It is essential to observe, however, that your use of TOR will not remain hidden. Certain websites may impose limitations on permissions granted via TOR.
3. Virtual machine
A virtual machine is essentially an internal duplicate of a physical computer. It enables the emulation of a different device via an application. After that, the settings for this emulated computer can be customized to your liking.

However, this tool is most effective when applied to duties that do not require an internet connection. When opening a file while ensuring that no one is observing is when it is most effectively utilized. After the file has been opened, the virtual machine is easily deleted.
VirtualBox is a software application that is compatible with Windows, Linux, and Mac.
4. Proxy servers
Proxy servers function as intermediaries connecting a user’s device to the internet. It is essentially an additional device that processes requests from the internet. Although conceptually comparable to a virtual machine, it exists as a distinct physical machine.
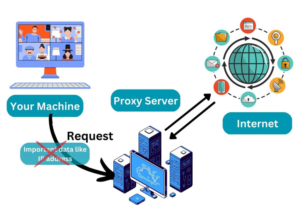
It protects your anonymity similarly to how a virtual private network (VPN) does (by concealing your IP address), but it can also block or accept cookies but prevent them from reaching your device and transmit a different user agent to prevent your browser from being identified.
The majority of VPN providers also provide proxy servers, making them a viable resource when seeking a dependable one.
5. Fake emails
As its name implies, a phony email is an email address that is not associated with the recipient’s actual identity.
Anonymity online is enhanced by sham emails, which not only conceal the sender’s true identity but also protect the recipient from phishing emails and malware, both of which are readily transmitted via email.
Using a fake email service or registering for an email account without providing your actual information is all that is required to create a fake email.
6. Incognito mode
“Going incognito” is the most straightforward method of achieving anonymity.
During this mode, your device will not store any data, including browsing history, cookies, site data, or information entered into forms.
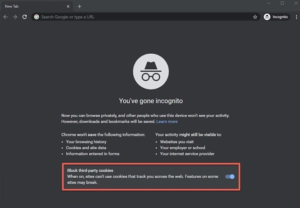
By enabling the privacy mode on the majority of web browsers, it is simple to conceal your online activities from other users of the same device.
7. Ad blockers
Ads are currently ubiquitous. Advertising is and always has been a profitable industry. However, there is a distinction between excellent and bad advertisements.
Effective advertisements are those that aim to reach the entire population. Poor advertisements, or interest-based marketing as the businesses they work for prefer to call it, violate our online privacy by targeting us individually through the monitoring of our online activity and location. However, tracking algorithms are not unlawful and have even been deemed “clever.”

Nevertheless, advertisements that contain malware that can infect your device and prevent you from using it are the worst.
Ad blockers are a viable solution for mitigating these risks to one’s privacy and online safety. Typically, ad blockers are implemented as browser extensions that function immediately and require no further configuration.
You have the option of installing AdBlock, uBlock Origin, or Adblock for Google Chrome. Opera offers the following ad blockers: uBlock Origin, Adblock Plus, and Opera Ad Blocker.
8. Secure messaging apps
If you must utilize an online messaging application, you should be aware that the most widely used ones may not offer the highest level of security.

Although Facebook Messenger does offer a “secret conversation” feature, the social networking platform Facebook has never precisely been known for its security.

Use applications such as Signal or Telegram instead. In addition to utilizing end-to-end encryption, these applications also support voice conversations.
9. File shredder
The significance of the right to be forgotten has become more prominent in the news due to the introduction of the General Data Protection Regulation by the European Union. This privilege requires entities that collect or process data to delete the PII of the data subject entirely from their systems.

You can implement the same procedure on your personal device by utilizing a “file shredding” application. However, the matter is that it is very difficult to completely remove sensitive files from a device.

Merely removing the file by deleting it and emptying the recycle container on your device does not effectively eliminate it; rather, your device merely perceives the space it occupies as vacant and accessible space. These “dead” files may return to torment you if someone with the knowledge to locate them discovers them.
One may employ software applications such as Eraser (for Windows) or Dr. Cleaner (for Mac) to “shred” sensitive files by repeatedly overwriting them with arbitrary patterns comprising random sets of data.
10. DuckDuckGo
DuckDuckGo is an alternative search engine to Google and Bing, which employ behavioral sensors to provide targeted advertisements, as it does not monitor user activity. It prevents the filter bubble of personalized search results and prioritizes your privacy.

The application provides practical functionalities such as safe search to safeguard against explicit content, region-specific searching, and an immediate answer function that presents an answer in a separate section of the screen above the search results.
Wrapping Up
Every corner, our online privacy is being invaded. Our online activities are lawfully monitored by advertisements, while hackers pilfer our personal data.
In the long term, the GDPR might be beneficial, but that remains to be seen. What currently transpires is what holds significance.
Today, these instruments will facilitate a more private and secure online experience for you.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE








