After Extorting $42 Million, the Akira Ransomware Gang Now Targeting Linux Servers
After Extorting $42 Million, the Akira Ransomware Gang Now Targeting Linux Servers
As of January 1, 2024, threat actors responsible for the Akira ransomware gang have illegally acquired an estimated $42 million in proceeds after infiltrating the networks of over 250 victims.
Akira ransomware has affected numerous businesses and critical infrastructure entities across North America, Europe, and Australia since March 2023, according to a joint alert issued by cybersecurity agencies from the Netherlands, the United States, and Europol’s European Cybercrime Centre (EC3).
“In April 2023, following an initial focus on Windows systems, Akira threat actors deployed a Linux variant targeting VMware ESXi virtual machines.”
Early on, the double-extortion group was observed utilizing a C++ variant of the locker; however, as of August 2023, they transitioned to a Rust-based codebase. It is noteworthy to mention that the e-criminal in question is entirely differentfrom the Akira ransomware family that operated during the year 2017.
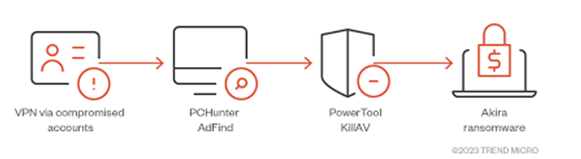
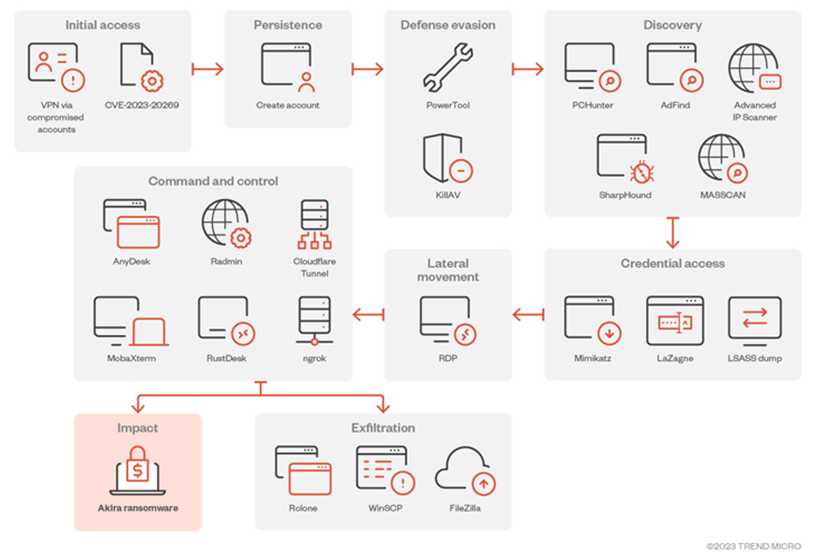
The initial infiltration of target networks is enabled through the exploitation of publicly recognized vulnerabilities in Cisco appliances, such as CVE-2020-3259 and CVE-2023-20269.
Vulnerabilities may also exploit virtual private network (VPN) services that do not implement multi-factor authentication (MFA) safeguards, employ legitimate credentials, or utilize Remote Desktop Protocol (RDP).

Akira actors are also recognized for employing a variety of methods to evade detection, including establishing persistence by creating a new domain account on the compromised system and utilizing a Bring Your Own Vulnerable Driver (BYOVD) attack against the ZemanaAntiMalware driver to terminate antivirus-related processes.

The adversary employs credential extraction tools such as Mimikatz and LaZagne to facilitate privilege escalation while traversing laterally within the victim’s network utilizing Windows RDP. The process of data exfiltration is carried out utilizing RClone, FileZilla, WinRAR, and WinSCP.
“Akira ransomware encrypts targeted systems using a hybrid encryption algorithm that combines Chacha20 and RSA,” described Trend Micro in an October 2023 publication of an analysis of the ransomware.

“Additionally, the Akira ransomware binary, like most modern ransomware binaries, has a feature that allows it to inhibit system recovery by deleting shadow copies from the affected system.”
In certain cases, the financially motivated group has also distributed two distinct ransomware variants (Akira_v2) targeting ESXiencryptors and Windows encryptors during the same compromise event.
Based on source code and blockchain information, it is probable that the Akira ransomware group has ties to the defunct Conti ransomware organization. Avast published a decryptor for Akira in July of last year; however, it is probable that the vulnerabilities have been rectified by now.
Akira’s transformation to focus on Linux enterprise settings is consistent with the strategies employed by other well-known ransomware families, including RTM Locker, LockBit, Cl0p, Royal, and Monti.
LockBit’s Difficulties to Reappear
Trend Micro previously disclosed that the extensive law enforcement operation that brought down the prolific LockBit gang in February had a substantial effect on the group’s ability to recover. As a result, the organization resorted to posting outdated and fabricated victims on its newly established data leak website.
“LockBit was one of the most productive and popular RaaS strains in operation, with possibly hundreds of affiliates, such as numerous connected with other prominent strains,” according to Chainalysis in February.

Blockchain analytics firm: Colonel Cassad, a journalist based in Sevastopol who has a proven track record of seeking payments for Russian militia group operations in the authorized jurisdictions of Donetsk and Luhansk since the outbreak of the Russo-Ukrainian war in 2022, was linked to a LockBit administrator via cryptocurrency trails, according to the firm.

Colonel Cassad (aka Boris Rozhin) was associated with an anti-Ukraine misinformation campaign organized by the Russian state-sponsored group APT28, according to Cisco Talos in January 2022.
“After the operation, LockBitSupp [the purported leader of LockBit] appear to be seeking to inflate the alleged victim count while additionally concentrating on publishing victims from nations whose law enforcement organizations engaged in the change,” Trend Micro reported in a recent in-depth investigation.
“This is potentially a strategy to strengthen the narrative that it would return more powerfully and target those accountable for its disturbance.”
LockBitSuppacknowledged the temporary decrease in profits during an interview with Recorded Future News last month. However, the company pledged to enhance its security protocols and “work as long as my heart beats.”

“Losing reputation and trust is detrimental to the ability to attract affiliates, as it hinders the ability to convince individuals to return. Operation Cronos effectively targeted the most vital component of its enterprise: its brand,” Trend Micro reported.
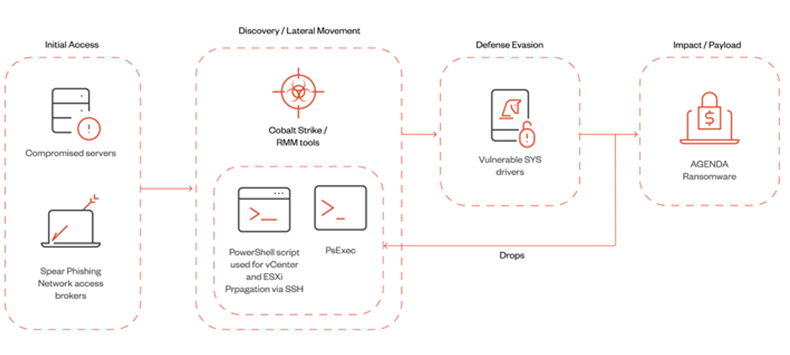
Agenda Resurfaces Featuring a Revised Rust Version
Additionally, this development coincides with the Agenda ransomware group’s (also known as Qilin and Water Galura) utilization of a modified Rust variant to infiltrate VMWare vCenter and ESXi servers via Cobalt Strike and Remote Monitoring and Management (RMM) tools.
“The Agenda ransomware’s capacity to propagate to virtual machine infrastructure indicates that its operators are additionally branching out to new targets and systems,” the cybersecurity organization reported.
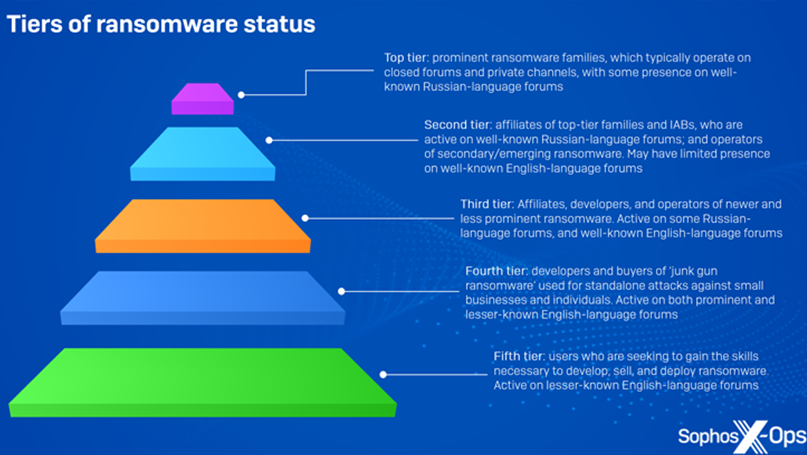
While the threat landscape remains energized by a new wave of ransomware actors, it is also becoming more evident that “crude, cheap ransomware” available on the cybercrime underground is being utilized in actual attacks. This enables lower-tier individual threat actors to generate substantial profits without the need to be affiliated with a well-organized group.
It is noteworthy that a significant portion of these variants can be obtained for an individual, one-time fee commencing at $20 for a solitary installation. Conversely, a limited number of them, including HardShield and RansomTuga, are provided complimentary of charge.
“Junk-gun ransomware enables criminals to participate in the activity inexpensively, easily, and independently, away from the intricate structure of modern ransomware,” Sophos said, characterizing it as a “relatively new phenomenon” that further reduces the barrier to entry.
“They are able to target small companies and people, who are doubtful to have the means to adequately defend themselves or react successfully to events, without giving anyone else a cut.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE






