All You Require To Understand About Wireshark

All You Require To Understand About Wireshark
What is Wireshark?
The industry standard for network protocol analysis software is commonly regarded as Wireshark, an open-source tool. Wireshark is maintained and updated for new network technology and encryption techniques by a global community of network experts and software developers.
Wireshark is used for troubleshooting and teaching in government agencies, enterprises, non-profits, and educational organizations. There isn’t a more effective method for learning low-level networking than using Wireshark to examine traffic.
Wireshark should only be used on networks where packet inspection is permitted. It is forbidden to examine packets with Wireshark without authorization
How is Wireshark operated?
A packet sniffer and analysis tool is called Wireshark. It records network traffic from many connections, including frame relay, Bluetooth, Ethernet, and wireless (IEEE.802.11), and saves the information for further study.
Editor’s Note: A single communication from any network protocol (such as TCP, DNS, etc is referred to as a “packet.”
Editor’s Note 2: Because LAN traffic is carried out in broadcast mode, any machine running Wireshark can view communications between any two other computers. You must capture the packets on the local computer in order to view traffic going to an external website.
With Wireshark, you may refine and focus on certain elements of the network trace by filtering the log either before the capture begins or while the analysis is ongoing. For instance, you can be configured to exclusively display packets sent from a single machine, or you can establish a filter to view TCP traffic between two IP addresses. One of the main reasons Wireshark has become the go-to tool for packet analysis is because of its filters.
When should Wireshark be used?
With the use of Wireshark, one may decipher network communication patterns and determine the root cause of communication problems.
Wireshark is used for?
- Network administrators diagnose issues on a network.
- Security engineers investigate network security concerns.
- QA specialists check apps.
- Programmers troubleshoot protocol implementations.
- Users of a network are taught about a certain protocol.
When is Wireshark not appropriate to use?
In addition to being a useful teaching tool, Wireshark may assist in debugging a variety of network problems. But Wireshark is unable to:
Assist a person who is unsure about network protocols: To utilize Wireshark, users need to have a basic understanding of network operations.
Seize traffic originating from places other than your local computer and the system it communicates with: It is not possible for Wireshark to capture network traffic from every other system.
Alert you about dangers: The closest thing Wireshark can do is display faulty packets and use color coding.
Wireshark for Linux
Installing Wireshark on Linux can be a little different depending on the Linux distribution. If you aren’t running one of the following distros, please double-check the commands.
From a Terminal prompt, run these commands:
sudo apt-get install wireshark
sudo dpkg-reconfigure wireshark-common
sudo adduser $USER wireshark
Kali Linux
Wireshark is probably already installed because it’s part of the basic package. Check your menu under the option “Sniffing & Spoofing” to verify.
Data packets on Wireshark
Now that we have Wireshark installed, let’s go over how to enable the Wireshark packet sniffer and then analyze the network traffic.
Capturing data packets on Wireshark
When you open Wireshark, you see a screen showing you a list of all the network connections you can monitor. You also have a capture filter field to only capture the network traffic you want to see.
You can select one or more of the network interfaces using shift+left-click. Once select the network interface, you can start the capture, and there are several ways to do that.
Click the first button on the toolbar, titled “Start capturing packets.”

You can select the menu item Capture -> Start.
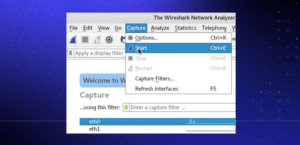
Or you could use the keystroke Control+E.
During the capture, Wireshark will show you the packets captured in real time.
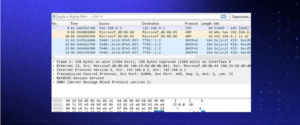
After you have all the necessary packets collected, end the capture using the same menu items or buttons that you used to start it.
It is best practice to halt Wireshark’s packet capture before doing any analysis. Wireshark data packet analysis.
Three separate panels are displayed by Wireshark when you examine packet data. All of the packets in the capture are listed in the top window, called Packet List. The other two panes adjust to display the details of the selected packet when you click on it. Additionally, you can determine if the packet is a part of a dialogue. The following information explains each column in the top pane:
No.: The packet that was collected has this number order. This packet is part of a discussion, as shown by the bracket.
Moment: The length of time this specific packet was collected after you began the capture is indicated in this column. Altering this value will cause a different option to appear in the Settings menu.
Source: This is the address of the packet’s sending system.
Destination: This is the packet’s destination address.
Protocol: This kind of packet is what it is. TCP, DNS, DHCPv6, or ARP are a few examples.
Length: The length of the packet, expressed in bytes, is displayed in this column.
Details: The information displayed in this column relates to the contents of the packet and varies based on its kind.
Depending on the kind of packet, the center pane, Packet Details, displays as much intelligible information as it can. The highlighted text in this area can be used to construct filters with a right-click.
The packet is shown in hexadecimal in the Packet Bytes pane at the bottom, just as it was recorded.
You may choose to see only the packets included in a discussion by right-clicking on the packet while viewing it and choosing Follow.
Filters for Wireshark
The capture and display filters in Wireshark are among its greatest features. Using filters, you may see the capture in the exact way you need to in order to diagnose and resolve the current problem. Here are a few filters to get you going.
Wireshark capture filters
Capture filters limit the captured packets by the chosen filter. If the packets don’t match the filter, Wireshark won’t save them. Examples of capture filters include:
host IP-address: This filter limits the captured traffic to and from the IP address.
net 192.168.0.0/24: This filter captures all traffic on the subnet.
dst host IP-address: Capture packets sent to the specified host.
port 53: Capture traffic on port 53 only.
port not 53 and not arp: Capture all traffic except DNS and ARP traffic.
Wireshark display filters
Wireshark display filters change the view of the capture during analysis. After you’ve stopped the packet capture, use display filters to narrow down the packets in the Packet List to troubleshoot your issue.
One of the most useful display filters is:
ip.src==IP-address and ip.dst==IP-address
This filter shows packets sent from one computer (ip.src) to another (ip.dst). You can also use ip.addr to show packets to and from that IP. Other filters include:
tcp.port eq 25: This filter will show you all traffic on port 25, which is usually SMTP traffic
icmp: This filter will show you only ICMP traffic in the capture, most likely they are pings
ip.addr! = IP_address: This filter shows you all traffic except the traffic to or from the specified computer
Analysts even build filters to detect specific attacks, like this filter used to detect the Sasser worm:
ls_ads.opnum==0x09
Additional Wireshark features
Beyond the capture and flattering, several other features in Wireshark can make your job easier.
Wireshark colorization options
You can configure Wireshark to color your packets in the Packet List according to the display filter, which allows you to emphasize the packets you want to highlight. Check out some examples here.
Wireshark promiscuous mode
By default, Wireshark only captures packets going to and from the computer where it runs. By checking the box to run Wireshark in promiscuous mode in the capture settings, you can capture most of the traffic on the LAN.
Wireshark command line
Wireshark does provide a command line interface (CLI) if you operate a system without a graphical user interface (GUI). The best practice would be to use the CLI to capture and save a log so you can review the log with the GUI.
Wireshark commands
Wireshark: run Wireshark in GUI mode
Wireshark –h: show available command line parameters for Wireshark
Wireshark –a duration:300 –i eth1 –w Wireshark. : capture traffic on the ethernet interface once for five minutes. –a means to automatically stop the capture, -i specifies which interface to capture
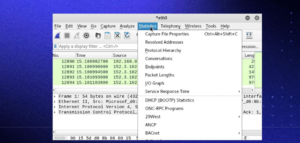
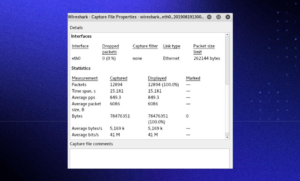
Metrics and statistics
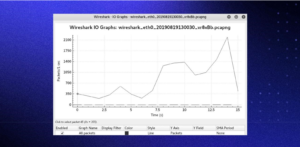
Under the Statistics menu, you’ll find a plethora of options to view details about your capture.
Capture File Properties:
Wireshark I/O Graph:
How News4Hackers Can Help?
News4Hackers is an international news agency that is committed to delivering intriguing and practical articles about cybersecurity-related subjects. In addition, News4Hackers adheres to providing its readers with up-to-date information concerning the most recent developments, approaches, technologies, and cyber threats that have the intention of compromising organizations worldwide. To guarantee that you are expeditiously updated on the most recent technological developments, our news organizers diligently oversee the market daily.
Furthermore, it is imperative to underscore that Craw Security maintains a partnership with News4Hackers, a well-regarded organization that specializes in cybersecurity, in order to provide insightful analysis and perspectives on numerous significant nations, including India. To obtain further details about their exceptionally successful cybersecurity education programs or any other relevant subject, please do not hesitate to contact them at the phone number +91-9513805401.
READ MORE ARTICLE HERE









