Belkasoft CTF4 (Kidnapping Case)
In this article, we’ll look at how to solve the CTF (Capture The Flag) of a Kidnapping Case that happened somewhere of a school-going boy who got kidnapped while having a threatening tip that he was about to be kidnapped, and guess what! He got kidnapped afterward!
For this, participants were given 24 hrs to solve all the questions and they were also provided trials of Belkasoft Evidence Center X and Passware, but you can use any forensic tool, which you are comfortable using because you must have to maintain the integrity of the evidence. However, if you will use any new forensic tool which you are not comfortable to use then, you may alter the evidence integrity. The image was a Linux machine, and the CTF is not straight to gather all the evidence so, you have to dig deep inside to solve it. So, now let’s start ahead.

Belkasoft CTF4: (Kidnapping Case)
In this article, we’ll look at how to solve the CTF (Capture The Flag) of a Kidnapping Case that happened somewhere of a school-going boy who got kidnapped while having a threatening tip that he was about to be kidnapped, and guess what! He got kidnapped afterward!
For this, participants were given 24 hrs to solve all the questions and they were also provided trials of Belkasoft Evidence Center X and Passware, but you can use any forensic tool, which you are comfortable using because you must have to maintain the integrity of the evidence. However, if you will use any new forensic tool which you are not comfortable to use then, you may alter the evidence integrity. The image was a Linux machine, and the CTF is not straight to gather all the evidence so, you have to dig deep inside to solve it. So, now let’s start ahead.
1. Users (Baby – 100 pts)
Question – List all users of the laptop.
Sol. This task is a little tricky, as Some of the participants thought that there are 3 users in the. But, keep in mind that flag format relates to the format only, not to the number of answers.
- Load the image file to the forensic tool.
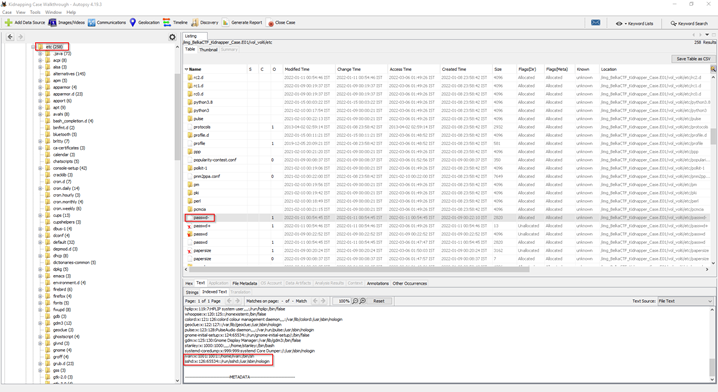
- Now navigate to the file’s directory /etc/passwd or you can also find the users in /home directory.
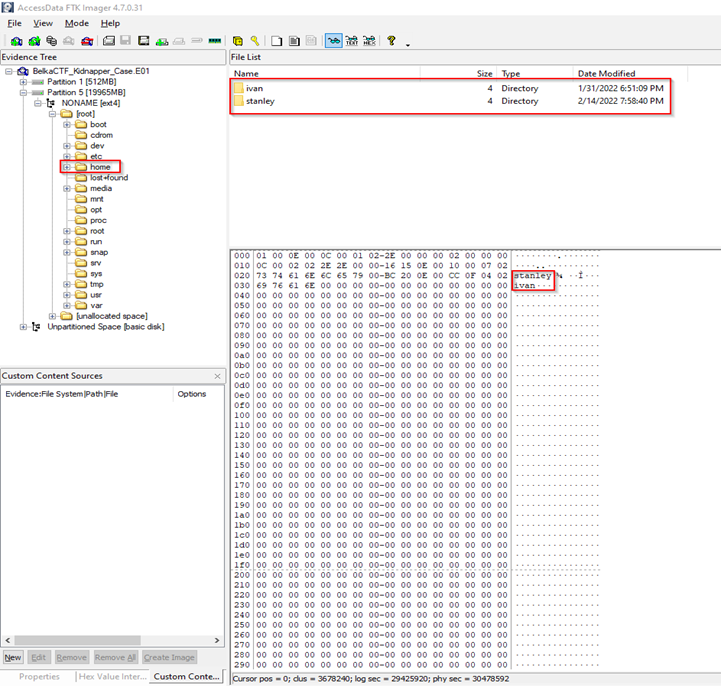
- Now you will see the list of users in that image.
Flag: ivan, stanley
2. Special Website (Baby – 100 pts)
Question – What web application was used by the boy to earn his pocket money?
Sol. To find the application the boy used to earn money; you have to list the browsing history of the Linux machine.
- Firstly, you have to load the image in any Forensic tool of your choice.
- Now navigate to the Web History option of your Forensic Tool.
- You will also see the web history database source location in (\home\ivan\.mozilla\firefox\yyxsdegu.default-release\places.sqlite) directory.
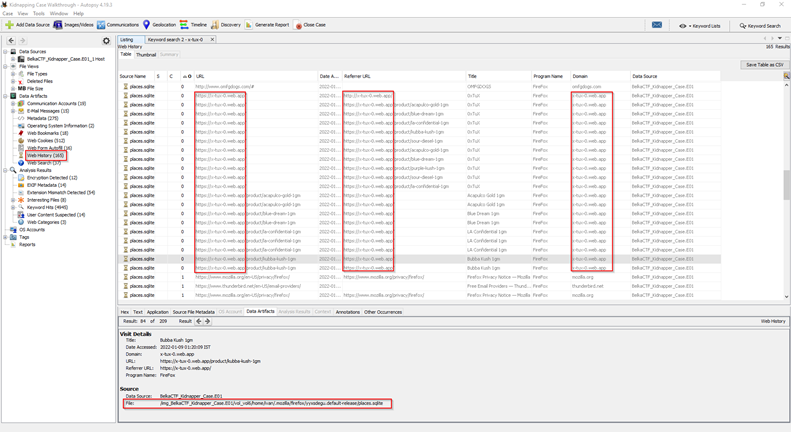
- Now you will see that the boy was using https://x-tux-0.web.app to earn his pocket money.
Flag: https://x-tux-0.web.app
3. Wallet (Baby – 100pts)
Question – Which BTC wallet did the boy use to sell drugs?
Sol. In the above question we have identified the website, the boy used to sell drugs.
- Now let’s try to open that same link (https://x-tux-0.web.app) which the boy used to sell drugs.
- You will notice that the website the boy used to sell drugs is still alive.
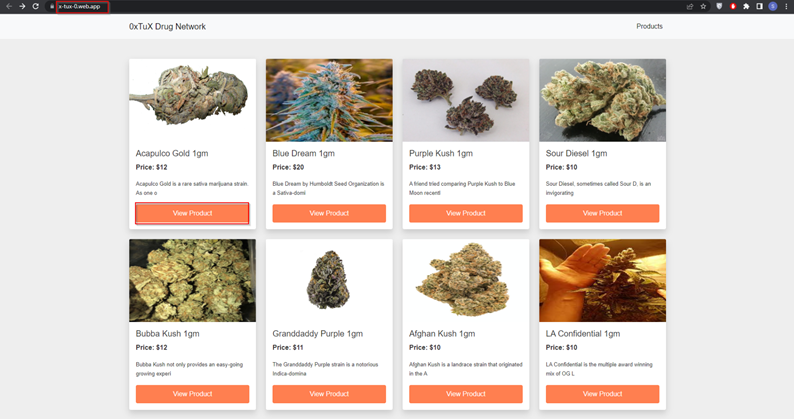
- Now click on any product, then you will get the bitcoin address the boy used to sell drugs.

Flag: 1KFHE7w8BhaENAswwryaoccDb6qcT6DbYY
4. Passme (Moderate–500pts)
Question – On which date does the kid’s database show the most sales for “Acapulco Gold”? (Format: YYYY-MM-DD)
Sol:
- First, open Email chats for gathering information, and will seek some important artifacts.
- You will find a conversation between the boy and the customer with the monthly sell database. Now export that Monthly-DB file. But unexpectedly it was encrypted with a password.
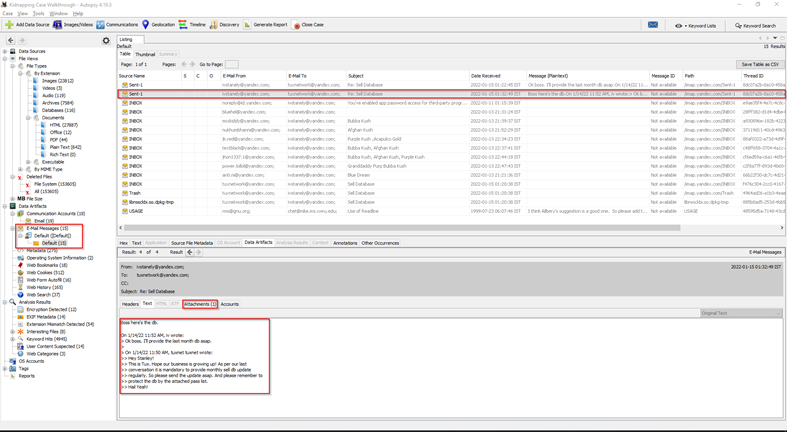
- Now as per the conversation, we now have to find the wordlist which he used to encrypt the Monthly-DB file.
- Now open the text files present in that system by simply using filters by extensions and sort them by size. You will find some wordlists, now export all that wordlist to proceed further in cracking.
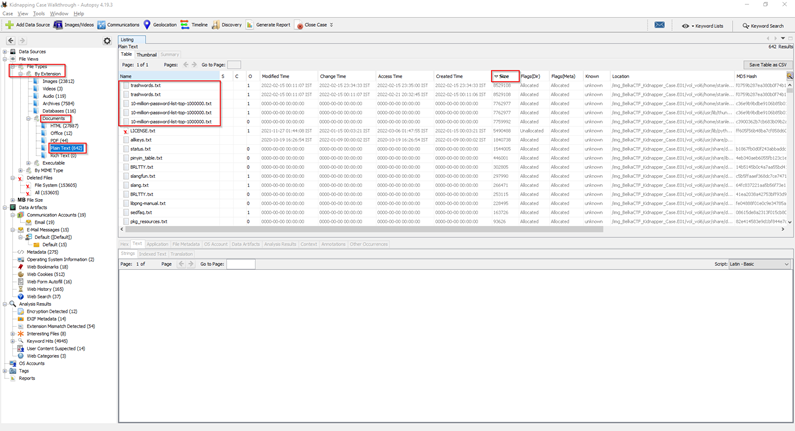
- You can use any cracking tool for cracking the file.
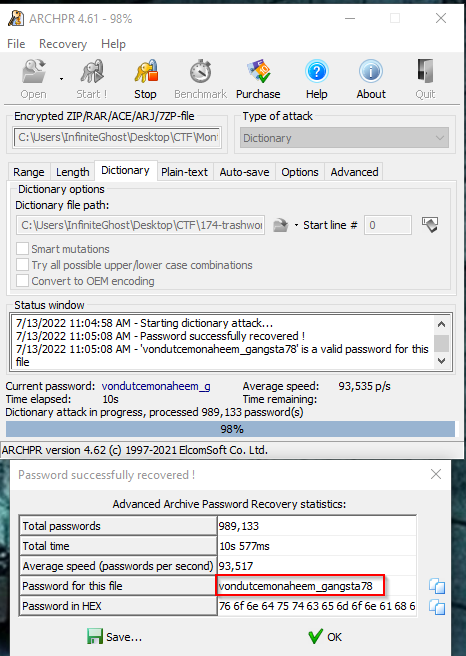
As you see the password is cracked with trashwords.txt, now open the zip file and analyze the database file. - After extracting the database, you will get 2 years of (2020, 2021) database files, now next analyze all the files to find the most sales of “Acapulco Gold”. After analyzing all the files, you will find most sales of “Acapulco Gold” on Date-5-2021.
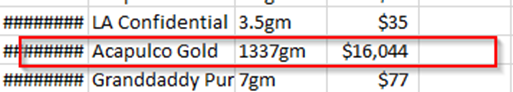
Flag: 5-2021
5. Cryptlet (Tricky—750pts)
Question- What was the other BTC wallet of the victim, which he used to hide his “under the counter” sales from his superior?
Sol:
- In the Forensic tool of your choice, simply open some the image file and navigate to (/img_BelkaCTF_Kidnapper_Case.E01/vol_vol6/home/ivan/Documents/.custom/).
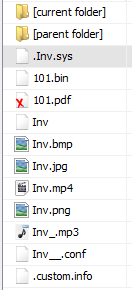
- You will see some files with mismatch extensions files, and you will find 2 files suspicious, one is only missing the first 4 bytes of the file signature, and another also has the first 4 bytes missing and the endianness is swapped for every 2 bytes. So, you first need to convert the hex value, in 2-word length, from little endian to big endian, and then add the 4 missing file signature bytes.
- Now after converting the 101.bin file from little endian to big endian, compare that file with the .inv.sys file, if it matches then add the file signature to its starting and save that file.
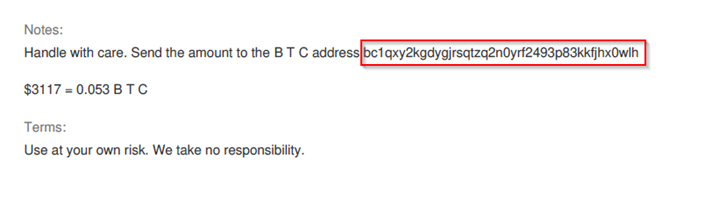
Flag: b1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh
6. Notipass (Tricky – 750pts)
Question – What is the password to the boy’s notes?
Sol: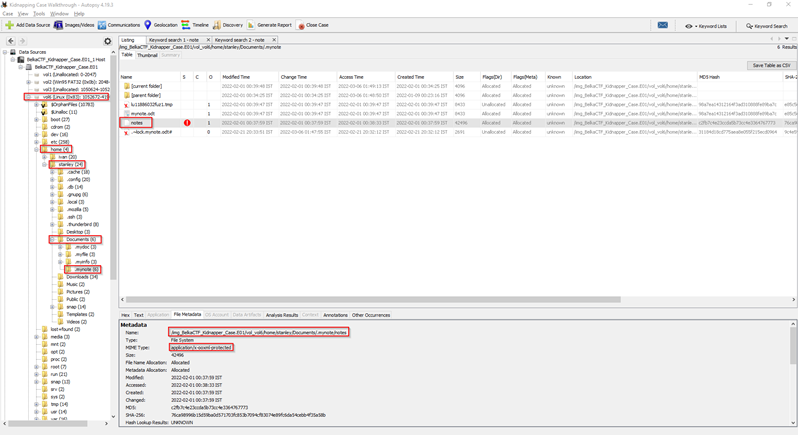
- In the forensic Workstation of your choice, simply search for a note in the keyword search box. You will find a document named notes, now move to that file directory /img_BelkaCTF_Kidnapper_Case.E01/vol_vol6/home/stanley/Documents/.mynote/, and export it to your local workstation and add document file extension (.docx or .odt) to it, but unfortunately you will see that the file is encrypted with a password.
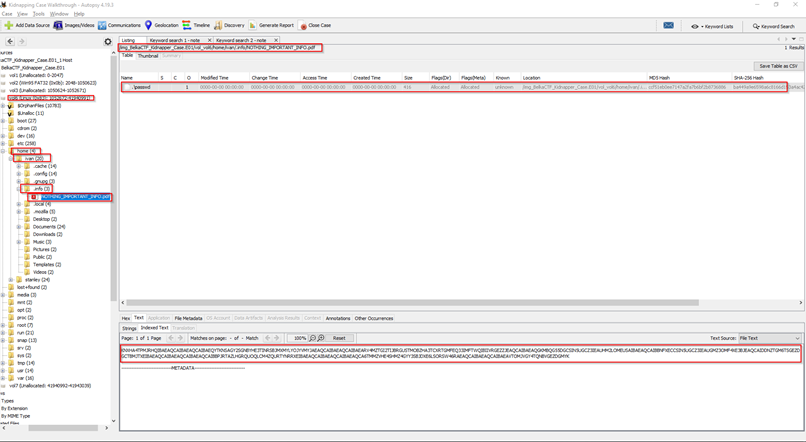
- Now we have to look for some more directories for finding the password of that doc. File. This will take some time to find out the right file that’s why you have to maintain patience when you are investigating any case. After searching all the directories, I came to the point where I found a suspicious document file named NOTHING_IMPORTANT_INFO.pdf, here after opening this file you will see a string of some random character, but don’t ignore it, because ignoring any suspicious or unreadable character could render your case, as it is the hash encoded with BASE32 and ROT13. You can use the https://gchq.github.io/CyberChef site to decode that sting.
- After decoding, use that password to open that suspicious notes file.
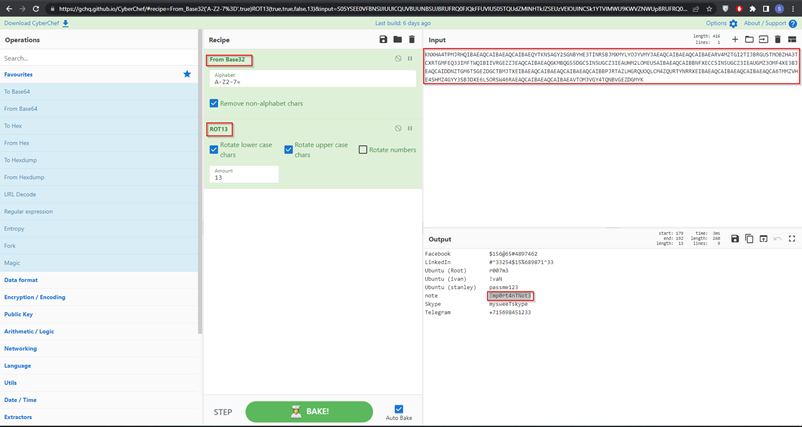
FLAG: !mp0rt4nTNot3
7. Specudio (Hard – 1000pts)
Question — What is the “secret pin” mentioned in the notes?
Sol: The task name Specudio gives some hints like the flag is related to any audio file.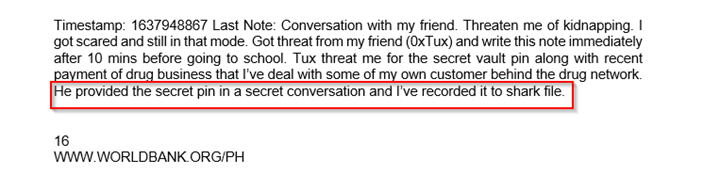
- Firstly, open that notes file that you have decrypted before, and start analyzing it, you will note some indicators at the last of the document, that it is recorded in shark (which could only be a Wireshark file).
- So now we have to find the PCAP/PCAPNG file in the image, so start searching for that pcap/pcapng file. You will find that file in /img_BelkaCTF_Kidnapper_Case.E01/vol_vol6/home/ivan/Music/.secs/.secret.pcapng directory.
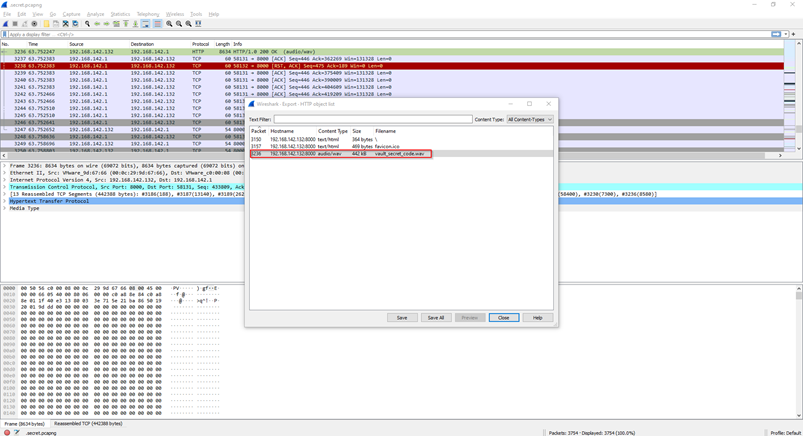
Now dump that file and open it using Wireshark, then apply a filter to only extract objects of the HTTP protocol. Navigate to the File option in the top left corner in Wireshark and click on Export Objects => HTTP. 4. After dumping that vault_secret_code.wav file you can do spectral analysis of the file on https://www.dcode.fr/spectral-analysis website. After uploading the audio file, you will get the secret PIN.
4. After dumping that vault_secret_code.wav file you can do spectral analysis of the file on https://www.dcode.fr/spectral-analysis website. After uploading the audio file, you will get the secret PIN.
Flag: {1257}
8. Ultimatum (Baby – 100pts)
Question- When did the boy receive a threat? (Format: Epoch Time)
Sol: In the notes, the victim says that he got threatened 10 minutes before, he went to school and made this entry.
- Open that note file, and move to the last conversation where u will get the Epoch Timestamp of the last conversation, But read the conversation carefully that this conversation is immediately 10 minutes after he was threatened.
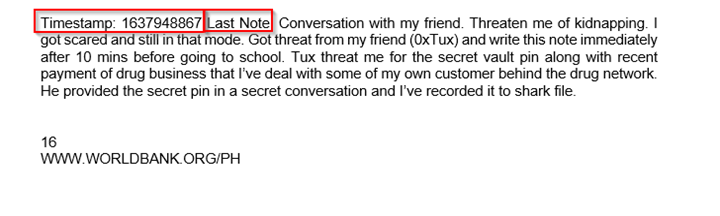
- Now subtract 600 seconds from the currently given timestamp. Because 1min = 60 sec.
So, 10 min = 60 * 10= 600sec. So, after subtracting we will get 1637948267, which is your flag.
Flag: 1637948267
9. Whois (Warmup – 200pts)
Question – Who was the kidnapper? (Format: Nickname, email)
Sol:
- From the note, we know who the kidnapper is (0xTux), but now we need the email address.
- After searching for the file you will find the mycon.zip file in home/ivan/.local (hidden directory).
- But this file is also password protected so you have to crack it using any archive cracking software.
- After cracking you will get the password 1257, which you have found in question 7.
- You will find the email address of the kidnapper after decrypting the file. {[email protected]}
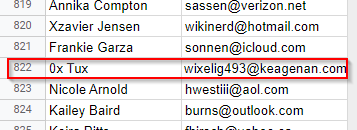
Flag: 0x Tux, [email protected]
10. Pride (Final—250pts) BONUS POINT
You can also be proud of yourself to have solved the complex kidnapper CTF. Now go and share the news on Twitter or LinkedIn!
This is only the Bonus task that will allow you to get 250 pts for a social post on your success with BelkaCTF. There was no standard flag; every URL was manually checked to avoid cheating.









Every weekend i used to pay a quick visit this
website, because i want enjoyment, for the reason that this
web page conations truly nice funny stuff too.