CERT-In Might Be Compromised by a Group of Pakistani Hackers; Claims made in a Telegram Chat
CERT-In Might Be Compromised by a Group of Pakistani Hackers; Claims made in a Telegram Chat
There is a chance that the Indian Computer Emergency Response Team (CERT-In) is compromised at the hands of Pakistani malicious hackers. Read the full story now…

Recent reports indicate that an anonymous threat actor from Pakistan may have compromised the official Computer Emergency Response Team (CERT-In) of India. The subject asserts that they have obtained illicit entry to CERT-In’s network and now have complete authority over the organization’s email database and internal network. The threat actor has offered to sell data and network-level access in a private Telegram conversation where he or she has made these claims.
Assisting in the handling of cyber incidents in India, CERT-In has established programs to disclose vulnerabilities. Utilizing this vulnerability, the threat actor claims to possess authorization to the internal email server, which is inaccessible to the general public. The server is home to exceedingly sensitive data pertaining to unpatched and undisclosed vulnerabilities. In exchange for authorization to access the email server and network infrastructure of CERT-In, the threat actor demands a significant ransom of $10,000.

Also Read : A Report Shows Amazon Used A Shell Company to Acquire Intels on Rivals like Walmart and Flipkart
Although verification of these claims is still pending, the threat actor has provided a substantial quantity of evidence to substantiate their claims. Internal documents, email exchanges, proof-of-concept videos showcasing unpatched vulnerabilities, and additional materials comprise this evidence. A portion of this evidence has been made available for additional evaluation and verification.

Following additional inquiry, a number of intriguing discoveries have surfaced. A thread of emails indicates that Pakistani APT36 may have obtained access to a computer at the headquarters of the Indian Air Force. Moreover, APT36 had previously gained entry to the Delhi Police network prior to its recent compromise via a ransomware attack. Indicators of Chinese APT groups conducting specific attacks on critical infrastructure are also present, along with copies of First Information Reports (FIRs) lodged against breaches executed by unidentified threat actors.

This incident casts doubt on the cybersecurity capabilities of the Indian government, as its own CERT has been compromised by hackers, the very adversaries it was created to defend against the common Indian public and organizations from the harmful effects of worldwide malicious threat actors.
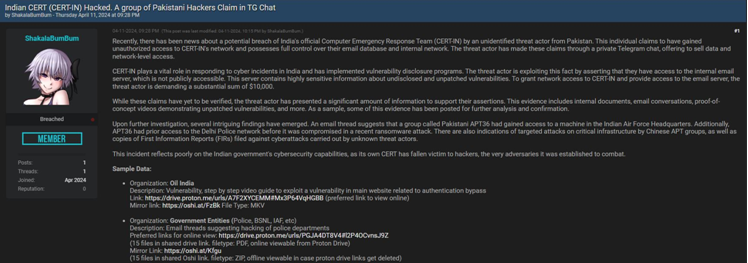
Moreover, the adversaries even provided the sample data for the following hacking scenarios:
| Organization | Oil India |
| Description | Vulnerability, step-by-step video guide to exploiting a vulnerability in the main website related to authentication bypass. |
| Link | https://drive.proton.me/urls/A7F2XYCEMM#Mx3P64VqHGBB (preferred link to view online) |
| Mirror link | https://oshi.at/FzBk File Type: MKV |
You may even check one more instance with the same hacking scenario:

| Organization | Government Entities (Police, BSNL, IAF, etc.) |
| Description | Email threads suggesting hacking of police departments. |
| Link | https://drive.proton.me/urls/PGJA4DT8V4#l2P4OCvnsJ9Z
(15 files in shared drive link. filetype: PDF, online viewable from Proton Drive) |
| Mirror link | https://oshi.at/Kfgu (15 files in shared Oshi link. filetype: ZIP, offline viewable in case proton drive links get deleted) |
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Also Read : How Attackers Can Own a Business Without Touching the Endpoint?





