Critical Bug Leads to Almost 2,000 Citrix NetScaler Instances Being Hacked
By using a previously reported serious security flaw as a weapon in a massive assault, which led to almost 2,000 Citrix NetScaler instances having been infected with a backdoor.
In a Tuesday advisory, NCC Group stated that “an attacker believed to have exploited CVE-2023-3519 in an automated manner, installing web shells on vulnerable NetScalers in order to obtain persistent access.”
Even after a NetScaler has been patched and/or restarted, the adversary is still able to run whatever command they want via this web shell.
A serious code injection flaw that affects NetScaler ADC and Gateway servers and could result in the unofficial execution of code remotely is known as CVE-2023-3519. Last month, Citrix patched it.
The news came a week after the Shadowserver Foundation reported that it had found over 7,000 online instances of NetScaler ADC and Gateway that were susceptible and unpatched and that the bug was being used to remotely access servers by dropping PHP web shells.
1,828 NetScaler servers are still backdoored, according to a subsequent analysis by NCC Group, of which 1,248 have previously been patched.
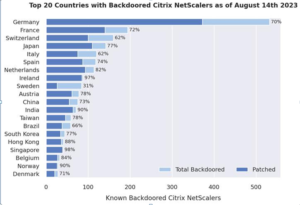
This shows that even though the majority of administrators were conscious of the flaw and have since updated their NetScalers to a secure version, they had not (properly) examined for indicators of successful exploitation, according to the business.
2,491 web shells in all have been discovered among 1,952 different NetScaler appliances. Germany, France, Switzerland, Japan, Italy, Spain, the Netherlands, Ireland, Sweden, and Austria are home to the majority of the affected instances.
Aside from the European focus, it is noteworthy that no web shells were discovered on any of the thousands of NetScaler servers that were reported to be susceptible late last month in Canada, Russia, and the United States.
According to estimates, 6.3% of the 31,127 NetScaler instances that were vulnerable to CVE-2023-3519 as of July 21, 2023, were penetrated by the mass exploitation campaign.
The revelation comes at the same time as Mandiant has made an open-source tool available to assist enterprises in checking their Citrix devices for signs of CVE-2023-3519 post-exploitation activity.
About The Author:
Yogesh Naager is a content marketer that specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Read More Article Here





