New Ransomware Found: Blackmatter Ransomware 2021

NEW RANSOMWARE FOUND: BLACKMATTER RANSOMWARE
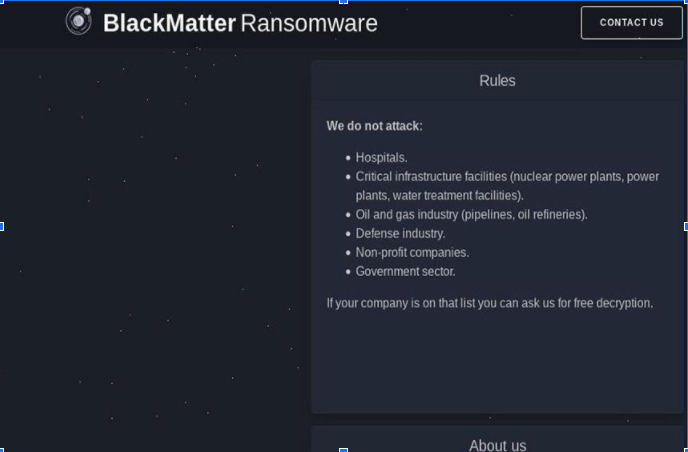
Threat intelligence companies say that earlier this month, a pre unknown user with the handle “BlackMatter” declared the launch of BlackMatter Ransomware via 2 massive, Russian-language forums, spoken communication it offered a “greatest hits” against a number of ransomware operations in history.
“The project has incorporated in itself the best features of DarkSide, REvil, and LockBit,” BlackMatter asserted in July 19 posts, says danger intelligence firm Recorded Future.
The decision of the name for the ransomware bunch reviews REvil. “REvil recently named their Windows Registry key ‘BlackLivesMatter,'” says danger intelligence firm Flashpoint.
That key name was available in the adaptation of REvil utilized in the attack against the software firm Kaseya, says Kevin Beaumont, head of the security tasks community for London-based style retail Arcadia Group.
REvil Banded Or Disbanded?
The development of BlackMatter follows REvil evidently closing down after the July 2 attack it released through Kaseya’s far off administration programming, contaminating around 60 of its oversaw specialist co-op clients and up to 1,500 of their customers’ systems. On Thursday, Kaseya said it had obtained the capacity to decode each target’s records and was assisting them with doing so, and on Monday it gave an explanation that it had not paid a payoff to REvil for a decryptor.
On July 13, REvil obviously shut down its information spill site and installment entry. “Around the same time, XSS prohibited REvil’s representative UNKN” – otherwise known as Unknown – Flashpoint says, referring to the XSS darknet criminal gathering.
Regardless of whether REvil has closed down tasks and possibly chose to rebrand and start again under an alternate name – or might do as such – stays unclear.
REvil Code Used By The Attackers
No less than one association has succumbed to another attack including REvil’s code, says Fabian Wosar, CTO at Emsisoft. “REvil is back … basically kind of. We have seen a target that was plainly hit by a fixed REvil variation. The attacker probably fixed a current REvil payload to leave out the key mass that is generally encoded, with the operator mass nulling it out,” Wosar says by means of Twitter.
Wosar says whoever is employing REvil might be at least one previous offshoot of at least one ransomware-as-a-administration activity. In such tasks, executives create crypto-locking malware, which offshoots access as a cloud-based help, through an interface. Associates utilize the code to contaminate associations, and at whatever point a target pays a payment. The partner and the activity’s executives share in the profits.
In any case, as far as REvil, Wosar says the attacker is possibly not “OG” – slang for unique criminal, referring for this situation to being a center individual from the first group. “We don’t accept this to be crafted by the OG REvil administrators or somebody who approached the REvil source code,” he says. “It is almost certain we are managing a previous member here who would not like to acknowledge that his most loved ransomware operator went dull.”





