Spear-Phishing Attacks by Cloud Atlas Target Russian Agricultural and Scientific Firms

Spear-Phishing Attacks by Cloud Atlas Target Russian Agricultural and Scientific Firms
The entity known as Cloud Atlas has been associated with a series of targeted phishing assaults against Russian businesses.

The targets encompassed a Russian agro-industrial organization and a state-owned research company, as stated in a report by F.A.C.C.T., an independent cybersecurity firm established subsequent to Group-IB’s official departure from Russia earlier this year.
Cloud Atlas is an enigmatic cyber espionage group that has been operational since at least 2014. The threat actor, known by multiple names including Clean Ursa, Inception, Oxygen, and Red October, is notorious for its consistent and ongoing efforts aimed at Russia, Belarus, Azerbaijan, Turkey, and Slovenia.
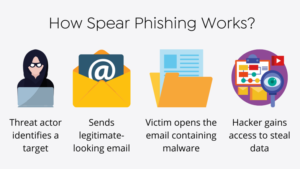
In December 2022, Check Point and Positive Technologies provided a comprehensive account of multi-stage assault sequences that resulted in the implementation of a backdoor called PowerShower, which is based on PowerShell. Additionally, the attack involved the use of DLL payloads that may establish communication with a server controlled by the perpetrator.
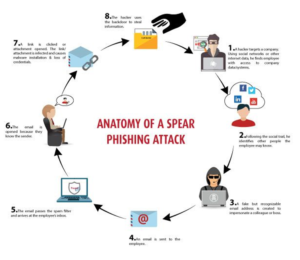
The initial step involves receiving a phishing message containing a deceptive document that takes use of CVE-2017-11882, a memory corruption vulnerability in Microsoft Office’s Equation Editor that has been known for six years. This vulnerability is used by Cloud Atlas to initiate the execution of harmful payloads, a strategy they have been using since October 2018.
“According to Kaspersky’s report in August 2019, the actor persistently employs extensive spear-phishing campaigns that rely on straightforward yet efficient techniques to successfully infiltrate their targets.” “In contrast to numerous other intrusion sets, Cloud Atlas has deliberately refrained from utilizing open source implants in its recent campaigns, with the intention of being less selective.”

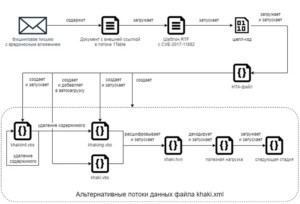
The current death chain, as detailed by F.A.C.C.T., closely resembles the one outlined by Positive Technologies. It involves the successful exploitation of CVE-2017-11882 through RTF template injection. This vulnerability allows for the execution of shellcode, which is responsible for downloading and executing an obfuscated HTA file. The emails are sent using well-known Russian email providers, Yandex Mail and VK’s Mail.ru.
The malevolent HTML application subsequently initiates the execution of Visual Basic Script (VBS) files, which are eventually accountable for retrieving and executing an unidentified VBS code from a remote server.

“The Cloud Atlas group has demonstrated long-standing activity, meticulously strategizing every facet of their offensive maneuvers,” Positive Technologies stated of the group’s operations in the previous year.
“The group has maintained the same toolkit for an extended period of time. They attempt to conceal their malicious software from researchers by employing unique payload requests and verifying their authenticity.” The organization evades detection from network and file attack detection systems by utilizing authentic cloud storage and extensively documented program features, including within Microsoft Office.

The business has reported that a minimum of 20 enterprises based in Russia have been infiltrated using Decoy Dog, a customized variant of Pupy RAT. The company has attributed these attacks to an advanced persistent threat actor named Hellhounds.
The currently updated malicious software, in addition to enabling the adversary to control the infected host from a distant location, includes a scriptlet specifically created to send telemetry data to an “automated” account named “LamirHasabat” (@lahat) on the Mindly.Social instance of Mastodon.
“Following the publication of materials regarding the initial iteration of Decoy Dog, the creators of the malware exerted significant effort to impede its identification and examination, both in network traffic and within the file system,” stated security experts Stanislav Pyzhov and AleksandrGrigorian.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE






