AXLocker Ransomware Encrypted Files and Accessing your Discord Accounts. Be Aware!
DISCORD, one of the most popular social media platforms, became the victim of a ransomware group’s attack. Not only did the victim’s data become encrypted, but their accounts were also hijacked. The main culprit in this cyberwar is “AXLocker.”
Logging in to Discord needs credentials data. After that, App sends a User Authentication Token that gets saved on the device. Token helps in login imitating as a user. Or, you can take it as it is used to generate API requests that get data about the registered account.
Adversaries are trying to steal these tokens, allowing them to access accounts elsewhere, using accounts for their malicious intent. Discord has become popular among NFT Platforms and Cryptocurrency Groups. Therefore, a moderator token would allow adversaries to run Scams and steal funds.
AxLocker is a two-in-one threat.
Cyble, Researchers
They have analyzed a sample of the latest Ransomware tool, “AXLocker,” and they found out that the ransomware tool not only encrypts files but also steals the Discord Token of the Victim. As usual ransomware, nothing was fascinating or complex about this malware or the adversary who runs it.
Process of Encryption and Further
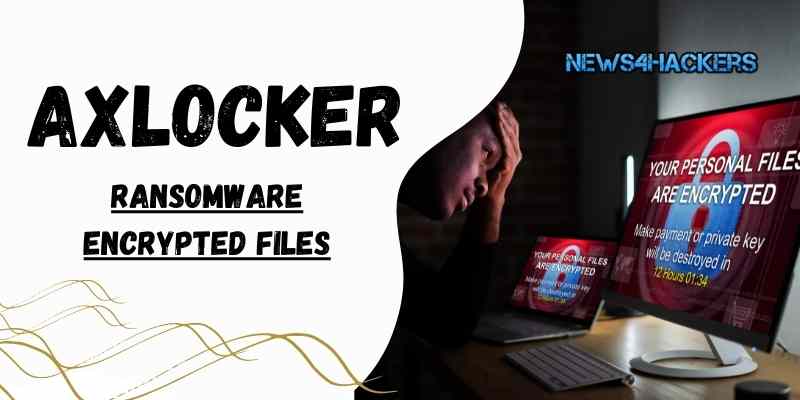
- As you can see in the figure below, running this malicious program will target specific file extensions and folders to exclude them from the loaded data.
- In the process of file encryption, AXLocker Tool utilizes AES Algorithm. However, it does not attach a filename extension to the encrypted files; that’s why they show up with their normal names.
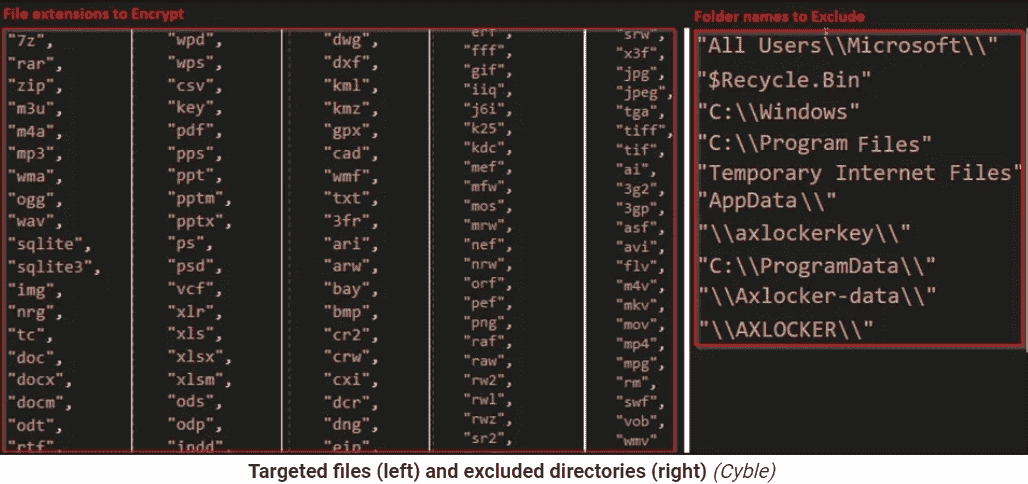
- After that, AXLocker Tool transfer – the victim ID, System Details, Data Stored in Browsers, & Discord Tokens to adversaries’ Discord Channel via Webhook URL.
- AXLocker Tool will scan the following directories to steal Discord Token and extract tokens via regular expressions.
- Discord\Local Storage\leveldb
- discordcanary\Local Storage\leveldb
- Discordptb\leveldb
- Opera Software\Opera Stable\Local Storage\leveldb
- Google\Chrome\User Data\\Default\Local Storage\leveldb
- BraveSoftware\Brave-Browser\User Data\Default\Local Storage\leveldb
- Yandex\YandexBrowser\User Data\Default\Local Storage\leveldb
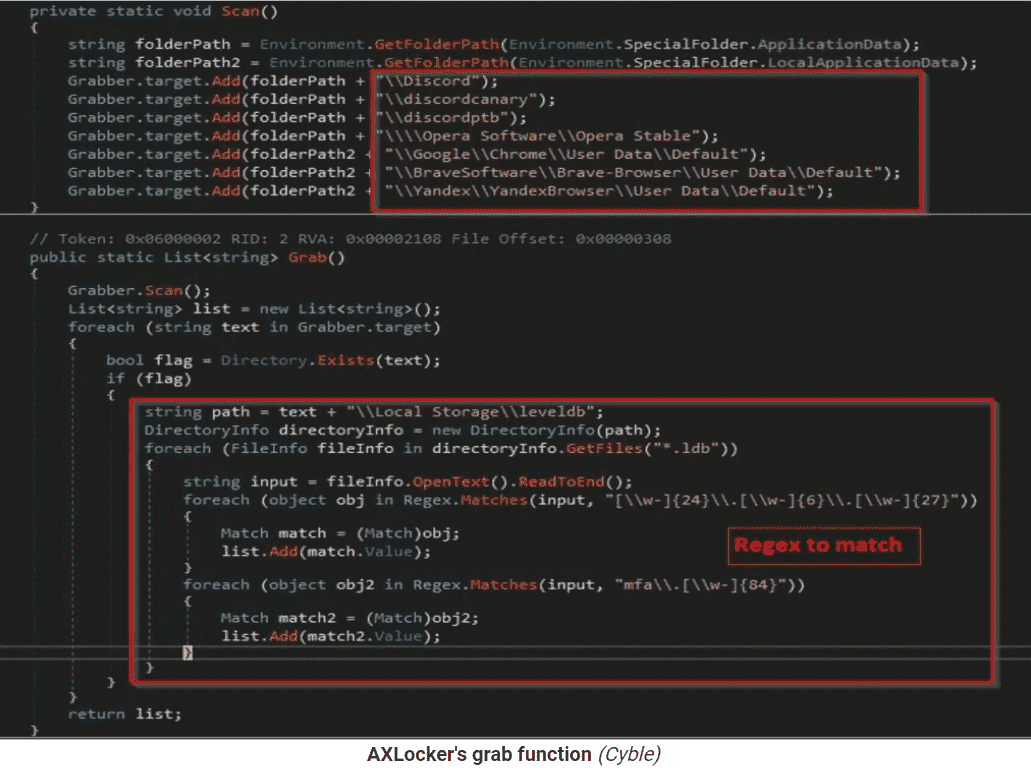
- Following the process, victims see a pop-up window with a ransom note that notifies them that their data has been encrypted and how to contact adversaries to pay ransom for getting a decryptor.
- Adversaries set 48 hours of contact time for victims with their victim ID; however, the ransom charge is anonymous in the note.
As the ransomware potentially targets clients instead of organizations, it could become a “BomB” for huge communities. Thus, if you see your computer getting encrypted by AXLocker Tool, you should immediately change your Discord Password.
This will stop the validation of stolen tokens by ransomware. Hush! This may not be helpful in file recovery, but it will stop further victimization of your accounts, data, and the groups you have joined.
For more amazing facts & information like this, you can follow us on News4Hackers. Leave a comment if you have any queries.
Kindly read more articles :
Thales, French Defence and Technology Group victimized by Lockbit Gang | Data Leaked
TikTok came back again by Backdoor in India. How & Why, Read Now!