Enumeration in Ethical Hacking

Enumeration in Ethical Hacking
Enumeration in Ethical Hacking
An essential step in the ethical hacking process is enumeration, which gives practitioners useful data on the target systems, services, and users. As part of the Certified Ethical Hacker v12 (CEH v12) curriculum, mastering enumeration techniques is essential for identifying potential vulnerabilities and attack vectors. In this article, we explore the fundamentals of enumeration, along with the tools and commands used by ethical hackers to conduct thorough assessments.

Understanding Enumeration:
Enumeration involves the systematic extraction of information from target systems, networks, and applications. By enumerating available resources, services, and configurations, ethical hackers gain insights into the structure and vulnerabilities of the target environment. Enumeration serves as a precursor to further analysis and exploitation, enabling practitioners to assess security risks and devise appropriate mitigation strategies.
Enumeration Techniques:
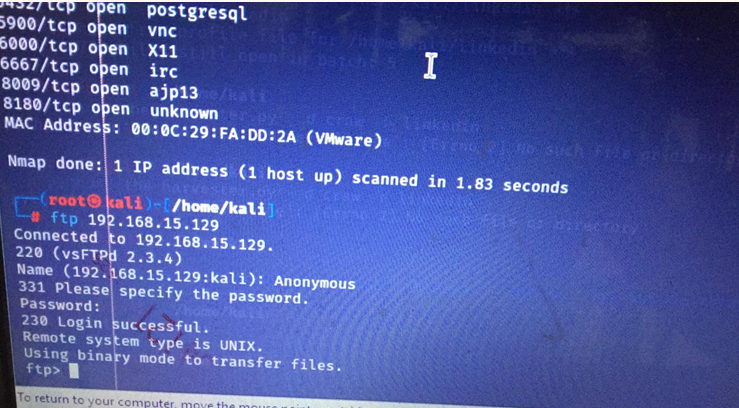
- Service Enumeration: Service enumeration involves identifying and enumerating network services running on target systems. Ethical hackers leverage port scanning techniques to discover open ports and services, such as FTP, SSH, Telnet, HTTP, and SMTP. Once identified, practitioners use service-specific enumeration techniques to gather additional information, such as version details, banner messages, and configuration parameters.
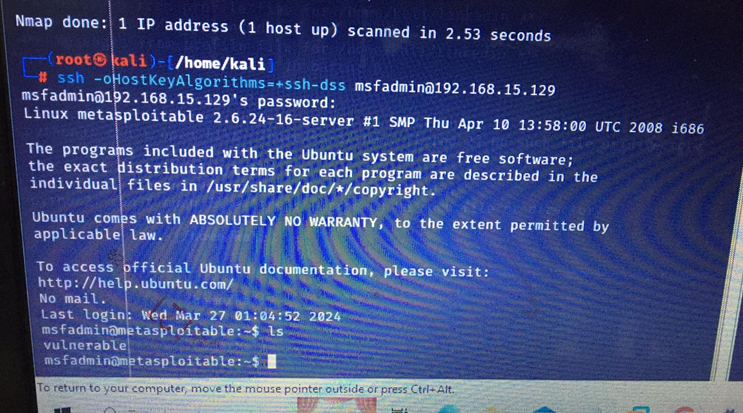
- User Enumeration: User enumeration focuses on identifying valid user accounts within target systems or applications. Ethical hackers leverage various techniques, such as brute force attacks, username enumeration, and user profiling, to gather intelligence about user accounts and access privileges. User enumeration is critical for assessing the strength of authentication mechanisms and identifying potential avenues for unauthorized access.
- Network Enumeration: Network enumeration involves mapping and profiling network resources, devices, and configurations. Ethical hackers utilize techniques such as network scanning, SNMP enumeration, and DNS enumeration to discover network topology, device relationships, and service dependencies. Network enumeration provides valuable insights into the scope and complexity of the target environment, facilitating targeted attacks and lateral movement.
Enumeration Tools and Commands:
- Nmap (Network Mapper):
- Command: nmap -sV -A [target]
- Description: Nmap is a versatile network scanning tool that supports service version detection (-sV) and aggressive enumeration (-A), providing detailed information about target systems and services.
- Enum4linux:
- Command: enum4linux [target]
- Description: Enum4linux is a Linux utility for enumerating information from Windows and Samba systems, including user accounts, share permissions, and group memberships.
- SNMP Enumeration Tools:
- Command: snmpwalk -c public -v1 [target]
- Description: SNMP enumeration tools like snmpwalk allow for querying SNMP-enabled devices to retrieve system information, network configurations, and device statistics.
- LDAP Enumeration Tools:
- Command: ldapsearch -x -h [target] -b “dc=example,dc=com”
- Description: LDAP enumeration tools like ldapsearch enable querying LDAP directories to extract information about users, groups, and organizational units within Active Directory environments.
- DNS Enumeration Tools:
- Command: dnsrecon -d example.com
- Description: DNS enumeration tools like dnsrecon facilitate querying DNS servers to discover domain information, subdomains, and DNS records.
Conclusion:
Enumeration is a fundamental aspect of ethical hacking, providing practitioners with the insights needed to assess the security posture of target systems and networks. By mastering enumeration techniques and leveraging appropriate tools and commands, ethical hackers can identify vulnerabilities, assess risks, and contribute to the ongoing effort of safeguarding digital assets. As ethical hacking continues to evolve, continuous learning and experimentation are essential for staying abreast of emerging threats and techniques in enumeration.
READ MORE ARTICLE HERE







