Microsoft: Cybercriminals “Cadet Blizzard APT” is controlled by Russia’s Military Intelligence “GRU”

GRU has control over Russian-Linked APT Group “Cadet Blizzard,” which is succumbed to a series of wiping attacks from Microsoft.
According to Microsoft, the perpetrator behind all attacks done by the Russian APT Group “Cadet Blizzard” was none other than the Russian General Staff Main Intelligence Directorate “GRU.”
IT Behemoth
Cadet Blizzard is unique from other recognized APT organizations, such as Forest Blizzard (STRONTIUM) and Seashell Blizzard (IRIDIUM), commanded by the Russian military intelligence GRU.
Moreover, CadetBlizzard actions are incredibly disruptive, unlike those of other APT organizations with ties to Russia.
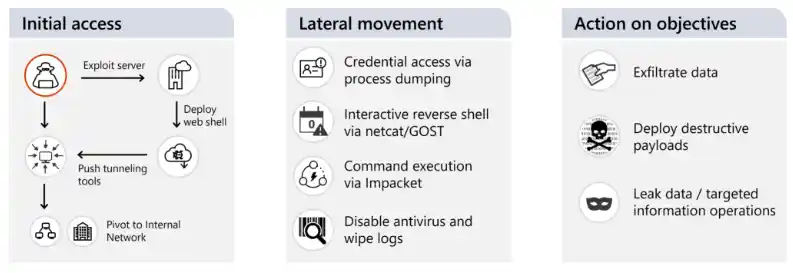
Cadet Blizzard was first recognized by the Microsoft Threat Intelligence Centre (MSTIC) as DEV-0586. In January 2022, the group was seen in Ukraine carrying out devastating malware strikes on numerous organizations.
Cadet Blizzard, the organization that developed and used the WhisperGate wiper, was discovered a month prior to the invasion of Ukraine. The crew was also seen vandalizing various Ukrainian organizations’ websites.
The gang has allegedly been operating since at least 2020, according to Microsoft. It concentrated on emergency services, non-profit/non-governmental organizations, law enforcement, government services, and non-profit/non-governmental organizations in Ukraine.
Microsoft, Report
“Cadet Blizzard is a Russian GRU-sponsored threat group that Microsoft began tracking following disruptive and destructive events occurring at multiple government agencies in Ukraine in mid-January 2022.”
“Cadet Blizzard infiltrates compromised networks and keeps a footing there for months, frequently stealing data before causing disruptions. During January and June 2022, Microsoft noticed a surge in Cadet Blizzard‘s activity, followed by a protracted period of decreased activity.
When the APT performed numerous operations against targets in Ukraine and Europe in January 2023, Microsft noticed a new uptick in the group’s activity. The researcher discovered that the APT group operates seven days a week and performed operations outside of normal office hours for their key European targets.
The researchers alert that the APT group may choose to attack NATO members who assist the military actions of the Ukrainian government. To check environments and evaluate for potential compromise, Microsoft offered signs of compromise.
For more amazing facts & information like this, you can follow us on News4Hackers. Leave a comment if you have any queries.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.
Kindly read another news articles:
Websites of the Swiss Federal Administration are “Unavailable” following a Cyberattack.
An IT expert loses ₹59.65 Lakhs to online criminals in “task fraud.”