Advanced Surveillance Skills Identified in the macOS Variant of LightSpy Spyware

Advanced Surveillance Skills Identified in the macOS Variant of LightSpy Spyware
The LightSpy spyware, which was recently identified as targeting Apple iOS users, is in fact an already undocumented macOS variant of the implant, according to cybersecurity researchers.
The artifacts associated with the cross-platform malware framework that is likely capable of infecting Android, iOS, Windows, macOS, Linux, and routers from NETGEAR, Linksys, and ASUS were analyzed separately by both Huntress Labs and ThreatFabric. The results of their analysis are as follows.
In a report released last week, ThreatFabric stated that the threat actor group employed two publicly available exploits (CVE-2018-4233, CVE-2018-4404) to distribute implants for macOS. “The Metasploit framework is likely the source of a portion of the CVE-2018-4404 exploit.” Those exploits were employed to target macOS version 10.
LightSpy was initially disclosed to the public in 2020; however, the Dutch mobile security firm and Lookout have since disclosed possible links between the spyware and DragonEgg, an Android surveillance tool.
BlackBerry disclosed a “reinvigorated” cyber espionage campaign in April of this year, which was designed to distribute an iOS variant of LightSpy to users in South Asia. However, it has been discovered that this is a macOS version that is significantly more sophisticated and utilizes a plugin-based system to collect a variety of information.
“It is also important to mention that the sample was recently uploaded to VirusTotal from India, but this is not a particularly strong indicator of an active campaign or targeting within the area,” Huntress specialists Stuart Ashenbrenner and Alden Schmidt stated.
“It’s a contributing factor, but without greater proof or insight into delivery processes, it should be taken with a heavy grain of salt.”

The macOS variant has been active in the wild since at least January 2024, according to ThreatFabric’s analysis. However, it is restricted to approximately 20 devices, the majority of which are considered to be test devices.
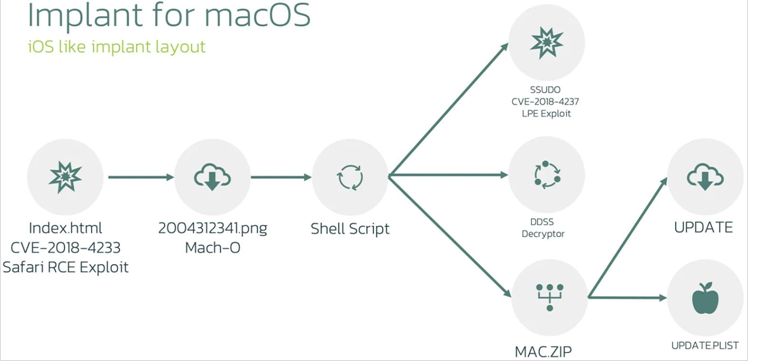
The attack chain commences with the exploitation of CVE-2018-4233, a Safari WebKit vulnerability, through the use of rogue HTML pages to initiate code execution. This results in the delivery of a 64-bit Mach-O binary that impersonates a PNG image file.

The binary is primarily intended to extract and execute a shell script, which in turn retrieves three additional payloads: a ZIP archive, an encryption/decryption utility, and a privilege escalation exploit.
Subsequently, the script extracts the contents of the ZIP archive — update and update.plist — and grants root privileges to both. The information property list (plist) file is employed to establish persistence for the other file, ensuring that it is launched upon each system restart.
The “update” file (also known as macircloader) functions as a loader for the LightSpy Core component, enabling the latter to establish communication with a command-and-control (C2) server, retrieve commands, and download modules.

The macOS version includes support for ten distinct plugins that can be used to capture audio from the microphone, take photos, record screen activity, harvest and delete files, execute shell commands, grab the list of installed applications and running processes, and extract data from web browsers (Safari and Google Chrome) and iCloud Keychain.
Additionally, two additional plugins enable the capture of information regarding all other devices that are connected to the same network as the victim, the list of Wi-Fi networks to which the device has connected, and the specifics of adjacent Wi-Fi networks.

“The Core serves as a command dispatcher and additional plugins extend the functionality,” ThreatFabric emphasized. “Both the Core and plugins could be updated dynamically by a command from C2.”
The cybersecurity firm claimed that it was able to identify a misconfiguration that enabled access to the C2 panel, which includes a remote control platform that contains information about the victims and the associated data.
“Regardless of the targeted platform, the threat actor group focused on intercepting victim communications, such as messenger conversations and voice recordings,” according to the organization. “For macOS, a specialized plugin was designed for network discovery, aiming to identify devices in proximity to the victim.”

The development is the result of attacks on Android devices that have targeted users of mobile banking apps in Uzbekistan and Brazil with well-known banking trojans, including BankBot and SpyNote. Additionally, users in Latin America and the Caribbean were infected by impersonating a Mexican telecom service provider.
Additionally, a report from the Citizen Lab and Access Now has revealed evidence of Pegasus spyware attacks that targeted seven Russian and Belarusian-speaking opposition activists and independent media in Poland, Lithuania, and Latvia.
“The deployment of Pegasus spyware to target Russian- and Belarusian-speaking journalists and activists dates back until at least 2020, with more attacks following Russia’s full-scale invasion of Ukraine in February 2022,” Access Now reported, indicating that “a single Pegasus spyware operator may be behind the targeting of at least three of the victims and possibly all five.”

In a statement that was shared with Meduza, NSO Group, the manufacturer of Pegasus, stated that it is unable to disclose information regarding specific customers. However, it did clarify that it exclusively distributes its products to countries that are affiliated with the United States and Israel. It also stated that it would commence an investigation, following which it may suspend or terminate the service.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE






