For Continuous 5 Years, Chinese Hackers Have Operated Undetected in U.S. Critical Infrastructure

For Continuous 5 Years, Chinese Hackers Have Operated Undetected in U.S. Critical Infrastructure.
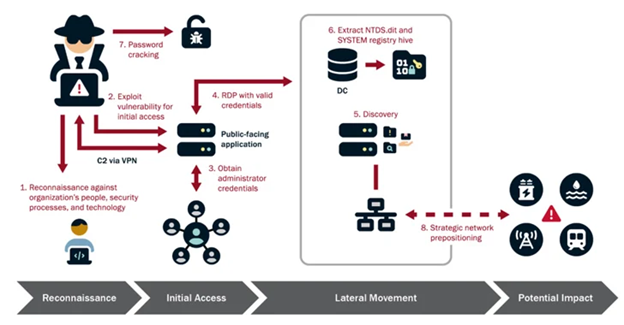
The U.S. authorities announced on Wednesday that the Chinese state-sponsored hacking gang, Volt Typhoon, has infiltrated some vital infrastructure networks within the country for a minimum of five years.
The threat actor’s targets encompass the industries of communications, energy, and transportation, as well as water and wastewater infrastructure in the United States and Guam.
The U.S. government stated that Volt Typhoon’s selection of targets and behavior does not align with conventional cyber espionage or intelligence-gathering operations. The U.S. authoring agencies have a strong belief that Volt Typhoon actors are strategically positioning themselves on IT networks in order to laterally move to OT assets and disrupt their functions.

The objective is to establish a presence on IT networks in advance, ensuring continuity and gaining comprehensive knowledge of the target environment. This is done to carry out disruptive or damaging cyber attacks on essential infrastructure in the United States, specifically during a significant crisis or conflict with the nation.
The collaborative advisory, issued by the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and the Federal Bureau of Investigation (FBI), received support from other countries belonging to the Five Eyes (FVEY) intelligence alliance, including Australia, Canada, New Zealand, and the U.K.

Volt Typhoon, also known as Bronze Silhouette, Insidious Taurus, UNC3236, Vanguard Panda, or Voltzite, is a clandestine cyber espionage outfit based in China that is thought to have been operational since June 2021.
The incident was initially discovered in May 2023 when FVEY and Microsoft disclosed that the hacking group successfully gained long-term access to vital infrastructure organizations in the U.S. and Guam without being detected. They achieved this primarily by utilizing living-off-the-land (LotL) techniques.

The U.K. National Cyber Security Centre (NCSC) stated that “living off the land” is a type of tradecraft that enables attackers to operate covertly. This involves conducting malicious activities that appear similar to legitimate system and network behavior, making it challenging for organizations with advanced security measures to distinguish between them.
Volt Typhoon employs a strategy of utilizing multi-hop proxies, such as KV-botnet, to redirect malicious traffic through a network of compromised routers and firewalls in the United States. This is done to conceal the true source of the activity.
In a study issued in June 2023, cybersecurity firm CrowdStrike acknowledged its heavy dependence on a wide range of publicly available tools to target a specific group of victims in order to accomplish its strategic objectives.
The agencies observed that Volt Typhoon actors engage in thorough pre-exploitation reconnaissance to gather information about the target organization and its surroundings. They then customize their tactics, techniques, and procedures (TTPs) to suit the victim’s specific environment. Furthermore, they allocate continuous resources to sustain their presence and knowledge of the target environment, even after the initial compromise.
The gang also depends on authentic accounts and utilizes robust operational security, which, when combined, enables long-term persistence without being detected.

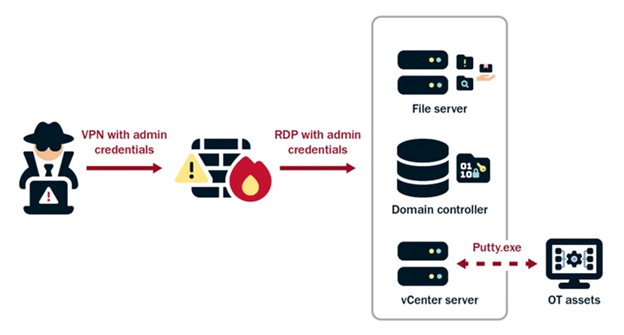
In addition, the nation-state has been detected trying to acquire administrator credentials within the network by exploiting privilege escalation vulnerabilities. They then use the increased access to move laterally, gather information, and fully infiltrate the domain.
The primary objective of the campaign is to maintain access to the infiltrated environments, systematically redirecting their efforts over a span of years to verify and broaden their unlawful entry points. According to the agencies, they demonstrate their careful and thorough approach by frequently obtaining domain credentials to ensure continued access to up-to-date and valid accounts.

The CISA, FBI, and NSA stated that the actors not only exploit stolen account credentials but also employ LOTL tactics to evade detection and refrain from leaving any malware artifacts on systems that could trigger warnings.
“Their unwavering emphasis on covert operations and operational security enables them to sustain undetected presence over extended periods of time.” In addition, Volt Typhoon improves its operational security by selectively deleting logs to hide their activities within the infiltrated environment.
The recent revelation by Citizen Lab has uncovered a network of 123 websites across 30 countries in Europe, Asia, and Latin America. These websites, impersonating local news outlets, are part of a large-scale influence campaign orchestrated by a Beijing-based public relations firm called Shenzhen Haimaiyunxiang Media Co., Ltd. The campaign aims to promote pro-China content.

The digital watchdog located in Toronto, known as PAPERWALL, has identified an influence operation that bears resemblances to HaiEnergy. However, it is important to note that the two operations have different operators and distinct tactics, techniques, and procedures (TTPs).

The Citizen Lab stated that a prominent characteristic of PAPERWALL, which can be witnessed on several websites, is the transient quality of its most forceful elements. This refers to the regular removal of pieces that criticize Beijing’s critics from these websites, occurring sometime after their first publication.
The spokeswoman for China’s embassy in Washington, in a statement provided to Reuters, criticized the tendency to label pro-China articles and publications as ‘disinformation’ while seeing anti-China ones as ‘actual information,’ deeming it a clear example of bias and double standards.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE NEWS HERE
Two are Arrested After Delhi Police Expose an Accounts For Hire Racket
FASTag Fraud: Beware of Becoming A Victim of FASTag Fraud at Toll Plazas
A Mumbai-based investor was duped out of ₹4.56 crore in cyber fraud on Instagram.







