Fresh Wi-Fi Vulnerabilities Offer Cyber Intruders Access to Android and Linux Devices.
Fresh Wi-Fi Vulnerabilities Offer Cyber Intruders Access to Android and Linux Devices.
Two authentication circumvent vulnerabilities have been discovered in open-source Wi-Fi software installed on Android, Linux, and ChromeOS devices. These vulnerabilities have the potential to deceive users into connecting to a rogue network replicating a legitimate one or granting an attacker access to a trusted network without requiring a password.

CVE-2023-52160 and CVE-2023-52161, which correspond to vulnerabilities identified during security evaluations of wpa_supplicant and Intel’s iNet Wireless Daemon (IWD), were identified, respectively.
“By exploiting these vulnerabilities, malicious actors can trick users into connecting to phony trusted networks, intercept their traffic, and gain access to otherwise secure networks without requiring the password,” according to a new study conducted by Top10VPN and Mathy Vanhoef, who has identified Wi-Fi attacks such as KRACK, DragonBlood, and TunnelCrack.

Specifically, CVE-2023-52161 grants an adversary the ability to illicitly infiltrate a secured Wi-Fi network, thereby putting current users and devices at risk of malware infections, data breaches, and business email compromise (BEC). It is present in IWD versions 2.12 and earlier.
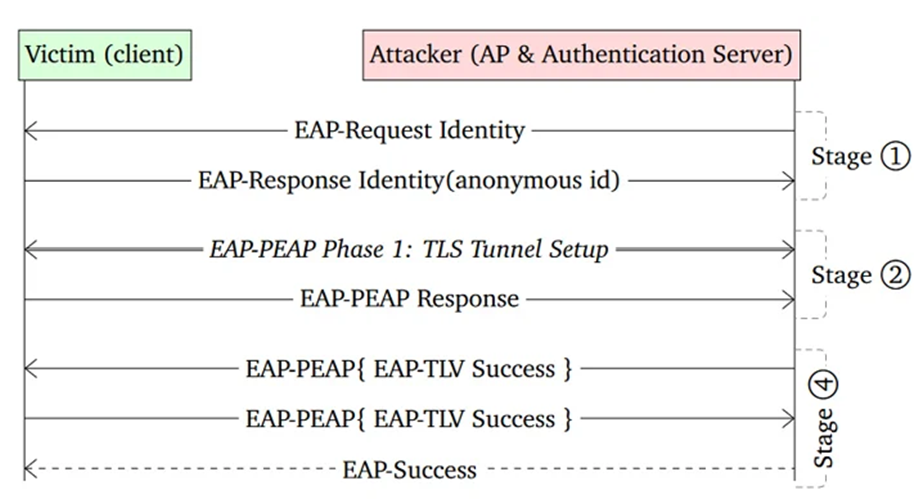
The vulnerability CVE-2023-52160, conversely, impacts wpa_supplicant 2.10 and earlier. Furthermore, it is the more critical of the two vulnerabilities due to the fact that it constitutes the default software utilized by Android devices to process authentication requests to wireless networks.
However, this only affects Wi-Fi clients that have not been appropriately configured to authenticate the authentication server’s certificate. However, any network that employs a Linux device as a wireless access point (WAP) is susceptible to CVE-2023-52161.
In order to exploit CVE-2023-52160 successfully, the perpetrator must possess the SSID of a Wi-Fi network to which the target has previously established a connection. Additionally, the threat actor must be in close physical proximity to the victim.
“One possible such scenario might be where an attacker walks around a company’s building scanning for networks before targeting an employee leaving the office,” according to the investigators.
Ubuntu (1, 2), Debian (1, 2), and Red Hat (1), among other major Linux distributions, have issued advisories regarding the two vulnerabilities. The wpa_supplicant vulnerability has been rectified in ChromeOS versions 118 and later; however, Android solutions have not yet been released.

“In the meantime, it’s critical, therefore, that Android users manually configure the CA certificate of any saved enterprise networks to prevent the attack,” according to Top10VPN.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE






