Know All About WPScan: A Widely Famous Cybersecurity Tool

Know All About WPScan: A Widely Famous Cybersecurity Tool
WPScan serves as an indispensable instrument in protecting WordPress sites from potential vulnerabilities. In light of the ongoing evolution of cyber threats, implementing routine searches using WPScan can aid in the detection of security vulnerabilities and safeguard websites against potential assaults.
How To Start Using WPScan?
Use this command:
gem update wpscan
If you installed on a Mac using the Homebrew method, substitute the following:
brew upgrade wpscan
How to run a basic scan with WPScan?
Your WPScan command will invariably commence with the word “wpscan” and subsequently specify the URL of the target application.
wpscan –url yourwebsite.com
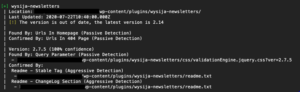
Executing the preceding command will conduct a rudimentary survey of your website. WPScan will generate a plethora of “Interesting Findings” from your site’s code within a few moments. The aforementioned information may comprise:
- Headers to discover server information
- Accessibility of xmlrpc.php
- Accessibility of wp-cron.php
- WordPress version
- Active theme and its basic information
- Active plugins and their basic information
- Discoverable Config backups
Diverse configurations of websites and servers may expose distinct types of information.
Attempt to access your site from behind a firewall by appending the following option to the end of the command:
wpscan –url yourwebsite.com –random-user-agent
- Enumerate all installed plugins:
> wpscan –url https://example.com –enumerate ap - Enumerate all themes:
wpscan –url https://example.com –enumerate at - Enumerate users:
wpscan –url https://example.com –enumerate u - Scan and enumerate plugins, themes & users in a single command:
wpscan –url https://example.com –enumerate ap,at,u
Password Brute-Forcing
- Perform a password attack on a specific username:
wpscan –url https://example.com –passwords passwords.txt –usernames admin - Perform a password attack using a list of usernames:
wpscan –url https://example.com –passwords passwords.txt –usernames users.txt - Perform a password attack with a custom password list:
wpscan –url https://example.com –passwords custom.txt
Vulnerability Scanning
- Enumerate All WordPress vulnerabilities:
wpscan –url https://example.com –enumerate vp,vt,vt - Enumerate vulnerable plugins:
wpscan –url https://example.com –enumerate vp,vt,vt - Enumerate vulnerable themes:
wpscan –url https://example.com –enumerate vp - Enumerate vulnerable timthumbs:
wpscan –url https://example.com –enumerate vt - Retrieve plugin and theme vulnerability data from WPVulnDB:
wpscan –url https://example.com –enumerate vp,vt,vt –api-token YOUR_API_TOKEN
Miscellaneous
- Update WPScan’s database:
wpscan –update - Use a custom user agent:
wpscan –url https://example.com –user-agent “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.3”
How News4Hackers Can Help?
News4Hackers is a global news source that offers timely and informative articles on the subject of cybersecurity. Furthermore, News4Hackers is dedicated to delivering current news to our readers regarding the latest advancements, methodologies, technologies, and cyber attacks that specifically target businesses on a global scale. Every day of the week, our news collectors maintain constant vigilance for the latest technological advancements with the intention of delivering them to you in a timely manner.
Moreover, Craw Security maintains an association with News4Hackers, a reputable organization specializing in cybersecurity that offers analysis and perspectives on various notable countries, including India. For any inquiries concerning the commencement dates of their highly effective cybersecurity training courses or any other matter related to cybersecurity, please reach out to them at +91-9513805401.
READ MORE ARTICLE HERE
Aircrack-ng – A Globally Famous Cybersecurity Tool
Metasploit Framework
How to Crack Passwords Using John The Ripper?
Nikto – The Hacker’s Chosen Cybersecurity Tool









