Metasploit Framework

Metasploit Framework
Metasploit Framework is a versatile open-source framework widely used in the realm of penetration testing and ethical hacking. Developed by Rapid7, it stands out for its modularity, allowing users to tailor it to their specific needs. With both a command-line interface (CLI) for scripting and a graphical user interface (Armitage) for a more user-friendly experience, it caters to a broad user base.
Running seamlessly on various operating systems, including Linux, Windows, and macOS, Metasploit ensures flexibility across different environments. Its active community contributes to its continual improvement, with new modules and updates addressing emerging security challenges.
Metasploit’s strength lies in its integration capabilities, allowing users to combine it with other security tools and frameworks. This interoperability enhances overall testing and assessment capabilities. It serves as a valuable learning resource, offering extensive documentation, tutorials, and community forums for individuals interested in mastering penetration testing and ethical hacking.
One notable aspect is its payload customization, enabling users to adapt and refine their approaches based on specific testing requirements. Overall, Metasploit’s adaptability, community support, and educational resources contribute to its prominence in the field of ethical hacking.
# Parts of Metasploit-Framework
It is written in Ruby. And all the plugins, exploits, and modules are also developed in Ruby. This is the only reason you see the ruby in the exploits of exploitDB.
The exploits are developed according to the real-life scenario of an attack. So for example, if the exploit requires authentication, the exploit will have the must to define parameters in the msfconsole.
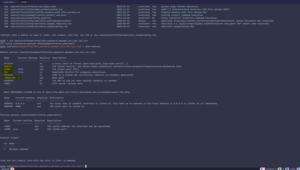
# Pre-requisites
– Ruby Programming Language
– RubyGems
– Database Software
– PostgreSQL recommended; support for MySQL, SQLite
– Java Development Kit (JDK)
– Git
– Network Configuration
– Firewalls configured for necessary communication
– Administrative Privileges
# Auxiliary modules in use
For demonstration purposes, we can use the Metasploit framework for scanning the wordpress website. WordPress is a content management system which is written in PHP language. It is widely used to this date. We have some default (not so hidden) dirs. And this module basically enumerates it.
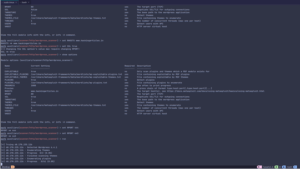
So for example, this is an endpoint that is checked by this module:
`/wp-json/wp/v2/users`
It might tell us the existing wordpress users.
Actually, if you are curious to know how these modules and exploits work then you can check it out by going to this dir:
`/usr/share/metasploit-framework/modules/auxiliary/scanner/http`
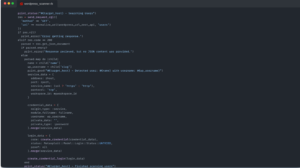
This seems really interesting if you have some experience in developing. You can literally change the entire module/exploit according to your needs.
# msfvenom
msfvenom is a crucial component within the Metasploit Framework, serving as a versatile payload generator and encoder. With its capabilities, security professionals can craft custom payloads tailored to specific exploitation scenarios.
This tool is instrumental in creating a variety of payloads, such as reverse shells and meterpreter sessions, and provides options for specifying payload types, encoding techniques, and output formats. msfvenom plays a vital role in penetration testing and ethical hacking by enabling the development of malicious payloads, often used to assess and enhance the security of systems. Its flexibility and range of supported platforms make it a go-to tool for security practitioners seeking to simulate real-world attack scenarios and strengthen their organization’s defenses. Additionally, its encoding features contribute to evading antivirus detection, making it an essential resource for ethical hackers testing the resilience of target systems.
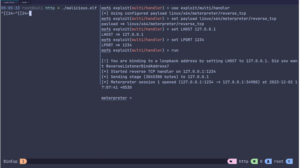
# msfvenom&msfconsole – reverse shell
There are so many platforms reverse shell available on the msfvenom. You can generate the reverse shell payloads for Android, Windows, Linux, OpenBSD, aix, etc. And if you generate the meterpreter session payload with the msfvenom you can get the interactive shell and other working plugins on the msfconsole for that session.
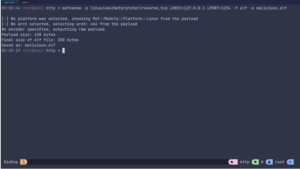
Once I have it generated in elf format for linux, I can just use the msfconsole to listen for the connections.

Once that malicious elf is executed, you can have a meterpreter session opened. Now, you can perform many commands on the victim’s system under the privileges.
How News4Hackers Can Help?
News4Hackers is international-standard cybersecurity news and informatory articles providing organization. At News4Hackers, we sincerely assist our readers in learning about the newest trends, techniques, technologies, and cyberattacks on businesses around the world. Our news collectors keep an eye out 24 hours a day, seven days a week for the latest tech news so that they can get it to you as soon as possible.
In addition, Craw Security is related to News4Hackers, which is the best place to learn about cybersecurity in India and many other well-known countries around the world. You can call their hotline at +91-9513805401 if you have any questions about when their best cybersecurity training classes start or about anything else that has to do with cybersecurity.
READ MORE ARTICLE HERE









