Ransomware Known As Double-Extortion Play Targets 300 Organizations Globally

Ransomware Known As Double-Extortion Play Targets 300 Organizations Globally
As of October 2023, the Play ransomware has reportedly affected around 300 organizations, in accordance with a newly published joint cybersecurity advisory issued by the United States and Australia.
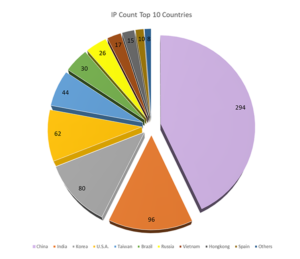
“Play ransomware attackers utilize a double-extortion method, encoding systems shortly after stealing info and have affected an extensive number of businesses and critical infrastructure groups in North America, South America, Europe, and Australia,” according to authorities.
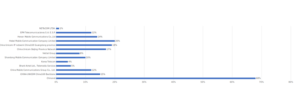
Play, alternatively referred to as Balloonfly and PlayCrypt surfaced in 2022. It infiltrated enterprises and distributed file-encrypting malware by exploiting security vulnerabilities in Microsoft Exchange servers (CVE-2022-41040 and CVE-2022-41082) and Fortinet appliances (CVE-2018-13379 and CVE-2020-12812).
Corvus data indicates that ransomware attacks are increasingly exploiting vulnerabilities as initial infection vectors, with the percentage increasing from nearly zero in the second half of 2022 to nearly one-third in the first half of 2023.
Adlumin, a cybersecurity firm, disclosed in a report released last month that Play has been converted into a ransomware-as-a-service (RaaS) operation by being made available to other threat actors “as a service.”
The group’s ransomware attacks are distinguished by the utilization of both publicly available and custom tools, such as AdFind for initiating Active Directory queries, GMER, IOBit, and PowerTool to incapacitate antivirus software, and Grixba to gather data on backup software, remote administration tools, and network configurations installed on a system.

In addition to lateral movement, data exfiltration, and encryption, the threat actors have been observed utilizing Mimikatz, SystemBC, and Cobalt Strike for post-exploitation.
“The Play ransomware gang employs a double-extortion theory, encoding systems shortly after exfiltrating info,” according to the organizations. “Ransom notes do not contain a fresh ransom demand or payment directions, rather, victims are given instructions to get in touch with the threat actors via email.”
Play reportedly claimed the lives of close to forty victims in November 2023, considerably lagging behind its competitors LockBit and BlackCat (also known as ALPHV and Noberus), according to data compiled by Malwarebytes.
The notification arrives several days subsequent to the publication of an updated bulletin by U.S. government agencies concerning the Karakurt group. Recognized for its preference for extortion over encryption-based attacks, the group gains initial network access through phishing, intrusion brokers (also referred to as initial access brokers), and the purchase of stolen login credentials.
“Karakurt victims did not report the encryption of infected machines or files; instead, Karakurt perpetrators have made claims that they stole data and threatened to sell it off or expose it to the general population unless they’re granted payment of the desired ransom,” according to the authorities.

In addition, the developments coincide with rumors that law enforcement may have targeted the BlackCat ransomware, whose dark web breach portals were inaccessible for five days. The e-crime syndicate, nevertheless, attributed the disruption to a hardware malfunction.

Furthermore, it has been reported that an emerging ransomware group called NoEscape executed an exit scam, wherein they allegedly “suspended the group’s web panels and data leak sites in exchange for the ransom payments.” This allegedly prompted other criminal organizations, such as LockBit, to recruit their former associates.
It is not unexpected that the ransomware landscape is in a perpetual state of change and evolution, whether as a result of external pressure from law enforcement or other factors. The collaboration among the BianLian, White Rabbit, and Mario ransomware organizations in a joint extortion campaign that specifically targeted publicly traded financial services firms provides additional evidence for this claim.

Resecurity stated in a report published last week, “These cooperative ransom campaigns are uncommon, but maybe becoming more prevalent due to the participation of initial access brokers (IABs) collaborating with multiple groups on the dark web.”
In addition to this, Resecurity, Inc. (USA) has identified a significant connection among three prominent ransomware groups, a law enforcement agency (LEA), and a prominent investment organization in Singapore, as revealed by a recent Digital Forensics & Incident Response (DFIR) engagement. The HUNTER (HUMINT) division of Resecurity identified a joint extortion campaign involving the BianLian, White Rabbit, and Mario ransomware organizations that targeted publicly traded financial services companies.

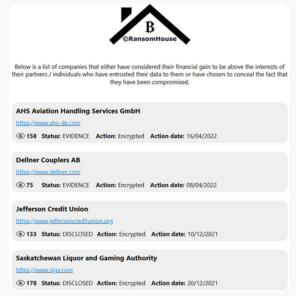
Another element that potentially contributes to increased cooperation is the establishment of cybercriminal diaspora networks through law enforcement interventions. “Participants displaced from these threat actor networks might be more amenable to working together with competitors.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE





