The Most Complex iPhone Hack Ever Compromized a Secret Hardware Function on Apple Devices
Operation Triangulation spyware attacks, which targeted Apple iOS devices, utilized never-before-seen vulnerabilities that allowed adversaries to circumvent critical hardware-based security measures implemented by the company.
Kaspersky, a Russian cybersecurity firm that became one of the targets of the campaign at the start of 2023, characterized it as the “most sophisticated attack chain” it has ever witnessed. Since 2019, the drive is thought to have been active.
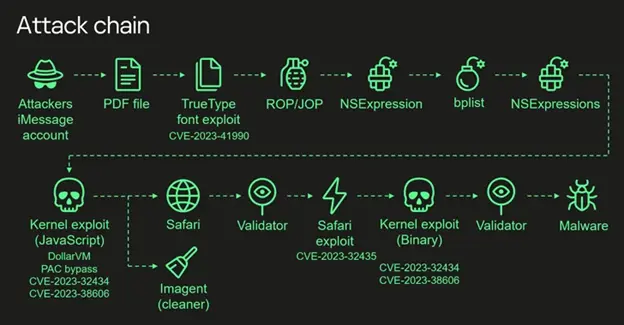
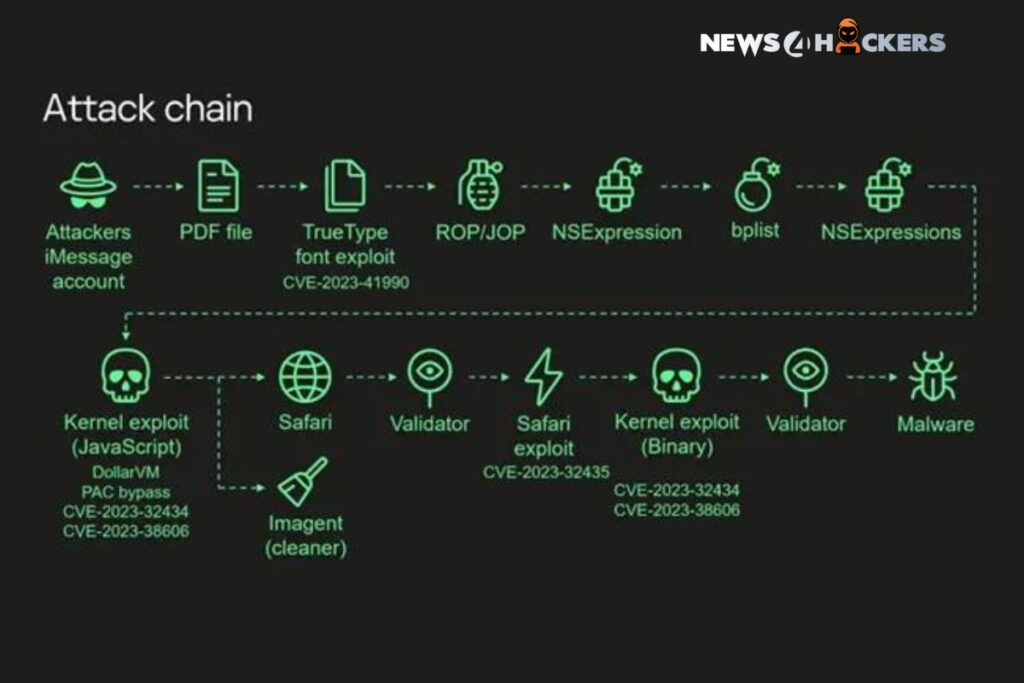
The exploitation operation encompassed the strategic utilization of four zero-day vulnerabilities linked in a sequence to gain an unparalleled degree of access and infiltrate target devices operating iOS versions prior to iOS 16.2. The overarching objective was to amass confidential data.
The zero-click assault commences with an iMessage containing a malevolent attachment, which is processed automatically without user intervention in order to acquire elevated permissions and subsequently execute a spyware module. More precisely, it entails the exploitation of the subsequent susceptibilities as weapons:

- CVE-2023-41990: A vulnerability exists in the FontParser component that, when exploited to process an iMessage containing a specially crafted font file, could result in the execution of arbitrary code. (Apple iOS 15.7.8 and iOS 16.3 address)
- CVE-2023-32434: A kernel integer overflow vulnerability that a malicious application could exploit to execute arbitrary code with kernel privileges. (Apple iOS 15.7.7, iOS 15.8, and iOS 16.5.1 address)
- CVE-2023-32435: A memory corruption flaw in WebKit that, when exploited to process customized web content, could result in the execution of arbitrary code. (Apple iOS 15.7.7 and iOS 16.5.1 address)
- CVE-2023-38606: A kernel vulnerability that allows a malignant application to alter a sensitive kernel state. (Regarded in iOS 16.6)
It is noteworthy to mention that Apple issued patches for CVE-2023-41990 in January 2023. However, the company did not disclose information regarding the exploitation until September 8, 2023, coinciding with the release of iOS 16.6.1, which addressed two additional vulnerabilities (CVE-2023-41061 and CVE-2023-41064) that were actively exploited in the Pegasus spyware campaign.
This increases the total number of zero-day vulnerabilities that have been actively exploited and patched by Apple since the beginning of the year to twenty.

Among the four identified vulnerabilities, CVE-2023-38606 warrants particular attention due to its ability to circumvent hardware-based security measures protecting sensitive regions of the kernel memory. This is achieved by exploiting memory-mapped I/O (MMIO) registers, a previously unidentified and undocumented feature.
The vulnerability specifically affects Apple A12-A16 Bionic SoCs, identifying unidentified MMIO blocks of registers associated with the GPU coprocessor. How the mysterious threat actors responsible for the operation came to be aware of its existence is presently unknown. Whether it was developed by Apple or by a third party such as ARM CoreSight is also unknown.

In other words, CVE-2023-38606 is the pivotal component in the exploit chain that is intricately linked to the efficacy of the Operation Triangulation campaign. This is due to the fact that it grants the malicious actor complete authority over the compromised system.
“Our guess is that this unidentified hardware function was probably put there to be utilized for debugging or testing reasons by Apple engineers or the factory, or that it was added by mistake,” security researcher Boris Larin commented. “Because this function is not utilized by the firmware, we have no idea how intruders would know how to take advantage of it.”
“Although hardware security is considerably more challenging to reverse-engineer than software and frequently relies on ‘security through obscurity,’ this is a defective strategy because all secrets are eventually revealed. ‘Security by obscurity’-based systems are incapable of attaining genuine encryption.”
The emergence of this information coincides with a report by the Washington Post that Apple’s late-October alerts regarding potential state-sponsored spyware attacks against Indian journalists and opposition politicians prompted the government to dismiss the accusations as an “algorithmic malfunction” within the technology behemoth’s systems.

Furthermore, senior administration officials exerted pressure on the company to provide alternative explanations for why the warnings might have been issued and demanded that the political impact of the warnings be mitigated. India has not yet affirmed or denied the use of spyware similar to that developed by the NSO Group’s Pegasus.
The Washington Post reported, citing sources with knowledge of the situation, that “Indian officials requested Apple to retract the warnings and apologize for their error,” and that “Apple India’s corporate communications executives started privately requesting Indian technology journalists to emphasize in their articles that Apple’s warnings might be false alarms,” in an effort to deflect attention from the government.

About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE NEWS HERE
Rubrik, A Microsoft-backed Organization Shares A Plan to “Increase” Cybersecurity in India
Spear-Phishing Attacks by Cloud Atlas Target Russian Agricultural and Scientific Firms








