Top 10 Hacking Jobs in 2024
Top 10 Hacking Jobs in 2024
“Ethical hackers” are of paramount importance in safeguarding against cyber threats within the ever-evolving realm of cybersecurity. As we progress into the year 2024, there is an increasing need for proficient experts in this particular domain.

In addition to possessing the requisite technical expertise to compromise systems, ethical hacking requires an awareness of the intricacies of cybersecurity in order to defend against and protect against cyber threats. With the ongoing expansion of the digital landscape, these leading cybercrime positions will play a crucial role in influencing the security stance of organizations globally.
What are Hacking Jobs?
In the domains of cybersecurity and ethical hacking, careers involving hacking entail the application of one’s expertise in computer networks, systems, and software to detect and resolve security flaws. Ethical hackers, as opposed to malicious hackers, employ their skills to enhance system security and defend against unauthorized hacking endeavors. These occupations are crucial for ensuring the digital security of businesses in a variety of industries.
Here is an examination of the features of hacking jobs:
- Identifying Vulnerabilities,
- Developing Security Solutions,
- Performing Penetration Testing,
- Ensuring Compliance,
- Forensic Analysis,
- Educating and Training, etc.
Top 10 Hacking Jobs in 2024
As we progress into the year 2024, there is an increasing need for proficient experts in this particular domain:
- Cybersecurity Analyst:

Features:
These experts evaluate and appraise weaknesses in the infrastructure (including software, hardware, and networks) and develop tactics to reduce the risks. They have a crucial function in upholding the security stance of a company.
- Penetration Tester (Pen Tester):

Features:
Penetration testers are ethical hackers who mimic cyber-attacks in order to detect and exploit weaknesses in systems, networks, and applications. Their perspectives are essential for fortifying security measures.
- Security Consultant:

Features:
Security consultants provide specialized guidance to enterprises on multiple facets of information security, encompassing the formulation of policies and strategies, evaluation of risks, and handling of crisis situations.
- Incident Responder:

Features:
These experts are the initial responders in the event of a cyber-attack. They oversee the consequences of security breaches, perform forensic investigations, and strive to minimize the harm.
- Network Security Engineer:

Features:
Their responsibility lies in safeguarding the network and its accessible resources against illegal intrusion. Their role entails the implementation of security measures such as firewalls, virtual private networks (VPNs), and intrusion detection systems.
- Chief Information Security Officer (CISO):

Features:
A Chief Information Security Officer (CISO) is a high-ranking executive who holds the responsibility for overseeing the comprehensive information security of a business. Their role involves formulating and executing the long-term security strategy while supervising the safeguarding of IT resources.
- Ethical Hacker for IoT (Internet of Things):

Features:
These hackers specialize in the field of IoT and specifically target security issues related to linked devices. They assess and safeguard a variety of gadgets, spanning from industrial machinery to personal smart devices.
- Application Security Developer:

Features:
These developers prioritize the development of software applications with a strong emphasis on security. They incorporate security measures throughout the development phases of software systems, applications, and programs.
- Cryptographer:

Features:
Cryptographers design cryptographic algorithms, ciphers, and security systems to encode confidential data. In 2024, their position is important as the protection of data privacy and the establishment of secure communications take center stage in the field of cybersecurity.
- Forensic Computer Analyst:

Features:
These analysts discover digital evidence within computers and digital storage devices. They have a crucial function in the investigation of cybercrimes and the provision of evidence for legal proceedings.
Best Course for Hacking in Delhi
Within the periphery of Delhi NCR, there are several courses that you can take to become a verified cybersecurity professional and work as an expert in the near future. In addition to this, you may seek guidance from the best cyber security training professionals with many years of quality experience in training many interested individuals.

To know more about the batches that are available in the near future, give us a call at +91-9513805401 and chit-chat with our skilled educational counselors.
Skills and Expertise
Hackers in professional roles often have a solid background in computer science, information technology, and cybersecurity. Proficiency in programming, network management, and systems analysis is widespread. Moreover, it is anticipated that they possess current knowledge of the most recent cybersecurity trends, technologies, and procedures.
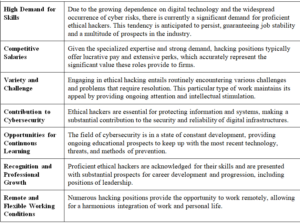
Benefits of Doing A Hacking Job in 2024
Several benefits have been recorded of doing an ethical hacking job so far. There would be an equivalent amount of benefit will be there for doing the same category of jobs in the coming year of 2024.
Some of the prominent benefits of doing an ethical hacking job in 2024 are mentioned below:
| High Demand for Skills | Due to the growing dependence on digital technology and the widespread occurrence of cyber risks, there is currently a significant demand for proficient ethical hackers. This tendency is anticipated to persist, guaranteeing job stability and a multitude of prospects in the industry. |
| Competitive Salaries | Given the specialized expertise and strong demand, hacking positions typically offer lucrative pay and extensive perks, which accurately represent the significant value these roles provide to firms. |
| Variety and Challenge | Engaging in ethical hacking entails routinely encountering various challenges and problems that require resolution. This particular type of work maintains its appeal by providing ongoing attention and intellectual stimulation. |
| Contribution to Cybersecurity | Ethical hackers are essential for protecting information and systems, making a substantial contribution to the security and reliability of digital infrastructures. |
| Opportunities for Continuous Learning | The field of cybersecurity is in a state of constant development, providing ongoing educational prospects to keep up with the most recent technology, threats, and methods of prevention. |
| Recognition and Professional Growth | Proficient ethical hackers are acknowledged for their skills and are presented with substantial prospects for career development and progression, including positions of leadership. |
| Remote and Flexible Working Conditions | Numerous hacking positions provide the opportunity to work remotely, allowing for a harmonious integration of work and personal life. |
Challenges in Doing A Hacking Job
There are certain challenges present as well in performing an ethical hacking job that cannot be neglected. They come hand-in-hand with the benefits.
Some of the primary challenges in doing an ethical hacking job are mentioned below:
- Keeping Up with Rapid Technological Changes,
- High Pressure and Responsibility,
- Legal and Ethical Complexities,
- Sophistication of Cyber Threats,
- Resource Constraints,
- Public Misunderstanding,
- Balancing Proactive and Reactive Strategies, etc.

About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Read More News Here
Govt. of India To Ban 9 Crypto Exchanges Including Binance For Not Complying Anit-Money Laundering Laws
Not Just 2023, 2024 will also Witness Significant Advancements in AI
How Safe Are Indians from Cyber Crime? 761 Cyber Attacks Every Minute in 2023, Even ISRO Targeted!