“Top 10 Computer Viruses 2023”

Computer Viruses create chaos in the world. Have you noticed yet? Hello there! As you know, our world is developing at a faster rate; a need has emerged to learn about information, technology, and data security.
Moreover, there are a lot of things that you need to know about in the IT Industry cuz most things are connected to and depend upon the IT Sector. Sharing information & ideas with everyone from afar has become possible with the help of online platforms or, we can say, the Internet.
In today’s topic, we’ll talk about some of the most brutal software that created chaos in the IT Sector with a huge amount of assets, & monetary loss. As you know, there is a lot to learn in this industry, and we’ve got the opportunity to explore many more things than focusing on a single one. Most Brutal Weapons, “Computer Viruses.”
What is a Computer Virus?
A malicious program (software) is executed to replicate, make modifications to other system features, and enter its own code. Its replication can impact various features of a computer system, and then the system will become a “Compromised Device.” Due to such impact, things as the below happen.
- Slow System Performance,
- Data Loss, and
- System Crashes.
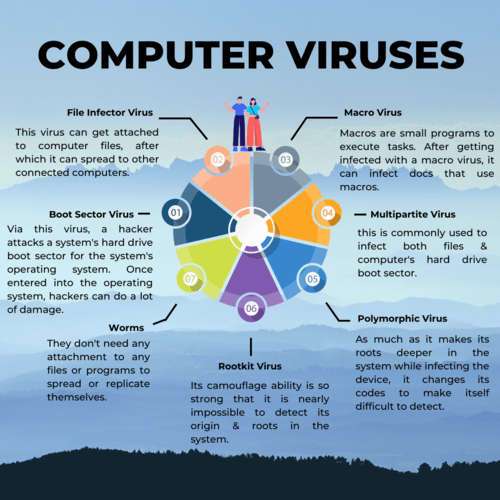
Types of Computer Virus
Various kinds of viruses have been launched in the few years.
History of Computer Virus?

Top 10 Virus Attacks in History





Top Computer Viruses 2023
1) I-Worm

I-Worm, a virus capable of spreading via making its replica. It sends itself to other connected devices via email. Moreover, it’s also known as a “worm” cuz it spreads itself via networks, similar to an earthworm. It can cause a lot of trouble to networks while deleting/ corrupting files and utilizing system assets.
2) Reveton
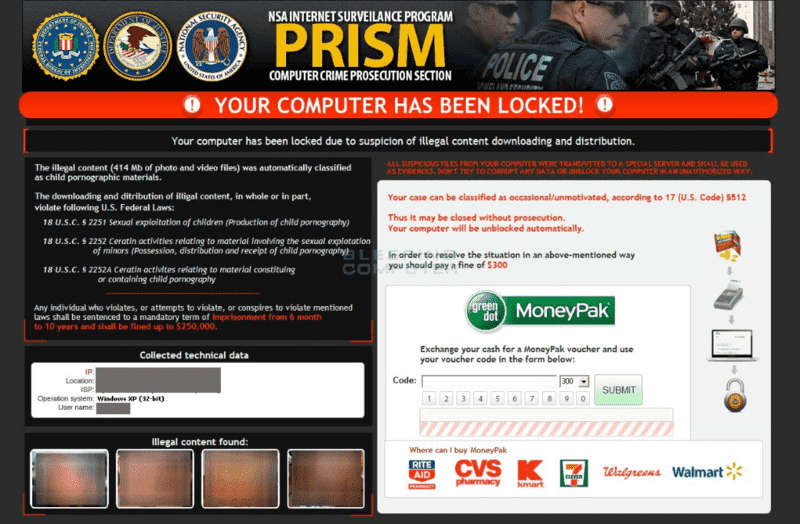
It’s malware specifically customized to extort money from victims by showing fake alerts claiming the victim has committed a crime and is liable for the sin. Message imitates a legitimate law enforcement warning. Sometimes, it also shows up with a replica of a legitimate law enforcement logo.
The victim is tormented with a fake fine to pay in 48 hours or is said that he needs to wait for further legal action. Sometimes, malware can lock the compromised device and block access to the desktop.
3) Dyreza

Using this malware, adversaries steal financial credentials from anonymous targets. Usually, it is presented via email/ web pop-ups in order to fool users into installing malware. Using malware, adversaries can also collect data saved on the devices related to
a) Usernames and Passwords,
b)Credit Card Numbers and
c)other Sensitive Data.
4) Shamoon

Found in 2012, it was a massive destructive tool that victimized Windows-based systems. Organizations’ networks were in a great state of danger because of it.
The Virus was capable of deleting data, & overwriting the Master Boot Record of the compromised PC, which slowed down the machine’s features.
Moreover, the Middle East was the most time victim of cyber-attacks pulled out with the help of the Shamoon virus.
5) Flame

It is a highly advanced and customized investing tool found in 2012. Usually used in the collection and analysis of data from PC & networks. However, it’s capable of a lot of malicious acts, such as
- Stealing Passwords,
- Capturing Screenshots & Keyboard Strokes, and
- Monitoring Network Activity.
Believers believe that it was specifically designed for espionage & cyberwarfare operations while a nation-state manufactured it.
6) Ransomware

These are some specifically designed malicious software to block access to a PC/ data until the due ransom. They make their way commonly via phishing emails/ fake websites. Once deployed, it encrypts files and folders on the device. Then shows a message of ransom demand to pass the decrypt key.
7) Zeus Trojan

Basically used to steal confidential financial credentials from anonymous targets. Spreading ways are via malicious emails, websites, and other online sources. Moreover, it’s capable of
- Stealing Passwords
- Credit Card Numbers
- other Confidential Data from Targets.
Its most dangerous attribute is that it can evade detection from anti-virus programs. It can also be used to generate botnets for sending spam emails and other malicious stuff.
What do we need to know about computer viruses in 2023?
2023 is the year we need to be more advanced in getting to know the ways of hackers. Predictions say that viruses will be able to spread faster and go through networks without getting detected. Further, it demands enhanced security measures to protect our data from online threats.
Ensure that the following steps are followed properly
a) Daily software update
b) An antivirus Program must be installed on all devices.
c) Avoid phishing emails and other social engineering tactics
All that is to protect their data and online activities.
For more amazing concepts and knowledge, follow our official page of News4Hackers. Learn, Research, and Grow!
If you want to learn more about ethical hacking, you can get in contact with Craw Security.
Kindly read another articles:
Internal Investigation is running on Network Breach | FBI Hack
GoDaddy Became the Victim of a Data Breach Caused by an Anonymous Hacker Group